Methods of anonymity online. Part 1. Just about the difficult

"They are naive, like small children,
Those who believe in anonymity on the Internet. "
M. Sandomirsky
Hi, habrayuzer!
This article made me write various “reviews” of anonymity schemes that have recently appeared on the Internet. Here I, simplifying many technical points, will talk about various methods and ways to ensure anonymity on the web. If the topic finds a response, in the next articles in the series I will move on to more interesting technical details.
To make it easier, we divide the anonymity in the Internet into two directions:
- “Social anonymity” is what a person himself consciously or unconsciously talks about himself on the Web.
- “Technical anonymity” - when the leak of de-anonymizing data is associated with the used hardware and applications.
We will focus on technical anonymity.
All parts here:
Part 1: Methods of anonymity online. Just about the complicated .
Part 2: Methods of anonymity online. Data leaks .
Part 3: Methods of anonymity online. Firefox .
Part 4: Methods of anonymity online. Tor & VPN. Whonix .
Proxy servers
Globally, when they say a proxy server, they mean something that acts as an intermediary between the client and the addressee.
In terms of ensuring anonymity, proxy servers are:
- HTTP (web) proxy servers. Such servers pass only HTTP traffic through themselves, by default adding data on the use of proxies to the transmitted traffic;
- SOCKS proxy servers. Unlike HTTP proxy servers, SOCKS transmits all the information without adding anything from itself. The SOCKS protocol is at the session level of the OSI model, this achieves independence from high-level protocols: HTTP, FTP, PORZ, etc., which allows SOCKS to pass all traffic through itself, not just HTTP;
- Separately, it is worth mentioning CGI-proxy or “anonymizers”, which are essentially a web-server with a form, where the client enters the address of the desired site. Then the page of the requested resource opens, but the address of the CGI proxy is visible in the address bar of the browser. A CGI proxy, like any web server, can use https to protect the communication channel between itself and the client.
The scheme of the proxy servers you see in the picture, everything is simple:

')
Proxy Pros Benefits:
- proxies are cheap, you can find many free proxies on the net.
Cons of proxy servers:
- need to trust the proxy server;
- for http-proxy, HTTP-headers must be filtered: “HTTP_X_FORWARDED_FOR: client, ip1 ...”, HTTP_VIA, HTTP_FORWARDED, etc .;
- Proxy protocols (http, SOCKSx) do NOT support encryption between the HTTP / SOCKS / Elite / Anonymous proxy and the client. And SSL-proxy means only that the client can work with https-resources;
- proxy chains are ineffective: " Hello Proxy1, send my message:" forward to Proxy3; forward to Proxy4; forward to encrypted.google.com/c8e8df895c2cae- something else-more- encrypted -166baf 'for Proxy2? "Thank you !;
- the need to set up a proxy server for each application or use separate soksifikatorov programs, such as Proxifier.
VPN / SSH
I will talk about VPN, meaning also SSH tunnels. Since, despite some differences, their basic principle is the same.
The scheme of the VPN is shown in the picture:

