3070 hours of hack quest, report and stories of participants

Participants in one of the offline hacker tournaments Cyber Readiness Challenge
On Friday, the cyber readiness challenge hack quest, which was conducted by Symantec and CROC, ended on Friday.
Often there are hakkvesty that make people far from professional infoboda. Such quests can be found on the tasks for a guessing game: to pass, you need not so much skill as luck and guessing what the author had in mind. And here, it seems, a very rare thing has turned out: the competition was made by people fumbling in the infobox, but at the same time they were far from the CTF world. As a result, the tasks turned out to be naive on the one hand, but at the same time technically correct. In one competition, tasks such as “Scan the grid. How many machines do we have on the network? ”And hardcore like“ Decipher the clogged base64 block, multi-byte xor-key unknown. ”Vlad "vos" Roskov
')
Participants connected to a simulator simulating the network of a large corporation EDC. Under the scenario in the EDC security system, several incidents occurred. The company hires to figure out what happened to the best experts in the field of information security, to prove or disprove the possibility of hacking.
In general, the game took about 3070 hours (total time spent by participants). In total, 143 players from different regions of Russia logged in, about two thirds of whom actively participated.
Winners
I place - vos - Vlad Roskov - St. Petersburg;
II place - VY_CMa - Igor Kanygin - Omsk;
III place - AV1ctOr - Victor Alyushin from Moscow.
According to the results of the online part, Vlad Roskov won, speaking under the nickname of vos. He almost immediately went into the lead and kept it until the very end, where he came with 36,800 out of 38,800 possible points, this is 88 out of 90 tasks (no one took the last two flags). Now, we are waiting for Vlad on the offline part of the tournament on September 10th.
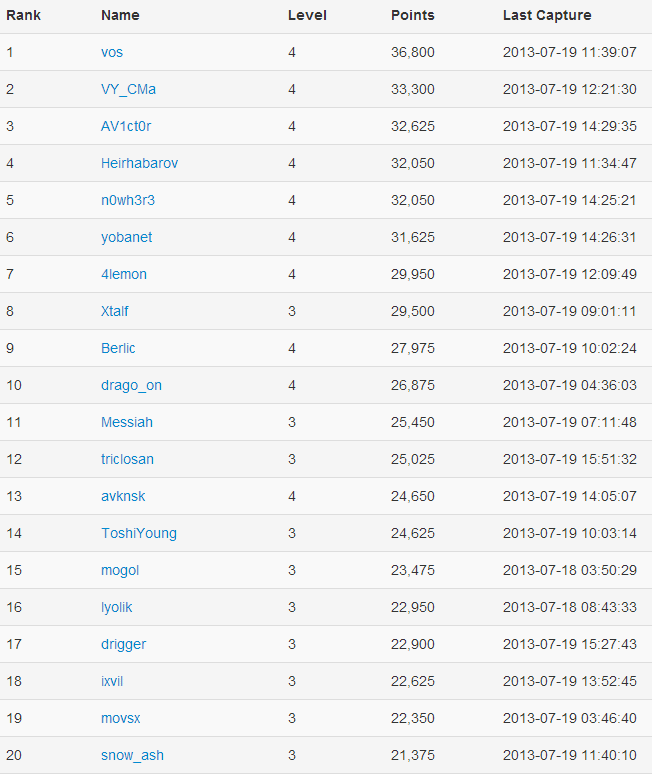
Top 20. Pay attention to the gap between the first players.
Vlad's story about the tournament
Here is what Vlad himself told about the game to journalists:
“In my opinion, a hardened participant in computer security competitions (CTF), the game was amazing: the tasks were naive, but at the same time fascinating. That's great rarity. Anyone who wants to try their hand at simple and at the same time technically literate tasks on information security is highly recommended to complete the Cyber Challenge next time. I look forward to the offline stage, and I thank Symantec and CROC for the cool quest. ”
And here is what he told me already for Habr (hereinafter, these are abbreviations and the assembly of several letters, where the dialogue took place):
I have my own view on this challenge, slightly distorted by the professional deformation of the burned CTF member. Simantekovsky hakkvest surprised: he was both naive and interesting. This happens rarely.
