Keyboard input using IME
Introduction
In Asian language cultures there are a large number of characters that do not always fit on a standard keyboard layout. To enter these characters, a special technology was developed, which was called the Input Manager Editor (Rus. “Input Method Editors”). The Input Method Editor (IME) is a program or component of the operating system that allows users to enter characters that are not physically present on the keyboard.
Although the term “input method editor” (IME) was originally used only in Microsoft Windows, it is currently used in other operating systems, when it is important to distinguish the input method from the program functionality that provides it and general support for input methods. operating system.
The term “input method” usually means a certain input method from a keyboard in a language, such as Cantse, input using Pinyin or using “dead” keys. ”
The term “input method editor” usually means a specific program that allows you to use an input method (for example, SCIM or Microsoft IME).
Default IME system
If the language culture contains no more than 100 characters, then when typing from the keyboard, it is not necessary to convert several keystrokes to a single character, as was the case with typewriters. For modern keyboards, this rule is relevant, for example, QWERTY keyboards contain 102 keys and several modifiers. However, if more than 100 characters are present in the language, then it is necessary to provide for the conversion of a combination of the entered characters before using them in the application. This process is called the “communication process” (FEP) and IME is the standard way for FEP in Windows.
As standard, IME uses a syllable phonetic input card for the selected language. In the normal scenario, the user enters Latin characters that are included in the pronunciation of a particular syllable. If IME recognizes the syllable entered, it displays to the user a list of words or phrases of candidates from which the user can choose the final version. The selected word is then sent to the application through a series of Microsoft Windows messages - WM_CHAR. Since the IME operates at a level below the normal application (by intercepting keyboard input), the presence of the IME is transparent to the application. Almost all application windows can easily take advantage of IME, not knowing about its existence and not requiring special coding.
Entering a single word can occur in two or three stages, depending on the chosen language system.
For example, the script for the Japanese language:
- The user enters the designation of syllables in Latin. For example, the word "tsunami" is typed as "tsunami".
- Introduced syllables in the Latin alphabet are automatically replaced with symbols from hiragana or katakana. Hiragana and Katakana are syllabary alphabets in which each sound of the Japanese language has its own hieroglyph. For example, if the user selects hiragana: “Tsu” is automatically replaced with “つ”, “na” -> “な”, “mi” -> “み”.
- The user can leave the word written in hiragana, and can convert to a hieroglyph. Converting to hieroglyphs is similar to the T9 input system: in the worst case, the user is presented with a list of options from which he must choose one option. In the example with the “tsunami”, the hiragana “つ な み” turns into hieroglyphs “津 波”. At the third stage, you can control the conversion, usually using the keys "Space", "Enter", arrows, "numpad". For example, Space converts from hiragana to hieroglyphs, another Space shows a list with replacement options, “Enter” means to finish the conversion and leave the entered characters “as is”.
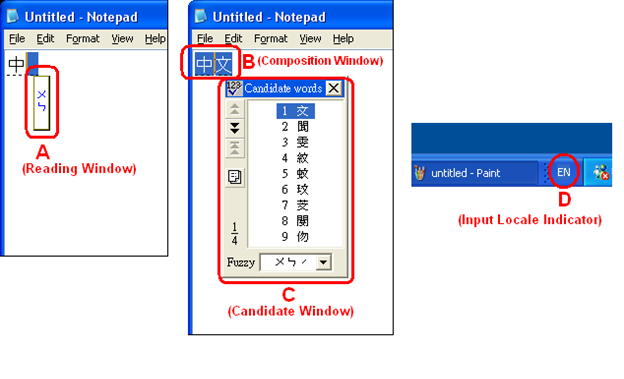
The first screenshot shows how the user enters a sequence of characters called the “composition string” (en. “Composition string”). It should be noted that the sequence of the two proposed characters was converted to one “F” symbol in a notebook.
The second screenshot shows that the user has completed the input of syllables, and the IME system prompts you to select the appropriate word (The user clicked “space”). The user can confirm the input of a word by pressing “Enter”.
After pressing “Enter” to confirm the entered word, the application (in the example, notepad) receives the resulting string as a WM_IME_CHAR message. Subsequently, if the application does not process this message, it will receive a standard WM_CHAR message from the IME system.
')
Overriding default IME behavior
Typically, IME uses standard Windows procedures for creating windows (using WinAPI).
Note: When an application is running in full-screen mode, as is customary, for example, for games, standard windows do not work and cannot be displayed over the application. To solve this problem, an application must process IME messages on its own, rather than rely on IME windows to accomplish this task.
As a standard, an application can use the IME library directly, by processing IME-related messages and invoking an input method manager (IMM).
When a user uses an IME layout to enter complex characters, IMM sends messages to the application to notify him of important events, such as launching a composition window or “show a list of candidate words”. An application typically ignores these messages and sends them, by default, to a Windows message handler, which causes the IME library to be called.
