Protection against listening to SIP using - TLS + SRTP + encrypted tunnel and Yealink T26p phone

Are you paranoid? It seems to you that they constantly want to overhear you? Do you have important negotiations? Then you here!
In this post I will discuss the main difficulties in setting up your Yealink T26p phone.
To begin with, we will make the phone pick up an encrypted tunnel with certificates to the OpenVPN server, and then run inside the SIP tunnel with encrypted signaling and voice! (TLS + SRTP).
Who cares please under the cat.
For a start, I propose to get acquainted with the work scheme.
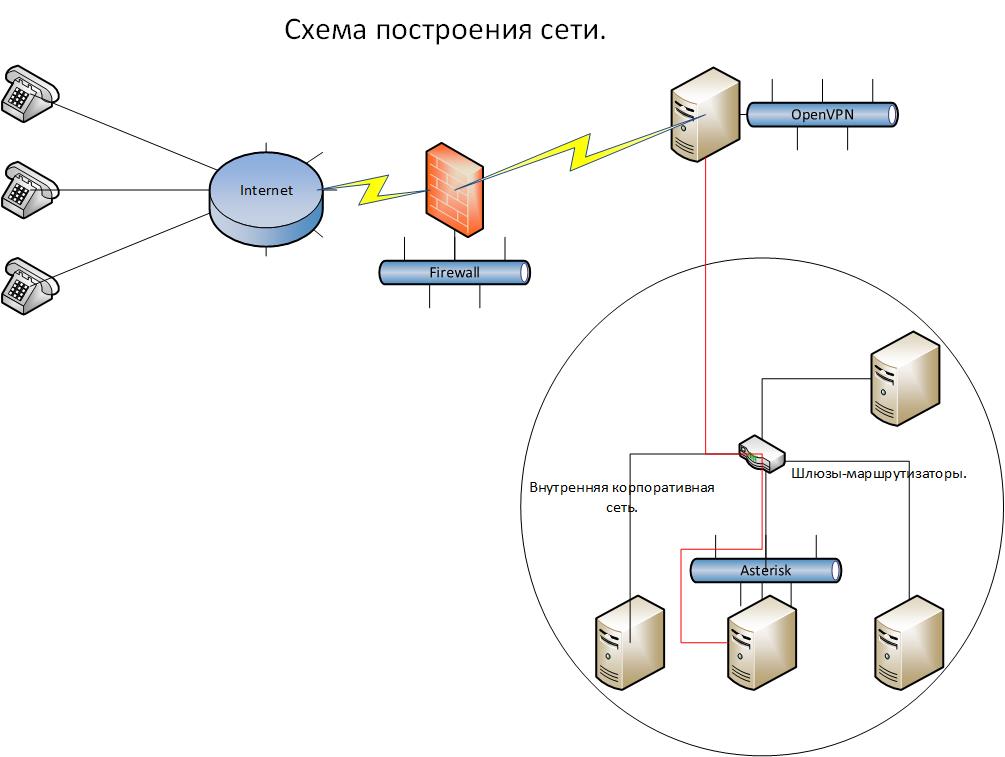
The meaning of work in the following - the phones are connected from anywhere via the Internet. They raise the encrypted channel to the only OpenVPN server sticking into the world of the port. And then from this server telephony goes to the depths of the corporate network, to the Asterisk server hidden there. But as you can see, the channel to the OpenVPN server is encrypted, but inside the corporate network where there are a lot of staff, you can intercept SIP traffic on any of the gateways and then decrypt it and find out what the conversation was about! This piece of the network is specially marked with a red line. Therefore, we will configure SRTP + TLS on the asterisk and will also encrypt the traffic inside the network so that it is protected from unscrupulous company employees. Thus, the circle of persons having access to conversations is greatly narrowed.
To install the OpenVPN server, I used a Centos 6.4 dvd image. The installation will not stop, everything is standard.
