Django development server and HTTPS testing
Hello dear community,
Having chosen the Django framework for developing a corporate website, I was faced with the problem of testing its work using the HTTPS protocol when using the embedded web server. Despite the support for working with secure connections in Django, the bundled web server does not serve HTTPS requests.
The first thing that came to mind was to raise a full-fledged web server (for example, Apache ) for development and testing, but what if you didn't want to give up the convenience and ease of use of the Django embedded web server?
')
A search on the Internet for “django + https” issued several articles dated 2009 and 2012 , in which it is proposed to use stunnel for HTTPS testing.
This article is an instruction obtained as a result of setting up
First you need to install
The basic
In our case, there is no need to make changes, as the
But what you need is a X.509 certificate.
The stunnel manual contains the following certificate requirements:
To generate a private key and certificate, we will use OpenSSL (must be present in Ubuntu 04/12/1):
During generation, you must enter the owner information ( country codes for convenience).
At the output we get two files
Now create a configuration file for the tunnel.
An example of the
Create a configuration file in the home directory:
In our case, it has the following contents:
Let's check what happened?
Run
The HTTPS = on environment variable is required for a proper HTTPS simulation in Django, without it the request.is_secure () method will return False.
Check the “listening” ports:
The tunnel was successfully created -
To kill a tunnel, the
Open any existing URL in the browser using
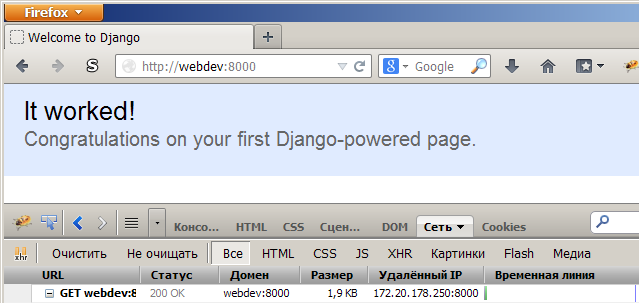
It was

It became
As a result, we get the ability to debug a Django project using HTTPS without having to keep a full-fledged web server.
I want to note that there is a version for Windows and Android on the site
Thank you all for your attention and I hope that this information will be useful to someone.
At the end I will list the advantages and disadvantages that I have noted for myself, and also provide a list of links.
+ installation of a full-fledged web server is not required;
+ ability to build tunnels for several Django web servers;
+ use the benefits of the embedded web server.
- this is not a full-fledged HTTPS-enabled web server;
- the need to install and configure additional software;
- in fact, the Django web server handles HTTP requests (see logs below).
Having chosen the Django framework for developing a corporate website, I was faced with the problem of testing its work using the HTTPS protocol when using the embedded web server. Despite the support for working with secure connections in Django, the bundled web server does not serve HTTPS requests.
The first thing that came to mind was to raise a full-fledged web server (for example, Apache ) for development and testing, but what if you didn't want to give up the convenience and ease of use of the Django embedded web server?
')
A search on the Internet for “django + https” issued several articles dated 2009 and 2012 , in which it is proposed to use stunnel for HTTPS testing.
This article is an instruction obtained as a result of setting up
stunnel under the Django development environment on Ubuntu 12.04.1 LTS x64.Software environment
- Ubuntu 12.04.1 LTS (x64)
- OpenSSL 1.0.1 Mar 14 2012
- Python 2.7.3
- virtualenv 1.8.4
- Django 1.5.1
Install and configure stunnel
First you need to install
stunnel (version 4.x, branch 3.x is no longer supported): $ sudo apt-get install stunnel4 The basic
stunnel settings are in the /etc/default/stunnel4 : # /etc/default/stunnel # Julien LEMOINE <speedblue@debian.org> # September 2003 # Change to one to enable stunnel automatic startup ENABLED=0 # Configuration file loacation mask FILES="/etc/stunnel/*.conf" OPTIONS="" # Change to one to enable ppp restart scripts PPP_RESTART=0 In our case, there is no need to make changes, as the
stunnel will be used only in conjunction with the Django web server at the time of development and testing.But what you need is a X.509 certificate.
Certificate Generation
The stunnel manual contains the following certificate requirements:
... Each SSL enabled daemon needs a valid X.509 certificate to the peer. It also needs to enter the incoming data. OpenSSL package ...
... The order of contents of the .pem file is important. It should contain the unencrypted private key first, then a signed certificate (not certificate request). There should be also empty lines after certificate and private key. Plaintext certificate information appended should not be discarded. So the file should look like this:
----- BEGIN RSA PRIVATE KEY -----
[encoded key]
----- END RSA PRIVATE KEY -----
[empty line]
----- BEGIN CERTIFICATE -----
[encoded certificate]
----- END CERTIFICATE -----
[empty line]
To generate a private key and certificate, we will use OpenSSL (must be present in Ubuntu 04/12/1):
$ cd ~ $ openssl genrsa -out private.key $ openssl req -new -x509 -key private.key -out stunnel.cert -days 365 During generation, you must enter the owner information ( country codes for convenience).