Currently, commercial providers offer the following VPN protocols:
- PPTP - used most widely, fast, easy to configure, but is considered the “least protected” compared to the others;
- L2TP + IPSec. L2TP provides transport, and IPSec is responsible for encryption. This bundle has stronger encryption than PPTP, is resistant to PPTP vulnerabilities, also provides message integrity and party authentication;
- OpenVPN - safe, open, and therefore, common, allows you to bypass many locks, but requires a separate software client;
- SSTP is as secure as OpenVPN, it does not require a separate client, but is very limited in platforms: Vista SP1, Win7, Win8.
Virtually all commercial VPN providers offer a choice of two protocols: OpenVPN and PPTP. Less commonly, the proposed protocol L2TP + IPSec. And quite a few offer the protocol SSTP.
We should also mention the services that provide “DoubleVPN” when, before you access the Internet, traffic passes 2 different VPN servers in different countries, or even “QuadVPN”, when 4 servers are used, which the user can select himself and place in an arbitrary okay
An interesting study on the anonymity and reliability of commercial VPN servers was conducted by torrentfreak.com: torrentfreak.com/vpn-services-that-take-your-anonymity-seriously-2013-edition-130302
VPN providers were asked questions:
- Do you keep journals that allow you or third parties to match the ip-address or time stamp with your client? If so, what data do you store?
- Under what jurisdiction does your company work, and under what circumstances will you disclose the data to a third party?
- In case you receive a DMCA notification or its European equivalent, what will you do with it?
- What payment systems do you work with and how are they related to user accounts?
Summarizing, it is worth noting that the majority of VPN providers are unanimous in their answers: “Logs are not stored, and if they are stored, they are not very long, it is impossible to calculate the subscriber from them. It is very difficult for us to press and force us to give at least something. ” Of course, there are no other responses from services whose main purpose is to ensure the anonymity of users.
VPN / SSH Pros:
- quick and convenient, no need to separately configure applications.
Disadvantages of VPN / SSH:
- need to trust the VPN / SSH server / provider.
I note that most of the thematic add-ons for browsers and “programs for anonymity” are basically used by proxy servers and VPN servers to hide the ip-address of the client.
Tor. Great and terrible
A lot has already been said about Tor, but I will try to tell just :)
Tor is a router system in which a client connects to the Internet through a chain of nodes. As a rule, the chain consists of three nodes, each of them is unknown address of the client and the resource at the same time. In addition, Tor encrypts messages separately for each node, and open traffic is visible only to the output router.
Now Tor is 10 authoritative (control) nodes, about 4,200 intermediary nodes, including approximately 900 output nodes.
The picture is a simplified scheme of work

I note that the traffic goes back in clear form, at the output node it is encrypted with a temporary symmetric key and transmitted over the chain (yes, the traffic itself is encrypted on symmetric keys, and these keys are already encrypted on asymmetric keys).
They are angry because they demand too much: it is safe to transfer traffic from any application to the network, protection from a global observer, confidentiality of transmitted data, etc. But it solves the main problem with its threat model: a rather high level of client anonymity when sending only http- traffic subject to all mandatory rules: www.torproject.org/download/download-easy.html.en
Pros of Tor :
- high degree of anonymity of the client while observing all the rules;
- ease of use (downloaded Tor Browser Bundle, launched and enjoyed).
Cons Tor:
- output traffic is tapped;
- low speed;
- availability of management servers.
I found a poll on Tor in one of the forums. The number of respondents does not indicate the reliability of the results, but the winning answer is very correct :)

Tor's work is invariably accompanied by people's doubts about its reliability and anonymity. Now we will not analyze it in detail, I promise to do it in the next articles of the cycle, where I will describe in detail some important details of Tor and try to answer all the questions.
I2p
Many words have been said about I2P, I will be laconic and I will try to explain everything clearly.
I2P is an anonymous network running on top of the Internet. It has its own sites, forums and other services. By its architecture, it is completely decentralized, and Ip addresses are nowhere used in ip-addresses.
I2P has two main concepts:
- A “tunnel” is a temporary unidirectional path through a list of nodes. Tunnels are incoming and outgoing;
- “NetDb network base”, which is distributed to one degree or another across all I2P clients. Its purpose is to store information about how a client can connect to a specific recipient.
NetDb database stores:
- RouterInfos - contact data of routers (clients), used to build tunnels (simplifying, they are the cryptographic identifiers of each node);
- LeaseSets - contact details of recipients, used to connect outgoing and incoming tunnels.
At the beginning of 2013, I2P included 25,000 routers and 3,000 LeaseSets.
I'll tell you about the algorithm of interaction of nodes:
Step one. The Kate node builds outgoing tunnels. It accesses NetDb for data about routers and builds a tunnel with their participation.

