Skype spam campaign endangered hundreds of thousands of users.
Methods of spreading malware are key to cybercriminals, since the sooner this threat spreads, the more damage it can cause. In mid-May 2013, we observed a massive spam campaign on Skype and Gtalk, in which attackers used social engineering techniques.
In less than 48 hours from the start of this campaign, more than half a million users followed the malicious links that were sent in messages. It is important to note that these links were shortened and were converted to the full address using various web services, through which we were able to get statistics of users navigating through these links. The use of the Google URL Shortener service has been fixed, whose addresses begin with goo.gl, with more than 490,000 users following these links.
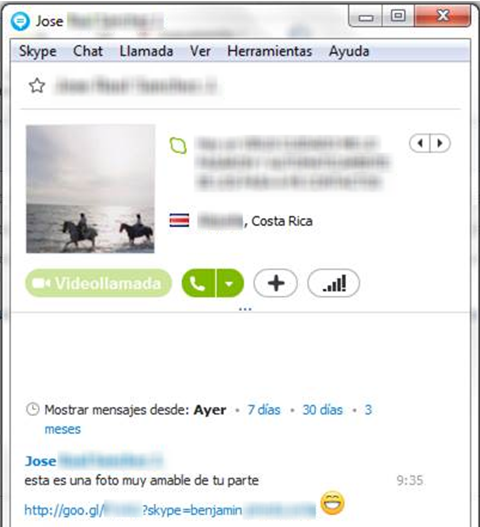
Fig. One of the spam messages.
')
One of the most important factors in this spam campaign is that its victims were users all over the world. The most affected users of the following countries: Russia, Germany, Brazil, Colombia, Mexico, USA. In line with this, it can be assumed that the attackers used their language for each country in spam messages. This greatly increased the effectiveness of the spam campaign. In the next screenshot, you can see how many clicks on the links were made within a few hours from the start of the spam campaign.
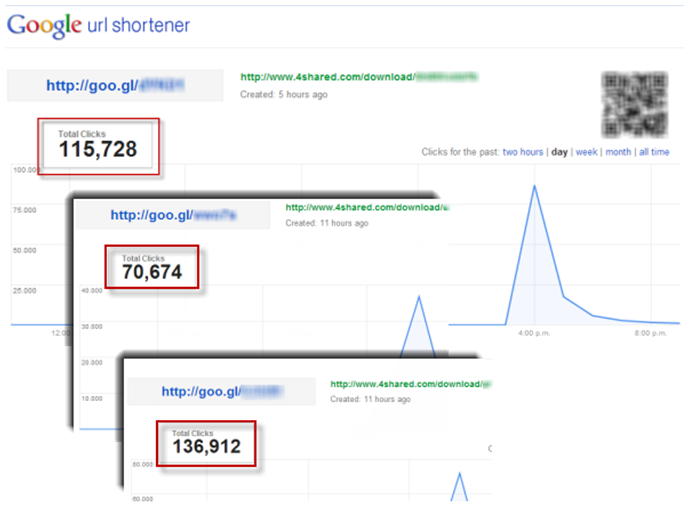
Fig. Statistics go on shortened link service Google URL Shortener.
All these links redirected users to download a malicious program that shows up as Win32 / PowerLoader.A . This malicious program downloads and executes the Dorkbot worm dropper , which has the functionality of sending messages to the user's contacts every 15 minutes.
According to the service, which converts URLs to the usual format, 83% of all transitions were performed from systems running Windows. The remaining 17% share among themselves iOS, Mac OS X, Linux, BlackBerry.
After some time, cybercriminals switched to using other link deployment services other than the Google URL Shortener. Namely: bit.ly, ow.ly, urlq.d, is.gd, fur.ly. This change did not actually affect the speed at which the threat spreads, as users continued to follow the links generated by the infected systems.
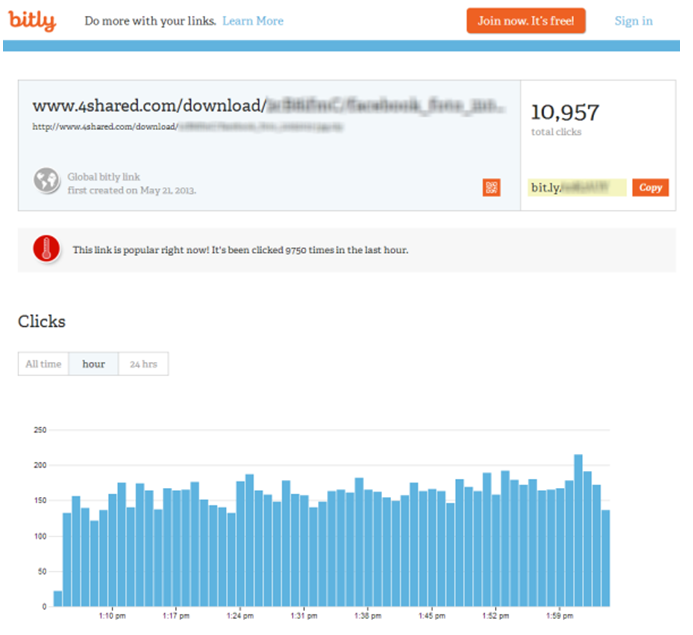
Fig. Statistics of transitions under the shortened link of the bitly service.
Fortunately, most link deployment services have blocked malicious links, but attackers can still give instructions to bots that will allow them to continue the attack in the future. In accordance with the data of the bit.ly service, the majority of link clicks were made from Germany, for which more than 8,000 link clicks were recorded.
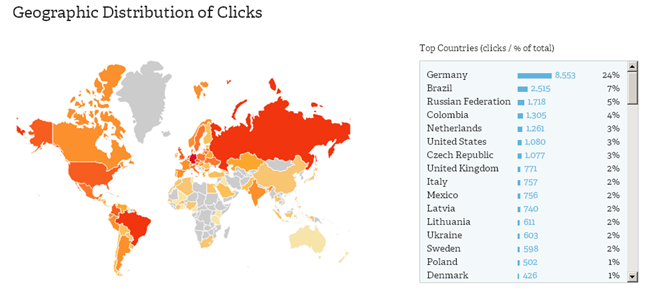
Fig. Statistics by countries, in which the users of which countries are most often referred by malicious links.
The malicious code that was used to deliver to users' computers via links in messages was a bootloader based on Power Loader and the main purpose of which was to download a Dorkbot dropper.
In less than 48 hours from the start of this campaign, more than half a million users followed the malicious links that were sent in messages. It is important to note that these links were shortened and were converted to the full address using various web services, through which we were able to get statistics of users navigating through these links. The use of the Google URL Shortener service has been fixed, whose addresses begin with goo.gl, with more than 490,000 users following these links.

