Mobile Internet security inside and out
With the development of mobile networks, mobile Internet is also developing. Everyone is used to the usual Internet: twisted pair, Ethernet, TCP / IP. And what does the Internet mobile hide in itself? Let's try to find out! In our study, we will touch on the general principles of the mobile Internet, take a closer look at the GPRS Tunneling Protocol, talk about the GRX network and discuss some practical approaches to the security of a mobile packet network.
How each of us connects to the mobile Internet? In principle, you need to know only three parameters: APN, login and password. APN is an access point through which a subscriber can connect to the necessary service (WAP, MMS, Internet); with our operators, it usually looks like internet. <operator-name> .ru. Login and password are usually simple: internet - internet or something like that.
Now that we know the necessary parameters, we can connect to the mobile Internet! How does this mysterious procedure occur? It occurs in two stages:
')
Let's take a closer look at each of them.
In the GPRS Attach procedure, the phone starts to “communicate” with the operator's packet network. There is an authentication and authorization of user equipment on the following parameters:
IMSI (International Mobile Subscriber Identity, individual subscriber number) - for identification
IMEI (International Mobile Equipment Identity - International Mobile Equipment Identity) can also be checked. This identifier can be used to check the lists of stolen equipment, and if a specific IMEI is on the list of stolen, then access to the network may be denied, or even reported "where it should be" :)
Upon successful completion of the GPRS Attach procedure, the PDP (Packet Data Protocol) Context Activation procedure begins. To understand this procedure, we digress and define some concepts.
SGSN (Serving GPRS Support Node, GPRS customer service node) is a device that implements the basic functions of packet data processing in a mobile network.
GGSN (GPRS Gateway Service Node, gateway GPRS node) is a device that provides data transmission from the operator’s network to external networks (for example, to the Internet). In fact, it can be a regular router with support for some specific functions.
GTP (GPRS Tunneling Protocol) is a protocol stack used in GPRS, UMTS and LTE networks.
So, PDP Context Activation (the scheme is greatly simplified).

What happens during the implementation of this scheme?
In essence, the PDP Context Activation procedure is the creation of a tunnel between the telephone and the gateway in the carrier's network. And now we can go to your favorite sites and read the mail.
Immediately the question arises: how does all this work in roaming? It turns out that there is a special network: GRX (Global Roaming Exchange) - a network for exchanging packet data of roaming subscribers of mobile networks. Through it and all our traffic "runs". Like this:

What do we see? We see that the packages with our favorite series run through half the world from our operator to the operator in a warm country. They run on a special network, wrapped in GTP protocol. And all the negotiations between the operators' special trains are being conducted on the same GTP.
And here comes the idea: wouldn’t we try to figure out something similar under laboratory conditions? Build your SGSN and GGSN. Well, how come to incredible discoveries?

