Extortionist Win32 / Nymaim - Obfuscation Chronicles
Last month, we wrote about the Home Campaign malware campaign. The attackers for a long time compromised web servers running Apache Linux, using a malicious Apache module known as Darkeech (found by ESET as Linux / Chapro). This code was used to redirect website users to the Blackhole Exploit Kit. The analysis of the attack revealed that its payload was the Win32 / Nymaim family of ransomware (ransomware). This analysis focuses on the technical features of this malware and how to install it on users' computers.

Infection
')
The method by which users infect Nymaim is shown below. As we mentioned earlier, it consists in a user visiting a compromised web server through which a web page with malicious code is delivered. In the case of Nymaim, the result of visiting such a resource becomes a blocked user's computer. To download the main Nymaim code, the well-known “ Pony Loader ” downloader is used (found by ESET as Win32 / Fareit ).
To maintain the visible legitimacy of its executable file, Fareit is provided with digital signature information.

Such an attribute of samples Fareit gave us the opportunity to group the necessary samples for analysis. Analyzing them, we found out that the catch-cdn.com domain was used by this malicious code to extract Nymaim droppers, which was then installed on compromised computers. We observed the download of a file with the same name 6.exe, which at different times was Win32 / Sirefef (aka ZeroAccess), Win32 / Urausy (Win32 / LockScreen) and Win32 / Nymaim droppers. The following figure shows the timeline for the distribution of malware that was downloaded to this static URL.
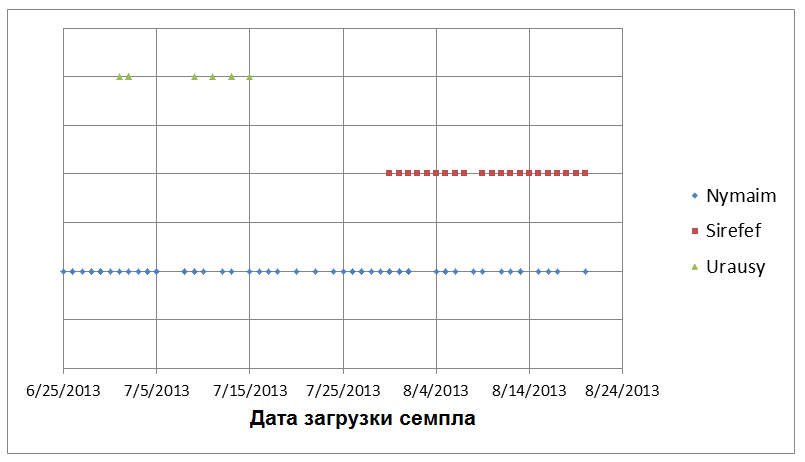
The algorithm used to change these families of malicious programs on the server is not entirely clear to us. We noted that the Urausy samples were available for download the first half of July. Sirefef appeared at the beginning of August, and Nymaim appeared regularly throughout the entire time interval.
Specifications
The process of infection Win32 / Nymaim can be divided into two stages. At the first stage, the downloader tries to download the main body of Nymaim by accessing the list of hard-wired IP addresses. After the download is complete, this code renames its file to an arbitrary name. At each of these stages, the extortionist uses several common methods to prevent his analysis.
One of these methods is obfuscation of the code execution flow (control flow obfuscation). Malicious code manually modifies the call stack to transfer control to the desired function, thus hiding the true transitions between functions during static analysis.