Fig. One of the spam messages.
')
One of the most important factors in this spam campaign is that its victims were users all over the world. The most affected users of the following countries: Russia, Germany, Brazil, Colombia, Mexico, USA. In line with this, it can be assumed that the attackers used their language for each country in spam messages. This greatly increased the effectiveness of the spam campaign. In the next screenshot, you can see how many clicks on the links were made within a few hours from the start of the spam campaign.

Fig. Statistics go on shortened link service Google URL Shortener.
All these links redirected users to download a malicious program that shows up as Win32 / PowerLoader.A . This malicious program downloads and executes the Dorkbot worm dropper , which has the functionality of sending messages to the user's contacts every 15 minutes.
According to the service, which converts URLs to the usual format, 83% of all transitions were performed from systems running Windows. The remaining 17% share among themselves iOS, Mac OS X, Linux, BlackBerry.
After some time, cybercriminals switched to using other link deployment services other than the Google URL Shortener. Namely: bit.ly, ow.ly, urlq.d, is.gd, fur.ly. This change did not actually affect the speed at which the threat spreads, as users continued to follow the links generated by the infected systems.

Fig. Statistics of transitions under the shortened link of the bitly service.
Fortunately, most link deployment services have blocked malicious links, but attackers can still give instructions to bots that will allow them to continue the attack in the future. In accordance with the data of the bit.ly service, the majority of link clicks were made from Germany, for which more than 8,000 link clicks were recorded.

Fig. Statistics by countries, in which the users of which countries are most often referred by malicious links.
The malicious code that was used to deliver to users' computers via links in messages was a bootloader based on Power Loader and the main purpose of which was to download a Dorkbot dropper.
Source: https://habr.com/ru/post/182754/
All Articles