After a long search, it turned out the following.
There is a special purpose software that implements some of the functions of the SGSN. It looks like a script for Linux, which is able to emulate all the necessary procedures (GPRS Attach and PDP Context Activation) and issue a complete interface for accessing the Internet as if we stuck a 3G modem. Upon learning of this, we immediately rushed to look for a device that was ready to shoulder the functions of GGSN. It turned out that the popular Cisco 7200 router is quite suitable.
After some manipulations, settings and tests, success awaited us.
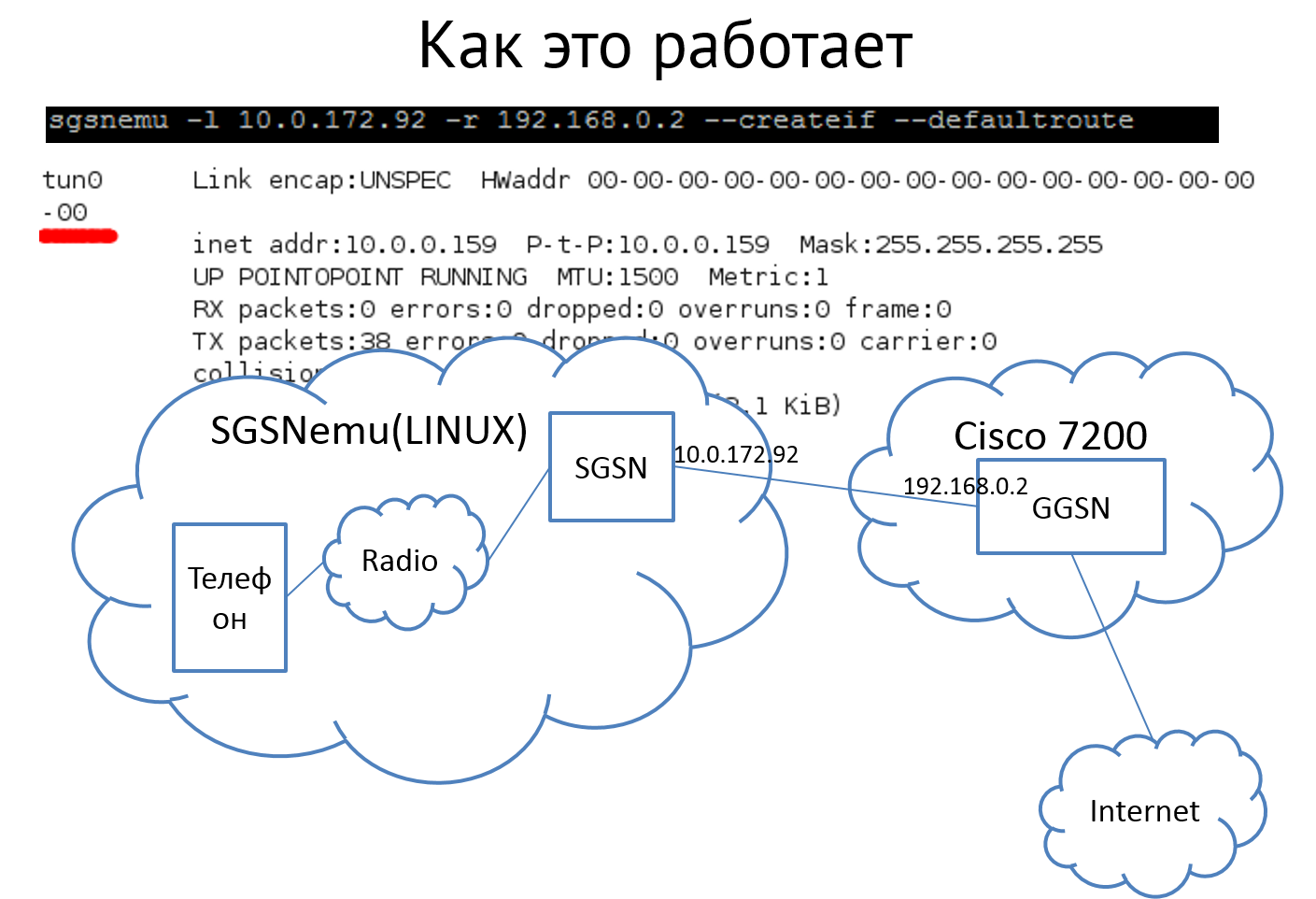
The stand easily lifted tunnels through which the real Internet was "visible". We immediately began to look at what packages go between our mighty SGSN and GGSN. Do they look like real ones? With a sinking heart, we open a dump - and yes! packages like real ones.

