We use tablets and smartphones to work with Dell

The rapid development of mobile technologies that we have seen over the last few years has led to the fact that many modern tablets are no longer inferior to average laptops, bought 3-4 years ago, often even ahead of the latter in many ways. The performance of smart phone phones is also growing every year, and most devices of this class have long been transformed from simple dialers into multifunctional combines, allowing to solve a huge number of very different tasks relevant to the user.
Several years ago, Intel offered an interesting approach to corporate policy, in which employees of enterprises were given the opportunity to use their personal devices for work. Almost immediately, this idea was picked up by other major players, the policy was called BYOD (“Bring your own device”). The introduction of the BYOD concept required close attention to security issues, but this approach gave more mobility to employees, allowing them to use work and free time much more efficiently.
In this article, we will discuss some of the Dell solutions that will help implement BYOD policies, and also talk about the features of the concept itself.
')
A bit about BYOD policy
Nowadays, almost every high school student has an advanced smartphone with a powerful, at least dual-core processor, an integrated camera and a bunch of applications on board. After graduating from school and entering a higher education institution, “personal animals” like a tablet and a smartphone remain nearby, and, by the time the university is completed, young people are so used to using their gadgets (not only for entertainment, but also for studying) that to use the same devices and at work looks to them very, very attractive. Modern young people, whether they are high school students or students, glide through life so quickly that mobility when working in a new workplace seems quite natural to them.
