How I studied in Informzaschita
Preface: This post is dedicated not so much to the learning process itself, but to some of the harsh everyday life of this training center in the context of the disciplines taught by it.

One wonderful evening, the thought was born, and not whether to go on information security courses in areas of interest, cook in a team, share experiences, gain some knowledge.
As a result of short throwing, the choice fell on the training center Informzaschity.
From advertising.
The list of training programs offered today by the Training Center (TC) includes more than 150 courses and comprehensive programs on information and economic security, more than 70% of which are author's unique programs in the following areas:
The teachers of the Informzaschita Training Center are practitioners and are engaged in research activities on topical security issues based on the seven laboratories of the Training Center. The results of research activities and practical experience of the specialists of the Training Center form the basis of the author's courses.
The first swallows.
')
Once in the audience of the training center, a suspicious ad was immediately noticed, on which the following was written: login: admin, password: 1111.
It turns out that these are credentials for logging into a personal computer, which is located at each training place. At the same time, in the process of studying, this computer acts only as a “reader”, a means of accessing the website of the training center.
Well, we include, inside WinXP, the peer-to-peer Workgroup network, and of course, full admin rights, which are undoubtedly vital for the site reader.
We go to the website of the training center, which asks to register to gain access to the material being taught.
During the registration process, a variety of personal data is requested, who you work with, e-mail, full name and so on. Immediately annoying that communication with the site goes through an open channel.

Paranoia screams and jerks its feet, so I immediately add https out of habit, but alas.

This implies that the portal can work from any place where there is Internet. For example, from such reliable and trusted sources as Internet cafes.
All right, we are going through a difficult stage of registration, the comrades in happiness, carefully filling the fields, are puffing up next to them. And here it is a long-awaited moment, we are on the site. A bunch of interesting menus, among which attracts attention section "My Groups". And what's inside? And inside there is the fruit of carefully filling in the fields with the personal data of each participant.
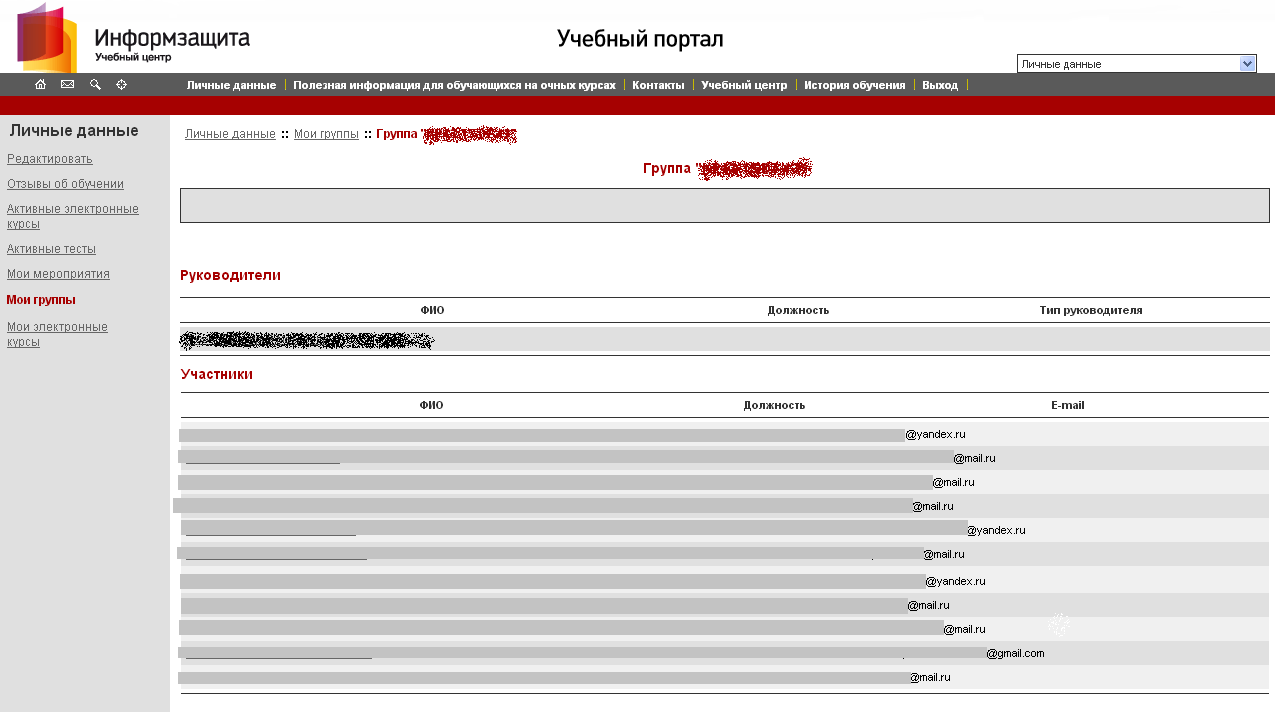
Of course, initially I was not going to give my neighbor my personal soap, I thought the soap was purely to restore the forgotten password, but the CA website made a choice for me, and indeed the Lord ordered it to be shared. And as we will see further, it will probably share not only with a good neighbor.
The farther into the forest ...
Okay. Listen to the course. We communicate with colleagues. Colleagues note the low speed of the portal, something slows down supposedly poor guy, albeit from the intranet. At some point, I stick a flash drive into the "reader" and pump the necessary material for study. Next, the flash drive wanders into a personal netbook with Linux, I am surprised to notice suddenly appeared new interesting files autorun.inf and xxx.vmx.
The "reader" instantly translates into the category of personal enemies, in connection with which there is a painful interest, what does it mean to spoil a flash drive?
At hand was only avz. We scan.
The first hit, an old acquaintance Kido / Confiker, and we were still amazed at the portal brakes. Got bred dear.