Similar packages can go to the GRX-network, and they may well be overheard by an evil hacker. What does he see there? Let's try to find out.
GTP protocol can be of several types: GTP-U is used to directly package and transfer user data, GTP-C for session management (it is with its help the PDP Context Activation procedure and other service procedures are performed); there is also GTP '(GTP Prime) - it is used to transfer billing information. GTP does not support peer authentication and encryption; it works over UDP. What is interesting about all this? It is interesting here almost everything!
Take GTP-U and see what a tunnel with user data looks like. Tunnels are separated by a TEID (Tunnel Endpoint Identificator) parameter.
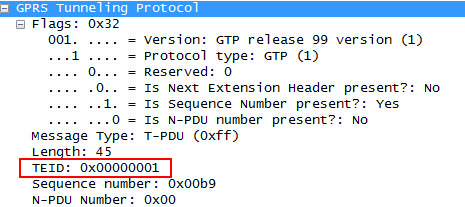
Upon further study, it turned out that, if desired, the TEID field can be changed, and by sending a packet with a spoofed tunnel identifier, you can unexpectedly break into someone else's session.
But GTP-C. Surprisingly, if there is no authentication or hints of encryption of the transmitted data, you can try not only to listen, but also, sorry, send something. For example, "left" requests to establish or terminate a session.
Let us try to outline the vectors of possible attacks and consider them closer.
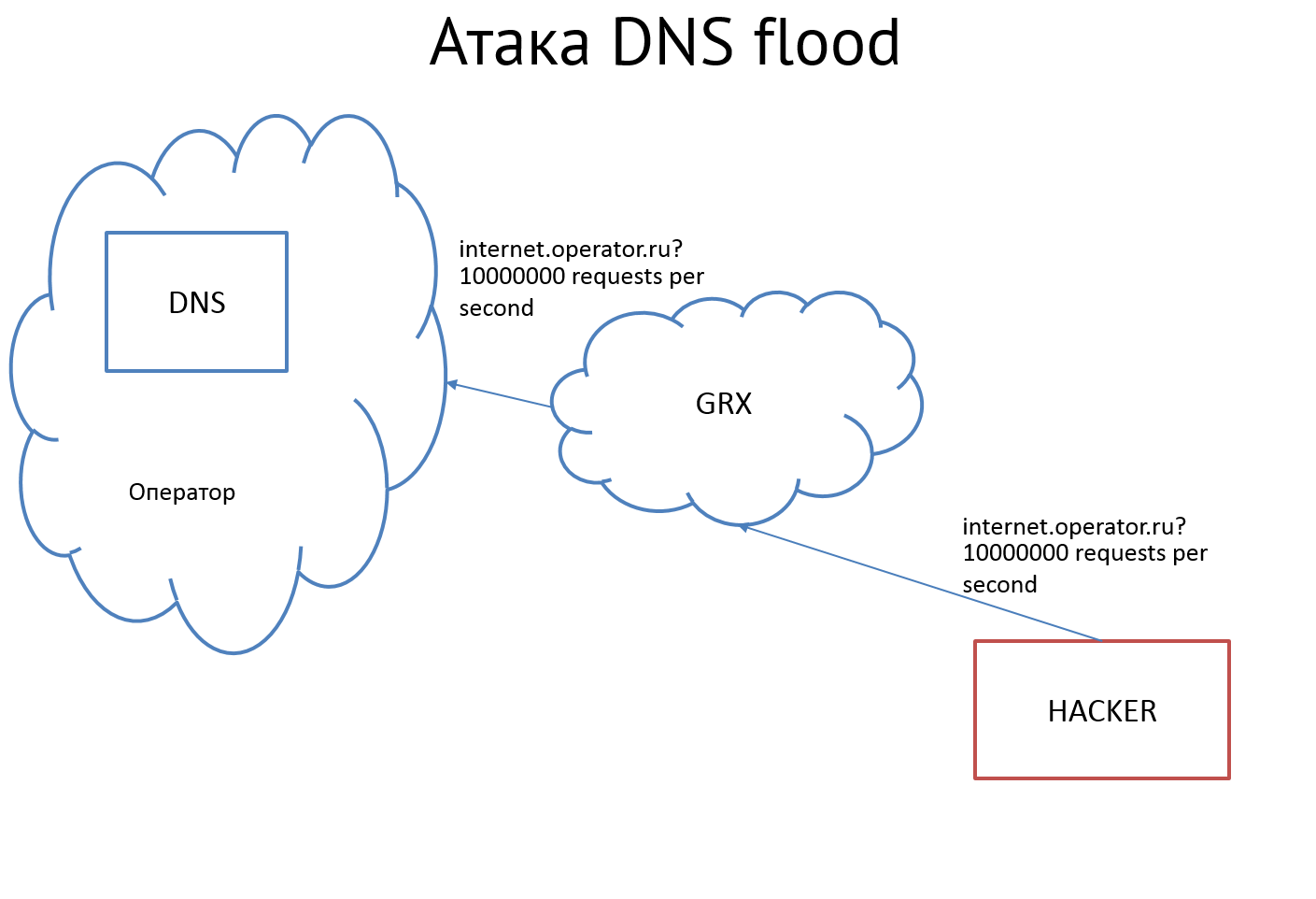
Here, for example, attack DNS flood. The attacker sends a large number of requests for permission APN of our operator. All these packets will bombard the poor carrier DNS, which will not withstand the heat and generally refuse to transmit the GGSN address to anyone, causing a global DoS for subscribers.
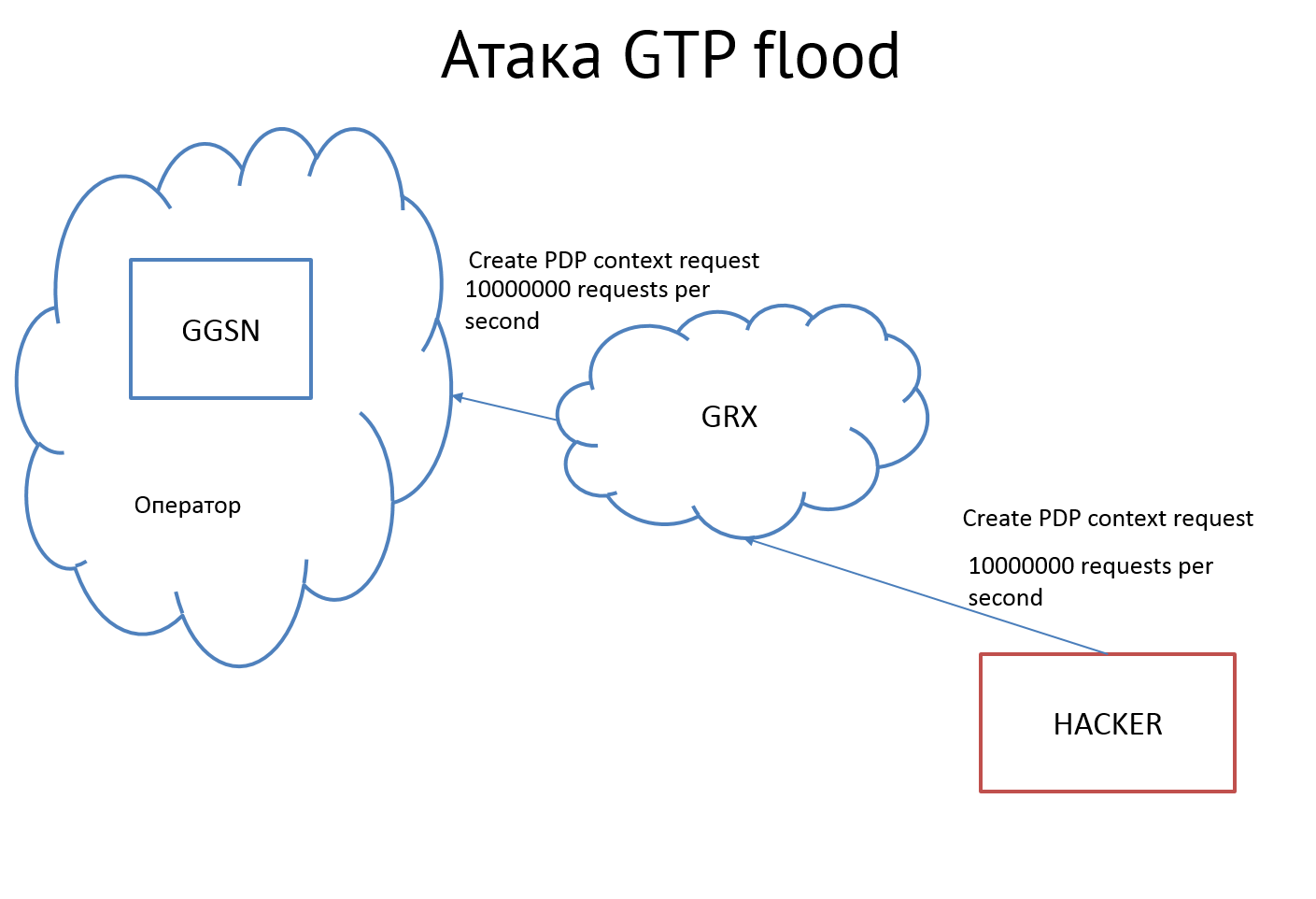
Or, the attacker will begin to send his own requests to create a PDP context. GGSN, seeing such pressure, may well think, or even hang. Which again will lead to a denial of service subscribers.
But what if, instead of creating requests, you try sending session break requests?
For example, like this:

