Carberp source leaks are a big hit to user security.
It is no longer a secret that the full source code of the famous banking malware Carberp leaked to the public. About 5GB of source code were in the field of view of virtually anyone. Archive includes:
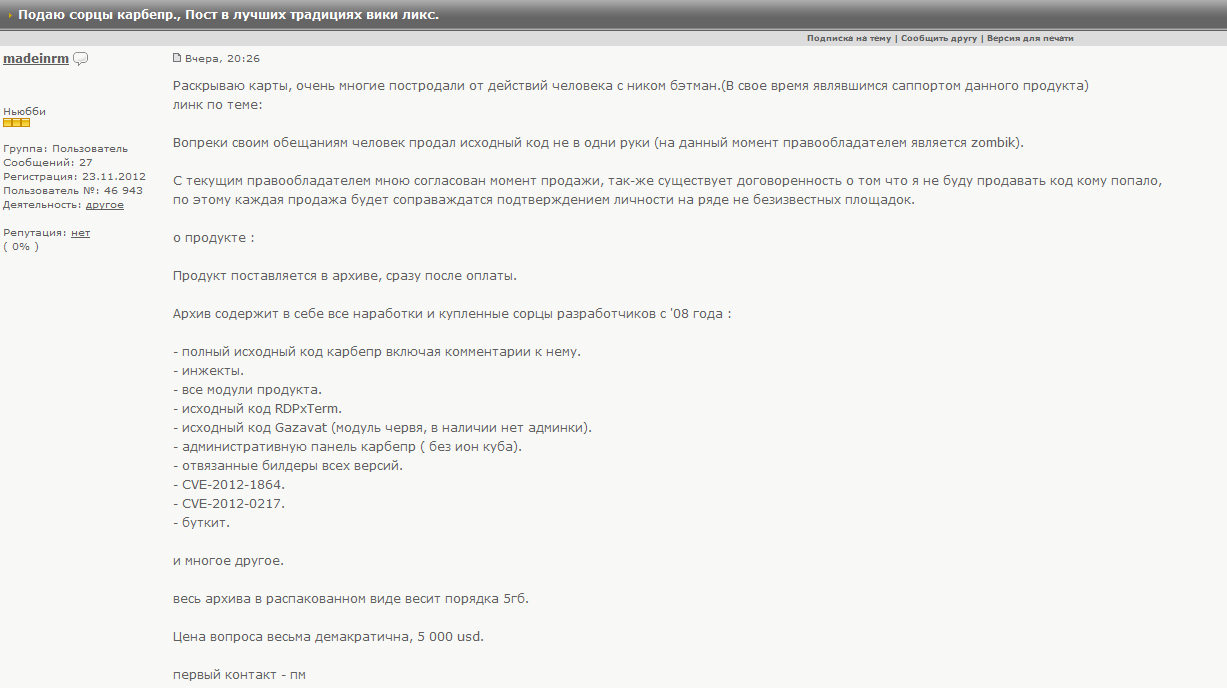
As in the case of Zeus, the story began with the fact that the archive with the texts was put up for sale in several underground forums. Below is a post with an ad from one of the forums. Initially, the information that the original Carberp texts were put up for sale was published by Trusteer on June 18th, i.e. about a week ago. It was indicated that the price of the archive is $ 50,000. But later on one of the forums there was information that the texts are sold at a very low price, only $ 5,000. The archive includes texts of malicious code and purchased third-party developments since 2008.
')
We managed to get an archive of Carberp source code and we can state that the leak of Carberp source code is the largest among those that used to be among the malicious programs . At the same time, this indicator includes both the number of possibilities of the malicious code itself, which are described by the included texts, their degree of detail, as well as the destructiveness that clones based on these source texts can inflict.
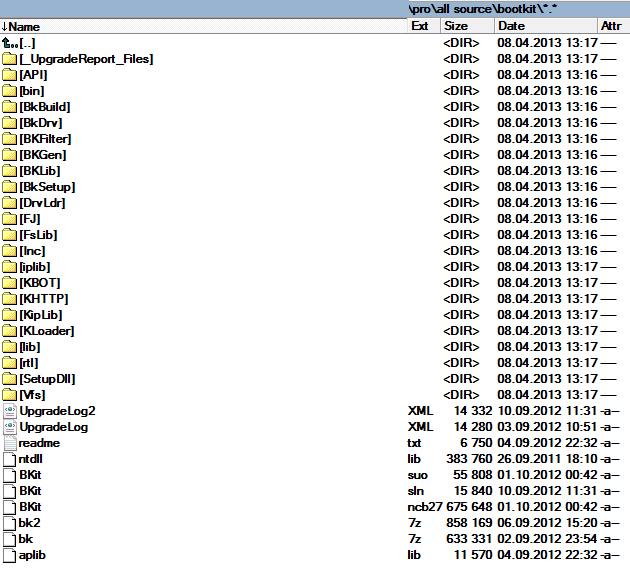
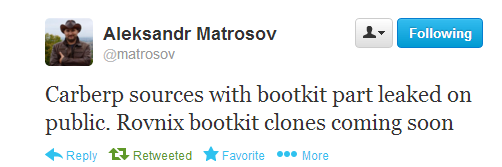
One of the moderators of kernelmode.info, EP_X0FF collected statistics on the families of malicious programs, the functionality of which is described by leaked texts. This list is really impressive (!): Ursnif, Rovnix, Alureon, Phdet, Zeus, Vundo, SpyEye . All of these families of malware are very well known to supervisors and are widely distributed.

