Competency model of a computer security specialist

Competence model is an attempt to create the most adequate model of a specialist, which would take into account the needs of the market for specialists in computer (information) security, the requirements set by enterprises for such employees, as well as the capabilities of the higher education institution to train such specialists.
I propose to get acquainted with the idea and make constructive suggestions.
')
Introduction
The supramental race of beings created the computer "Deep Thought" - the second in performance over the whole existence of time and the Universe - to find the Final Answer to the greatest question of Life, the Universe and All That. After seven and a half million years of computation, Deep Thought gave the answer: “Forty-two.” The reaction was:
- Forty-two! - screamed Lunkkuol. “Is that all you can say after seven and a half million years of work?”
“I checked everything very thoroughly,” said the computer, “and with all certainty I declare that this is the Answer.” It seems to me that if we are absolutely honest with you, the whole thing is that you yourself did not know what the Question is.
- But this is the Great Question! The Final Question of Life, the Universe and All That! - almost howled Lunkkuol.
“Yes,” said the computer in the voice of a sufferer who enlightens the fool. - And what is this question?
Douglas Adams “The Hitchhiker's Guide to the Galaxy”
Following the basic postulate of management that we cannot control what we cannot measure, it is necessary to create conditions for managing the training of specialists in computer security. The main question or goal that is posed in this work is to create the most adequate competence model of a specialist, which would take into account the needs of the market for such specialists, the requirements imposed by enterprises on such employees, as well as the capabilities of the higher education institution to train such specialists.
In addition, it is necessary to take into account advanced domestic and foreign experience in the field of information technology, psychology and recruitment. For the most part, a computer security specialist will be confronted with the work of modern information systems, as well as prevent unscrupulous people from taking over information of commercial value.
This paper is divided into three chapters. The first chapter gives an understanding of what to consider as a competency, what to consider as a competence model, what methods are used in practice to create a qualitative competence model of a specialist.
The second chapter describes the competency model, which was compiled as a result of the analysis, classification and generalization of the material association of computer and information technology enterprises (APCIT) according to the third generation GOS VPO standard for specialties related to information technology, as well as the competencies indicated by JSC “ Svyazinvest "for specialists in information and economic security. It is important to note that APKIT used the experience of such companies as ABBYY, Intel, Microsoft, Motorola, IBM, Oracle, 1C, EMC, Sun, Cisco, Luxoft, Kaspersky Lab, which are leaders in the information technology industry and their requirements for creating competency models. training specialists are based on the real needs of this market.
The third chapter provides a generalization of the resulting model of a specialist and an assessment of the existing level of training of specialists in computer security for the developed model. In addition, further paths are indicated to improve the competency model itself and to improve the educational process.
Chapter 1. Basic concepts, types and structure of competencies
Wireless telegraph is easy to understand. An ordinary telegraph looks like a very long cat: you pull on the tail in New York, and it meows in Los Angeles. Wireless is the same, but without a cat.
Albert Einstein
Core Competence Concepts
To begin with, we will designate the basic concepts with which we will operate, considering competencies. This is necessary for a uniform and clear understanding of the material presented. Given the variety of different definitions and interpretations used in theory and practice, it should be remembered that the definitions given are not true in the last resort, but only the options that are used in the stated material. The proposed definitions are not standardized, but they make it possible to correctly designate the basic terms used in this work.
Unfortunately, in the Russian language, several popular and frequently used expressions have historically taken root, including single-root words with the word “competence”. This is significantly confusing when trying to comprehend the essence of the concept of "competence" in relation to the training of specialists in the university and to the business in the field of personnel management. For example, we like to say: “He is incompetent,” “It is not within my area of expertise.” “He is incompetent” does not mean at all that a person does not possess any competencies. As a rule, behind these expressions lies an assessment of the level of authority of the subject. And absolutely nothing to do with the terminology used in the system of competencies.