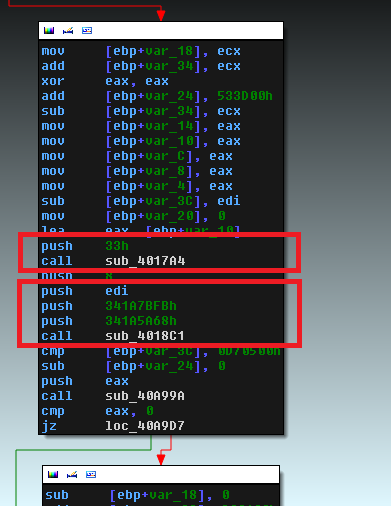
In the screenshot above, two obfuscation methods are highlighted. The first is to call a function that modifies the value on the stack of the parent function depending on the parameter passed. In more detail, this method is presented below.
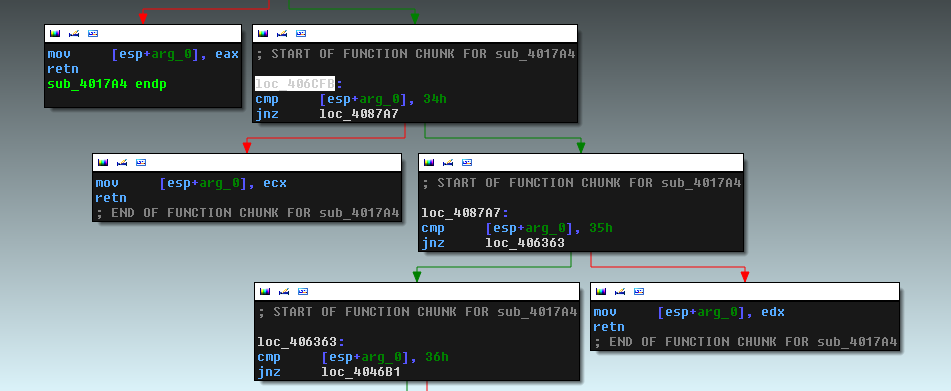
Depending on the argument passed to the function (0x34, 0x35, 0x36), the contents on the stack are modified by one of the registers, which is equivalent to a simple push reg command. For example, in the case of the argument 0x34, we get push ecx.
The second method of obfuscation is used in the function below and is intended to hide the true addresses of the called functions. Below you can see that the argument passed to the function will be used as an offset when calling another function, that is, it is used as a constant to calculate the required address.
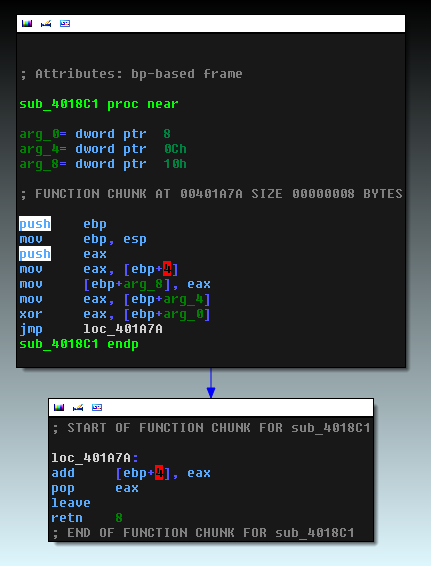
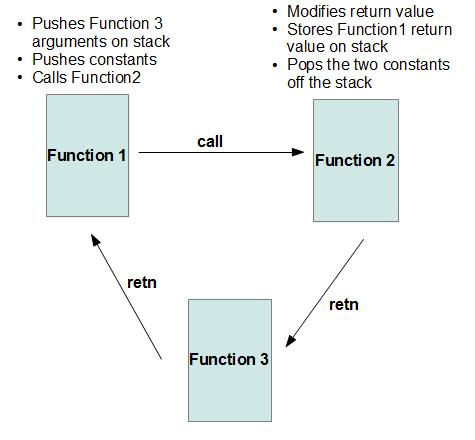
As can be seen from this code, the function uses two constants, passed to it as arguments, to calculate the required bias using XOR and ADD operations. Next, the result of this operation is saved on the stack, and the value of the address used by the retn function to transfer control to the calling function is modified. This will invoke the new function.
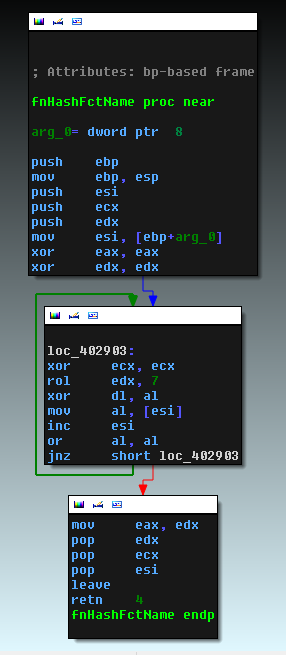
Another type of obfuscation used in Nymaim refers to calling the Win32 API functions. When the malicious code needs to call the desired function from the DLL, it reads the base address of this DLL from the encrypted data section. The address of the functions is calculated by pre-prepared hashes of the names of these functions. Below is the function code that computes the hash of the function name. It is then used for comparison.
When the address of the function is found, it is stored in memory and then used in various places in the code using a jump instruction. Another feature is the fact that when returning from the API, the execution flow goes not to the malicious code, but to the instruction in the ntdll.dll call EBX. Immediately before calling the API, Nymaim modifies the stack so that after exiting the API, the thread of execution switches to ntdll.dll, and EBX, in turn, will contain the actual return address. More clearly, this process is shown below.
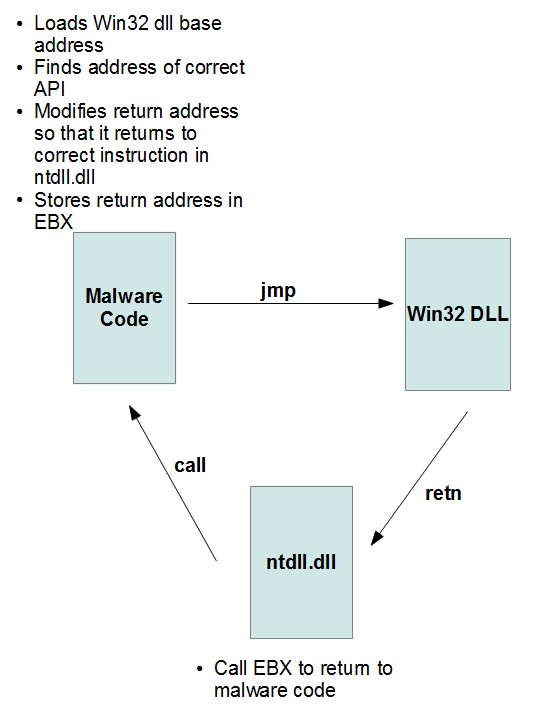
Such manipulations allow Nymaim to make debugging difficult, especially when stepping through (tracing). The stack-correctable return address prevents the function from executing in the debugger “before returning from the function”.
Nymaim uses string encryption. The decryption function is as shown below.

