Public discussion of the GOST project on the protection of digitized video data from accidental and deliberate distortion
Dear users!
 Our company has been a member of the Technical Committee for Standardization TK-234 “Alarm Systems and Anti-Crime Protection Systems” for several years and is an active participant in the standardization processes in the field of security systems. It so happened that the adoption of standards in our country is happening, so to speak, "behind the scenes" on the basis of the decision of a fairly modest group of experts. This state of affairs seems to us to be wrong and now, during the development of the next standard, we decided on our own initiative to organize a public discussion on the draft GOST “Security Television Systems. Protection of digitized video data from accidental and deliberate distortion ".
Our company has been a member of the Technical Committee for Standardization TK-234 “Alarm Systems and Anti-Crime Protection Systems” for several years and is an active participant in the standardization processes in the field of security systems. It so happened that the adoption of standards in our country is happening, so to speak, "behind the scenes" on the basis of the decision of a fairly modest group of experts. This state of affairs seems to us to be wrong and now, during the development of the next standard, we decided on our own initiative to organize a public discussion on the draft GOST “Security Television Systems. Protection of digitized video data from accidental and deliberate distortion ".
We will be extremely grateful for the constructive criticism of the project, and all valuable comments and suggestions will be made in the next edition of the standard. If this experience is successful, then we will submit to the court of a respected Habrow auditorium all the projects of all standards passing through TC-234. Standard text under the cut.
')
Introduction
Television security systems are designed to be used to protect people and property at protected sites from criminal encroachment. The resulting digitized video data must be protected from accidental and deliberate distortion. This standard allows you to streamline the existing and developed methods of protection of digitized video data intended for use as part of anti-crime protection systems.
This standard should be applied in conjunction with GOST R 51558-2008 “Television security tools and systems. Classification. General technical requirements. Test methods ", as well as with GOST R 54830-2011" Television security systems. Compression of digitized video data. General technical requirements and algorithms evaluation methods.
NATIONAL STANDARD OF THE RUSSIAN FEDERATION
General requirements
Video surveillance systems. Digital video data from accidental or deliberate distortion. General requirements
Introduction Date -
1 area of use
This standard applies to digital television security systems (hereinafter referred to as COTS) and establishes general technical requirements for the application of various methods of protecting digitized video data in CTC from accidental and deliberate distortion.
This standard specifies the requirements for the application of various protection methods in digitized video data.
This standard is used in conjunction with the standards of GOST R 51558, GOST 34.11-2012, GOST ISO / IEC 17799-2005.
2 Normative references
This standard uses normative references to the following standards:
GOST R 51558-2008 Television security systems and systems. General technical requirements and test methods.
GOST R 54830-2011 Television security systems. Compression of digitized video data. Classification. General technical requirements and algorithms evaluation methods.
GOST R 50922-2006 Information Security. Basic terms and definitions.
GOST R 51275-2006 Information Security. The object of informatization. Factors affecting information.
GOST R 34.11-2012 Information technology. Cryptographic protection of information. Hash function
GOST R 34.10-2012 Information technology. Cryptographic protection of information. Processes of formation and verification of electronic digital signature.
GOST R ISO / IEC 17799-2005 Information technology. Practical rules of information security management.
GOST R 1.5-2004 National Standards of the Russian Federation. Rules of construction, presentation, design and notation.
GOST 28147-89 Information processing systems. Cryptographic protection. Algorithm of cryptographic transformation.
GOST 19.401-78. ESPD The text of the program. Requirements for the content and design.
GOST 19.402-78. ESPD Program description.
GOST 19.404-79. ESPD Explanatory note. Requirements for the content and design.
3 Terms and definitions
In this standard, the following terms are used with the corresponding definitions:
3.1 video data (video data), video stream (video stream): An analog signal that carries information about the spatial and temporal parameters of images.
3.2 digitized video data (digitized video data): Data obtained by analog-to-digital conversion of video data, representing a sequence of bytes in a certain format (RGB, YUV or others).
3.3 digitized video data format (digitized video data format); video format: Representation of digitized video data, ensuring their processing by digital computing means.
Note - The format of digitized video data includes the color model used and the dimension (number of bits) of the representation of each channel for the color model used.
3.4 video container (video container): a format of a file or video stream in which video and service information is stored or transmitted for further processing / analysis of a video sequence, or an integral part of another file and container for storing and transmitting video sequence and service information. The specification of the video container describes the way in which the transmitted data is presented, and may impose restrictions on the coding algorithms.
3.5 video data integrity: ensuring the reliability and completeness of information and methods for its processing.