First of all, let us denote the difference between the concepts of “competence” and “competence” []. They are based on the Latin root compete - I seek, I correspond, I come up.
Competence is a certain characteristic of a person, necessary for the performance of certain works and allowing its owner to obtain the necessary results of work.
Competence is the ability of an individual with a personal characteristic to solve work tasks to obtain the necessary work results.
In other words, competence is the standard of behavior required for a certain activity, and competence is the level of knowledge of this standard of behavior, that is, the final result of its application.
Key competencies - a set of competencies that allows an employee to perform their professional duties as effectively as possible.
ZUN - knowledge, skills, abilities.
PVK - professionally important qualities: individual qualities of the subject of activity, influencing the efficiency of the activity and the success of its development. “Professionally important qualities are qualities that are important for the profession, regardless of the particular company.”
A competency model is a structured set of necessary, identifiable, and measurable competencies with behavioral indicators.
Behavior indicators are standards of behavior that correspond to the effective actions of a person with a specific competence. At the same time, as a rule, the object is manifestations of a high level of competence.
Competence clusters are a set of competencies (usually from two to five) connected in a single semantic block. Most often, models distinguish such clusters as: intellectual (mental) activity, achievement of results, work with people, work with information.
Types of competencies
Speaking about the types of competencies, two significant points should be noted:
- species diversity of competences in the absence of standards;
- the existence of several classifications, that is, species diversity (there is not a single classification of types of competencies, there are many different classifications for various reasons. It is very problematic to orient in this variety of species. Many classifications are extremely inconvenient and obscure, which makes their use in practice extremely difficult. But One way or another, the current situation affects the practice of building a competency model).
In a variety of theoretical and practical materials on the topic of competence, you can find a variety of typologies. In world practice, there are examples of attempts to develop universal typologies and competency models that claim to be the world standard. For example, SHL - the world leader in the field of psychometric assessment and solution development - back in 2004 declared the creation of a universal basic competence structure by a group of consultants under the leadership of Professor Dave Bartram. The basic structure created by the Bartram group included 112 components headed by the so-called “Big Eight Competencies”. It is possible that global unification trends will soon lead to the emergence of a single standard generally accepted by all. Competences are a rather peculiar tool, so it is practically very difficult to create a single set of competencies that any university and any company can use.
In addition, one should not forget that competence must be measurable. That is, introducing competence, it is necessary to check it for the possibility of assessment. It is important to remember precisely when developing a competency model, since it is often tempting to include personal qualities of a social nature. For example, "justice." To measure the presence of this competence in a person is very problematic, since the concept of "fair" is largely relatively and difficult to identify.
Professional competencies are localized in scale. But a certain set of professional competencies is inherent in any position and / or specialty. This type of competence is a set of personal characteristics, as well as the knowledge and skills necessary to work effectively in a particular position. Considering that our classification of competencies is limited to university frameworks, professional competencies of positions and professional competencies of activities or professional areas should not be confused.
The professional competencies of the activities and areas are more generalized. And the professional competence of the position is limited to the specific company. For example, there may be competences of an employee of the pedagogical sphere - they are typical for all specialists engaged in pedagogical activities, regardless of the organization in which they work, or they may be the professional competencies of a teacher of a specific educational organization. Speaking of professional competencies as a kind of competencies, we are talking about them.
Table 1
 Management competencies are the most localized and complex type of competencies. These are the competencies necessary for the fulfillment of managerial duties to those who will occupy managerial positions, whether it be personnel management or system administration. Strangely enough, the development of managerial competencies is the most difficult - the temptation to create a model of an ideal supermanager is too great, which is unlikely to be implemented in practice. Therefore, when developing, it is recommended to include in the list of managerial competencies an optimal set based on the principle of necessary and sufficient competences.