At the second stage of its execution, Win32 / Nymaim uses similar methods of obfuscation, but the code functionality has been extended to ensure survival after a reboot and block the screen. Malicious code uses the usual autorun practice of writing itself to Software \ Microsoft \ Windows NT \ CurrentVersion \ Winlogon \ shell.
Our analysis showed that in some situations, Win32 / Nymaim at the second stage of its execution installs another threat on a compromised computer, namely Win32 / Sirefef. In addition, in the future, Nymaim can download to the computer and other Trojan programs.
The main task of Nymaim is to block the computer. To do this, download the HTML page with information about blocking. This flexibility allows attackers to display various user-intimidating pages, for example, depending on its location or software installed on it (for example, any media files or torrent client). As a result, the screen lock information becomes very likely for the user. To do this, the user’s system searches for the following running processes.
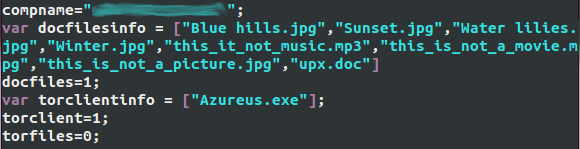
In addition, Nymaim searches for files with the following extensions: .doc, .xls, .psd, .bmp, .jpg, .mpg, .mov, .rtf, .fla, and .mp3. The collected information will be stored in the compdata.js file, which will later be included in the HTML blocking code. An example of such a file is shown below.
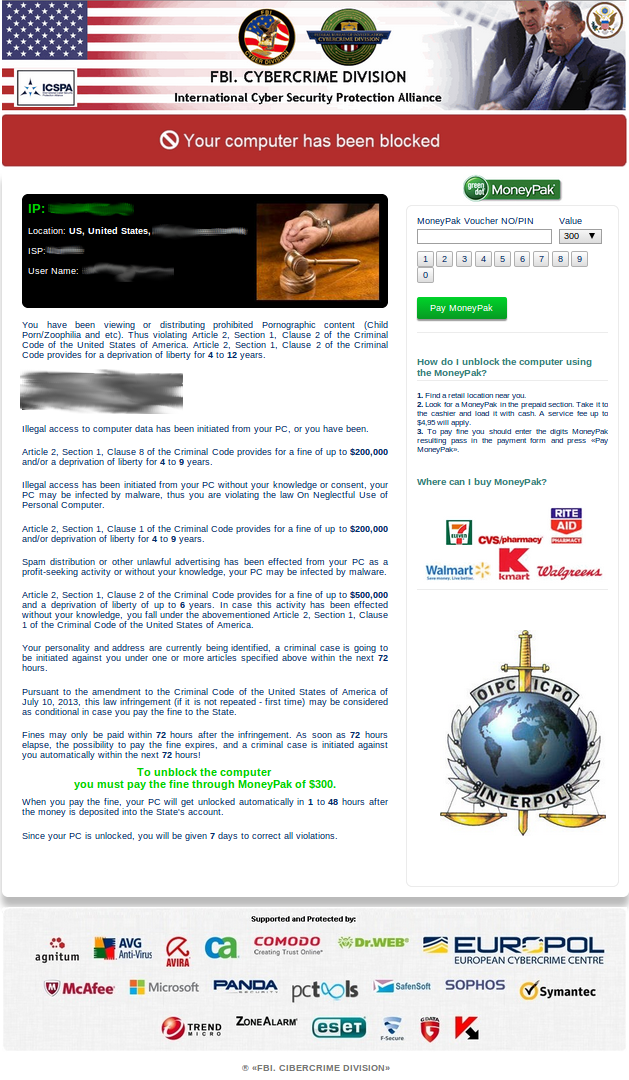