Step two. Boris builds an entrance tunnel in the same way as an outgoing tunnel is built. It then publishes its coordinates or the so-called “LeaseSet” to NetDb (here note that the LeaseSet is transmitted through the outgoing tunnel).
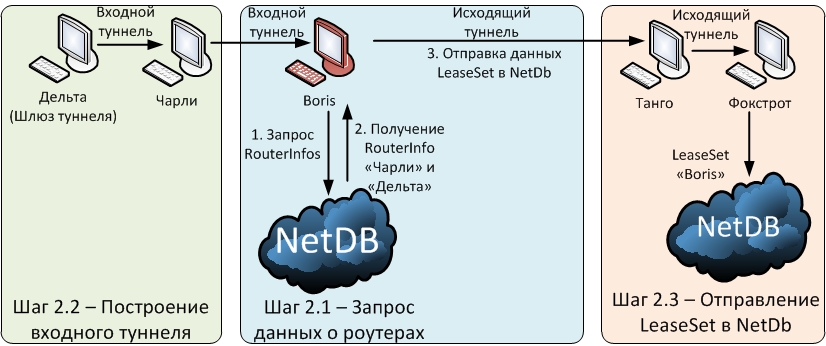
Step three. When Kate wants to send a message to Boris, she asks Boris for NetDb LeaseSet. And outgoing tunnels forwards the message to the destination gateway.

I2P has the ability to access the Internet through special Outproxy, but they are unofficial and, by a combination of factors, even worse than the output nodes of Tor. I2P developers say: " If you want the Internet, use Tor ."
Pros I2P:
- high degree of anonymity of the client;
- complete decentralization, leading to network stability;
- data confidentiality: end-to-end encryption between the client and the addressee.
Cons I2P:
- low speed;
- "Your Internet".
Details on I2P, including protection mechanisms, and with them I2P is fine, I will also tell in the next articles of the cycle.
Other means
In fact, there were dozens of separate projects dedicated to anonymity on the Internet, not counting “browser add-ons” and “anonymity programs”. Other, less popular, solutions are simply either compromised, or are not yet so popular, and, therefore, have not been studied by the world expert community to talk about their sufficient reliability. Now the most promising projects are actively developing:
- Freenet freenetproject.org
- GNUnet gnunet.org
- JAP (He is John Donym, based on Tor) anon.inf.tu-dresden.de/index_en.html
- RetroShare retroshare.sourceforge.net
- Perfect Dark www21.atwiki.jp/botubotubotubotu
A separate interesting example of anonymous networks are networks based on Wi-Fi. While in the traditional approach, the transport functions of any anonymous network are performed by the Internet, the use of wireless solutions allows achieving independence from Internet providers:
- Byzantium project: project-byzantium.org
- Netsukuku project - Networked Electronic Technician Skilled in Ultimate Killing, Utility and Kamikaze Uplinking: netsukuku.freaknet.org
- BATMAN project - Better Approach To Mobile Ad-hoc Networking: www.open-mesh.org/projects/open-mesh/wiki
Conclusion
In conclusion, I will quote from the main page of the I2P project: “ Anonymity has no unambiguous threshold, after which you can relax - we are not trying to create something“ completely anonymous ”, but we are working to make attacks on such a network more and more“ expensive ” for intruders . "
Indeed, the technical part is only a small component of anonymity on the Internet. It is important to understand that the reliability of each such scheme rests on the means: material resources and time that can be spent on its compromise.
Ps. If in the comments I see the desire of people, then in the following article we will talk about:
1. Tom, how, from a technical point of view, Tor, I2P and the difference between SOCKS 4, 4a, 5 in terms of anonymity work.
2. Pros and cons of combining Tor and VPN and about other, less popular, and even exotic anonymity schemes.
3. Specific leakage of deanonimizing data.
Also ask questions, make comments, I will be happy to answer them. Thank!
Source: https://habr.com/ru/post/190396/
All Articles