Cloud computing threats and methods to protect them
A data center (DPC) is a collection of servers located on the same site in order to improve efficiency and security. Data center protection is a network and physical protection, as well as fault tolerance and reliable power. Currently, the market offers a wide range of solutions to protect servers and data centers from various threats. They are united by the focus on a narrow range of tasks . However, the range of these tasks has undergone some expansion due to the gradual crowding out of classical hardware systems by virtual platforms. Known types of threats (network attacks, vulnerabilities in operating system applications, malicious software) were added due to the complexity associated with controlling the environment (hypervisor), traffic between guest machines, and access rights. Internal issues and data center protection policies, requirements of external regulators, have expanded. The work of modern data centers in a number of industries requires the closure of technical issues, as well as issues related to their security. Financial institutions (banks, processing centers) are subject to a number of standards, the implementation of which is based on the level of technical solutions. The penetration of virtualization platforms has reached a level where almost all companies using these systems are very seriously engaged in enhancing their security. Note that just a year ago, interest was rather theoretical .
In today's environment, it is becoming increasingly difficult to protect business-critical systems and applications.
The emergence of virtualization has become an important reason for the large-scale migration of most systems on the VM, however, the solution of security problems associated with the operation of applications in the new environment requires a special approach. Many types of threats are sufficiently studied and protection tools have been developed for them, but they still need to be adapted for use in the cloud.
Cloud control and management is a security issue. There is no guarantee that all cloud resources are counted and there are no uncontrolled virtual machines, no extra processes are running and the mutual configuration of cloud elements is not broken. This is a high-level type of threat, because it is connected with cloud manageability as a unified information system and for it the general protection needs to be built individually. To do this, you must use the risk management model for cloud infrastructures.
Physical security is based on strict control of physical access to servers and network infrastructure. Unlike physical security, network security primarily consists of building a robust threat model that includes intrusion protection and a firewall. Using a firewall involves the operation of the filter, in order to distinguish the internal data center networks on subnets with different levels of trust. These can be separate servers accessible from the Internet or servers from internal networks.
In cloud computing, the most important role of the platform is virtualization technology. To preserve data integrity and provide protection, consider the main known threats to cloud computing.
Cloud computing security requirements do not differ from data center security requirements. However, data center virtualization and the transition to cloud environments lead to the emergence of new threats.
Internet access to computing power management is one of the key characteristics of cloud computing. In most traditional data centers, the access of engineers to the servers is controlled at the physical level; in cloud environments, they operate over the Internet. Differentiation of access control and ensuring transparency of changes at the system level is one of the main protection criteria.
')
Virtual machines are dynamic. Create a new car, stop its work, you can start it again in a short time. They are cloned and can be moved between physical servers. This variability is difficult to influence the integrity of the security system. However, vulnerabilities of the operating system or applications in a virtual environment are spread out of control and often manifest themselves after an arbitrary period of time (for example, when restoring from a backup). In cloud computing environments, it is important to reliably capture the security status of the system, and this should not depend on its state and location.
Cloud computing servers and local servers use the same operating systems and applications. For cloud systems, the threat of remote hacking or malware infection is high. The risk for virtual systems is also high. Parallel virtual machines increase the “attacked surface”. Intrusion detection and prevention systems must be able to detect malicious activity at the virtual machine level, regardless of their location in the cloud environment.
When the virtual machine is turned off, it is at risk of infection. Access to the repository of virtual machine images via the network is sufficient. With the virtual machine turned off, it is absolutely impossible to run security software. In this case, protection should be implemented not only within each virtual machine, but also at the hypervisor level.
When using cloud computing, the network perimeter is blurred or disappears. This leads to the fact that the protection of the less protected part of the network determines the overall level of security. To distinguish between segments with different levels of trust in the cloud, virtual machines must themselves provide protection by moving the network perimeter to the virtual machine itself (Figure 1.). Corporate firewall - the main component for implementing IT security policies and delimiting network segments, is not able to affect servers hosted in cloud environments.
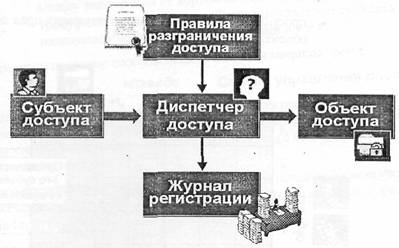
Fig. 1. The scheme of the mechanism of access control
Vulnerabilities of operating systems, modular components, network protocols, and others are traditional threats, for which it is enough to protect the interweb screen, firewall, antivirus, IPS and other components that solve this problem. At the same time, it is important that these protection tools work effectively in a virtualized environment.
This type of attack is associated with cloud layering, a common security principle. In the article on the danger of clouds, the following solution was proposed: To protect against functional attacks for each part of the cloud, you need to use the following means of protection: for proxies - effective protection against DoS attacks, for the web server - page integrity control, for the application server - level screen applications, for a DBMS - protection against SQL injections, for a data storage system - the correct backups (backup), access control. Separately, each of these defense mechanisms have already been created, but they are not brought together for comprehensive cloud protection, so the task of integrating them into a single system needs to be addressed during the creation of the cloud.