')
We fix the locale glitch right away.
export LC_CTYPE=en_US.UTF-8 Enable forwarding on network interfaces.
nano /etc/sysctl.conf # net.ipv4.ip_forward = 1 We include loading the network interface at startup.
nano /etc/sysconfig/network-scripts/ifcfg-eth0 # . ONBOOT=yes We update CentOS.
cd /usr/src/ yum update -y Add the desired repository.
wget http://fedora.ip-connect.vn.ua/fedora-epel/6/i386/epel-release-6-8.noarch.rpm rpm -Uvh epel-release-6-8.noarch.rpm We put the required packages.
yum install openvpn git bridge-utils -y EasyRSA is now separate and on githaba - therefore:
git clone https://github.com/OpenVPN/easy-rsa.git cp -r /usr/src/easy-rsa/easy-rsa /etc/openvpn/ I advise you to copy the original VPN configuration for subsequent additions and changes and comment out all the lines there, then it will be convenient to look for the necessary commands to add and their syntax.
cp /usr/share/doc/openvpn-2.3.1/sample/sample-config-files/server.conf /etc/openvpn/ nano /etc/openvpn/server.conf # , : port 1194 proto udp dev tun0 ca /etc/openvpn/easy-rsa/2.0/keys/ca.crt cert /etc/openvpn/easy-rsa/2.0/keys/server.crt key /etc/openvpn/easy-rsa/2.0/keys/server.key dh /etc/openvpn/easy-rsa/2.0/keys/dh1024.pem server 172.19.7.0 255.255.255.0 ifconfig-pool-persist ipp.txt push "route 172.19.7.0 255.255.255.0" keepalive 10 120 user root group root persist-key persist-tun status openvpn-status.log log /var/log/openvpn.log verb 3 mute 20 comp-lzo no Change the encryption method from sha256 to MD5. The phone does not understand the first method. In the easy-rsa assembly there are 3 options for the openssl file, we will change them all at once so as not to find out which system will be used when generating keys and certificates.
cp /etc/openvpn/easy-rsa/2.0/openssl-0.9.6.cnf /etc/openvpn/easy-rsa/2.0/openssl-0.9.6.cnf.orig && sed -e 's/default_md.*=.*sha256/default_md = md5 /g' /etc/openvpn/easy-rsa/2.0/openssl-0.9.6.cnf.orig > /etc/openvpn/easy-rsa/2.0/openssl-0.9.6.cnf cp /etc/openvpn/easy-rsa/2.0/openssl-0.9.8.cnf /etc/openvpn/easy-rsa/2.0/openssl-0.9.8.cnf.orig && sed -e 's/default_md.*=.*sha256/default_md = md5 /g' /etc/openvpn/easy-rsa/2.0/openssl-0.9.8.cnf.orig > /etc/openvpn/easy-rsa/2.0/openssl-0.9.8.cnf cp /etc/openvpn/easy-rsa/2.0/openssl-1.0.0.cnf /etc/openvpn/easy-rsa/2.0/openssl-1.0.0.cnf.orig && sed -e 's/default_md.*=.*sha256/default_md = md5 /g' /etc/openvpn/easy-rsa/2.0/openssl-1.0.0.cnf.orig > /etc/openvpn/easy-rsa/2.0/openssl-1.0.0.cnf Next, change the default values
nano /etc/openvpn/easy-rsa/2.0/vars export KEY_SIZE=1024 export KEY_COUNTRY="RU" export KEY_PROVINCE="CA" export KEY_CITY="Moscow" export KEY_ORG="YOURCOMPANY" export KEY_EMAIL="info@YOURCOMPANY.ru" export KEY_OU="MY" You can start generating certificates:
Go to the desired directory where we will generate keys and certificates.
cd /etc/openvpn/easy-rsa/2.0 [root@test 2.0]# source ./vars NOTE: If you run ./clean-all, I will be doing a rm -rf on /etc/openvpn/easy-rsa/2.0/keys [root@test 2.0]# ./clean-all # , , Common Name [root@test 2.0]# ./build-ca Generating a 1024 bit RSA private key .........++++++ .......................++++++ writing new private key to 'ca.key' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [RU]: State or Province Name (full name) [CA]: Locality Name (eg, city) [Moscow]: Organization Name (eg, company) [YOURCOMPANY]: Organizational Unit Name (eg, section) [changeme]: Common Name (eg, your name or your server's hostname) [changeme]:test Name [changeme]: Email Address [mail@host.domain]: Create a certificate and key for the server
All answers can be left by default.