3.6 authenticity of video data (authenticity video data): the property of the system to preserve immutability or to detect the fact of unauthorized change of information and attributes that establish authorship.
3.7 electronic digital signature, electronic signature (signature): electronic digital signature (signature), electronic signature: The string of bits obtained as a result of the signature generation process. (ISO / IEC 14888-1: 2008 [4])
The PRI mee
1. A string of bits that is a signature may have an internal structure, depending on the specific signature generation mechanism.
2. In this standard, in order to maintain terminological continuity with the existing domestic regulatory documents and published scientific and technical publications, it is established that the terms “electronic signature”, “digital signature” and “electronic digital signature” are synonyms.
3.8 private key: the secret part of a pair of asymmetric encryption algorithms. For EDS, a unique sequence of characters known to the holder of the signature key certificate and intended to create an electronic digital signature in electronic documents using electronic digital signature tools.
3.9 hash function (collision-resistant hash-function): A function that maps strings of bits to strings of fixed length and satisfies the following properties:
3.9.1 from this function value, it is difficult to calculate the source data displayed in this value;
3.9.2 for given source data it is difficult to calculate other source data displayed in the same function value;
3.9.3 it is difficult to calculate any pair of input data displayed in the same value. Note: in this standard, in order to maintain terminological continuity with the existing national regulatory documents and published scientific and technical publications, it has been established that the terms "hash function", "cryptographic hash function", "hash function" and "cryptographic hash function" are synonymous .
3.10 check sum: A number calculated by performing certain operations on the input data, usually used to check the correctness of data transmission over communication channels.
Note: In this standard, the term “checksum” is used to designate a mechanism for non-cryptographic control of information.
3.11 frame group: a certain number of consecutive frames of video data.
3.12 message (message) : a string of bits of limited length.
3.13 SDP (Session Description Protocol): a network protocol designed to describe a streaming session. SDP message may contain destination addresses; UDP port numbers for the sender and receiver; media formats that can be used during the session; start and stop time.
3.14 overhead information : information added to a frame or group of frames containing the numbering, date and time of transmission, as well as other data determined by the semantics of the COT.
3.15 IP address (Internet Protocol address): a sequence of bits that identify the recipient or sender of the transmitted data.
3.16 UTC time (Universal Time, Coordinated): Coordinated Universal Time Scale. The time scale calculated by the International Bureau of Measures and Weights and the International Earth Rotation Service so that the offset relative to the International Atomic Time Scale is an integer number of seconds, and relative to the Universal Time Clock does not exceed 0.9 s according to GOST 8.567.
3.17 RTSP (Real-Time Streaming Protocol): real-time streaming protocol. It is an application level protocol that provides control of data delivery for real-time applications.
3.18 local time (local time): the time set on the video source.
3.19 keyframe: frames in which the picture in the frame changes significantly.
4 General provisions
The purpose of this standard is to regulate the requirements for methods of protecting digitized video information from accidental and deliberate distortion in the process of their transmission and storage.
4.1 The implementation of the protection methods specified in this standard should ensure the authenticity of digitized video data during transmission between parts of the COT and storage.
4.2 This standard does not discuss methods of protection against distortions resulting from violations of connection methods, setting up equipment and other physical actions.
4.3. For digital video data, the following types of distortion are possible:
• substitution of a frame or group of frames;
• substitution of a fragment / fragments of an individual frame or a group of frames;
• changing the order of personnel or groups of personnel;
• delete a frame or groups of frames;
• loss of proprietary information associated with the video sequence;
• distortion of proprietary information associated with the video sequence.
These distortions may occur as a result of accidental or deliberate exposure.
This standard introduces the concept of data protection level. Each level has its own means and methods of protection. Levels of protection of digitized video data:
• level I - protection against accidental and deliberate distortion.
• Level II - protection against accidental distortion.
5 General requirements
5.1 Methods of protection of digitized video data from accidental or intentional distortion should be developed (modernized) in accordance with the requirements of this standard, technical specifications (TU) and / or other technical documentation for specific methods
5.2 Documentation confirming the applied level of protection of digitized video data against accidental or intentional distortion, must comply with GOST 19.401, GOST 19.402, GOST 19.404.
5.3 Mandatory for all levels of protection of digitized video data against accidental and deliberate distortion is the use of video formats / containers with the ability to resynchronize the video stream when the header is lost / damaged, i.e. such, the title of which begins with a synchronization token, which makes it possible to unambiguously determine the next title if the previous one is damaged.
