Malefactors more actively use Win32 / Bicololo
In our ranking of threats this year, the Win32 / Bicololo Trojan is present in all monthly reports with various activity statistics. Despite the fact that the threat activity tends to decline over the past few months, we recorded an increase in the number of malicious links that are used to install this malware. Such links are masked as graphic files.
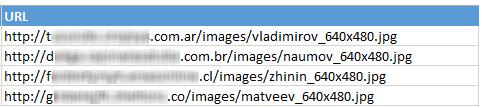
Similar links were sent by attackers in various social services and messengers. When you click on the link, the browser prompts the user to save the file on the hard disk, while you may notice that the download file has the extension .scr , and not .jpg . When you run such a screen saver file, you can see that the changes it makes to the system (including modifying the system hosts file) hint at the potential malicious actions of this program.
')
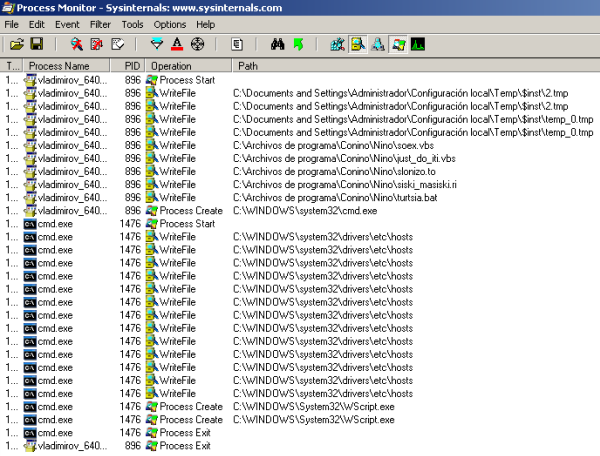
It can be seen that the malicious process created creates several temporary files, as well as 5 auxiliary files. Two files are scripts in Visual Basic Script. After writing the files, it creates an auxiliary process for executing the command line interpreter to execute the created batch file. This batch file turtsia.bat launches the first script, soex.vbs. To do this, use the built-in tool wscript.exe.

The ProcMon log shows that this script does not perform any significant actions. Next is the execution of the second script just_do_iti.vbs. It installs malicious code into the startup item, creates additional files necessary for work and finishes.
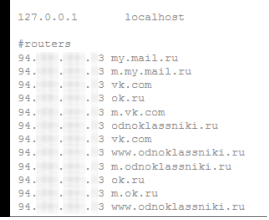
Next, the hosts file is modified to redirect social services. networks on phishing resources.
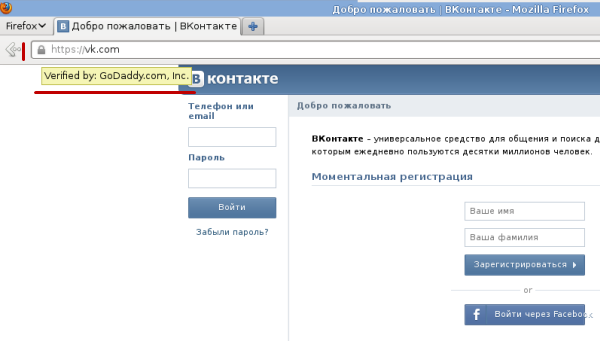
As a result of this operation, the user is redirected to a page very similar to the original when visiting the VKontakte social network. The differences lie in the impossibility of changing the language and the impossibility of switching to https without information about the certificate. Below is such a phishing page.
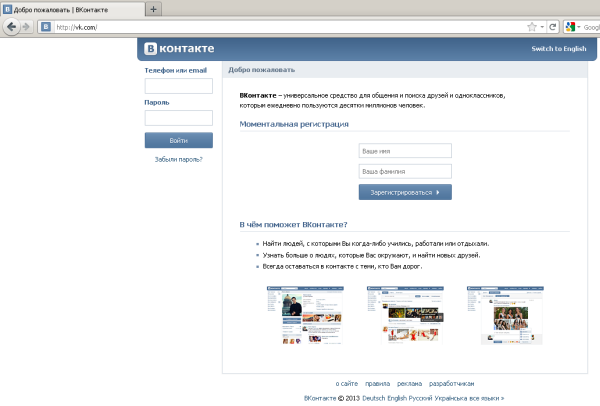
At the same time on the original site you can go to https without any problems.
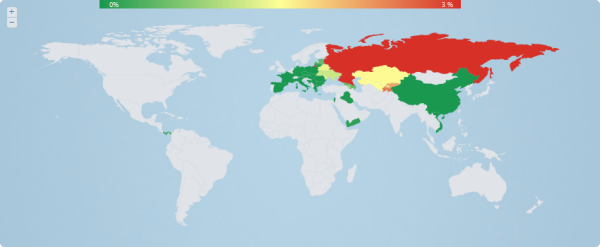
It should be noted that Win32 / Bicololo is focused specifically on Russia; this is evident from the social services targeted by the malicious code, as well as its geography of distribution.
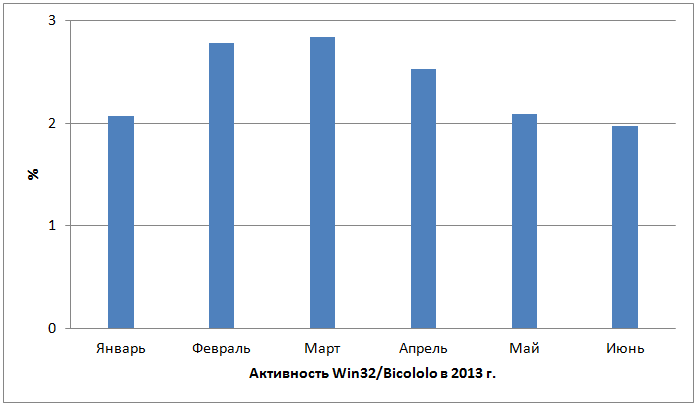
Below is the statistics of Bicololo activity in 2013.

Similar links were sent by attackers in various social services and messengers. When you click on the link, the browser prompts the user to save the file on the hard disk, while you may notice that the download file has the extension .scr , and not .jpg . When you run such a screen saver file, you can see that the changes it makes to the system (including modifying the system hosts file) hint at the potential malicious actions of this program.
')

It can be seen that the malicious process created creates several temporary files, as well as 5 auxiliary files. Two files are scripts in Visual Basic Script. After writing the files, it creates an auxiliary process for executing the command line interpreter to execute the created batch file. This batch file turtsia.bat launches the first script, soex.vbs. To do this, use the built-in tool wscript.exe.

The ProcMon log shows that this script does not perform any significant actions. Next is the execution of the second script just_do_iti.vbs. It installs malicious code into the startup item, creates additional files necessary for work and finishes.
Next, the hosts file is modified to redirect social services. networks on phishing resources.

As a result of this operation, the user is redirected to a page very similar to the original when visiting the VKontakte social network. The differences lie in the impossibility of changing the language and the impossibility of switching to https without information about the certificate. Below is such a phishing page.

At the same time on the original site you can go to https without any problems.

It should be noted that Win32 / Bicololo is focused specifically on Russia; this is evident from the social services targeted by the malicious code, as well as its geography of distribution.

Below is the statistics of Bicololo activity in 2013.

Source: https://habr.com/ru/post/186642/
All Articles