Most users connect to the cloud using a browser. It examines such attacks as Cross Site Scripting, “hijacking” passwords, intercepting web sessions, “man in the middle” and many others. The only protection against this type of attack is the correct authentication and the use of an encrypted connection (SSL) with mutual authentication . However, these protections are not very convenient and very wasteful for cloud creators. There are many unsolved problems in this branch of information security.
The hypervisor is one of the key elements of a virtual system. Its main function is the sharing of resources between virtual machines. An attack on the hypervisor can result in one virtual machine being able to access memory and resources of another. It will also be able to intercept network traffic, select physical resources, and even push the virtual machine from the server. As standard methods of protection, it is recommended to use specialized products for virtual environments, integrate host servers with the Active Directory service, use complexity and password aging policies, and standardize access procedures to host server control tools, use the built-in virtualization host firewall. It is also possible to disable such frequently used services as, for example, web access to the virtualization server.
A large number of virtual machines used in the cloud requires control systems that can reliably control the creation, transfer and disposal of virtual machines. Intervention in the control system can lead to the appearance of virtual machines - stealth, capable of blocking some virtual machines and exchanging others.
The most effective ways to protect in the field of cloud security published the organization Cloud Security Alliance (CSA) . After analyzing the information published by the company, the following solutions were proposed.
Encryption is one of the most effective ways to protect data. The provider providing access to the data must encrypt the client information stored in the data center, as well as in cases of no need, permanently delete.
Encrypted data during transmission must be available only after authentication. Data will not be able to read or make changes, even in cases of access through unreliable nodes. Such technologies are well known, algorithms and reliable protocols AES, TLS, IPsec have long been used by providers.
Authentication - password protection. To ensure higher reliability, they often resort to tools such as tokens and certificates. For transparent interaction of the provider with the authentication system during authorization, it is also recommended to use the LDAP (Lightweight Directory Access Protocol) and SAML (Security Assertion Markup Language).
Using an individual virtual machine and a virtual network. Virtual networks should be deployed using technologies such as VPN (Virtual Private Network), VLAN (Virtual Local Area Network) and VPLS (Virtual Private LAN Service). Often, providers isolate user data from each other by changing the code data in a single software environment. This approach has risks associated with the danger of finding a hole in a nonstandard code that allows access to data. In cases of a possible error in the code, the user can get the data of another. Recently, such incidents often occurred.
The described solutions for protection against threats to the safety of cloud computing have been repeatedly applied by system integrators in private cloud projects. After applying these solutions, the number of incidents that have occurred has significantly decreased. But many problems associated with the protection of virtualization still require careful analysis and well-developed solutions. We will consider them in more detail in the next article.
In today's environment, it is becoming increasingly difficult to protect business-critical systems and applications.
The emergence of virtualization has become an important reason for the large-scale migration of most systems on the VM, however, the solution of security problems associated with the operation of applications in the new environment requires a special approach. Many types of threats are sufficiently studied and protection tools have been developed for them, but they still need to be adapted for use in the cloud.
Existing cloud computing threats
Cloud control and management is a security issue. There is no guarantee that all cloud resources are counted and there are no uncontrolled virtual machines, no extra processes are running and the mutual configuration of cloud elements is not broken. This is a high-level type of threat, because it is connected with cloud manageability as a unified information system and for it the general protection needs to be built individually. To do this, you must use the risk management model for cloud infrastructures.
Physical security is based on strict control of physical access to servers and network infrastructure. Unlike physical security, network security primarily consists of building a robust threat model that includes intrusion protection and a firewall. Using a firewall involves the operation of the filter, in order to distinguish the internal data center networks on subnets with different levels of trust. These can be separate servers accessible from the Internet or servers from internal networks.
In cloud computing, the most important role of the platform is virtualization technology. To preserve data integrity and provide protection, consider the main known threats to cloud computing.
1. Difficulties in moving normal servers to the computing cloud
Cloud computing security requirements do not differ from data center security requirements. However, data center virtualization and the transition to cloud environments lead to the emergence of new threats.
Internet access to computing power management is one of the key characteristics of cloud computing. In most traditional data centers, the access of engineers to the servers is controlled at the physical level; in cloud environments, they operate over the Internet. Differentiation of access control and ensuring transparency of changes at the system level is one of the main protection criteria.
')
2. Dynamic virtual machines
Virtual machines are dynamic. Create a new car, stop its work, you can start it again in a short time. They are cloned and can be moved between physical servers. This variability is difficult to influence the integrity of the security system. However, vulnerabilities of the operating system or applications in a virtual environment are spread out of control and often manifest themselves after an arbitrary period of time (for example, when restoring from a backup). In cloud computing environments, it is important to reliably capture the security status of the system, and this should not depend on its state and location.