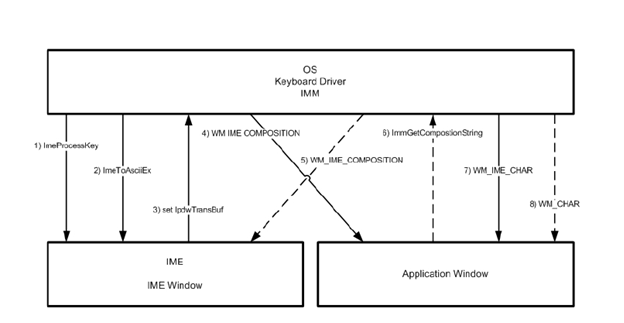
The process diagram (Fig. 2) shows how the text input process occurs:
- When the IMM receives keystrokes from the keyboard driver, it sends virtual characters to the IME system, calling the “ImeProcessKey” function. If the result of this function is “0”, then the keystroke must be handled by the operating system and the application itself. WM_KEYDOWN and WM_KEYUP messages will be sent to the application, and then WM_CHAR or WM_COMMAND.
- If the IME system returned a result other than "0", then IMM will transmit the pressed characters by calling the IME library's "ImeToAsciiEx" function.
- The IME system returns the "lpdwTransBuf" parameter, which contains the Windows messages that must be passed to the application. The IME system also takes hIMC, as a parameter, where the “composition string” is indicated. During operation, the IME system will change the contents of the hIMC memory area.
- Each time IMM receives the "lpdwTransBuf" parameter, it checks whether this buffer contains messages for the application. Usually the buffer contains a WM_IME_COMPOSITION message that must be sent to the application each time the composition string changes.
- If the application does not support IME, then it will not process the WM_IME_COMPOSITION message. Thus, the user will not see the input. In this case, the message is transmitted to the corresponding IME UI window (which is created by the IME system during initialization in the “ImeInquire” function), which is always created if the IME is activated. The IME window will show the composition string as entered by the user.
- If the application supports IME, then it will process the WM_IME_COMPOSITION message. If you want to get the contents of the composition string, the application calls the function “ImmGetCompositionString” from the library “Imm32.dll”. The WM_IME_COMPOSITION message can also notify the application that a string has been formed.
- If an application receives a composition string from IMM, then it should call the DefWindowProc function for the WM_IME_CHAR message, since further processing can generate this message again.
- If the application does not support IME, then it will receive a WM_IME_CHAR message. If the application supports Unicode, then the Unicode character will be passed in the parameters; if not, the application will receive a WM_CHAR message, but it will know that it is necessary to convert the character.
- As a result, the application always receives the WM_CHAR message and knows whether to convert the character.
The IME library is a regular DLL file, usually with the extension “.ime”. Each IME system must be registered in Microsoft Windows in the registry: "HKEY_LOCAL_MACHINE \ SYSTEM \ ControlSet00X \ Keyboard Layouts". For any application, you can always get its keyboard context.
Potential threat using IME system
Each Keyboard Layout, including IME systems, is always loaded into each process of the operating system. A normal application running in the user environment cannot prevent the loading of keyboard modules into its address space. The IME library, as a Windows library, is required to export several functions that can be overridden. Also, when loading a library, the DLLMain function is always called.
To implement an attack, such as Keylogger, an attacker simply needs to create his own IME system for any keyboard layout (for example, IME for US, UK, RU, CH, JP, KR), which does not display windows and performs character conversion. Those. will be invisible to the user.
As mentioned above, the IMM manager always transmits keystroke codes to the selected IME system, calling the ImeProcessKey and ImeToAsciiEx functions exported from the IME library.
The easiest way to intercept keystrokes is to use the “ImeProcessKey” function, which should always return “0” to prevent further processing of messages for a given character. Since IME-library is loaded into all processes, the user will not be able to notice suspicious activity by standard means (for example, there will not be a separate process for the IME-library).
Also, if ImeProcessKey returns a nonzero value, then key interception can be performed in the ImeToAsciiEx function, but it is necessary to convert the scan code of the pressed key to a character in the desired encoding, which is a trivial operation.
More malicious actions
Signed (legal) IME-library files can be easily deleted from the user's computer. If an IME library is created by hackers, then it can be added instead of a legal library. This can lead to the following threats:
- Malicious IMEs can change the standard IME of all users;
- Even if the user changes the default IME, IME editors that have already been selected will not be changed. The user must log in to the OS or restart the computer.
- If the IME-library is running in a separate thread, then it can continue to work. The user will not be able to complete it with standard means.
- Malicious users may set special registry change rights to make it difficult to remove the IME library.
- IME is loaded even in 16-bit applications and applications from the command line.
- IME can download the WinSock subsystem to access the Internet.
Source: https://habr.com/ru/post/183858/
All Articles