b54 a week later
More than a week ago, Microsoft announced the start of operation b54 , aimed at disabling botnets built using the malicious code Citadel. The operation mainly aims to destroy an established scheme for extracting monetary gain from these botnets by intruders. In addition, it includes actions to clean computers from malicious code bots, together with the ISP.
As part of this operation, Microsoft posted in open access materials of civil lawsuits to John Doe (defendants, whose exact identity has not yet been established). One of the documents specifies the prescriptions according to which this operation should proceed. Its essence comes down not to the total dismantling of various botnet control servers (Citadel allows you to set the builder’s configurations in such a way that each user of the crimeware toolkit gets its own botnet from the bots that were created by this builder), but to reorient the botnet so that it does not allowed attackers to gain control over an already infected system. Such a scheme is achieved using the method of overwriting a part of the contact information on the domains accessed by the Citadel (C & C) bot from the registrar of these domains.
For all registered Citadel domains (listed in Appendix A ), registrars should take the following actions:
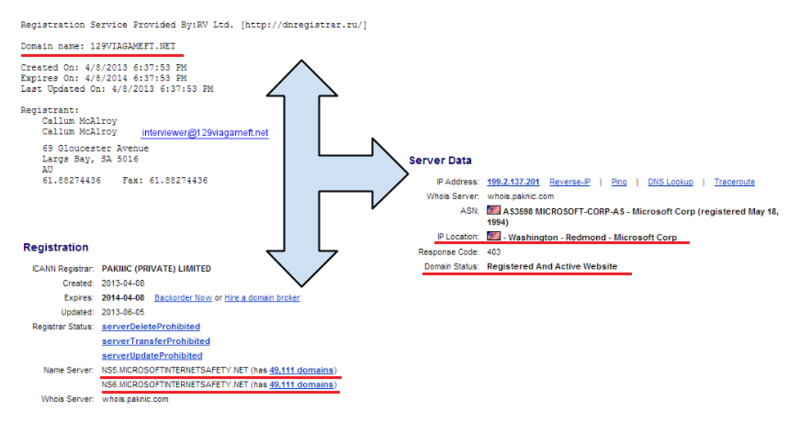
An example of information from one of these domains is shown in the figure below (information obtained using the service whois.domaintools.com).
')
For all other Citadel domains, i.e. those that are not registered in Appendix A, take actions:
For these domains, the information in WHOIS will be as follows:
The bad news is that a certain number of Citadel domains are used by security firms and reporters to capture the activity of Citadel botnets (sinkhole). They specifically created these domains and registered them for themselves to get statistics on the work of the botnet. Not looking at the contact details of such domains, the company re-registered them for themselves, which led to the disruption of the tracking systems of botnets of other companies .
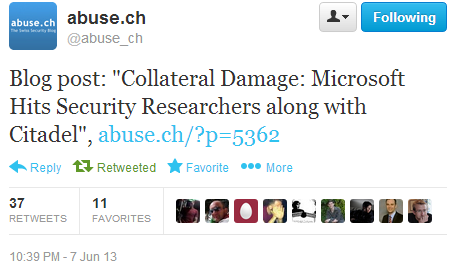
One of the first who saw this behavior of their domains was Roman Hüssy, the creator of ZeusTracker. He drew attention to the fact that the domains intended for the sinkhole botnet are now pointing to Microsoft servers in the address range 199.2.137.0/24. It is clear that his domains suffered the fate of becoming the property of the company. As a result, Microsoft disabled about 300 domains of abuse.ch, making it difficult to further monitor botnet activity. According to experts, about 1,000 domains out of 4,000 captured by the company were designed specifically for sinkhole operations and did not pose any danger to users .
After the company acquired the domains in its possession, the phase of “introducing” a special configuration file for bots (computers infected with the Citadel code) began. The fact is that Citadel bots poll their domains for the purpose of receiving a configuration file and subsequent instructions. The file, created by Microsoft, instructs bots to unblock AV resources, which will allow users infected with Citadel to access the antivirus distributions on the network. In addition, this configuration file regulates the Microsoft server as the main one for communicating with C & C, that is, the bot will no longer poll other servers, but will always connect to it only.
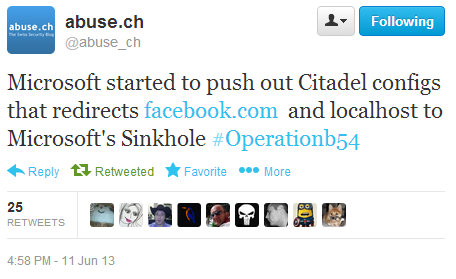
After a few more days, it was noted that now the configuration file created by the company for bots includes information on redirecting user requests addressed to facebook.com and localhost also to the Microsoft server. When visiting fb on an infected computer, the user will be redirected to a warning page from Microsoft.

