Cloud networking and network connectivity with the cloud

Hello, dear lovers of cloud computing.
Today I was forced to write a post about networks — about those networks that are used in our cloud . I will do my best to explain how everything is organized here, and also I will talk about how you can connect to our cloud.
')
So, to begin with: if you take a virtual machine with us in the cloud , then you automatically get an external routed network with a mask / 29. This means that you do not immediately have two, not three, not four, but as many as 5 WHITE ADDRESSES! One address is left for us to use on the router. But then begins customization for the client. This means that we can:
- provide an external routable network with more addresses
- provide an isolated network for communication between virtual machines
- combine different options for providing these networks
- issue both internal and external networks
- issue 2 or more external networks or internal networks.
Everything is limited by your imagination and desire to work with our technical support service. Let us dwell on each case.
Case 1 (easy):
You get a service for placing in the cloud of your virtual machine. We create a pool of resources and allocate you a network with 5 addresses. You configure the virtual machine in accordance with the instructions received and (TADAM!) It works (who would doubt?).
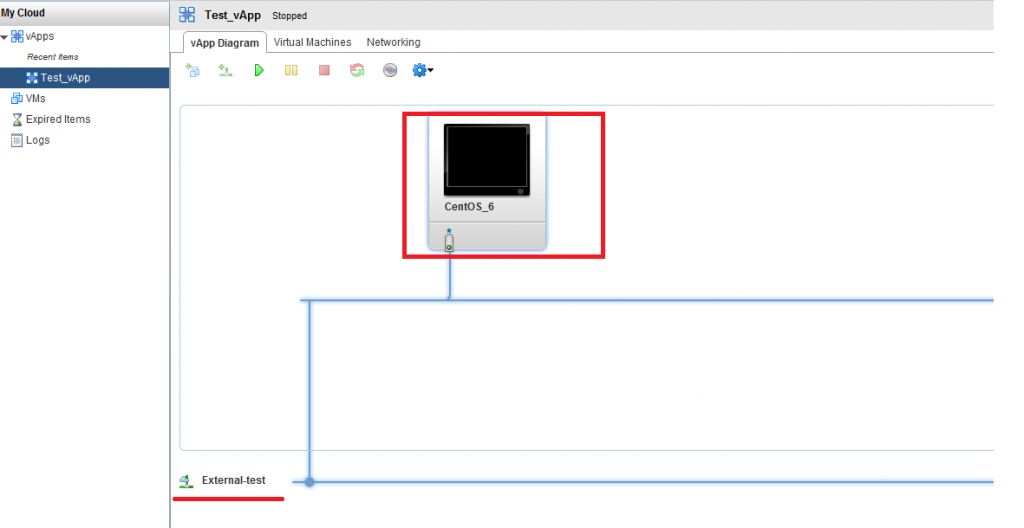

You wanted to save money and instead of taking another car for a new site, you just hung up another address with an alias. And (TADAM!) - it works too.
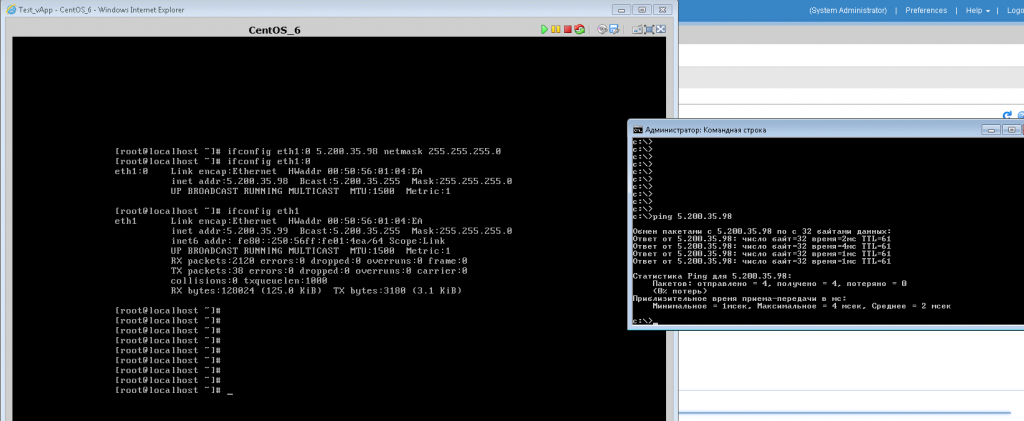
Case 2 (even easier, because I have not met yet):
You are a developer. Moreover, such a developer, which is convenient to work in the console VMware. You need to organize a test stand to check the next HelloWorld project. Fine! We load our cars into the cloud (which is already rented), connect them to a dedicated internal network, turn on and check everything we want. Bonus: you can use any addressing inside such a VLAN.