But still unknown to the animal. I really wanted to pick it out, but there was no lcd at hand, and it strongly resisted extraction to the living.
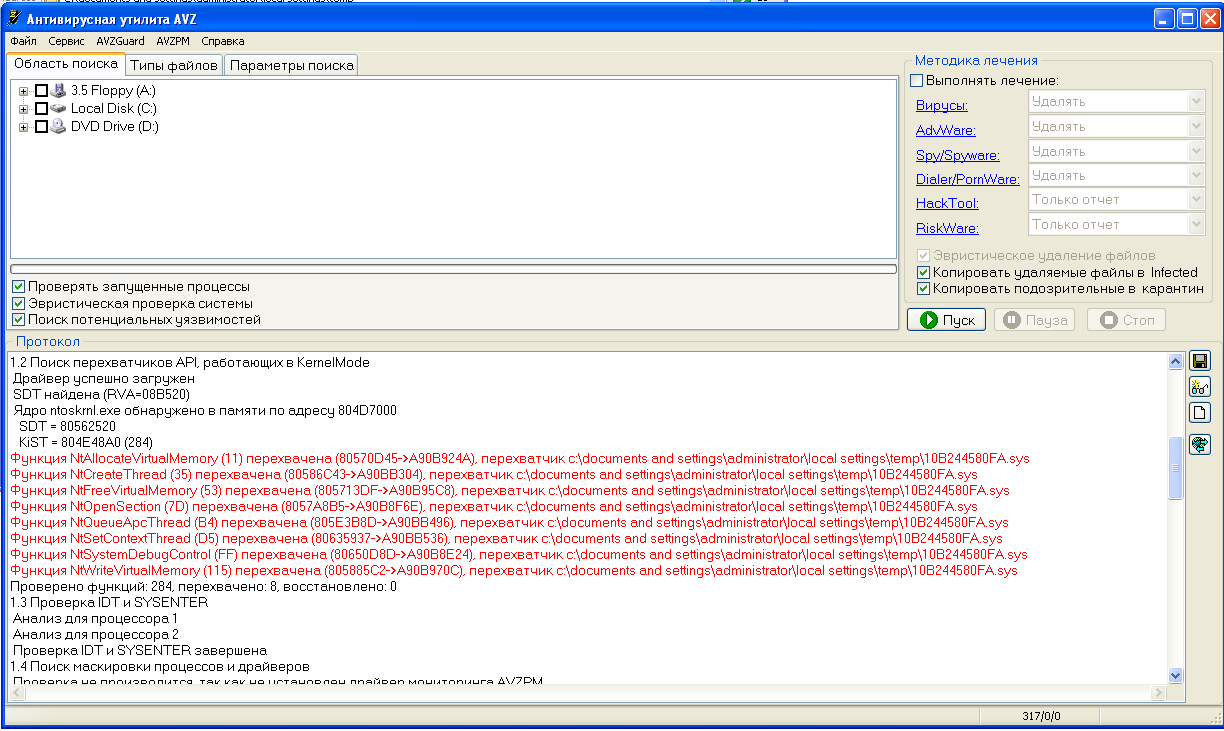
Paranoia screamed in a bad voice that it was all for a reason, that some evil spammer booths might have already added my soap to mailing lists or were preparing a targeted attack with my data.
A sober mind, notices that on the other hand, this is probably some kind of internal military development of local TC specialists to maintain the tone of the cadets. Collect, for example, statistics, and how many people will then infect their home computers? And how many corporate networks? Therefore, in particular, to facilitate the work of the combat load, outdated software and Axis are used on the "reader" without any unnecessary actual patches there. And even such a banality as an antivirus is not installed.