Requirements for the protection of level II digitized video data
5.4 The protection level of digitized video data II is implemented by the checksum calculation algorithm.
5.4.1 Checksum requirements:
a) The size of the register for calculations should ensure the probability of an error not more than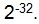
b) The checksum calculation algorithm should ensure that a change in one bit of input data leads to an average change of 50% of the checksum bits.
It is recommended to use the CRC32 algorithm [1].
Level I security requirements
5.5 The level of protection of digitized video data I is implemented by adding information to the digitized video data and signing a group of digital signature frames.
5.5.1 The added information to the digitized video data contains the numbering of the frame group, information about the transmission time and the technical characteristics of the video source.
5.5.1.1 Requirements for numbering a frame group:
a) Groups of frames should be numbered in ascending order.
b) Numbering must begin with 1.
c) The numbering step is 1.
5.5.1.2 Information on the transmission time should contain:
a) time (hours, minutes)
b) date (day, month, year)
c) the difference between UTC and local time
5.5.1.3. Requirements for the technical characteristics of the video source. Information must contain:
a) SDP message when transferring digitized video data by the RTSP protocol [4]
b) the IP address of the transmitting video camera when transmitting digitized video data using non-RTSP protocol
c) the number of the last reference frame for compressed frames.
5.5.2. EDS Requirements
a) Adding EDS for each group of frames of digitized video data is mandatory.
b) EDS should be generated in real time.
c) The calculation of the hash function for the EDS should be performed after adding the information to the video data.
d) Formation and verification of EDS should be carried out according to GOST 34.10.
e) Video sources must have technical protection that excludes the possibility of removing and / or replacing the private key. The organization of this technical protection is not considered in this standard.
Appendix A
(reference)
[1] CRC32-IEEE 802.3 Cyclic redundancy check. Cyclic redundancy code.
[2] Philip Koopman, Tridib Chakravarty. Cyclic Redundancy Code (CRC) Polynomial Selection For Embedded Networks, 2004.
[3] Typical requirements of the Federal Security Service of Russia No. 149/6 / 6-622 dated February 21, 2008 On the organization and operation of encryption (cryptographic) tools designed to protect information that does not contain information constituting state secrets when used to ensure security personal data during their processing in personal data information systems.
[4] RFC 2326. Real Time Streaming Protocol (RTSP), 1998.
See also Public discussion of the draft GOST on the compression of digitized audio data .
 Our company has been a member of the Technical Committee for Standardization TK-234 “Alarm Systems and Anti-Crime Protection Systems” for several years and is an active participant in the standardization processes in the field of security systems. It so happened that the adoption of standards in our country is happening, so to speak, "behind the scenes" on the basis of the decision of a fairly modest group of experts. This state of affairs seems to us to be wrong and now, during the development of the next standard, we decided on our own initiative to organize a public discussion on the draft GOST “Security Television Systems. Protection of digitized video data from accidental and deliberate distortion ".
Our company has been a member of the Technical Committee for Standardization TK-234 “Alarm Systems and Anti-Crime Protection Systems” for several years and is an active participant in the standardization processes in the field of security systems. It so happened that the adoption of standards in our country is happening, so to speak, "behind the scenes" on the basis of the decision of a fairly modest group of experts. This state of affairs seems to us to be wrong and now, during the development of the next standard, we decided on our own initiative to organize a public discussion on the draft GOST “Security Television Systems. Protection of digitized video data from accidental and deliberate distortion ".We will be extremely grateful for the constructive criticism of the project, and all valuable comments and suggestions will be made in the next edition of the standard. If this experience is successful, then we will submit to the court of a respected Habrow auditorium all the projects of all standards passing through TC-234. Standard text under the cut.
')
Introduction
Television security systems are designed to be used to protect people and property at protected sites from criminal encroachment. The resulting digitized video data must be protected from accidental and deliberate distortion. This standard allows you to streamline the existing and developed methods of protection of digitized video data intended for use as part of anti-crime protection systems.
This standard should be applied in conjunction with GOST R 51558-2008 “Television security tools and systems. Classification. General technical requirements. Test methods ", as well as with GOST R 54830-2011" Television security systems. Compression of digitized video data. General technical requirements and algorithms evaluation methods.
NATIONAL STANDARD OF THE RUSSIAN FEDERATION
TV security systems. Protect digitized video data from accidental and deliberate distortion.
General requirements
Video surveillance systems. Digital video data from accidental or deliberate distortion. General requirements
Introduction Date -
1 area of use
This standard applies to digital television security systems (hereinafter referred to as COTS) and establishes general technical requirements for the application of various methods of protecting digitized video data in CTC from accidental and deliberate distortion.