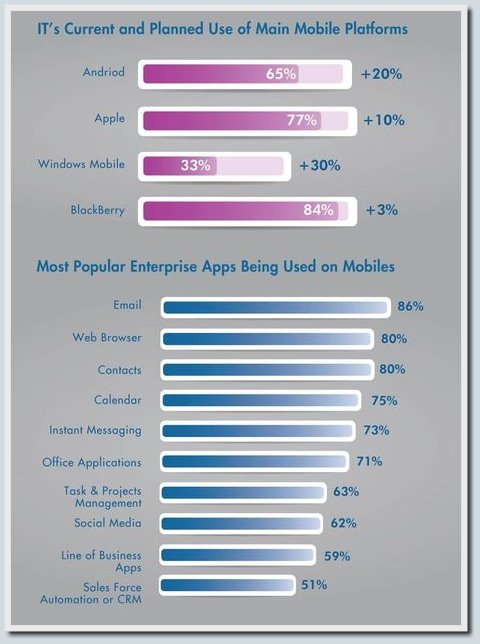
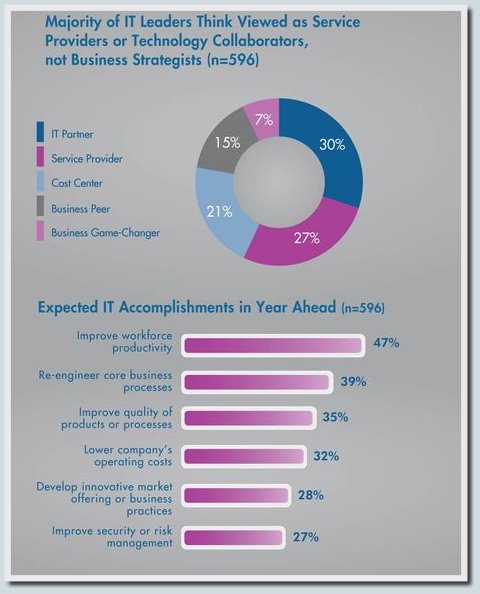
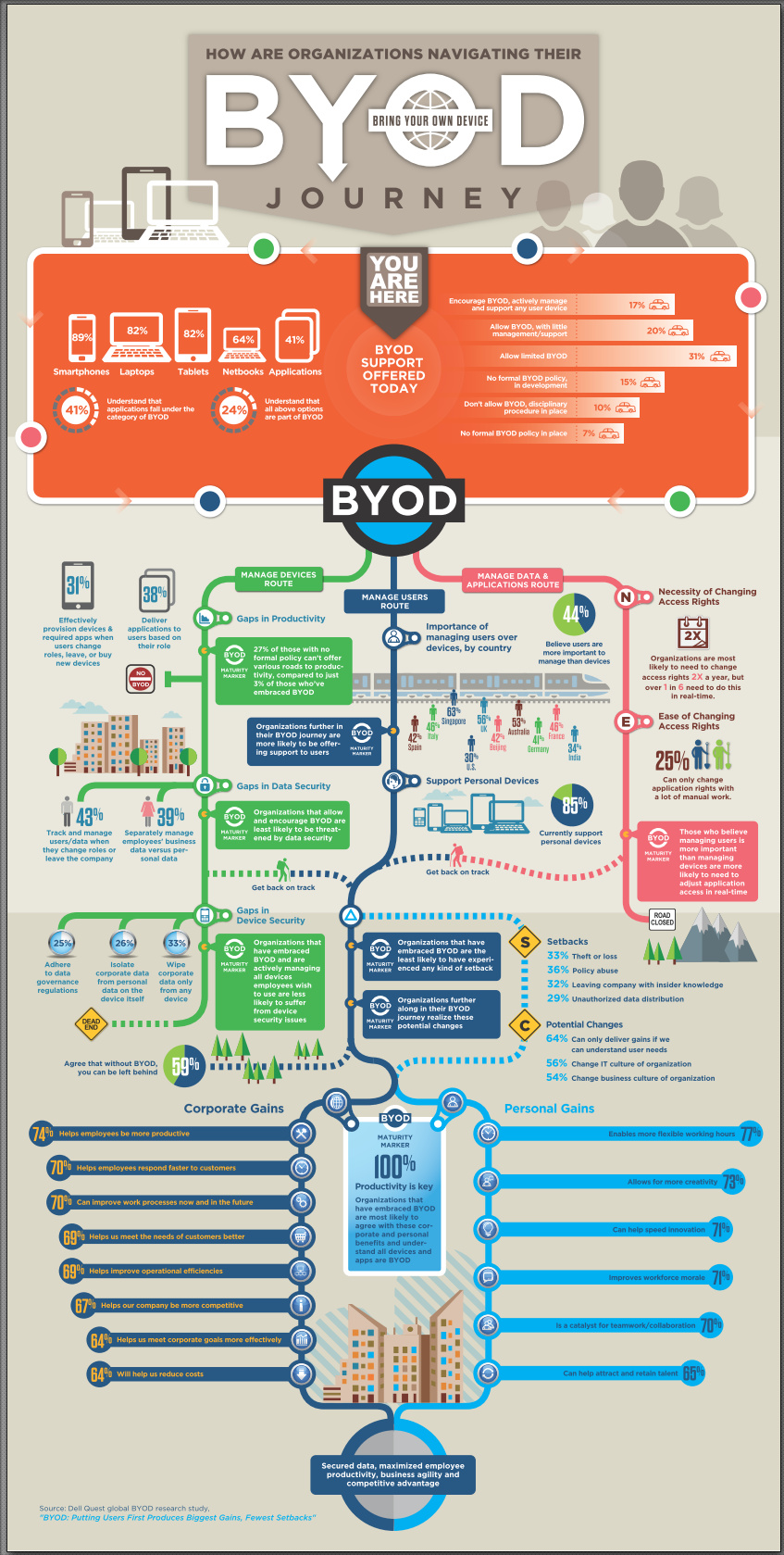
More mobility and freedom are provided by the BYOD policy, which we will discuss below. According to the results of Gartner 2013 statistical studies, Russia, Brazil, India and a number of other actively developing countries are now at the peak of the development of the BYOD trend. You can verify this by viewing the infographics, which we present below (some of the pictures are hidden under the spoilers, the language of the infographics is English).

More infographics
And now let's talk a little about the very concept of BYOD. The implementation of this approach requires careful planning and great attention to security issues, but the bonuses that individual employees and the company as a whole receive are more than worth the cost of time, money and other resources spent on this task.
Here is a short list of questions that you should pay attention to when planning events related to the implementation of BYOD:
- The number of mobile devices that will be connected to the enterprise network;
- Maintaining a balance between the security of business information and the preservation of the privacy of personal data of the user;
- Using encryption and cloud solutions;
- Preferential terms for the purchase of gadgets, partial payment of the cost of the device, as well as phone calls and Internet access at the expense of the company;
- The list of supported devices, supplemented by information on the minimum requirements for software and hardware, should be available to employees;
- It is necessary to provide an order of actions in case of loss of a device or dismissal of an employee.
