So, you decided to create a security department ...
This article answers the question of what he should do and how, with all the intimate details. It is understood that there is a project (startup) with a web part that worked for some time without security testing, but for some reason decided to implement it. For the last 2 years I have been working security in a startup with very large clients (a startup is one of the leaders in the world in its field), and I’m sure I have something to say on this topic (of course, all the information below is just my ideas, approaches and thoughts, and not howto guide and not one step to the side). The article is dedicated to interested bosses, PMs, as well as a person who will be referred to as Security Testing Team Lead and create a similar department from scratch.

So, you decided to create a security department ...
My congratulations, even if you just thought about it (and it’s quite cool if you take this moment into account when you hire new employees, wrote about it ). Break everything and everywhere, and more and more. Nowadays, a business can really shake from information leaks (including user leaks). Last year, full access to LinkedIN, Stratfor, Gamigo, NVidia, Adobe, eHarmony, Blizzard and many others. But for example, yesterday Ubi was hacked, did you hear ? Although, not surprisingly, they write that they have vulnerabilities right on the password change page

Well, okay, let's get down to business. And so, in the company there is a man-security. Of course, he is a specialist who, first of all, owns the skills of pentest and can perform this work. Also, some team management skills, knowledge of CI systems, as well as redmails or similar things (depends on the specifics of the project, but in general, similar approaches are everywhere). What should he do?
First month - second
Start testing everything yourself, and in blackbox mode. We receive the list of projects (their domains). Perhaps a list of IP addresses of all servers that are involved in the project (will reduce the time for exploration). And we begin to test.
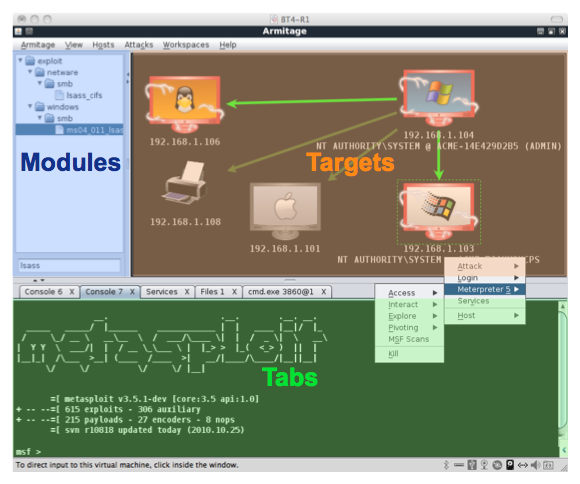
First, network services . We scan ports, arm ourselves with msf + armitage, check all exploits, configuration of dns server ( axfr , dns replay attack), web server . We test the “weak” accounts, not forgetting to use the startupname: startupname and similar pairs. In general, we are trying to make our way through the network in full, we don’t touch the web (if only during breaks). Along the way, we write down to ourselves all the used software (nginx / apache / pgsql). We will use this info later. I just have a text file with IPs and nmap results.
')
Weekdays
Once finished, reportable, with the administrator all corrected moved to the web. And so, we need a quick, but more or less high-quality detour. We use various scanners that will allow us to test the resource "in the forehead", and maybe even find something. We arm the burp-suite and go explore the functionality. Everywhere we endlessly send a universal xss vector (the thing is old, but which one):
Hidden text
"> [img = 1] <img - / style = - = expression (/ * '/ - / *', / ** / eval (name) //); width: 100%; height: 100%; position: absolute; behavior: url (# default # VML); - o-link: javascript: eval (title); - o-link-source: current name = alert (1) onerror = eval (name) src = 1 autofocus onfocus = eval (name) onclick = eval (name) onmouseover = eval (name) background = javascript: eval (name) //> "javascript:/*-->We look at various parameters that could be easily replaced or enumerate, in general we are looking for some obvious parameter tampering . There we also pay special attention to file uploading. We try the slave-unknown files (for example, in the case of php scripts with mime type jpg or png (idat chunks)). Quotes everywhere in a row. In general, it's not for me to talk about this here, everyone has their own techniques. We expect, by the way (depending on the scale of the project) what time we spend on a sort of “good luck”, for example - 10 working days.
