Find and neutralize. How to reveal the location of a mobile subscriber
In mobile networks it is possible to implement quite specific attacks. One of them - the disclosure of the location of the subscriber in real time up to the definition of the cell - will be discussed in this article. I do not indicate accuracy in more familiar units, since the size of a cell is not a constant value. In dense urban buildings, a cell can provide coverage of the order of hundreds of meters, and in the conditions of forests, fields and rivers of an intercity route - several kilometers.

')
Figure 1 (click to open in full size)
To begin with, I will conduct a small introduction to the structure of the cellular network using the example of the GSM standard. A simplified scheme of the standard is shown in Figure 1.
Coverage is provided by base stations (Base Station, BS), each of which, as a rule, has several antennas directed in different directions. The antenna provides cell radio coverage, each cell has its own identifier (Cell Identity, CI). Base stations are grouped into geographic areas (Location Area, LA). Grouping occurs most often on a territorial basis. The ID of such a group is called LAC (Location Area Code). In Figure 1, each base station provides coverage for three sectors.
Base stations are connected to a base station controller (Base Station Controller, BSC). In its simplest form, one LAC corresponds to one BSC. This is precisely the purpose of the LAC shown in the example (Figure 1). For clarity, LAC highlighted in different colors.
The territory covered by one LAC depends on the population density. In Moscow, within the Moscow Ring Road, there may be several dozens of LACs, and in a small region of central Russia, the division into LACs may be as follows: one LAC covers the regional center, the second LAC covers the rest of the territory of the region.
All BSC controllers are connected to the switch (Mobile Switching Center, MSC). In essence, the MSC is a conventional voice telephone call switch with a hardware and software extension to provide subscriber mobility features. In the era of widespread IP, it should be recalled that MSC operates with circuit switching (Circuit Switched) according to the static routing tables established in it based on the usual telephone numbering.
The Visitor Location Register (VLR) is a functionally considered a separate network element, but in fact is always integrated with the MSC. The VLR database contains information about subscribers who are currently within range of their MSC. And since the topic of the subscriber's location is the topic, it is worth mentioning that for each subscriber the VLR database stores information about the current LAC identifier and the identifier of the cell (CI) that was the last radio contact of the mobile phone with the network. That is, if a subscriber moves within the coverage area of one LAC without making or receiving calls, its location information in the VLR database does not change. In general, there may be several MSC / VLR nodes on a network. The example in Figure 1 shows two such nodes.
Two more functional nodes, the Home Location Register (HLR) and the Authentication Center (AuC), are located physically in a single module. HLR / AuC stores subscriber profiles of its network. The profile contains the following information: subscriber phone number, unique identifier of the SIM card (International Mobile Subscriber Identity, IMSI), keys for security, subscriber category (prepaid settlement system / postpaid settlement system), list of allowed and prohibited services, billing address center (for prepaid subscribers), the address of the MSC / VLR in which the subscriber is currently located. The same profile with some changes is copied to the VLR when the subscriber is registered in its area of operation.
Gateway switch (Gateway MSC, GMSC) is the receiving point for incoming calls. Based on information received from the HLR, it routes the call to the switch that the called subscriber is in range of.
In the process of establishing a call, sending SMS and other transactions, communication centers exchange signal messages with each other. The stack of protocols, a set of messages and their parameters in telephone networks (not only mobile) communication is called the Signaling System No. 7 (Signaling System 7, SS7). All SS7 protocols are open and available for review and study on the websites of international organizations such as ITU-T, 3GPP, GSMA. The attack described below relies on SS7 messages.
Of course, this attack will not be able to make any person from the street. To attack, stars must be placed in the correct order in the sky. Namely:
In order that the description of the attack is not bogged down under the boring definitions and terms, we will adhere to the following legend. A couple of our employees went on a business trip to Kiev: there they are scheduled to negotiate with potential customers. Judging by the time, the colleagues should already return with the result, but they report that there are difficulties in the negotiation process and they will have to stay. Now we will be looking for one of our colleagues and suggest that you track the entire process using the arrows in Figure 2.