The main benefit in case of using the BYOD policy is a comfortable working environment for employees and the opportunity to work remotely. The company can also save a significant amount of funds by reducing the cost of purchasing gadgets and their maintenance (however, in case of loss or breakdown of the device, a number of devices must be available for hot-swapping). The experience of a large number of enterprises shows that the implementation of the proposed concept also makes it possible to unload the support service thanks to the active help of the staff in setting up similar devices. Additional costs include the development of a BYOD strategy, the introduction of additional elements of the IT infrastructure, and the maintenance of a reserve of mobile devices.
One of the options for implementing the corporate BYOD policy is to enable employees to select from the list of supported devices those devices that are suitable for them. Dell offers a wide range of devices that fit well with the new concept, in particular, laptops, ultrabooks and tablets from the Latitude and XPS series. In our blog, Sergey Vilyanov has already talked about ultrabooks XPS 12 , XPS 13 , as well as about the Dell Latitude 10 tablet. These devices integrate very well with other solutions from Dell and, in addition, allow you to maximize the benefits of the “Bring your own device” strategy.
You can read more about BYOD policies in the Karen Ferris article published in the Official Magazine of the IT Service Management Forum. The Russian version of the article “BYOD is four letters from which CIOs are running in a panic,” by the same author, see this link .
Wyse PocketCloud - secure data exchange between devices of different classes with the ability to store files in the cloud

Dell offers several smart solutions that give you the ability to remotely access a computer or laptop with Windows and Mac OS X on board from their mobile gadgets. One of these solutions is PocketCloud Remote Desktop Pro . Thanks to this application, you can get remote access to both your files and images, as well as to the programs installed on your computer.
Versions of the program are available for iOS and Android (version 2.1 or higher), it is possible to connect to computers and laptops with Windows 8, Windows 7, Windows Vista, Windows XP, Windows Server 2003, Windows Server 2008, as well as Mac OS X 10.6 and Mac OS X 10.7 on board.
The application is optimized for use on smartphones and on tablets, has full support for multitasking, advanced accurate and sensitive touchpad for mouse and keyboard. The on-screen keyboard is activated automatically when the need arises. RDP specifications are automatically updated to the latest versions. The security of the application is provided by 128-bit encryption during data transfer.
The strengths of PocketCloud Remote Desktop, as well as the features of application settings are actively discussed on the w3bsit3-dns.com forum, additional information about the intricacies of this program can be found in the official wiki .
We also recommend you to pay attention to the PocketCloud Explore and PocketCloud Web applications, which are also developed by the Wyse division of Dell. The first application makes it possible to copy information from mobile devices to computers and back, use the cloud, and, besides, the load to support gadgets on Android and iOS, also knows how to work with tablets on Windows 8. The second application is a web-based management interface, with which you can copy the necessary files and folders from your computer to the cloud and back.
Enterproid divide - separate personal and workspace
Another useful solution within the framework of the BYOD concept makes it possible to use a mobile device, both for work and leisure, protecting the employer from the personal information of employees and at the same time maintaining a high level of security of corporate data.
Divide creates two isolated profiles on Android and iOS devices, separating the ones you need to work from personal applications. On Habré, this platform has already been mentioned , we will try to complement what was written a little.

The solution from Enterproid supports tablets and smartphones with Android older than version 2.2 on board, as well as devices from Apple with a version of the operating system not lower than iOS6.
All information inside the corporate profile of the gadget is encrypted using a symmetric AES block encryption algorithm with a 256-bit key.
In this solution, the system administrator through a web interface can remotely install business applications, manage security policies, determine the coordinates of the device, as well as “clear” the corporate profile of the device in case of loss of the device. The connection of the corporate profile of the device with the cloud is established via VPN, user applications from the personal profile are connected to the Internet directly. The system administrator does not have access to the device’s personal profile.