[root@test 2.0]# ./build-key-server server Generating a 1024 bit RSA private key .........................++++++ .............................++++++ writing new private key to 'server.key' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [RU]: State or Province Name (full name) [MOSCOW]: Locality Name (eg, city) [MOSCOW]: Organization Name (eg, company) [YOURCOMPANY]: Organizational Unit Name (eg, section) [changeme]: Common Name (eg, your name or your server's hostname) [server]: Name [changeme]: Email Address [mail@host.domain]: Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []: Using configuration from /etc/openvpn/easy-rsa/2.0/openssl-0.9.8.cnf Check that the request matches the signature Signature ok The Subject's Distinguished Name is as follows countryName :PRINTABLE:'RU' stateOrProvinceName :PRINTABLE:'MOSCOW' localityName :PRINTABLE:'MOSCOW' organizationName :PRINTABLE:'YOURCOMPANY' organizationalUnitName:PRINTABLE:'changeme' commonName :PRINTABLE:'server' name :PRINTABLE:'changeme' emailAddress :IA5STRING:'mail@host.domain' Certificate is to be certified until Mar 20 06:56:48 2023 GMT (3650 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated We generate the Diffie-Hellman key
[root@test 2.0]# ./build-dh Generating DH parameters, 1024 bit long safe prime, generator 2 This is going to take a long time ...................................................+.................................................................+...................+..+.........................................................................................................................................+...........+.......................................................+....+..................................................................................................+......................................................................+.................................................................................................+............................+.....................................................................+.............++*++*++* We generate a client key (for each car or phone it must be its own)
All answers are left by default.
[root@test 2.0]# ./build-key client1 Generating a 1024 bit RSA private key .++++++ ......++++++ writing new private key to 'client1.key' ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [RU]: State or Province Name (full name) [CA]: Locality Name (eg, city) [Moscow]: Organization Name (eg, company) [YOURCOMPANY]: Organizational Unit Name (eg, section) [changeme]: Common Name (eg, your name or your server's hostname) [client1]: Name [changeme]: Email Address [mail@host.domain]: Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []: Using configuration from /etc/openvpn/easy-rsa/2.0/openssl-0.9.8.cnf Check that the request matches the signature Signature ok The Subject's Distinguished Name is as follows countryName :PRINTABLE:'RU' stateOrProvinceName :PRINTABLE:'CA' localityName :PRINTABLE:'Moscow' organizationName :PRINTABLE:'YOURCOMPANY' organizationalUnitName:PRINTABLE:'changeme' commonName :PRINTABLE:'client1' name :PRINTABLE:'changeme' emailAddress :IA5STRING:'mail@host.domain' Certificate is to be certified until Mar 20 07:01:46 2023 GMT (3650 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated Preparing the file for connecting the phone:
Create a folder - inside there should be a keys folder and a vpn.cnf file.
Example vpn.cnf - instead of XXX, of course your server address is:
client dev tun proto udp remote XXX.XXX.XXX.XXX 1194 resolv-retry infinite nobind ca /yealink/config/openvpn/keys/ca.crt cert /yealink/config/openvpn/keys/client1.crt key /yealink/config/openvpn/keys/client1.key verb 3 mute 20 comp-lzo no Inside the keys folder there should be three files respectively - ca.crt, client1.crt, client1.key. File names in the config and in the folder must match. Files pull from the server after generation in any convenient way.
After that we put 7zip and archive the vpn.cnf file and the keys folder in the tar archive without compression. Or you can run on Linux from the folder with the vpn.cnf file and the keys folder:
tar cvf connect.tar ./vpn.cnf ./keys Go to the phone's web interface. Go to the tab Network> Advanced> Vpn. We set active = enabled, import the file and click submit at the bottom.