Figure 2 (click to open in full size)
1. A mobile phone is registered in the network of one of the Ukrainian mobile operators. At some point, the subscriber enters the LAC 41800 coverage area from the side of the CI 22C0 sector and continues to move up to the CI 22CF sector. What happens at this time in the network operator? When the phone is in the coverage area of the LAC 41800, the Location Update procedure is initiated, updating the LAC and CI values in the VLR database. As our colleague moves to the CI 22CF sector, no more changes occur in the VLR database.
2. We want to find out if our employees are really having difficult negotiations. And at some point we form an SMS with the Type-0 attribute and send it to the number of one of our colleagues. I remind you that according to legend, he is at this time in the sector CI 22CF.
3. SMS Type-0 has another name - SMS-ping. This message is not displayed on the mobile phone screen and is not saved in the list of received SMS. In addition, it performs actions that the subscriber did not plan, namely, updates location attributes in the VLR database. The current value of the sector in which the subscriber arrives, that is, the CI 22CF, is now stored in the VLR.
4. We have already begun our activity, but have not yet received a single byte of the result. Information about the location of the subscriber, though updated, but it is in the depths of the operator’s equipment, and in order to extract the data, we continue our research. In the next step, we form the sendRoutingInfoForSM signaling message, where our employee’s mobile number is specified as a parameter, and send this message to the operator's HLR.
5. In the world of telecoms, it is customary to trust each other, especially requests that come through SS7 networks, and the operator's HLR is not an exception to this rule. Figure 3 shows an excerpt from tracing. HLR finds in its databases the subscriber IMSI identifier (1) and the address of the MSC / VLR (2), in the area where the subscriber with the specified number is located, and without suspecting a trick, informs his “interlocutor” this data. Here you can pay attention to the values of some numbers. The first three digits of the IMSI identifier indicate the country code of the subscriber (Mobile Country Code, MCC). Code 250 is assigned to Russia (1). The switch address is provided in the more usual telephone numbering, where 380 is the international dialing code of Ukraine (2).
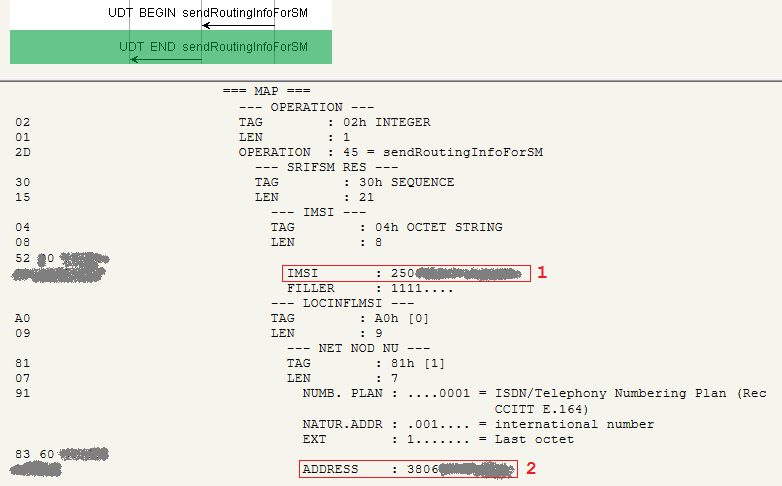
Figure 3
At this step, you can make a short pause. The fact is that there are services in the network that stop there and provide their users with information about the location of any mobile subscriber with the accuracy of a mobile switch.