Of the strengths of Divide, I would like to note the fast switching between applications from a personal and corporate profile, as well as good prospects for further improving the security of the platform at the hardware level thanks to the close cooperation of Enterproid with Qualcomm. In particular, the teams of both companies are actively working on using the capabilities of the TrustZone technology to even more safely separate the Divide profiles in tablets and smartphones on Android. Last year's news that AMD is also adopting the TrustZone technology , smoothly expanding its sphere of interest in the direction of mobile devices, also gives reason to rejoice.
Read more about the Divide platform below under the spoiler:
Interview with the creators of the Enterproid divide - Andrew Toy and Alexander Trewby
In order to better understand the technology, it will be useful to watch a video interview with CEO Enterproid - Andrew Toy :
and also read the text version of the Divide co-founder interview for Computer Business Review: Q & A: Enterproid's CCO & co-founder Alexander Trewby
In addition to the approach proposed by Enterproid for secure access to corporate data from mobile devices, some large companies also use so-called Mobile Device Management (MDM) solutions. However, in applications of this type, the ability to install applications for personal use is severely limited, in this case only business software is available. In addition, all user actions are actively monitored by a team of IT administrators, not leaving even a small piece of personal space, and this is contrary to the BYOD policy.
Another possible solution that could help ensure the security of business information on mobile devices is virtualization. But the need for a hypervisor, as well as the high demands on the hardware of the devices, make it impossible to use it for most devices at this stage of technology development. On Habré, they already wrote about the developments of students of the Academic University of St. Petersburg in the field of Android-based device virtualization ( part 1 , part 2 ), but it’s still far from the final stage of development.
At the moment, Enterproid's Divide is the best solution within the framework of the BYOD concept for mobile devices based on Android and iOS. Read more about the capabilities of this platform in the article “Implementing Your BYOD Mobility Strategy” . For more information about the nuances of iOS-based gadgets with WiFi, see Habrastia and "Wi-Fi Features in Apple iOS and Implications for Organizations' Networks . "
and also read the text version of the Divide co-founder interview for Computer Business Review: Q & A: Enterproid's CCO & co-founder Alexander Trewby
In addition to the approach proposed by Enterproid for secure access to corporate data from mobile devices, some large companies also use so-called Mobile Device Management (MDM) solutions. However, in applications of this type, the ability to install applications for personal use is severely limited, in this case only business software is available. In addition, all user actions are actively monitored by a team of IT administrators, not leaving even a small piece of personal space, and this is contrary to the BYOD policy.
Another possible solution that could help ensure the security of business information on mobile devices is virtualization. But the need for a hypervisor, as well as the high demands on the hardware of the devices, make it impossible to use it for most devices at this stage of technology development. On Habré, they already wrote about the developments of students of the Academic University of St. Petersburg in the field of Android-based device virtualization ( part 1 , part 2 ), but it’s still far from the final stage of development.
At the moment, Enterproid's Divide is the best solution within the framework of the BYOD concept for mobile devices based on Android and iOS. Read more about the capabilities of this platform in the article “Implementing Your BYOD Mobility Strategy” . For more information about the nuances of iOS-based gadgets with WiFi, see Habrastia and "Wi-Fi Features in Apple iOS and Implications for Organizations' Networks . "
PowerConnect ClearPass W Series - Dell's Complete Hardware and Software Solution

Dell, in addition to software solutions that help implement the BYOD concept, as well as high-quality gadgets that fit well into this corporate policy, offers several integrated solutions that provide secure access to business information from mobile devices. One of these solutions is the PowerConnect ClearPass W-series , which we'll talk about below.
This complex product provides a high level of protection and scalability, and also makes it possible to integrate a variety of devices with Windows, Mac OS X, Android and iOS on board into a corporate network.
PowerConnect W ClearPass100 and PowerConnect W ClearPass2500's intuitive and user-friendly interface allows employees without technical training to easily provide guest access or access to personal devices, as well as manage without affecting the integrity of the network and without overloading IT support services.
Server specifications, as well as detailed information about the capabilities of this integrated solution from Dell, see below under the spoiler:
PowerConnect W ClearPass100 and PowerConnect W ClearPass2500 - Specifications and Features
Security and Scalability:
Guest Access Functionality:
In addition, for devices connected within the framework of BYOD, you can fine-tune the profiles of user groups depending on the devices used, running applications and their location. There is a possibility of remote cleaning of corporate information from the gadgets used for work, in case of their loss.