Angry hacker, substituting the address of a foreign SGSN, will send requests to disconnect. GGSN, thinking that the subscriber downloaded his favorite series and wants to complete the Internet session, removes this tunnel from himself, breaking the connection.
Sketching a few vectors, turn our eyes to real objects in order to “touch” all this. Type the query "GGSN" in the shodan. Here is a piece of results issued.
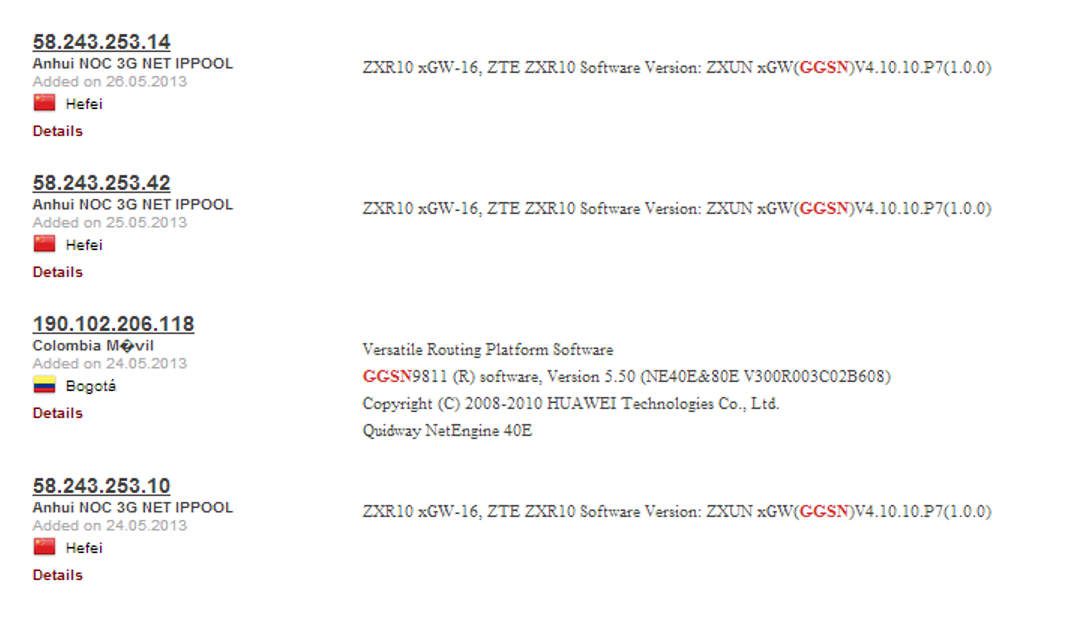
All this looks like a real GGSN, put on the Internet.
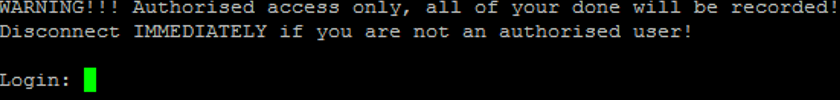
Or try writing a script that sends GTP-echo requests, and even let it go for a walk on the Internet: what if someone responds. And the respondents are:
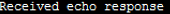
Sometimes even with open telnet.
In the new generation standard, codenamed LTE, GTP is still used, and therefore all of the above is relevant and will be relevant in the foreseeable future.
That's all for today. See you again!
I want to express my gratitude to the department of security analysis of network devices Positive Technologies for their help in preparing the material.
Author: Ilya Safronov, Positive Research.
How each of us connects to the mobile Internet? In principle, you need to know only three parameters: APN, login and password. APN is an access point through which a subscriber can connect to the necessary service (WAP, MMS, Internet); with our operators, it usually looks like internet. <operator-name> .ru. Login and password are usually simple: internet - internet or something like that.
Now that we know the necessary parameters, we can connect to the mobile Internet! How does this mysterious procedure occur? It occurs in two stages:
')
- GPRS Attach,
- PDP Context Activation.
Let's take a closer look at each of them.
GPRS Attach
In the GPRS Attach procedure, the phone starts to “communicate” with the operator's packet network. There is an authentication and authorization of user equipment on the following parameters:
IMSI (International Mobile Subscriber Identity, individual subscriber number) - for identification
- subscriber;
- Keys stored on the SIM card - for subscriber authentication;
- checking available services to the subscriber (Internet, MMS, WAP) by recording in the subscriber database
IMEI (International Mobile Equipment Identity - International Mobile Equipment Identity) can also be checked. This identifier can be used to check the lists of stolen equipment, and if a specific IMEI is on the list of stolen, then access to the network may be denied, or even reported "where it should be" :)
Upon successful completion of the GPRS Attach procedure, the PDP (Packet Data Protocol) Context Activation procedure begins. To understand this procedure, we digress and define some concepts.
SGSN (Serving GPRS Support Node, GPRS customer service node) is a device that implements the basic functions of packet data processing in a mobile network.
GGSN (GPRS Gateway Service Node, gateway GPRS node) is a device that provides data transmission from the operator’s network to external networks (for example, to the Internet). In fact, it can be a regular router with support for some specific functions.
GTP (GPRS Tunneling Protocol) is a protocol stack used in GPRS, UMTS and LTE networks.
So, PDP Context Activation (the scheme is greatly simplified).