Slept all nights - it's holy :)
In fact, we managed to quickly get ahead, having solved as many as 85 tasks on the very first day (thanks to the support of Symantec, which quickly responded to problems with accessing the task list). After that, I, frankly, froze long and hung with 34,300 points and the last delivery of the flag on the 15th. On the last day I sat down and picked it up, finished 3 tasks.
Close ones did not appreciate the whole day spent nose to the laptop :-D
The simplest thing is to accept the lack of access to the Internet when a gaming VPN is connected.
The greatest difficulty is to come up with a nickname longer than 3 characters when registering.
I read hints on assignments 88, 89. It did not help.
I liked and amazed isolation of the players' infrastructure from each other. I still do not understand how this was implemented. Did each of the hundreds of players have their own set of virtual players raised?
Most of all I liked the fact that the tasks, which were simple in terms of the formulation, forced us to move our brains and come up with an unusual solution. And it’s a damn cool feeling when an idea works the first time.
Victor Alyushin (III place):
I slept every night, but one night the laptop worked - I selected a password for mysql. In principle, everything is simple, except Metasploit, XSS, password selection for mysql and 2 and 3 flags at level 4).
I did almost everything right away, I just didn’t know how to select mysql passwords online ... When your bot was not working and I was thinking how to solve banter.edc, I thought that I had to hack IIS 4.0. Note: We are talking about 78 and 79 flags - as soon as a sufficient number of participants reached them, it turned out to identify the problem and fix it. The tips and the score are restored.
Most of all I liked that I had gone far and did not have to be bored. And also the fact that the Scoreboard hacked the cookie and banter.edc. Please do not change the algorithm and crush a hole on it, but now the decryption of cookies did not provide a special vulnerability, except for the possibility to steal the cookie.
Offline? Of course, just invite) I live in Moscow, so go far.
Teimur Heirkhabarov's story (IV place)
Reached the last 4 levels, it was possible to take 2 flags out of 5 on it. In general, I collected 87 flags, which allowed me to take the 4th place. It is difficult to say how much time I spent on the game. I started to play fully only from 3 days, and only in the evenings, during the day I had to work. I didn’t sleep only the last night, I couldn’t afford it for the rest, getting up to work at 6 in the morning. The main problem for me was the lack of time due to work. It would be good if the game began, for example, on Wednesday, to seize the weekend, when it would be possible to devote enough time to the game. I think many of those who played or those who wanted to play would agree with me, since many of them are working and family people.
The easiest were tasks from the category of which version of this or that software is installed on the server or how many hosts are on the network. The greatest difficulty was caused by 3 tasks. One of them is the brute force password of the MySQL DBMS user. I tried to find the password for about 2 days, in the end it turned out that the tool I used for the brute force worked incorrectly and even passed an effective password. After changing the tool, the password was picked up in a few minutes. 2 other tasks from the 3rd stage for a very long time could not be completed due to technical problems on the game servers. Because of this, it was not clear whether I was doing something wrong, or whether the game server was really failing. The result was the last.
Knowledge was enough, sometimes not enough practical skills. Had to "google" examples of the use of a utility.
Most of all I liked the third and fourth stages of the game, where there were puzzles that really make you think. And of course, the drive of the last hours of the game, when the serious struggle between the participants of the top ten of the rating was launched.
Offline? Most likely not. I live in Krasnoyarsk, far from Moscow.
Here is the story of Andrei Leonov (VII place), also not for journalists:
Took 86 flags. Several of them had to take without glasses, using all the clues.
I think that in total, the whole game took 50 hours. But at a fairly equal pace. I slept four hours a day.
As expected, I’m not very good at analyzing the network infrastructure and the linux toolkit. Because of the latter, it was not possible to take the 87 flag (I understood that it was necessary to redirect the ports through the machine 1.1.2.19, and even understood that it could help me, but I couldn’t find a specific implementation, either through nc or socat), which is very disappointing. Would rise higher in the standings.