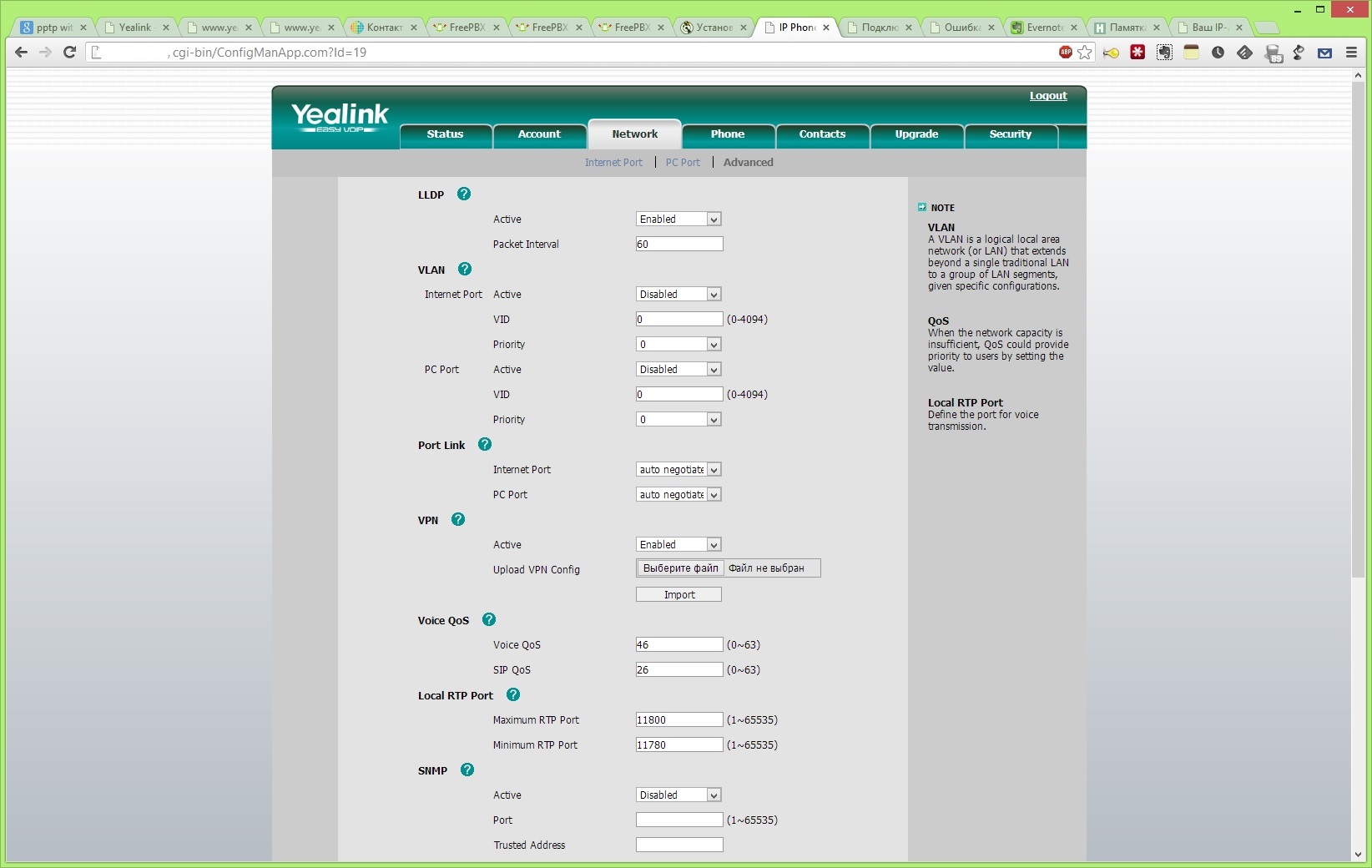
If the phone did not skip the file, you can reboot it. See that he has connected to our server by looking at the logs:
tail -n100 -f /var/log/openvpn.log Configure TLS + SRTP on Asterisk.
I will not write a setting from scratch for there are lots of articles, and mine too. I'll tell you how to make certificates, enable encryption and shove it all into the phone.
So on aster you need to make a Certificate Authority.
mkdir /etc/cert cd /etc/cert/ root@server-sip1:/etc/cert# openssl genrsa -des3 -out ca.key 4096 Generating RSA private key, 4096 bit long modulus .......................++ ...............................++ e is 65537 (0x10001) Enter pass phrase for ca.key: Verifying - Enter pass phrase for ca.key: root@server-sip1:/etc/cert# root@server-sip1:/etc/cert# root@server-sip1:/etc/cert# openssl req -new -x509 -days 365 -key ca.key -out ca.crt Enter pass phrase for ca.key: You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [AU]:RU State or Province Name (full name) [Some-State]:MOSCOW Locality Name (eg, city) []:MOSCOW Organization Name (eg, company) [Internet Widgits Pty Ltd]:YOURCOMPANY Organizational Unit Name (eg, section) []:VoIP Common Name (eg, YOUR name) []:YUORCOMPANY CA Email Address []:INFO@YOURCOMPANY.RU root@server-sip1:/etc/cert# root@server-sip1:/etc/cert# root@server-sip1:/etc/cert# ls ca.crt ca.key root@server-sip1:/etc/cert# CA created - then you need to load the ca.crt file into your phone so that it knows that this CA can be trusted - the Security> Trusted Certificates tab.

