Vulnerability in Android allows attackers to turn any application into a trojan
The Bluebox Security Labs research team recently discovered a vulnerability in the Android security model that allows you to change the .apk application code without damaging the application's cryptographic signature. Thus, you can turn any signed application into a Trojan program. And absolutely no one will notice the substitution. Neither the Play Market, nor the phone, nor the user.
This vulnerability has been present since the Android 1.6 version of “Donut” or, in other words, on any phone purchased not later than 4 years ago. Or it is almost 900 million devices. Depending on the type of application, attackers can use the vulnerability to steal data or create a mobile botnet.

For individuals and enterprises (a malicious application can access individual data, or penetrate enterprises), the danger is quite great, especially considering that applications developed by manufacturers of devices (for example, HTC, Samsung, Motorola, LG) or third parties who work in collaboration with the device manufacturer, have special privileges in Android.
Embedding the code into the application from the device manufacturer can provide full access to the Android system and all installed applications (or their data). The application will then have the opportunity not only to read arbitrary application data on the device (email, SMS messages, documents, etc.), but also there will be a chance to get access to the saved passwords. And it will not interfere with the normal functioning of the phone and control of any function (make arbitrary phone calls, send random SMS messages, turn on the camera and record the call). Finally, you can create a whole botnet.
')

How it works:
All Android applications have cryptographic signatures that allow the Android operating system to determine and check whether the program code has interfered or not. When the application is installed, a sandbox is created for it, Android records the digital signature of this application. All subsequent updates for the application must match this signature to verify that it is from the same author.
The vulnerability exploits a mismatch that is allowed when modifying an APK application without damaging the application's cryptographic signature. In simple terms, the vulnerability allows Android to be tricked and he will think that the application has not been changed.

In his presentation, Jeff will talk about bug 8219321 on the Android OS, which he reported to Google in February of this year, and an exploit that works on almost all Android devices, regardless of their age.
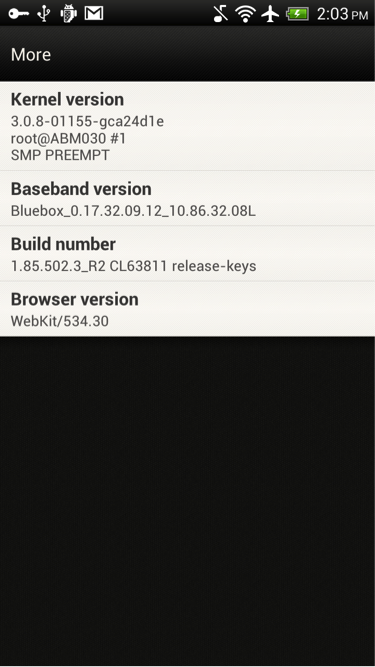
The screenshot shows that Bluebox Security has changed the application from the manufacturer so that they now have full access to the device. In this case, the company has changed the device software information.
Malicious users can use a variety of methods to distribute such Trojan applications, including sending them by e-mail, uploading them to a third-party Market, and posting them on any website. Some of these methods, especially third-party application repositories, are already being used to distribute malicious Android software. Using Google Play to distribute the application that has been changed - will not work. Because Google has updated the process of writing an application to the Market in order to block applications that contain this problem.
By the way, Google was notified of the vulnerability back in February, and the company shared information with their partners. And now partners need to decide when to release an update for devices. Forristal confirmed that one device, the Samsung S4, already has a patch that demonstrates that some device manufacturers have already started to release patches. Google has not yet released a patch for its Nexus devices, but the company is working on it.
If you do not have an account on Habrahabr, you can read and comment on our articles on BoxOverview.com
This vulnerability has been present since the Android 1.6 version of “Donut” or, in other words, on any phone purchased not later than 4 years ago. Or it is almost 900 million devices. Depending on the type of application, attackers can use the vulnerability to steal data or create a mobile botnet.

For individuals and enterprises (a malicious application can access individual data, or penetrate enterprises), the danger is quite great, especially considering that applications developed by manufacturers of devices (for example, HTC, Samsung, Motorola, LG) or third parties who work in collaboration with the device manufacturer, have special privileges in Android.
Embedding the code into the application from the device manufacturer can provide full access to the Android system and all installed applications (or their data). The application will then have the opportunity not only to read arbitrary application data on the device (email, SMS messages, documents, etc.), but also there will be a chance to get access to the saved passwords. And it will not interfere with the normal functioning of the phone and control of any function (make arbitrary phone calls, send random SMS messages, turn on the camera and record the call). Finally, you can create a whole botnet.
')

How it works:
All Android applications have cryptographic signatures that allow the Android operating system to determine and check whether the program code has interfered or not. When the application is installed, a sandbox is created for it, Android records the digital signature of this application. All subsequent updates for the application must match this signature to verify that it is from the same author.
The vulnerability exploits a mismatch that is allowed when modifying an APK application without damaging the application's cryptographic signature. In simple terms, the vulnerability allows Android to be tricked and he will think that the application has not been changed.

In his presentation, Jeff will talk about bug 8219321 on the Android OS, which he reported to Google in February of this year, and an exploit that works on almost all Android devices, regardless of their age.
The screenshot shows that Bluebox Security has changed the application from the manufacturer so that they now have full access to the device. In this case, the company has changed the device software information.

Malicious users can use a variety of methods to distribute such Trojan applications, including sending them by e-mail, uploading them to a third-party Market, and posting them on any website. Some of these methods, especially third-party application repositories, are already being used to distribute malicious Android software. Using Google Play to distribute the application that has been changed - will not work. Because Google has updated the process of writing an application to the Market in order to block applications that contain this problem.
By the way, Google was notified of the vulnerability back in February, and the company shared information with their partners. And now partners need to decide when to release an update for devices. Forristal confirmed that one device, the Samsung S4, already has a patch that demonstrates that some device manufacturers have already started to release patches. Google has not yet released a patch for its Nexus devices, but the company is working on it.
If you do not have an account on Habrahabr, you can read and comment on our articles on BoxOverview.com
Source: https://habr.com/ru/post/185516/
All Articles