What would I change? Some of the tasks, especially simple ones, seemed to me too simple and / or not entirely in the field of information security.
What are the differences from other tournaments? In the scientific-popularity. It was possible to participate even with a minimum of knowledge, but with a great desire, and to achieve not bad results, not only in the tournament scoreboard, but also in terms of obtaining new knowledge.
Difficulties ... well, everything is simple - I spent 2 or 3 tips on the following flags:
- How many hosts are online on the internal network
“The password from the netadmin database user is where the hydra failed me, fed her 200K passwords, and she was silent. Helped the answer to the support service that the password in one of the dictionaries of common passwords. By changing the brutal tool to metasploit / mysql_login, the response was received in a couple of minutes. And I spent the day on this flag)
- Flag 78 - many have cursed him. But the difficulty is not that I did not understand what to do, but in the strange work of the bot. But here - as it is. The strangest thing is that in the last-minute level table I don’t have information that I used all three clues. Miracles?) (Note - here everything is also explained by the same problem, which is described above).
Personally, my mercantile interest - more vulnerabilities in web applications. Good and different. Where is XXE? :) Where would you want a simple WAF (well, at least for quotes to be urlencod'it)? In non-critical tasks, it would be interesting to see something relatively new - SSRF. eg. Or less obvious vectors. Although this is already my whim - I understand this, I’m a single-line union working through mod_rewrite, that the elephant is a grain =) Now, if it were necessary to understand the vector, and understand that operation does not pass mod_rewite, copy the script to which data is transmitted, it would be more interesting.
Offline? It is necessary to register =). Personally and show yourself and look at others. I want to shake vos'u hand. Thank you so much for such an interesting five days. The pilot series went great - waiting for the next one :)
Andrew also told a few things that we will not publish yet, since these are obvious spoilers (the first online tournament was held in Russia, but it will be in other countries).
Our experience
As I have already said, the online tournament within the framework of the CRC was held, for our information, for the first time. Many participants asked to raise the IRC channel for communication, plus there was a miscalculation with one wrong hint (many people complained about the complexity of the brute force passwords). We will take into account these and other remarks, plus when we finish analyzing the statistics of the passage by all participants, we may modify the tasks and hints. After this, the tournament will be held not only in our country.
Who held the tournament and why?
Symantec Corporation (the world leader in security solutions, data backup and high availability) and CROC (Russian leader in the creation of IT infrastructures, # 1 in Russia for system integration services according to IDC reports for 2002–2012) . The main purpose of the Cyber Readiness Challenge in Russia and around the world is educational. Reports from past world tournaments can be found here . I wanted to cover the regions as much as possible in the online round, because the offline part will be exactly in Moscow, and not everyone will be able to participate.
How to participate?
September 10, 2013 in Moscow will be held offline-championship, in which anyone interested over 18 years can take part. It will be somewhat more difficult - participants will be given four hours to penetrate the RK Industries network and prove or disprove its participation in the attack on a competitor.
Who would advise such a tournament?
Vlad Roskov : Ideal for beginners, a good warm-up for those who are stitched.
Andrei Leonov : I would advise such a tournament to those who are just starting their way in the field of information security without shame of conscience. This does not mean that the tournament was simple. But given the fact that the tasks in general followed one of the other, and there were clues, sometimes containing a complete answer, it was possible to gain a lot of new knowledge. Or understand where even the tips were not enough :)
Viktor Alyushin : I would recommend to absolutely everyone - from beginners to professional pinteresters and simply to those who want to try themselves in hacking. For the latter, I would advise you to make step by step instructions [especially for Metasploit], say for 110% of the cost of the task;).
Teymur Heirkhabarov : To all those who are not indifferent to the topic of information security, and in particular its practical side ... For the first time, I participated in such an event.
You can register for the offline part here . Places still have.
CROC Cyber Conference
In parallel, the conference will take place CROC Cyber Conference, where experts discuss information security issues. All activities are aimed at raising the awareness of the inhabitants of Russia about the importance of protecting confidential data.
Source: https://habr.com/ru/post/187554/
All Articles