Figure 4
Figure 4 shows a snippet of a screenshot of the search results from the same person. Here we see the number of the subscriber (1). In addition, the service discloses the IMSI identifier (2), which is generally confidential information and must be kept by the operator with seven seals. Next we are shown the number of the service center where the subscriber is located (3). In fact, this is a shortened address of the mobile switch. In Russia, by the number of the service center, you can determine the region where the subscriber is located, since the addressing of the switches coincides with the regional telephone numbering. Unfortunately, for the Ukrainian mobile operators I could not find such a match.
6. Our search continues. Now we form the message provideSubscriberInfo, where as a parameter we set the identifier IMSI, and send this message to the address of the mobile switch. We obtained all the necessary parameters (IMSI and MSC / VLR address) in the previous step.
7. And again we will play on the general trust. The switch perceives the message as completely legal and gladly responds with the MCC / MNC network identifiers, the LAC value and the recently updated CI sector value.
Now look at the trace (figure 5). All values we need for direction finding are obtained:
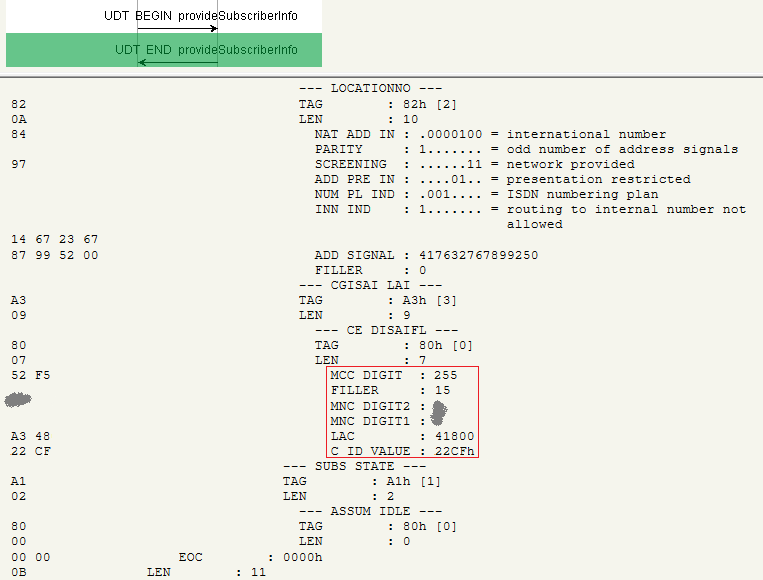
Figure 5
So far this is only a set of numbers from which we can find out the country by the MCC - code 255 is assigned to Ukraine. As long as everything converges. For the final shot, we open the service to determine the coordinates of the base station, of which a lot can be found in the network (Figure 6). And what do we see? This is not Kiev, but Feodosia, and the sector serves not the city limits, but the seashore with beaches! Now it’s clear what our colleagues have been on a business trip for so long :)
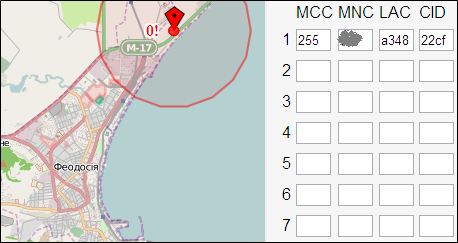
Figure 6
As users of the “service” described in the article, one can imagine criminal elements, industrial spies, private detectives ... But the question remains: who and how can realize such an attack?
First of all, this is a possibility for technical specialists of telecom operators, and the operator himself may be located in any country of the world.
Secondly, for the implementation of the service, a company can be specially created to obtain the necessary licenses, purchase equipment and connect to SS7 with the ability to operate the MAP protocol. Cash costs for the implementation of this option in Russia will be calculated in round sums and are unlikely to be able to pay off.
The third option is hacking the operator’s control network and introducing the bug into its existing infrastructure.
And law enforcement agencies have their own means of operational search activities (SORM), including the location search function.
Author : Sergey Puzankov, Research Center Positive Research.
PS I want to express my gratitude to the department for analyzing the security of the network devices of Positive Technologies and Vera Kraskova, who rested in the Crimea during our research and acted as the subscriber being referred to :)
System elements