From such unrest, I clicked on the CA website for some unknown link and got to the disclosure of the ways.

I clicked another link and suddenly got lists of unknown people from parallel courses.

Something is not right in the Danish kingdom with the division of rights and error handling.
Then I notice that a certain network drive from a certain server is attached to the "reader". Well, if it glows in "My Computer", probably for the purposes necessary for training. Shake, asks for a password. Everything is as per instructions in the center of the board, carefully typing a complex combination of 1111. And, everything opens. What a good and universal password for everything.
Here such interesting things were noticed literally within several fascinating minutes.

One wonderful evening, the thought was born, and not whether to go on information security courses in areas of interest, cook in a team, share experiences, gain some knowledge.
As a result of short throwing, the choice fell on the training center Informzaschity.
From advertising.
The list of training programs offered today by the Training Center (TC) includes more than 150 courses and comprehensive programs on information and economic security, more than 70% of which are author's unique programs in the following areas:
The teachers of the Informzaschita Training Center are practitioners and are engaged in research activities on topical security issues based on the seven laboratories of the Training Center. The results of research activities and practical experience of the specialists of the Training Center form the basis of the author's courses.
The first swallows.
')
Once in the audience of the training center, a suspicious ad was immediately noticed, on which the following was written: login: admin, password: 1111.
It turns out that these are credentials for logging into a personal computer, which is located at each training place. At the same time, in the process of studying, this computer acts only as a “reader”, a means of accessing the website of the training center.
Well, we include, inside WinXP, the peer-to-peer Workgroup network, and of course, full admin rights, which are undoubtedly vital for the site reader.
We go to the website of the training center, which asks to register to gain access to the material being taught.
During the registration process, a variety of personal data is requested, who you work with, e-mail, full name and so on. Immediately annoying that communication with the site goes through an open channel.

Paranoia screams and jerks its feet, so I immediately add https out of habit, but alas.

This implies that the portal can work from any place where there is Internet. For example, from such reliable and trusted sources as Internet cafes.
All right, we are going through a difficult stage of registration, the comrades in happiness, carefully filling the fields, are puffing up next to them. And here it is a long-awaited moment, we are on the site. A bunch of interesting menus, among which attracts attention section "My Groups". And what's inside? And inside there is the fruit of carefully filling in the fields with the personal data of each participant.

Of course, initially I was not going to give my neighbor my personal soap, I thought the soap was purely to restore the forgotten password, but the CA website made a choice for me, and indeed the Lord ordered it to be shared. And as we will see further, it will probably share not only with a good neighbor.
The farther into the forest ...
Okay. Listen to the course. We communicate with colleagues. Colleagues note the low speed of the portal, something slows down supposedly poor guy, albeit from the intranet. At some point, I stick a flash drive into the "reader" and pump the necessary material for study. Next, the flash drive wanders into a personal netbook with Linux, I am surprised to notice suddenly appeared new interesting files autorun.inf and xxx.vmx.
The "reader" instantly translates into the category of personal enemies, in connection with which there is a painful interest, what does it mean to spoil a flash drive?
At hand was only avz. We scan.
The first hit, an old acquaintance Kido / Confiker, and we were still amazed at the portal brakes. Got bred dear.

But still unknown to the animal. I really wanted to pick it out, but there was no lcd at hand, and it strongly resisted extraction to the living.

Paranoia screamed in a bad voice that it was all for a reason, that some evil spammer booths might have already added my soap to mailing lists or were preparing a targeted attack with my data.
A sober mind, notices that on the other hand, this is probably some kind of internal military development of local TC specialists to maintain the tone of the cadets. Collect, for example, statistics, and how many people will then infect their home computers? And how many corporate networks? Therefore, in particular, to facilitate the work of the combat load, outdated software and Axis are used on the "reader" without any unnecessary actual patches there. And even such a banality as an antivirus is not installed.

From such unrest, I clicked on the CA website for some unknown link and got to the disclosure of the ways.

I clicked another link and suddenly got lists of unknown people from parallel courses.

Something is not right in the Danish kingdom with the division of rights and error handling.
Then I notice that a certain network drive from a certain server is attached to the "reader". Well, if it glows in "My Computer", probably for the purposes necessary for training. Shake, asks for a password. Everything is as per instructions in the center of the board, carefully typing a complex combination of 1111. And, everything opens. What a good and universal password for everything.
Here such interesting things were noticed literally within several fascinating minutes.
Source: https://habr.com/ru/post/187266/
All Articles