I describe the creation and signing of the server certificate and for phones for the server, and repeat the procedure for the phone.
root@server-sip1:/etc/cert# openssl genrsa -out key-server.pem 1024 Generating RSA private key, 1024 bit long modulus .....++++++ ...++++++ e is 65537 (0x10001) root@server-sip1:/etc/cert# openssl req -new -key key-server.pem -out req-server.csr You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [AU]:RU State or Province Name (full name) [Some-State]:MOSCOW Locality Name (eg, city) []:MOSCOW Organization Name (eg, company) [Internet Widgits Pty Ltd]:YOURCOMPANY Organizational Unit Name (eg, section) []:VoIP Common Name (eg, YOUR name) []:server Email Address []:info@yourcompany.ru Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []: root@server-sip1:/etc/cert# root@server-sip1:/etc/cert# root@server-sip1:/etc/cert# root@server-sip1:/etc/cert# openssl x509 -req -days 365 -in req-server.csr -CA ca.crt -CAkey ca.key -set_serial 01 -out cert-server.crt Signature ok subject=/C=RU/ST=MOSCOW/L=MOSCOW/O=Yourcompany/OU=VoIP/CN=server/emailAddress=info@yourcompany.ru Getting CA Private Key Enter pass phrase for ca.key: root@server-sip1:/etc/cert# Preparing a certificate for Asterisk.
The file structure for an aster should look like this — first, the certificate file of the following form:
-----BEGIN CERTIFICATE----- MIIDvDCCAyWgAwIBAgIJAPMabsMiJJQPMA0GCSqGSIb3DQEBBQUAMIGbMQswCQYD [...] CfITDxcJBZfeXIPZP52+8FSMlm5985uMvao+emlIUGk11rY61Amxr387grDvgOaI -----END CERTIFICATE----- Then immediately the key file:
-----BEGIN RSA PRIVATE KEY----- MIICXQIBAAKBgQCqRw0jpQFn+f+lnDZiZzCRca9ojgu2brO+Q56jnqorvCIlYFC0 [...] FT65O46u6Vmp1gPbNklOEg7TtZUtfacPY2PyeP4KoHaG -----END RSA PRIVATE KEY----- You can build through cat:
root@server-sip1:/etc/asterisk/cert# cat /etc/cert/key.pem > /etc/asterisk/cert/asterisk.pem root@server-sip1:/etc/asterisk/cert# cat /etc/cert/cert-server.crt >> /etc/asterisk/cert/asterisk.pem Now we register in the sip.conf file (or sip_general_custom.conf if it is Elastix or FreePBX)
tcpenable=yes tcpbindaddr=0.0.0.0 tlsenable=yes tlsbindaddr=0.0.0.0 tlscertfile=/etc/asterisk/cert/asterisk.pem tlscafile=/etc/cert/ca.crt When everything is ready, you need to enable TLS and SRTP on a specific extension.
In the same way, we prepare a file for the phone and load it in the Security> Server Certificates menu.

This article in no way want to claim the completeness of the material. But I really wanted to bring these important nuances to the settings for a person who might later face this. It took me a week to clear up all the nuances of extracting and preparing certificates for a phone and an asterisk. If you have any suggestions how to do it - better \ faster \ more correctly, then I’ll read with pleasure in the comments!
Update. When setting up a Business HD IP DECT Phone, the W52P revealed a feature for uploading configs to it. It is necessary to prescribe in the paths without "/ yealink":
ca /config/openvpn/keys/ca.crt cert /config/openvpn/keys/client1.crt key /config/openvpn/keys/client1.key In addition, I would like to say that the Business HD IP DECT Phone W52P phone in the Asterisk password on the extension understands the "&" symbol, and the Yealink T26p phone does not understand.
For better stability in the phone, the Accounts tab has changed the Login expire to 600 and Subscribe period 300.
Source: https://habr.com/ru/post/186530/
All Articles