')
Figure 1 (click to open in full size)
To begin with, I will conduct a small introduction to the structure of the cellular network using the example of the GSM standard. A simplified scheme of the standard is shown in Figure 1.
Coverage is provided by base stations (Base Station, BS), each of which, as a rule, has several antennas directed in different directions. The antenna provides cell radio coverage, each cell has its own identifier (Cell Identity, CI). Base stations are grouped into geographic areas (Location Area, LA). Grouping occurs most often on a territorial basis. The ID of such a group is called LAC (Location Area Code). In Figure 1, each base station provides coverage for three sectors.
Base stations are connected to a base station controller (Base Station Controller, BSC). In its simplest form, one LAC corresponds to one BSC. This is precisely the purpose of the LAC shown in the example (Figure 1). For clarity, LAC highlighted in different colors.
The territory covered by one LAC depends on the population density. In Moscow, within the Moscow Ring Road, there may be several dozens of LACs, and in a small region of central Russia, the division into LACs may be as follows: one LAC covers the regional center, the second LAC covers the rest of the territory of the region.
All BSC controllers are connected to the switch (Mobile Switching Center, MSC). In essence, the MSC is a conventional voice telephone call switch with a hardware and software extension to provide subscriber mobility features. In the era of widespread IP, it should be recalled that MSC operates with circuit switching (Circuit Switched) according to the static routing tables established in it based on the usual telephone numbering.
The Visitor Location Register (VLR) is a functionally considered a separate network element, but in fact is always integrated with the MSC. The VLR database contains information about subscribers who are currently within range of their MSC. And since the topic of the subscriber's location is the topic, it is worth mentioning that for each subscriber the VLR database stores information about the current LAC identifier and the identifier of the cell (CI) that was the last radio contact of the mobile phone with the network. That is, if a subscriber moves within the coverage area of one LAC without making or receiving calls, its location information in the VLR database does not change. In general, there may be several MSC / VLR nodes on a network. The example in Figure 1 shows two such nodes.
Two more functional nodes, the Home Location Register (HLR) and the Authentication Center (AuC), are located physically in a single module. HLR / AuC stores subscriber profiles of its network. The profile contains the following information: subscriber phone number, unique identifier of the SIM card (International Mobile Subscriber Identity, IMSI), keys for security, subscriber category (prepaid settlement system / postpaid settlement system), list of allowed and prohibited services, billing address center (for prepaid subscribers), the address of the MSC / VLR in which the subscriber is currently located. The same profile with some changes is copied to the VLR when the subscriber is registered in its area of operation.
Gateway switch (Gateway MSC, GMSC) is the receiving point for incoming calls. Based on information received from the HLR, it routes the call to the switch that the called subscriber is in range of.
In the process of establishing a call, sending SMS and other transactions, communication centers exchange signal messages with each other. The stack of protocols, a set of messages and their parameters in telephone networks (not only mobile) communication is called the Signaling System No. 7 (Signaling System 7, SS7). All SS7 protocols are open and available for review and study on the websites of international organizations such as ITU-T, 3GPP, GSMA. The attack described below relies on SS7 messages.
Attack
Of course, this attack will not be able to make any person from the street. To attack, stars must be placed in the correct order in the sky. Namely:
- Must have access to SS7 signaling network.
- It is possible to generate any SS7 signaling messages (the attack will require the MAP protocol).
- There are no means of filtering incorrect or suspicious SS7 messages on the victim's network (about 90% of operators around the world do not think about such filtering).
In order that the description of the attack is not bogged down under the boring definitions and terms, we will adhere to the following legend. A couple of our employees went on a business trip to Kiev: there they are scheduled to negotiate with potential customers. Judging by the time, the colleagues should already return with the result, but they report that there are difficulties in the negotiation process and they will have to stay. Now we will be looking for one of our colleagues and suggest that you track the entire process using the arrows in Figure 2.