What happens during the implementation of this scheme?
- The phone sends a context activation request to the SGSN, which, among other things, includes a username, password and APN.
- SGSN, having received the APN, tries to resolve it on the internal DNS server. The server resolves the provided APN and returns the address of the responsible APN GGSN.
- At this address, the SGSN sends a request to create a PDP context.
- GGSN checks the login and password provided on the RADIUS server.
- Then it gets an IP address for our phone.
- And all the information needed to activate the PDP context is transmitted back to the SGSN.
- The SGSN completes the activation procedure by sending the data necessary for establishing a connection to the telephone.
In essence, the PDP Context Activation procedure is the creation of a tunnel between the telephone and the gateway in the carrier's network. And now we can go to your favorite sites and read the mail.
Roaming
Immediately the question arises: how does all this work in roaming? It turns out that there is a special network: GRX (Global Roaming Exchange) - a network for exchanging packet data of roaming subscribers of mobile networks. Through it and all our traffic "runs". Like this:

- Successfully having reached the hot edges, we decided to download our favorite series. Turned on the phone, started to connect to the Internet (send login, password, APN).
- The foreign SGSN tries to resolve the APN provided by us on its DNS server.
- The DNS server, not having found such records, calls the root DNS server, which is located in the GRX network.
- The root DNS server sends a request to the DNS server on the network of our native operator.
- That, in turn, responds to it with the address of our GGSN.
- The root DNS reports this address to the DNS server of the foreign operator.
- Which in turn reports this address to a foreign SGSN.
- The SGSN, knowing the GGSN address, sends it a request to activate the PDP context.
- GGSN, if all the conditions are met (there is money in the account, the correct username and password are indicated, etc.), sends a confirmation, SGSN accepts it and sends a confirmation to our phone for Internet access.
What do we see? We see that the packages with our favorite series run through half the world from our operator to the operator in a warm country. They run on a special network, wrapped in GTP protocol. And all the negotiations between the operators' special trains are being conducted on the same GTP.
And here comes the idea: wouldn’t we try to figure out something similar under laboratory conditions? Build your SGSN and GGSN. Well, how come to incredible discoveries?
SGSN + GGSN on the knee