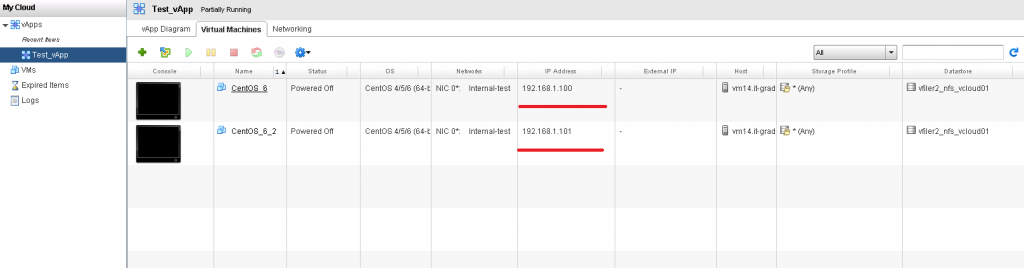
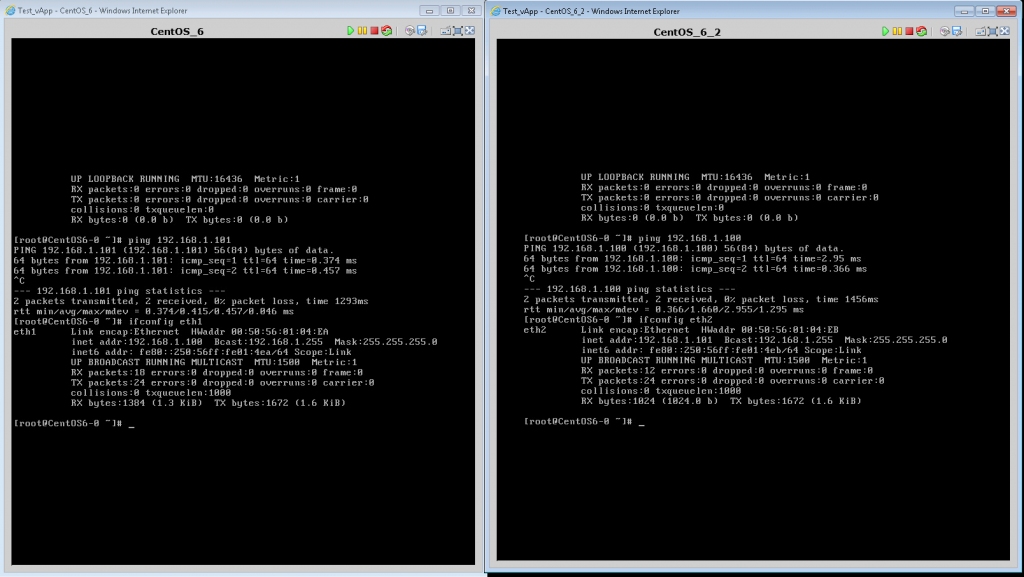
Case 3 (steamed, but not hard, because it requires approximately 5 mouse clicks more than in 1 case):
You went on about the "system" and decided not to stand out from the general mass of those who use the frontend / backend topology. For example, you have a web server with some important content and a database to which this same server accesses. The database should be unavailable from the Internet, because it is flooded with all sorts of marginals who are trying to steal / hack / add this same database. The easiest protection option is to protect it (the database, the database server) from communicating with the raging Internet at level 2 of the OSI network model. And this, too, is within our power. We issue 2 networks: a rich (as many as 5 IP addresses) external network and a dimensionless internal network. We connect the WEB server to these two networks with different adapters (YES, IT IS ALSO POSSIBLE!), We connect the database server only to the internal network. It will look like this topology:

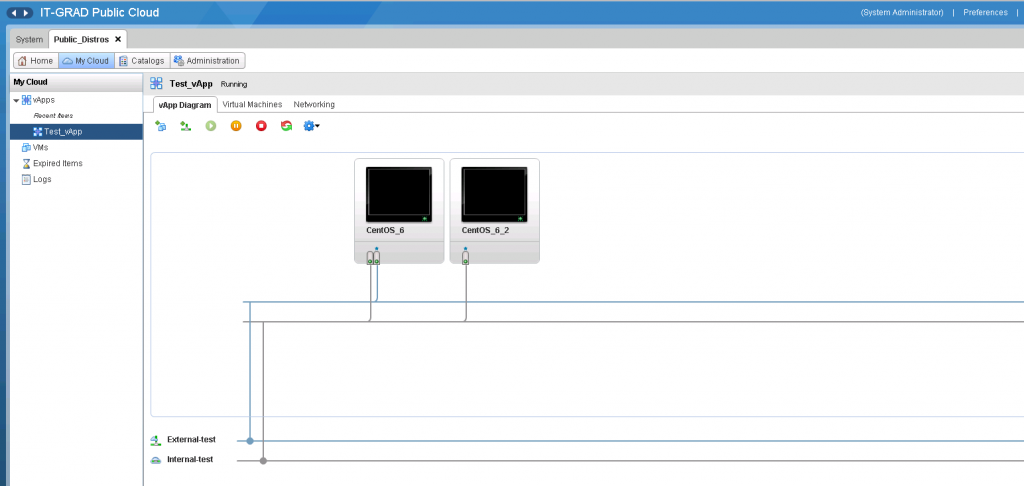
After these manipulations, we have separated the database north from the Internet and various malware will not get to it (but we know that this problem is only the tip of the iceberg, because the frontend needs to be finished, because through it the malware can still get to our defenseless server with database).