This standard specifies the requirements for the application of various protection methods in digitized video data.
This standard is used in conjunction with the standards of GOST R 51558, GOST 34.11-2012, GOST ISO / IEC 17799-2005.
2 Normative references
This standard uses normative references to the following standards:
GOST R 51558-2008 Television security systems and systems. General technical requirements and test methods.
GOST R 54830-2011 Television security systems. Compression of digitized video data. Classification. General technical requirements and algorithms evaluation methods.
GOST R 50922-2006 Information Security. Basic terms and definitions.
GOST R 51275-2006 Information Security. The object of informatization. Factors affecting information.
GOST R 34.11-2012 Information technology. Cryptographic protection of information. Hash function
GOST R 34.10-2012 Information technology. Cryptographic protection of information. Processes of formation and verification of electronic digital signature.
GOST R ISO / IEC 17799-2005 Information technology. Practical rules of information security management.
GOST R 1.5-2004 National Standards of the Russian Federation. Rules of construction, presentation, design and notation.
GOST 28147-89 Information processing systems. Cryptographic protection. Algorithm of cryptographic transformation.
GOST 19.401-78. ESPD The text of the program. Requirements for the content and design.
GOST 19.402-78. ESPD Program description.
GOST 19.404-79. ESPD Explanatory note. Requirements for the content and design.
3 Terms and definitions
In this standard, the following terms are used with the corresponding definitions:
3.1 video data (video data), video stream (video stream): An analog signal that carries information about the spatial and temporal parameters of images.
3.2 digitized video data (digitized video data): Data obtained by analog-to-digital conversion of video data, representing a sequence of bytes in a certain format (RGB, YUV or others).
3.3 digitized video data format (digitized video data format); video format: Representation of digitized video data, ensuring their processing by digital computing means.
Note - The format of digitized video data includes the color model used and the dimension (number of bits) of the representation of each channel for the color model used.
3.4 video container (video container): a format of a file or video stream in which video and service information is stored or transmitted for further processing / analysis of a video sequence, or an integral part of another file and container for storing and transmitting video sequence and service information. The specification of the video container describes the way in which the transmitted data is presented, and may impose restrictions on the coding algorithms.
3.5 video data integrity: ensuring the reliability and completeness of information and methods for its processing.
3.6 authenticity of video data (authenticity video data): the property of the system to preserve immutability or to detect the fact of unauthorized change of information and attributes that establish authorship.
3.7 electronic digital signature, electronic signature (signature): electronic digital signature (signature), electronic signature: The string of bits obtained as a result of the signature generation process. (ISO / IEC 14888-1: 2008 [4])
The PRI mee
1. A string of bits that is a signature may have an internal structure, depending on the specific signature generation mechanism.
2. In this standard, in order to maintain terminological continuity with the existing domestic regulatory documents and published scientific and technical publications, it is established that the terms “electronic signature”, “digital signature” and “electronic digital signature” are synonyms.
3.8 private key: the secret part of a pair of asymmetric encryption algorithms. For EDS, a unique sequence of characters known to the holder of the signature key certificate and intended to create an electronic digital signature in electronic documents using electronic digital signature tools.
3.9 hash function (collision-resistant hash-function): A function that maps strings of bits to strings of fixed length and satisfies the following properties:
3.9.1 from this function value, it is difficult to calculate the source data displayed in this value;
3.9.2 for given source data it is difficult to calculate other source data displayed in the same function value;
3.9.3 it is difficult to calculate any pair of input data displayed in the same value. Note: in this standard, in order to maintain terminological continuity with the existing national regulatory documents and published scientific and technical publications, it has been established that the terms "hash function", "cryptographic hash function", "hash function" and "cryptographic hash function" are synonymous .
3.10 check sum: A number calculated by performing certain operations on the input data, usually used to check the correctness of data transmission over communication channels.
Note: In this standard, the term “checksum” is used to designate a mechanism for non-cryptographic control of information.
3.11 frame group: a certain number of consecutive frames of video data.
3.12 message (message) : a string of bits of limited length.
3.13 SDP (Session Description Protocol): a network protocol designed to describe a streaming session. SDP message may contain destination addresses; UDP port numbers for the sender and receiver; media formats that can be used during the session; start and stop time.
3.14 overhead information : information added to a frame or group of frames containing the numbering, date and time of transmission, as well as other data determined by the semantics of the COT.
3.15 IP address (Internet Protocol address): a sequence of bits that identify the recipient or sender of the transmitted data.
