Who is guarding the watchmen?
IViZ Security, a specialist in penetration testing, published its latest report, “ (In) Security in Security Products 2013, ” in which it noted a rapid increase in the number of vulnerabilities in security solutions. In 2012, amid an approximately 20% increase in the total number of vulnerabilities, the number of vulnerabilities in security products increased almost 3 times!
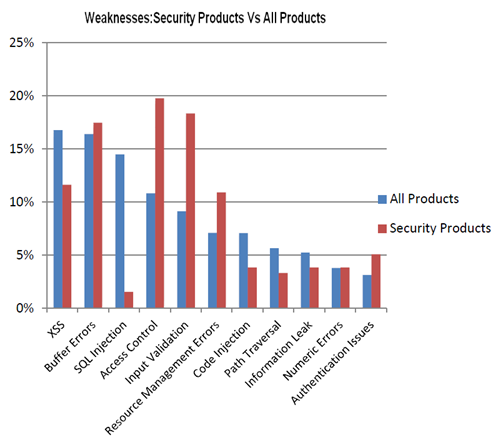
And what is most regrettable: compared with the total amount of errors of various types, the number of vulnerabilities in security products related to access control, resource management and authentication is incomparably higher. Given that similar errors in security products, in my opinion, are not permissible at all.
What do experts of iViZ Security recommend to do in these conditions?
The recipe is simple and complex at the same time:
- require the manufacturer not only to certify products, but also to test for vulnerabilities;
- conduct your own penetration tests for security solutions.
Can customers follow these guidelines? Theoretically, yes, but in practice it turns out that only mega-customers can require a vendor and something from him to demand, and no one will be able to spend extra money on testing the safety of products designed for security.
Can manufacturers provide higher quality products? Of course they can. There is a whole field of knowledge that helps to achieve this result and is dedicated to the development of secure (i.e., error-free and vulnerability-free) software. The best known practices in this area are:
- Microsoft Security Development Lifecycle;
- NIST Security Considerations in the System Development Life Cycle;
- Cisco Security Development Lifecycle;
- Software Assurance Maturity Model et al
Of course, following these recommendations makes development more expensive, but reducing the number of errors and vulnerabilities is guaranteed to reduce the number of complaints from users, which should compensate for the costs.
In particular, the Security Code has implemented a development process based on a combination of Microsoft and Cisco secure development lifecycles. All of its stages are documented in the framework of a certified quality management system and include, inter alia, advanced testing techniques, search for vulnerabilities and attack modeling, which allows us to put on the market high-quality and secure information protection tools.
In addition, due to the fact that the FSTEC of Russia in its recent documents on the protection of personal data recommended the use of software developed using methods of protected programming, we plan to post a description of our development process on the site soon.
Stepanenko Andrei, director of marketing for Security Code
')
Source: https://habr.com/ru/post/189048/
All Articles