3. Vulnerabilities within the virtual environment
Cloud computing servers and local servers use the same operating systems and applications. For cloud systems, the threat of remote hacking or malware infection is high. The risk for virtual systems is also high. Parallel virtual machines increase the “attacked surface”. Intrusion detection and prevention systems must be able to detect malicious activity at the virtual machine level, regardless of their location in the cloud environment.
4. Protection of idle virtual machines
When the virtual machine is turned off, it is at risk of infection. Access to the repository of virtual machine images via the network is sufficient. With the virtual machine turned off, it is absolutely impossible to run security software. In this case, protection should be implemented not only within each virtual machine, but also at the hypervisor level.
5. Perimeter Protection and Network Distribution
When using cloud computing, the network perimeter is blurred or disappears. This leads to the fact that the protection of the less protected part of the network determines the overall level of security. To distinguish between segments with different levels of trust in the cloud, virtual machines must themselves provide protection by moving the network perimeter to the virtual machine itself (Figure 1.). Corporate firewall - the main component for implementing IT security policies and delimiting network segments, is not able to affect servers hosted in cloud environments.

Fig. 1. The scheme of the mechanism of access control
Cloud Attacks and Solutions to Eliminate them
1. Traditional software attacks
Vulnerabilities of operating systems, modular components, network protocols, and others are traditional threats, for which it is enough to protect the interweb screen, firewall, antivirus, IPS and other components that solve this problem. At the same time, it is important that these protection tools work effectively in a virtualized environment.
2. Functional attacks on cloud elements
This type of attack is associated with cloud layering, a common security principle. In the article on the danger of clouds, the following solution was proposed: To protect against functional attacks for each part of the cloud, you need to use the following means of protection: for proxies - effective protection against DoS attacks, for the web server - page integrity control, for the application server - level screen applications, for a DBMS - protection against SQL injections, for a data storage system - the correct backups (backup), access control. Separately, each of these defense mechanisms have already been created, but they are not brought together for comprehensive cloud protection, so the task of integrating them into a single system needs to be addressed during the creation of the cloud.
3. Attacks on the client
Most users connect to the cloud using a browser. It examines such attacks as Cross Site Scripting, “hijacking” passwords, intercepting web sessions, “man in the middle” and many others. The only protection against this type of attack is the correct authentication and the use of an encrypted connection (SSL) with mutual authentication . However, these protections are not very convenient and very wasteful for cloud creators. There are many unsolved problems in this branch of information security.
4. Attacks on the hypervisor
The hypervisor is one of the key elements of a virtual system. Its main function is the sharing of resources between virtual machines. An attack on the hypervisor can result in one virtual machine being able to access memory and resources of another. It will also be able to intercept network traffic, select physical resources, and even push the virtual machine from the server. As standard methods of protection, it is recommended to use specialized products for virtual environments, integrate host servers with the Active Directory service, use complexity and password aging policies, and standardize access procedures to host server control tools, use the built-in virtualization host firewall. It is also possible to disable such frequently used services as, for example, web access to the virtualization server.
5. Attacks on control systems
A large number of virtual machines used in the cloud requires control systems that can reliably control the creation, transfer and disposal of virtual machines. Intervention in the control system can lead to the appearance of virtual machines - stealth, capable of blocking some virtual machines and exchanging others.
Security Security Solutions from the Cloud Security Alliance (CSA)
The most effective ways to protect in the field of cloud security published the organization Cloud Security Alliance (CSA) . After analyzing the information published by the company, the following solutions were proposed.
1. Data security. Encryption
Encryption is one of the most effective ways to protect data. The provider providing access to the data must encrypt the client information stored in the data center, as well as in cases of no need, permanently delete.
2. Data protection during transmission
Encrypted data during transmission must be available only after authentication. Data will not be able to read or make changes, even in cases of access through unreliable nodes. Such technologies are well known, algorithms and reliable protocols AES, TLS, IPsec have long been used by providers.
3. Authentication
Authentication - password protection. To ensure higher reliability, they often resort to tools such as tokens and certificates. For transparent interaction of the provider with the authentication system during authorization, it is also recommended to use the LDAP (Lightweight Directory Access Protocol) and SAML (Security Assertion Markup Language).
4. Isolation of users
Using an individual virtual machine and a virtual network. Virtual networks should be deployed using technologies such as VPN (Virtual Private Network), VLAN (Virtual Local Area Network) and VPLS (Virtual Private LAN Service). Often, providers isolate user data from each other by changing the code data in a single software environment. This approach has risks associated with the danger of finding a hole in a nonstandard code that allows access to data. In cases of a possible error in the code, the user can get the data of another. Recently, such incidents often occurred.
Conclusion
The described solutions for protection against threats to the safety of cloud computing have been repeatedly applied by system integrators in private cloud projects. After applying these solutions, the number of incidents that have occurred has significantly decreased. But many problems associated with the protection of virtualization still require careful analysis and well-developed solutions. We will consider them in more detail in the next article.
Source: https://habr.com/ru/post/183168/
All Articles