After a long search, it turned out the following.
There is a special purpose software that implements some of the functions of the SGSN. It looks like a script for Linux, which is able to emulate all the necessary procedures (GPRS Attach and PDP Context Activation) and issue a complete interface for accessing the Internet as if we stuck a 3G modem. Upon learning of this, we immediately rushed to look for a device that was ready to shoulder the functions of GGSN. It turned out that the popular Cisco 7200 router is quite suitable.
After some manipulations, settings and tests, success awaited us.

The stand easily lifted tunnels through which the real Internet was "visible". We immediately began to look at what packages go between our mighty SGSN and GGSN. Do they look like real ones? With a sinking heart, we open a dump - and yes! packages like real ones.

Similar packages can go to the GRX-network, and they may well be overheard by an evil hacker. What does he see there? Let's try to find out.
Security questions
GTP protocol can be of several types: GTP-U is used to directly package and transfer user data, GTP-C for session management (it is with its help the PDP Context Activation procedure and other service procedures are performed); there is also GTP '(GTP Prime) - it is used to transfer billing information. GTP does not support peer authentication and encryption; it works over UDP. What is interesting about all this? It is interesting here almost everything!
Take GTP-U and see what a tunnel with user data looks like. Tunnels are separated by a TEID (Tunnel Endpoint Identificator) parameter.

Upon further study, it turned out that, if desired, the TEID field can be changed, and by sending a packet with a spoofed tunnel identifier, you can unexpectedly break into someone else's session.
But GTP-C. Surprisingly, if there is no authentication or hints of encryption of the transmitted data, you can try not only to listen, but also, sorry, send something. For example, "left" requests to establish or terminate a session.
Let us try to outline the vectors of possible attacks and consider them closer.

Here, for example, attack DNS flood. The attacker sends a large number of requests for permission APN of our operator. All these packets will bombard the poor carrier DNS, which will not withstand the heat and generally refuse to transmit the GGSN address to anyone, causing a global DoS for subscribers.

Or, the attacker will begin to send his own requests to create a PDP context. GGSN, seeing such pressure, may well think, or even hang. Which again will lead to a denial of service subscribers.
But what if, instead of creating requests, you try sending session break requests?
For example, like this:

Angry hacker, substituting the address of a foreign SGSN, will send requests to disconnect. GGSN, thinking that the subscriber downloaded his favorite series and wants to complete the Internet session, removes this tunnel from himself, breaking the connection.
Sketching a few vectors, turn our eyes to real objects in order to “touch” all this. Type the query "GGSN" in the shodan. Here is a piece of results issued.

All this looks like a real GGSN, put on the Internet.
Or try writing a script that sends GTP-echo requests, and even let it go for a walk on the Internet: what if someone responds. And the respondents are:

Sometimes even with open telnet.

In the new generation standard, codenamed LTE, GTP is still used, and therefore all of the above is relevant and will be relevant in the foreseeable future.
That's all for today. See you again!
I want to express my gratitude to the department of security analysis of network devices Positive Technologies for their help in preparing the material.
Author: Ilya Safronov, Positive Research.
Source: https://habr.com/ru/post/188574/
All Articles