At the output we get two files
private.key and stunnel.cert , which need to be merged and add empty lines according to the template: $ (cat private.key ; echo ; cat stunnel.cert ; echo) > stunnel.pem Now create a configuration file for the tunnel.
configuration file
An example of the
stunnel.conf-sample configuration file is located in /usr/share/doc/stunnel4/examples/ , and the description of the parameters can be found in man stunel4 or in the documentation . Plus, the FAQ section on the program’s website contains some useful tips.Create a configuration file in the home directory:
$ cd ~ $ vim stunnel.conf In our case, it has the following contents:
; Certificate & Key cert = ./stunnel.pem ; Use SSL version 3, which is more secure sslVersion = SSLv3 ; If next argument is empty, then no pid file will be created pid = ; if 'yes' stay in foreground (don't fork) and log to stderr instead of via syslog foreground = no ; Performance tweak from FAQ (https://www.stunnel.org/faq.html) socket = l:TCP_NODELAY=1 socket = r:TCP_NODELAY=1 ; Enable compression compression = zlib ; Debugging - emerg (0), alert (1), crit (2), err (3), warning (4), notice (5), info (6), or debug (7) debug = 7 output = /var/log/stunnel4/stunnel.log ; HTTPS service section [https] ; Port to listen incoming client connections accept = 8443 ; Port which Django development server listens to connect = 8000 ; Tweak for MSIE (see FAQ or manual) TIMEOUTclose = 0 Let's check what happened?
Creating a tunnel and starting a web server
Run
stunnel and the built-in Django web server for the test project (empty project, immediately after django-admin.py startproject ): $ cd ~ $ stunnel4 stunnel.conf $ source django/bin/activate (django)$ cd django/projects (django)$ django-admin.py startproject testone (django)$ cd testone/ (djanho)$ HTTPS=on python manage.py runserver The HTTPS = on environment variable is required for a proper HTTPS simulation in Django, without it the request.is_secure () method will return False.
Check the “listening” ports:
$ netstat –an Active Internet connections (servers and established) Proto Recv-Q Send-Q Local Address Foreign Address State ... tcp 0 0 0.0.0.0:8443 0.0.0.0:* LISTEN tcp 0 0 127.0.0.1:8000 0.0.0.0:* LISTEN ... The tunnel was successfully created -
stunnel listens on all external interfaces port 8443, and the web server local connections on port 8000.To kill a tunnel, the
killall command will work: $ ps -e | grep stunnel4 12530 pts/1 00:00:00 stunnel4 12531 pts/1 00:00:00 stunnel4 12532 pts/1 00:00:00 stunnel4 12533 pts/1 00:00:00 stunnel4 12534 pts/1 00:00:00 stunnel4 12535 ? 00:00:00 stunnel4 $ killall stunnel4 Operation check
Open any existing URL in the browser using
https:// instead of http:// . At the first request, we should see warnings about an unreliable certificate, since It was signed by us personally, and not by an accredited center (Certificate Authority). After confirming the security exception, we will see the requested page received via the HTTPS protocol.
It was

It became
Conclusion
As a result, we get the ability to debug a Django project using HTTPS without having to keep a full-fledged web server.
I want to note that there is a version for Windows and Android on the site
stunnel , so you can try to build a similar scheme on these operating systems.Thank you all for your attention and I hope that this information will be useful to someone.
At the end I will list the advantages and disadvantages that I have noted for myself, and also provide a list of links.
Benefits
+ installation of a full-fledged web server is not required;
+ ability to build tunnels for several Django web servers;
+ use the benefits of the embedded web server.
disadvantages
- this is not a full-fledged HTTPS-enabled web server;
- the need to install and configure additional software;
- in fact, the Django web server handles HTTP requests (see logs below).
Web server logs
Validating models ...
0 errors found
July 26, 2013 - 10:06:33
Django version 1.5.1, using settings 'testone.settings'
Development server is running at 127.0.0.1 : 8000 /
Quit the server with CONTROL-C.
...
[26 / Jul / 2013 10:07:25] GET / HTTP / 1.1 200 1955
[26 / Jul / 2013 10:07:30] GET / HTTP / 1.1 200 1955
...
0 errors found
July 26, 2013 - 10:06:33
Django version 1.5.1, using settings 'testone.settings'
Development server is running at 127.0.0.1 : 8000 /
Quit the server with CONTROL-C.
...
[26 / Jul / 2013 10:07:25] GET / HTTP / 1.1 200 1955
[26 / Jul / 2013 10:07:30] GET / HTTP / 1.1 200 1955
...
Materials
Source: https://habr.com/ru/post/188106/
All Articles