New type of attacks - attacks on cars
Before we proceed to the article itself, I will tell such a case.
My friend bought a new BMW. He loves to drive - drove. When on the odometer was 8000km the official dealer called and said that the pads had been erased - it's time to change.
An article about how a Forbs American journalist and two security specialists from Twitter and IOActive tested the Ford Escape and Toyta Prius (added at the request in the comments). A first-person article from a journalist - Andy Greenberg.
I hit the brakes, and 3,500-pound (1 lb = 0,454kg) Ford Escape, refuses to stop, or even slow down - which causes a unique feeling of anxiety. In this case, when you press the brake pedal, a deep moaning sound is made, like an angry roar of buffaloes somewhere under the SUV chassis. The more I press the pedal, the louder the moan echoes the admiring cackling of the two hackers sitting behind me in the backseat.
')
Fortunately, this all happens at less than 5 miles per hour (1 mile = 1.609 km). So the Ford Escape just strives into a 6-foot-tall weed wall growing in the abandoned car park of South Bend, an Indiana shopping center that Charlie Miller and Chris Valasek selected as a test site for this day's experiments, some of which are shown in the video above. (When Miller discovered a destructive brake, he wasn’t so lucky: his mother rushed through his garage, destroying his lawnmower and damaging the back wall for $ 150).
“Well, now your brakes are working again,” says Miller, clicking on the keys on a battered MacBook, connected by cable to an inconspicuous data port near the parking brake. I completely leave the weeds and carefully stop the car. “When you lose faith in what a car does, what you tell it to do,” he adds after we jump out of the SUV, “it really changes your point of view on how the car works”
The fact that the car is not a simple machine made of glass and steel, but a hacked network of computers, is what Miller and Valasek spent last year trying to demonstrate. Miller, a 40-year-old safety engineer on Twitter, and Valasek, a 31-year-old director of security intelligence at Seattle IOActive Consulting, received $ 80,000 - plus a grant last fall from a crazy Pentagon research scientist who is known to be in the Advanced Office. defense research planning, uprooting security weaknesses in cars.
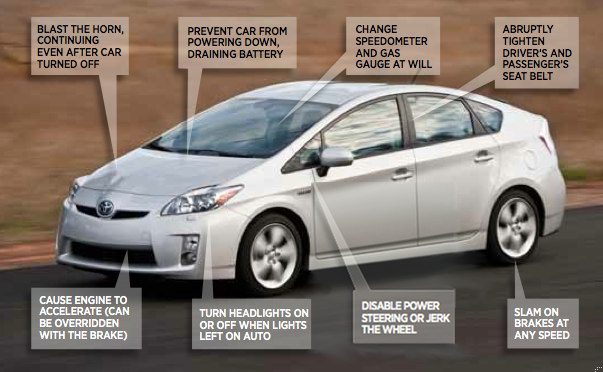
The duo plans to release their discoveries and attacking software, which they developed at the Defcon hacker conference in Las Vegas. They say that it is better to help other researchers find and fix what is connected with the safety of the automotive industry before hackers climb under the hood of unsuspecting drivers. The need to control this issue is growing as cars are increasingly automated and connected to the Internet, and the problem goes beyond Toyota and Ford. Virtually every American automaker provides cellular or Wi-Fi networks, like General Motors - OnStar, Toyota - Safety Connect, and Ford - SYNC. The mobile commerce and industry group GSMA estimates revenues from auto wireless devices at $ 2.5 billion today. The number of projects will grow tenfold by 2025. Without improved security, all of this is potentially vulnerable, and automakers still underestimate the importance of the issue.
Driving their cars for an hour, Miller and Valashek showed that they had understood enough about the Escape and Toyota Prius device (both models of 2010). A number of unpleasant surprises emerged: from an uncontrolled pedal to unexpected actuations of the Prius brake at high speed. They sent commands from their laptops that turned off the power steering, forged GPS readings and speedometers and odometers. Finally, they sent me to a country road, where Valasek showed that he could violently pull the Prius steering at any speed, which threatened to hit the corn field or head-on. “Imagine you are driving 80 miles an hour,” says Valashek, “and you are heading for a car near you or oncoming traffic. This is a setup. ”
A Ford spokesman says the company takes hackers "very seriously," but Toyota, in turn, doesn’t make any impression on the tricks of Miller and Valashek. “We focus, like the entire automotive industry, on preventing hacking by remote wireless devices,” he writes in an e-mail. Also, according to him, Toyota engineers are testing their machines for wireless attacks, “We believe our systems are reliable and secure.”
But the work of Miller and Valashek assumed physical access to the cars' computers for the following reason: obtaining wireless access to the car’s network is not new. A team of researchers from the University of Washington and the University of California, San Diego, experimenting on a sedan from an unnamed company in 2010, revealed that they could wirelessly penetrate the same critical systems that Miller and Valashek used, via OnStar, cellular, Bluetooth bugs, Android apps that sync with the car's network from the driver's smartphone or even a malicious file on an audio CD in the car's stereo system. “Scientists have shown that you can get remote code execution,” says Valasek, using hacker jargon, “to start executing commands on the system. We showed that you can do a lot of crazy things as soon as you rush inside the system "
One of the professors at UCSD (University of California, San Diego) participating in these tests, Stefan Savac, argues that wireless hacks are still possible and affect the entire industry: “Considering that attacks on automobile systems have not yet been noticed outside the laboratory “Manufacturers simply did not fully provide themselves with software,” he says. “The difficulties that we found existed on the PC in the early and mid-1990s.”
As cars move closer to Google’s dream of robotic cars, more and more options are potentially vulnerable to attack. Miller and Valasek used Toyota and Ford self-parking functions, for example, to grab steering. A car, such as the 2014 Mercedes-Benz S-Class, which can monitor traffic in a traffic jam (stop-and-go system) or follow the car on the contrary, without driver intervention, can give the hacker even more opportunities to attack, says analyst Gartner Group Tilo Kozlowski.
At the same time, Miller and Valasek argue that the best way to convince car companies to provide their cars with protection, to show what can be with a multi-ton rocket on wheels. It’s better to hijack a digital SUV now than when intruders take control of it. “If the only thing holding you back from crashing your car is that no one is talking about it,” says Miller, “then you are at risk anyway.”
Source: https://habr.com/ru/post/188966/
All Articles