Syrian hackers tweaked Twitter and The New York Times DNS records

The Syrian Electronic Army (SEA) claimed responsibility for hacking the DNS servers on Twitter and The New York Times, writes TechCrunch. Resources were attacked through their domain registrar Melbourne IT. By accessing registry entries, the SEA was able to change contact information and DNS.
It all started with the fact that the publication of The New York Times announced its hacking, namely the substitution of the DNS. The hack was attributed to the Syrian Electronic Army, because the DNS servers were redirected to a resource associated with the SEA.
During the interruption, The Times tried to compensate for the loss of control over DNS servers by posting on Twitter direct links to their IP address and news in the mobile version of news.nytco.com. At the same time, The Wall Street Journal took advantage of the situation by temporarily making its materials free.
')
Soon, problems appeared on Twitter image hosting. This was followed by a tweet from a hacker group stating that they had gained control of the Twitter.com domain. However, Twitter's DNS records were not changed, only contact information.
SEA later claimed responsibility for spoofing the Huffington Post UK and The New York Times DNS records. In the following tweet, the group announced the interception of the domain Twitter.co.uk, which also began to redirect to the SEA server. Domain Twimg.com, used for images and avatars Twitter, was intercepted in a similar way.
In general, the group announced access to 8 international domains of Twitter:
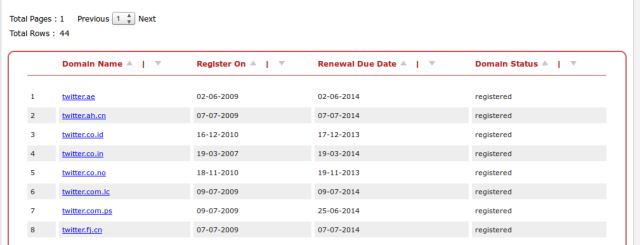
Both The New York Times and Twitter are ruled by Melbourne IT. After detecting a DNS spoofing, the registrar confirmed that the DNS records were changed through a reseller account in the Melbourne IT system, and stated that he is now checking the logs in order to determine, if possible, who used the reseller's login and password.
Source: https://habr.com/ru/post/191670/
All Articles