Supporting files that are used for blocking, namely, HTML code, scripts, and screen image files are stored in the Documents and Settings \ [user_name] \ Local Settings \ Temp directory (Windows XP). To lock the system, the extortionist creates a window sized to full screen and spawns two special streams. One of which will monitor the running processes and terminate the standard process manager taskmgr.exe in case of its launch. The second thread tracks the emergence of new desktops that could block the active “malicious” and switches back if they appear. This behavior is similar to the behavior of the extortioner Urausy, which was described by analysts AVAST. The following shows the appearance of the cover for users located in the United States.
The extortioner interacts with the remote server by sending him a bot ID. The server can send back some instructions for performing auxiliary operations. Bot ID is generated based on the value of HKEY_LOCAL_MACHINE \ Software \ Microsoft \ Cryptography \ MachineGuid . The server may not send the blocking page to the bot if the bot with the same ID is already in the server database.
Conclusion
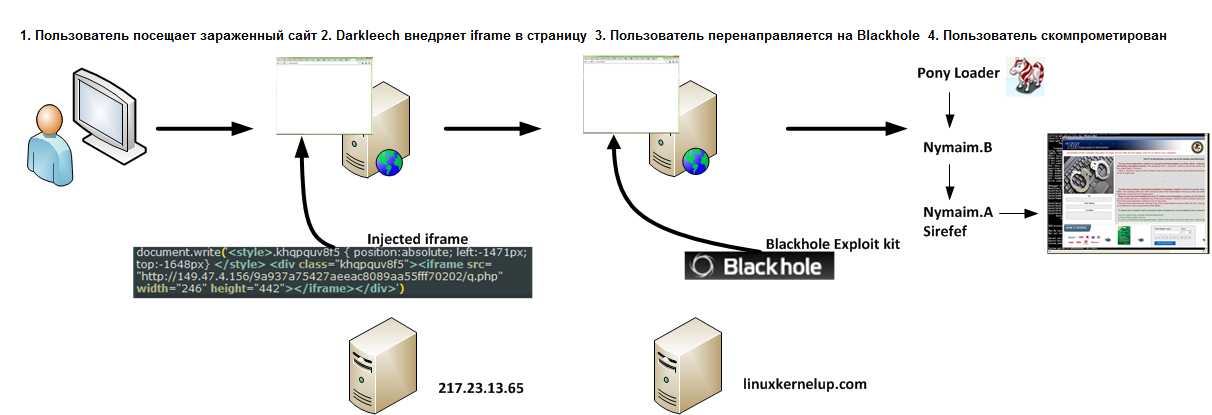
The home campaign monitored by us has been delivering the Win32 / Nymaim extortionist since March 2013. As we pointed out in our study, attackers use other families of malicious code to compromise users. Below is a diagram showing the stages of compromising the user's system in such a campaign.