Let us explain that Carberp initially did not have its bootkit component until 2011, when the developers bought the Rovnix framework (one of the first bootkit families that used the VBR infection method, which allowed loading its driver on x64 platforms bypassing OS restrictions). The Rovnix code and the history of the inclusion of its source texts in Carberp were described in detail by our colleague Alexander Matrosov here . We also compiled a complete report on the evolution of Carberp, in which it was possible to track the stages of development of malicious code.
Many publications and AV-vendors will write or have already written about the incident involving the leakage of Carberp source texts, as this is a really loud incident that could have unpleasant consequences. This refers to the fact of the appearance of clones of both the Carberp banking malware, the Rovnix bootkit platform, and other malicious code that can be generated by the source code of the malicious code.
Update : after a small inspection of the code, we also found out that the archive contains part of the texts of the well-known Stoned bootkit and Sinowal bootkit .
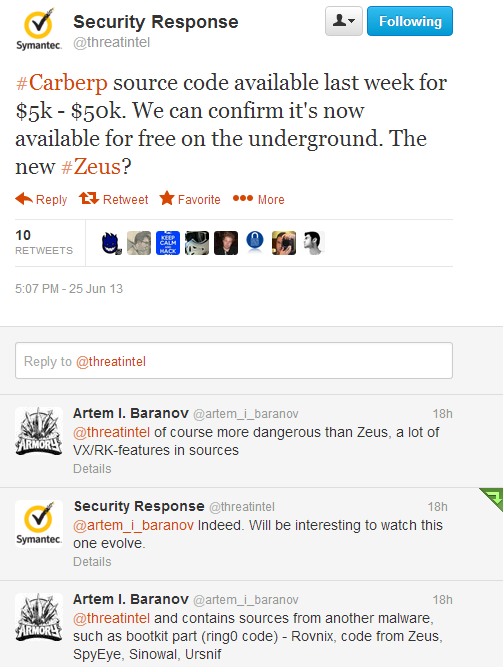
CSIS Peter Kruse Comment: (for threatpost )
- Source code of bootkit, km drivers and everything that works in km.
- Build droppers.
- Plugins
- Web injects.
- LPE exploits.
- A huge amount of other complete and necessary information to start your own project to develop malicious code.
As in the case of Zeus, the story began with the fact that the archive with the texts was put up for sale in several underground forums. Below is a post with an ad from one of the forums. Initially, the information that the original Carberp texts were put up for sale was published by Trusteer on June 18th, i.e. about a week ago. It was indicated that the price of the archive is $ 50,000. But later on one of the forums there was information that the texts are sold at a very low price, only $ 5,000. The archive includes texts of malicious code and purchased third-party developments since 2008.

')
We managed to get an archive of Carberp source code and we can state that the leak of Carberp source code is the largest among those that used to be among the malicious programs . At the same time, this indicator includes both the number of possibilities of the malicious code itself, which are described by the included texts, their degree of detail, as well as the destructiveness that clones based on these source texts can inflict.

One of the moderators of kernelmode.info, EP_X0FF collected statistics on the families of malicious programs, the functionality of which is described by leaked texts. This list is really impressive (!): Ursnif, Rovnix, Alureon, Phdet, Zeus, Vundo, SpyEye . All of these families of malware are very well known to supervisors and are widely distributed.

Let us explain that Carberp initially did not have its bootkit component until 2011, when the developers bought the Rovnix framework (one of the first bootkit families that used the VBR infection method, which allowed loading its driver on x64 platforms bypassing OS restrictions). The Rovnix code and the history of the inclusion of its source texts in Carberp were described in detail by our colleague Alexander Matrosov here . We also compiled a complete report on the evolution of Carberp, in which it was possible to track the stages of development of malicious code.
Many publications and AV-vendors will write or have already written about the incident involving the leakage of Carberp source texts, as this is a really loud incident that could have unpleasant consequences. This refers to the fact of the appearance of clones of both the Carberp banking malware, the Rovnix bootkit platform, and other malicious code that can be generated by the source code of the malicious code.
Update : after a small inspection of the code, we also found out that the archive contains part of the texts of the well-known Stoned bootkit and Sinowal bootkit .

CSIS Peter Kruse Comment: (for threatpost )
The package also has a bootkit for example, Stoned bootkit, Citadel, Ursnif etc. The package is currently undergoing deeper analysis. Chats and various usernames for several FTP servers. This also needs to be further further.
Source: https://habr.com/ru/post/184576/
All Articles