Technical characteristics of the two configurations of the considered solution are given below in the form of a table.
Read more about the PowerConnect ClearPass W-series on the official website .
- Each user is given a unique username and password. The solution provides easy integration with existing Active Directory directories.
- For guest and device accounts, the Remote Authentication Dial-In User Service ( RADIUS ) embedded database is used.
- Integrating a short messaging service (SMS) allows you to send security keys for wireless communication over an additional channel out of range, so you get scalable guest access with encryption.
- High scalability in the range of 50 to several thousand users provides tremendous opportunities for the development of the company. By purchasing the necessary license for the end user, you can use it as a basis for increasing functionality.
- The PowerConnect ClearPass W-Series lineup supports backing up all or individual configuration components and reports in real time or on a scheduled schedule, including when using file sharing based on FTP, FTP-over-SSL and SMB protocols.
- It is possible to delete or automatically terminate temporary accounts.
- Activity of guest accounts, as well as employees providing all guest access cases can be monitored by creating reports.
Guest Access Functionality:
- Easy to use self-registration portal.
- Support for various popular devices with guest client access, as well as personal devices: from multimedia phones to laptops, tablets and desktops.
- The ability to assign different access privileges for different types of users.
- Customizable login pages that allow you to use your brand and create unique user experiences.
In addition, for devices connected within the framework of BYOD, you can fine-tune the profiles of user groups depending on the devices used, running applications and their location. There is a possibility of remote cleaning of corporate information from the gadgets used for work, in case of their loss.
Technical characteristics of the two configurations of the considered solution are given below in the form of a table.
| PowerConnect W ClearPass100 | PowerConnect W ClearPass2500 | |
|---|---|---|
| PERFORMANCE | ||
| Maximum number of simultaneously connected visitors | 5,000 | 25,000 |
| CPU | Two quad-core Intel Xeon 2.66 GHz X3450 processors | Two quad-core Intel Xeon 2.66 GHz X5650 processors |
| Memory | 8 GB | 48 GB |
| Hard drives | Two 3.5-inch 250 GB SATA hard drives (7,200 rpm) | Four 2.5-inch, 300 GB (10,000 rpm) SAS hot-swappable drives |
| PERC RAID ( info ) | RAID-1 Controller PERC H200 | RAID controller PERC 6 / I SAS |
| Ports | Four USB 2.0 ports, one serial port, two video connectors | Four USB 2.0 ports, one serial port, two video connectors |
| BODY | ||
| Rack mounting: 1U rack mount enclosure, sliding guides included | + | + |
| Dimensions (depth x width x height) | 39.37 x 43.1 x 4.26 cm | 77.2 x 48.24 x 4.26 cm |
| Weight (unpacked) | 21.4 lbs / 9.73 kg | 39 pounds / 17.73 kg |
| RoHS compliant | + | + |
| OPERATING CONDITIONS | ||
| Working temperature | 10 to 35 ° C (50 to 95 ° F) | 10 to 35 ° C (50 to 95 ° F) |
| Storage temperature | –40 to 65 ° C (–40 to 149 ° F) | –40 to 65 ° C (–40 to 149 ° F) |
| NUTRITION | ||
| Power Supply | One | Two |
| AC input voltage / frequency | 110/220 V ~, 50/60 Hz with automatic selection | 110/220 V ~, 50/60 Hz with automatic selection |
| Maximum power consumption | 250 W | 717 W |
| Two Gigabit Ethernet ports | + | + |
Read more about the PowerConnect ClearPass W-series on the official website .
Dell KACE is another integrated solution from Dell that allows you to incorporate user gadgets into your corporate IT infrastructure. The hardware component of KACE is represented by two configurations - Dell KACE K1000 and Dell KACE K2000 . You can get acquainted with the program part in detail by watching videos from the Dell KACE Systems Management channel on Youtube, and you will find reviews from the heads of IT departments of companies that already use this solution (all videos are in English).
More about Dell KACE, we will tell you more in our blog. And our small review article on the modern concept of “Bring your own device” will end here.
Dell still has a lot of interesting solutions to maximize the benefits of BYOD policy, but read about them in the following articles.
Source: https://habr.com/ru/post/183098/
All Articles