Search for bugs with Google or “hacking” accounts on badoo.com
I want to tell you how Badoo protects the accounts of its customers. This article is written solely for educational purposes. I do not push anyone to commit illegal actions and do not pursue any malicious intent.
In March 2013, Badoo announced the contest “Test Badoo for Strength!”.
The competition attracted prizes and I, satisfied with the success in finding vulnerabilities for Yandex, registered on the site, looked at the links that came in the letters, and just drove them into the Google search box.
First, I found links that allow you to register under someone else’s email address without confirmation, received a letter in reply
To search for links, you can use Google Dorks , all possible query options are collected and sorted on the site.
Then I discovered a few more “little things”, the answer was the same.
My last find was a lot of links where you can log in to badoo.com, get full access to a user account, without having any hacking skills. There are user accounts from different countries to choose from, just follow the link and you are authorized. In addition, the links can go more than once.
')
We drive in Google, for example, site: https: //eu1.badoo.com/access.phtml
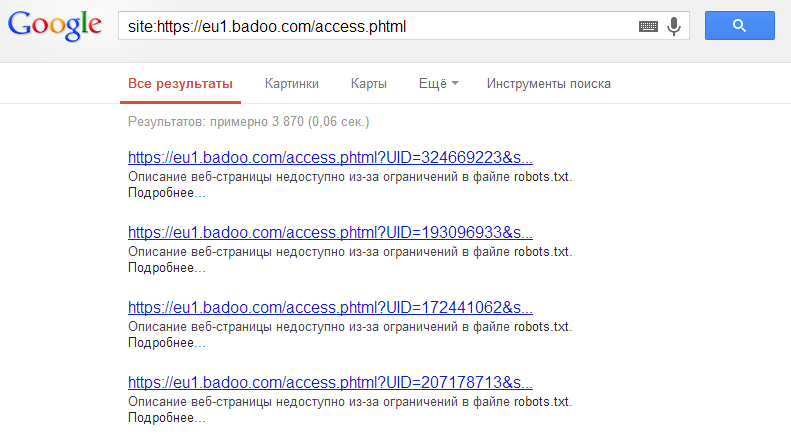
Follow the links and get into user profiles:

In this case, the answer I received only on the third letter:
I tried to explain the danger of logging in with someone else’s account, and asked if I could write an article on Habrahabr, which I received in response:
It has been more than four months since my correspondence with Badoo, Google is still possible to find authorization links that are not one-time.
Another interesting query: inurl: register.phtml site: badoo.com
This query finds links of the form:
eu1.badoo.com/invite/register.phtml? u
This is the invitation of the user to the site, in this link you can send as a UIN parameter any email not previously registered on the site, and you will not need a confirmation request for registration. The only inconvenience is that after clicking on the link from Google and replacing the email, you need to clear the browser cookie.
Example of registration uin = Any% 20email , there is no validation check:
I decided to write this article, because Badoo does not consider the possibility of authorization under another account a vulnerability.
PS Look for bugs with Google: inurl: phtml site: badoo.com
PPS After answering Badoo in the comments, on request inurl: forgot_enter site: badoo.com managed to get access to the actively used account ( video-proof , the file can be opened in any browser).

Not all Bug Bounty programs are equally useful.
In March 2013, Badoo announced the contest “Test Badoo for Strength!”.
The competition attracted prizes and I, satisfied with the success in finding vulnerabilities for Yandex, registered on the site, looked at the links that came in the letters, and just drove them into the Google search box.
First, I found links that allow you to register under someone else’s email address without confirmation, received a letter in reply
“Thank you, but this is not a vulnerability. Please keep checking our strength. ”
Google Dorks Requests, Bug Search
To search for links, you can use Google Dorks , all possible query options are collected and sorted on the site.
Then I discovered a few more “little things”, the answer was the same.
My last find was a lot of links where you can log in to badoo.com, get full access to a user account, without having any hacking skills. There are user accounts from different countries to choose from, just follow the link and you are authorized. In addition, the links can go more than once.
')
We drive in Google, for example, site: https: //eu1.badoo.com/access.phtml

Follow the links and get into user profiles:

Correspondence with badoo
In this case, the answer I received only on the third letter:
“This is not a vulnerability, this is a mistake and we will definitely fix it.
You have sent us several requests regarding pages indexed by Google, all of these applications have been answered to you that this is not a vulnerability.
The fact is that for legal users such links do no harm - if the email already exists in the system, then the new user will not be able to register with the same email.
As for the links to change the password, they are all invalid - when you switch to them, we say that “the link has ceased to be valid”.
So we will remove the excess from the issue of Google, but not immediately - indexing is not done at the moment.
If you still find links that act and can harm users - please send detailed instructions on how this can harm other users, then we consider this a vulnerability. ”
I tried to explain the danger of logging in with someone else’s account, and asked if I could write an article on Habrahabr, which I received in response:
“We once again looked at your application very carefully and decided that this problem is not a Badoo vulnerability.
When a user registers on our site, he himself indicates his email. In some cases, users specify an email, which, for example, automatically openly publishes all received messages. Either the users themselves in some other way openly publish the letters received from Badoo, including authorization links. Then, the published links are found by Google and include them in their issue. If you go to sites like birgo.mynet.com or twitmail.com , you will find a large number of messages from us that users themselves have made publicly available, consciously or by mistake:
birgo.mynet.com/badoo/archive/2011/2
twitmail.com/email/146079226/29/3-people-on-Badoo-are-waiting-to-chat-with-you-
We do not control such user actions and cannot stop them. However, a few weeks ago, we took measures to automatically invalidate the authorization links found by popular search engines. That is why of the huge number of links in the issue of Google, only a very small amount remains active. They were indexed by Google before we took action. As reindexing, all such links will be deactivated.
This decision of the jury on your application is final. "
Customer care
It has been more than four months since my correspondence with Badoo, Google is still possible to find authorization links that are not one-time.
Another interesting query: inurl: register.phtml site: badoo.com
This query finds links of the form:
eu1.badoo.com/invite/register.phtml? u
This is the invitation of the user to the site, in this link you can send as a UIN parameter any email not previously registered on the site, and you will not need a confirmation request for registration. The only inconvenience is that after clicking on the link from Google and replacing the email, you need to clear the browser cookie.
Example of registration uin = Any% 20email , there is no validation check:

I decided to write this article, because Badoo does not consider the possibility of authorization under another account a vulnerability.
PS Look for bugs with Google: inurl: phtml site: badoo.com
PPS After answering Badoo in the comments, on request inurl: forgot_enter site: badoo.com managed to get access to the actively used account ( video-proof , the file can be opened in any browser).
Source: https://habr.com/ru/post/189040/
All Articles