Infection
')
The method by which users infect Nymaim is shown below. As we mentioned earlier, it consists in a user visiting a compromised web server through which a web page with malicious code is delivered. In the case of Nymaim, the result of visiting such a resource becomes a blocked user's computer. To download the main Nymaim code, the well-known “ Pony Loader ” downloader is used (found by ESET as Win32 / Fareit ).

To maintain the visible legitimacy of its executable file, Fareit is provided with digital signature information.

Such an attribute of samples Fareit gave us the opportunity to group the necessary samples for analysis. Analyzing them, we found out that the catch-cdn.com domain was used by this malicious code to extract Nymaim droppers, which was then installed on compromised computers. We observed the download of a file with the same name 6.exe, which at different times was Win32 / Sirefef (aka ZeroAccess), Win32 / Urausy (Win32 / LockScreen) and Win32 / Nymaim droppers. The following figure shows the timeline for the distribution of malware that was downloaded to this static URL.

The algorithm used to change these families of malicious programs on the server is not entirely clear to us. We noted that the Urausy samples were available for download the first half of July. Sirefef appeared at the beginning of August, and Nymaim appeared regularly throughout the entire time interval.
Specifications
The process of infection Win32 / Nymaim can be divided into two stages. At the first stage, the downloader tries to download the main body of Nymaim by accessing the list of hard-wired IP addresses. After the download is complete, this code renames its file to an arbitrary name. At each of these stages, the extortionist uses several common methods to prevent his analysis.
One of these methods is obfuscation of the code execution flow (control flow obfuscation). Malicious code manually modifies the call stack to transfer control to the desired function, thus hiding the true transitions between functions during static analysis.

In the screenshot above, two obfuscation methods are highlighted. The first is to call a function that modifies the value on the stack of the parent function depending on the parameter passed. In more detail, this method is presented below.

Depending on the argument passed to the function (0x34, 0x35, 0x36), the contents on the stack are modified by one of the registers, which is equivalent to a simple push reg command. For example, in the case of the argument 0x34, we get push ecx.
The second method of obfuscation is used in the function below and is intended to hide the true addresses of the called functions. Below you can see that the argument passed to the function will be used as an offset when calling another function, that is, it is used as a constant to calculate the required address.

As can be seen from this code, the function uses two constants, passed to it as arguments, to calculate the required bias using XOR and ADD operations. Next, the result of this operation is saved on the stack, and the value of the address used by the retn function to transfer control to the calling function is modified. This will invoke the new function.

Another type of obfuscation used in Nymaim refers to calling the Win32 API functions. When the malicious code needs to call the desired function from the DLL, it reads the base address of this DLL from the encrypted data section. The address of the functions is calculated by pre-prepared hashes of the names of these functions. Below is the function code that computes the hash of the function name. It is then used for comparison.

When the address of the function is found, it is stored in memory and then used in various places in the code using a jump instruction. Another feature is the fact that when returning from the API, the execution flow goes not to the malicious code, but to the instruction in the ntdll.dll call EBX. Immediately before calling the API, Nymaim modifies the stack so that after exiting the API, the thread of execution switches to ntdll.dll, and EBX, in turn, will contain the actual return address. More clearly, this process is shown below.

Such manipulations allow Nymaim to make debugging difficult, especially when stepping through (tracing). The stack-correctable return address prevents the function from executing in the debugger “before returning from the function”.
Nymaim uses string encryption. The decryption function is as shown below.

At the second stage of its execution, Win32 / Nymaim uses similar methods of obfuscation, but the code functionality has been extended to ensure survival after a reboot and block the screen. Malicious code uses the usual autorun practice of writing itself to Software \ Microsoft \ Windows NT \ CurrentVersion \ Winlogon \ shell.
Our analysis showed that in some situations, Win32 / Nymaim at the second stage of its execution installs another threat on a compromised computer, namely Win32 / Sirefef. In addition, in the future, Nymaim can download to the computer and other Trojan programs.
The main task of Nymaim is to block the computer. To do this, download the HTML page with information about blocking. This flexibility allows attackers to display various user-intimidating pages, for example, depending on its location or software installed on it (for example, any media files or torrent client). As a result, the screen lock information becomes very likely for the user. To do this, the user’s system searches for the following running processes.
- Azureus
- Utorrent
- Mediaget
- Bittorrent
- Bitcomet
In addition, Nymaim searches for files with the following extensions: .doc, .xls, .psd, .bmp, .jpg, .mpg, .mov, .rtf, .fla, and .mp3. The collected information will be stored in the compdata.js file, which will later be included in the HTML blocking code. An example of such a file is shown below.

Supporting files that are used for blocking, namely, HTML code, scripts, and screen image files are stored in the Documents and Settings \ [user_name] \ Local Settings \ Temp directory (Windows XP). To lock the system, the extortionist creates a window sized to full screen and spawns two special streams. One of which will monitor the running processes and terminate the standard process manager taskmgr.exe in case of its launch. The second thread tracks the emergence of new desktops that could block the active “malicious” and switches back if they appear. This behavior is similar to the behavior of the extortioner Urausy, which was described by analysts AVAST. The following shows the appearance of the cover for users located in the United States.

The extortioner interacts with the remote server by sending him a bot ID. The server can send back some instructions for performing auxiliary operations. Bot ID is generated based on the value of HKEY_LOCAL_MACHINE \ Software \ Microsoft \ Cryptography \ MachineGuid . The server may not send the blocking page to the bot if the bot with the same ID is already in the server database.
Conclusion
The home campaign monitored by us has been delivering the Win32 / Nymaim extortionist since March 2013. As we pointed out in our study, attackers use other families of malicious code to compromise users. Below is a diagram showing the stages of compromising the user's system in such a campaign.

Source: https://habr.com/ru/post/191560/
All Articles