Putting it all together, maybe something will find such that it will be necessary to "twist". In general, we spend this time on attacks "in the forehead" and correct everything that the attacker would find, having no relation to the company (as a fact, not knowing much about it). It is most likely that the most critical bugs will be found and corrected during this period.
Third month sixth
For a month or two we can study the project, understand its logic and work. And we begin to take root in the development ... Whitebox in all its glory.
Much depends on the workflow in the project. The main idea of the implementation is to implement security code review and / or security testing features that are being prepared for the next release. New -> in progress -> done -> in testing -> tested -> security in testing -> security tested . The moment is that one person simply does not cope with testing the security of all features (it is obvious), so for now (if we haven’t taken anyone yet) we are testing only critical things (we evaluate them subjectively).
Here, before each release, you can do a full diff with the production server and watch all the new written code. Very useful.
And here we start no longer in the “crazy” mode, but more calmly and measuredly, dividing the functional in parts to test it. Every parameter, every ajax request and especially any forgotten things that no one uses and that were written by the developer who quit about 2 years ago (usually quite a few mistakes are made at the beginning of the development, since everything is “urgent, urgent, release soon!”) . At this stage, the leadership of the security team lead should not expect the same "booms" as in the first 2 months of work.
Month six + or we took someone else
At the moment when we decide that we have free time (the project as a whole is covered with tests, the source code has already been received and its analysis has been carried out, in the database where you need to add salt, everywhere you have “cut out” md5, etc.) we try to automate We introduce our work and implement security auto tests that we can create on the basis of various scanners (for example, nmap - we saved everything to the database, if we change the port state the next time we launch, we report in the report). Screw webui to w3af from Yandex (by the way, I did not use it myself). In general, we begin to write code and this is normal (although the position is not a programmer).
If there is still a person (and maybe not one), and if people are creative, we discuss it in order to check on the project. And so - we delegate to them a part (or all) of the work for 3-6 months (sometimes remembering to check what and how), expanding the set of autotests and not only.
Well, the office staff. We read , we apply. If possible, do a mass mailing about the need to update some kind of plugin / browser, if required.
Throughout the time
We train personnel (mostly developers, point out their mistakes, expand their horizons, etc.), monitor exploits (remember, did we record all the software in the first two months of work?), Look at the reports of the scanners implemented in CI development, constantly, constantly (!) we read new news and twitter of various security people and companies (or just different news aggregators), attend / speak at conferences (PHDays / ZN at least, if we take the RF), we play CTF. Perhaps a period of some “freebies”, but most often there is (or is invented by ourselves) some kind of new technology that needs to be urgently checked on the project. We support security from all sides and assign periods of “complete crawling”. When with a fresh head, as if for the first time, the whole project costs again (see month 1-2).
Generally
Many moments depend on the project, but according to my personal feelings that if you organize the work, as I described above, it will turn out efficiently (and there will be no similar reviews about it). Efficiency is expressed in lowering the risks to the security of a resource and its users. In monetary terms, security is quite difficult (although there are methods).
And as a small advertisement, if you know any interesting start-up / project / company in St. Petersburg (or distance), where (possibly) you need such a person, or a QA with such "inclinations", or a recorder, ready to learn and develop then let me know (I will be grateful), looking for work and various options. Or simply if you have something to say on the topic of job search, then write too :-)
Startups with dev-offices and worthy sn, ready to hire citizens of non-Russian Federation in St. Petersburg almost do not know (preferably working for foreign countries, I don’t want to give up constant communication in English).
Thank you for your attention and reading, I will be glad to discuss the article and expand my views on the organization of such a process.
Source: https://habr.com/ru/post/185402/
All Articles