Figure 2 (click to open in full size)
1. A mobile phone is registered in the network of one of the Ukrainian mobile operators. At some point, the subscriber enters the LAC 41800 coverage area from the side of the CI 22C0 sector and continues to move up to the CI 22CF sector. What happens at this time in the network operator? When the phone is in the coverage area of the LAC 41800, the Location Update procedure is initiated, updating the LAC and CI values in the VLR database. As our colleague moves to the CI 22CF sector, no more changes occur in the VLR database.
2. We want to find out if our employees are really having difficult negotiations. And at some point we form an SMS with the Type-0 attribute and send it to the number of one of our colleagues. I remind you that according to legend, he is at this time in the sector CI 22CF.
3. SMS Type-0 has another name - SMS-ping. This message is not displayed on the mobile phone screen and is not saved in the list of received SMS. In addition, it performs actions that the subscriber did not plan, namely, updates location attributes in the VLR database. The current value of the sector in which the subscriber arrives, that is, the CI 22CF, is now stored in the VLR.
4. We have already begun our activity, but have not yet received a single byte of the result. Information about the location of the subscriber, though updated, but it is in the depths of the operator’s equipment, and in order to extract the data, we continue our research. In the next step, we form the sendRoutingInfoForSM signaling message, where our employee’s mobile number is specified as a parameter, and send this message to the operator's HLR.
5. In the world of telecoms, it is customary to trust each other, especially requests that come through SS7 networks, and the operator's HLR is not an exception to this rule. Figure 3 shows an excerpt from tracing. HLR finds in its databases the subscriber IMSI identifier (1) and the address of the MSC / VLR (2), in the area where the subscriber with the specified number is located, and without suspecting a trick, informs his “interlocutor” this data. Here you can pay attention to the values of some numbers. The first three digits of the IMSI identifier indicate the country code of the subscriber (Mobile Country Code, MCC). Code 250 is assigned to Russia (1). The switch address is provided in the more usual telephone numbering, where 380 is the international dialing code of Ukraine (2).

Figure 3
At this step, you can make a short pause. The fact is that there are services in the network that stop there and provide their users with information about the location of any mobile subscriber with the accuracy of a mobile switch.

Figure 4
Figure 4 shows a snippet of a screenshot of the search results from the same person. Here we see the number of the subscriber (1). In addition, the service discloses the IMSI identifier (2), which is generally confidential information and must be kept by the operator with seven seals. Next we are shown the number of the service center where the subscriber is located (3). In fact, this is a shortened address of the mobile switch. In Russia, by the number of the service center, you can determine the region where the subscriber is located, since the addressing of the switches coincides with the regional telephone numbering. Unfortunately, for the Ukrainian mobile operators I could not find such a match.
6. Our search continues. Now we form the message provideSubscriberInfo, where as a parameter we set the identifier IMSI, and send this message to the address of the mobile switch. We obtained all the necessary parameters (IMSI and MSC / VLR address) in the previous step.
7. And again we will play on the general trust. The switch perceives the message as completely legal and gladly responds with the MCC / MNC network identifiers, the LAC value and the recently updated CI sector value.
Now look at the trace (figure 5). All values we need for direction finding are obtained:
- MCC - country code;
- MNC (Mobile Network Code) - mobile operator code;
- LAC (for further use you need to bring this value in hexadecimal form: 41800 = A348h);
- CGI (Cell Global Identity) - cell code, the value is immediately shown in hexadecimal.

Figure 5
So far this is only a set of numbers from which we can find out the country by the MCC - code 255 is assigned to Ukraine. As long as everything converges. For the final shot, we open the service to determine the coordinates of the base station, of which a lot can be found in the network (Figure 6). And what do we see? This is not Kiev, but Feodosia, and the sector serves not the city limits, but the seashore with beaches! Now it’s clear what our colleagues have been on a business trip for so long :)

Figure 6
Conclusion
As users of the “service” described in the article, one can imagine criminal elements, industrial spies, private detectives ... But the question remains: who and how can realize such an attack?
First of all, this is a possibility for technical specialists of telecom operators, and the operator himself may be located in any country of the world.
Secondly, for the implementation of the service, a company can be specially created to obtain the necessary licenses, purchase equipment and connect to SS7 with the ability to operate the MAP protocol. Cash costs for the implementation of this option in Russia will be calculated in round sums and are unlikely to be able to pay off.
The third option is hacking the operator’s control network and introducing the bug into its existing infrastructure.
And law enforcement agencies have their own means of operational search activities (SORM), including the location search function.
Author : Sergey Puzankov, Research Center Positive Research.
PS I want to express my gratitude to the department for analyzing the security of the network devices of Positive Technologies and Vera Kraskova, who rested in the Crimea during our research and acted as the subscriber being referred to :)
Source: https://habr.com/ru/post/191384/
All Articles