Case 4:
VMware has a product called vShield manager . In short: this is a regular firewall / router implemented as a virtual machine. In addition to all this - its interface integrates with vCloud and you can manage settings (rules, routing, IPSec, etc. things) directly from the cloud. Something like case 3. However, now you can add NAT rules and configure firewall policies for yourself from the GUI:
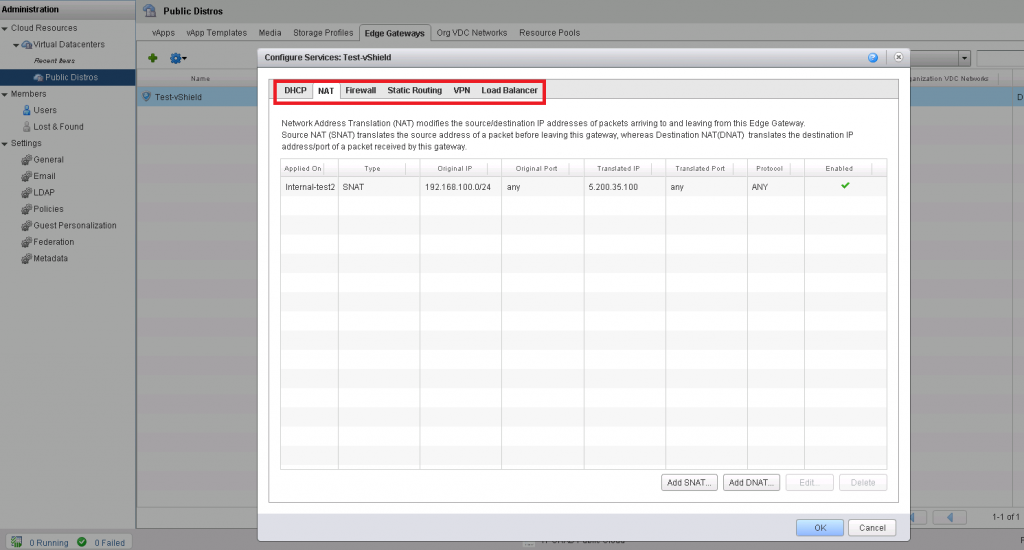
Case 4a:
This case is very similar to the previous version, but unlike it, not vShield is used as a router / firewall, but another solution (for example, MS TMG, Vyatta, or a customized distribution with the opensource system). Those. we also select organizations in the cloud 2 networks: internal and external, and connect them to this router.
Now I’ll tell you a little about how you can set up secure connections to your clouds. As you already guessed, there are 2 connection options: at the level of 2 OSI models and at the level of 3 of the same model.
Connection at level 2: you either pull the wire to our data center, or rent a VLAN from your provider, which is represented in our data center. We are forwarding this link to your cloud and voila.
The connection at level 3 is carried out via the public Internet using tunneling. This is the easiest way. It is also implemented on the basis of vShield, or any other specialized distribution. vShiled provides only IPSec tunnels. Below is an example of the current tunnel of one of our clients:

Now you know how networks work in the IT-GRAD cloud; how to connect to your cloud and what you need for it. If you are really interested - ask your questions, I will try to help.
Source: https://habr.com/ru/post/188608/
All Articles