As part of this operation, Microsoft posted in open access materials of civil lawsuits to John Doe (defendants, whose exact identity has not yet been established). One of the documents specifies the prescriptions according to which this operation should proceed. Its essence comes down not to the total dismantling of various botnet control servers (Citadel allows you to set the builder’s configurations in such a way that each user of the crimeware toolkit gets its own botnet from the bots that were created by this builder), but to reorient the botnet so that it does not allowed attackers to gain control over an already infected system. Such a scheme is achieved using the method of overwriting a part of the contact information on the domains accessed by the Citadel (C & C) bot from the registrar of these domains.
For all registered Citadel domains (listed in Appendix A ), registrars should take the following actions:
- leave WHOIS contact information for domain owners unchanged;
- domains must work without stopping their activities;
- DNS server addresses for these domains must be overwritten with the following: NS5.microsoftinternetsafety.net and NS6.microsoftinternetsafety.net.
An example of information from one of these domains is shown in the figure below (information obtained using the service whois.domaintools.com).
')

For all other Citadel domains, i.e. those that are not registered in Appendix A, take actions:
- transfer such domains into the ownership of Microsoft so that the company is granted the rights to administer them;
- replace contact information in such domains with the specified Microsoft;
- domains must work without stopping their activities;
- DNS server addresses for these domains must be overwritten with the following: NS5.microsoftinternetsafety.net and NS6.microsoftinternetsafety.net.
For these domains, the information in WHOIS will be as follows:
Domain Administrator
Microsoft Corporation
One Microsoft Way
Redmond, WA 98052
United States
Phone: +1.4258828080
Facsimile: +1.4259367329
domains@microsoft.com
Servers: NS5.microsoftinternetsafety.net, NS6.microsoftinternetsafety.net
The bad news is that a certain number of Citadel domains are used by security firms and reporters to capture the activity of Citadel botnets (sinkhole). They specifically created these domains and registered them for themselves to get statistics on the work of the botnet. Not looking at the contact details of such domains, the company re-registered them for themselves, which led to the disruption of the tracking systems of botnets of other companies .

One of the first who saw this behavior of their domains was Roman Hüssy, the creator of ZeusTracker. He drew attention to the fact that the domains intended for the sinkhole botnet are now pointing to Microsoft servers in the address range 199.2.137.0/24. It is clear that his domains suffered the fate of becoming the property of the company. As a result, Microsoft disabled about 300 domains of abuse.ch, making it difficult to further monitor botnet activity. According to experts, about 1,000 domains out of 4,000 captured by the company were designed specifically for sinkhole operations and did not pose any danger to users .
After the company acquired the domains in its possession, the phase of “introducing” a special configuration file for bots (computers infected with the Citadel code) began. The fact is that Citadel bots poll their domains for the purpose of receiving a configuration file and subsequent instructions. The file, created by Microsoft, instructs bots to unblock AV resources, which will allow users infected with Citadel to access the antivirus distributions on the network. In addition, this configuration file regulates the Microsoft server as the main one for communicating with C & C, that is, the bot will no longer poll other servers, but will always connect to it only.

After a few more days, it was noted that now the configuration file created by the company for bots includes information on redirecting user requests addressed to facebook.com and localhost also to the Microsoft server. When visiting fb on an infected computer, the user will be redirected to a warning page from Microsoft.

Source: https://habr.com/ru/post/183588/
All Articles