3.16 UTC time (Universal Time, Coordinated): Coordinated Universal Time Scale. The time scale calculated by the International Bureau of Measures and Weights and the International Earth Rotation Service so that the offset relative to the International Atomic Time Scale is an integer number of seconds, and relative to the Universal Time Clock does not exceed 0.9 s according to GOST 8.567.
3.17 RTSP (Real-Time Streaming Protocol): real-time streaming protocol. It is an application level protocol that provides control of data delivery for real-time applications.
3.18 local time (local time): the time set on the video source.
3.19 keyframe: frames in which the picture in the frame changes significantly.
4 General provisions
The purpose of this standard is to regulate the requirements for methods of protecting digitized video information from accidental and deliberate distortion in the process of their transmission and storage.
4.1 The implementation of the protection methods specified in this standard should ensure the authenticity of digitized video data during transmission between parts of the COT and storage.
4.2 This standard does not discuss methods of protection against distortions resulting from violations of connection methods, setting up equipment and other physical actions.
4.3. For digital video data, the following types of distortion are possible:
• substitution of a frame or group of frames;
• substitution of a fragment / fragments of an individual frame or a group of frames;
• changing the order of personnel or groups of personnel;
• delete a frame or groups of frames;
• loss of proprietary information associated with the video sequence;
• distortion of proprietary information associated with the video sequence.
These distortions may occur as a result of accidental or deliberate exposure.
This standard introduces the concept of data protection level. Each level has its own means and methods of protection. Levels of protection of digitized video data:
• level I - protection against accidental and deliberate distortion.
• Level II - protection against accidental distortion.
5 General requirements
5.1 Methods of protection of digitized video data from accidental or intentional distortion should be developed (modernized) in accordance with the requirements of this standard, technical specifications (TU) and / or other technical documentation for specific methods
5.2 Documentation confirming the applied level of protection of digitized video data against accidental or intentional distortion, must comply with GOST 19.401, GOST 19.402, GOST 19.404.
5.3 Mandatory for all levels of protection of digitized video data against accidental and deliberate distortion is the use of video formats / containers with the ability to resynchronize the video stream when the header is lost / damaged, i.e. such, the title of which begins with a synchronization token, which makes it possible to unambiguously determine the next title if the previous one is damaged.
Requirements for the protection of level II digitized video data
5.4 The protection level of digitized video data II is implemented by the checksum calculation algorithm.
5.4.1 Checksum requirements:
a) The size of the register for calculations should ensure the probability of an error not more than
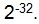
b) The checksum calculation algorithm should ensure that a change in one bit of input data leads to an average change of 50% of the checksum bits.
It is recommended to use the CRC32 algorithm [1].
Level I security requirements
5.5 The level of protection of digitized video data I is implemented by adding information to the digitized video data and signing a group of digital signature frames.
5.5.1 The added information to the digitized video data contains the numbering of the frame group, information about the transmission time and the technical characteristics of the video source.
5.5.1.1 Requirements for numbering a frame group:
a) Groups of frames should be numbered in ascending order.
b) Numbering must begin with 1.
c) The numbering step is 1.
5.5.1.2 Information on the transmission time should contain:
a) time (hours, minutes)
b) date (day, month, year)
c) the difference between UTC and local time
5.5.1.3. Requirements for the technical characteristics of the video source. Information must contain:
a) SDP message when transferring digitized video data by the RTSP protocol [4]
b) the IP address of the transmitting video camera when transmitting digitized video data using non-RTSP protocol
c) the number of the last reference frame for compressed frames.
5.5.2. EDS Requirements
a) Adding EDS for each group of frames of digitized video data is mandatory.
b) EDS should be generated in real time.
c) The calculation of the hash function for the EDS should be performed after adding the information to the video data.
d) Formation and verification of EDS should be carried out according to GOST 34.10.
e) Video sources must have technical protection that excludes the possibility of removing and / or replacing the private key. The organization of this technical protection is not considered in this standard.
Appendix A
(reference)
[1] CRC32-IEEE 802.3 Cyclic redundancy check. Cyclic redundancy code.
[2] Philip Koopman, Tridib Chakravarty. Cyclic Redundancy Code (CRC) Polynomial Selection For Embedded Networks, 2004.
[3] Typical requirements of the Federal Security Service of Russia No. 149/6 / 6-622 dated February 21, 2008 On the organization and operation of encryption (cryptographic) tools designed to protect information that does not contain information constituting state secrets when used to ensure security personal data during their processing in personal data information systems.
[4] RFC 2326. Real Time Streaming Protocol (RTSP), 1998.
See also Public discussion of the draft GOST on the compression of digitized audio data .
Source: https://habr.com/ru/post/183732/
All Articles