Management competencies are the most localized and complex type of competencies. These are the competencies necessary for the fulfillment of managerial duties to those who will occupy managerial positions, whether it be personnel management or system administration. Strangely enough, the development of managerial competencies is the most difficult - the temptation to create a model of an ideal supermanager is too great, which is unlikely to be implemented in practice. Therefore, when developing, it is recommended to include in the list of managerial competencies an optimal set based on the principle of necessary and sufficient competences.Competency structure
The competency framework serves as the basis for developing a competency model. We will discuss further what constitutes a competency model.
And now about our own competence structure - about what elements competencies consist of and what these elements represent, see table. one.
From the table we see that the structure of competence is quite complex, including a set of elements, the combination of which makes, in fact, competence the universal tool we are talking about. From the presented structure, it becomes clear why the competence cannot be considered only the ZUN or the PWC, which are only an element of the competence.
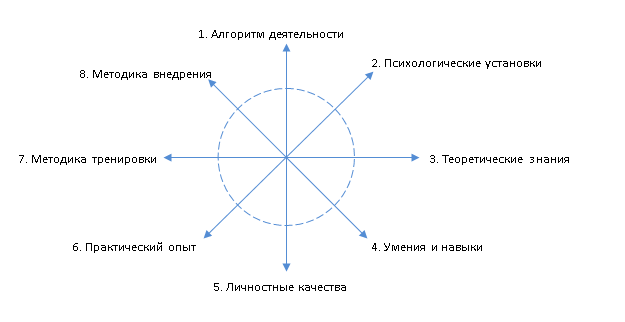
Figure 1. The full universal competence structure (START).
It should be noted that in the theory and practice of building a competence model there are different types of competency structures. For example, the so-called START is actively used - a full universal competence structure (see Fig. 1).
In addition, many do not use off-the-shelf developments, fundamentally go their own way and develop their own competency structures. This is justified and effective only if experienced specialists are involved in the development of the model, since for novice developers this task is either not within the strength or threatens to create an incorrect and inefficiently working competence structure.
Competency model
A model is a logical description of components and functions that reflect the essential properties of the object being modeled.
A competency model is a logical description of the elements and functions of competencies. The competence model contains a detailed description of the standards of human behavior in a particular position leading to the achievement of official goals.
The degree of detail in the competency model depends on the goals for which the model is applied. Some seek to cover the whole range of information and develop a model for all occasions. Such a model, as a rule, is very difficult to use and ineffective. In addition, it is very difficult to develop, since, according to experts, the difference between many competences is extremely small and hardly distinguishable. The experience of recent years of applying the competency model shows that the set of competencies should be optimal and include only key standards of behavior.
Our task is to show the logic and technology of development and application of the competency model in a simple version.
The role of the competency model in the management system. Areas of use
Competences are closely connected with the strategy of the educational process, respectively, their purpose is to contribute to the realization of strategic goals. The competence model solves this problem through certain functions and areas of application of these functions. Applications are shown below. Functions are a type of specific activity through which the competence model works in a particular area. For example, in the field of personnel training and development, the competence model works through assessments of the zone of missing competencies for an employee. Consider them in more detail.
As mentioned at the outset, the competency model is a multifunctional and almost universal tool, so it works in various areas of management. In the first place - in the management of human resources.
Content of competency model
As it has already become clear from the above, the content of the competency model includes:
- a complete set of competencies and behavioral indicators;
-description of standards of conduct or standards of action leading to the implementation of the tasks and goals;
- levels of competence (if they are provided and applied).
In itself, the content of the model is not a guarantee for creating a tool to improve the efficiency of the educational and working process. The effectiveness of the model depends on the quality of the content. And the result of using the model is directly related to the quality of organizational activity and the harmony of the entire management system. Unfortunately, very often the competence models, which include all the necessary elements, nevertheless, do not give the expected effect, but only spend resources on their maintenance. Often the reason for this situation is the poor quality of the model.
The qualitative content of the model must meet the following criteria:
1. Compliance with the strategic goals of the industry. This means that the developed competences should contribute to the further activities of graduates in various companies in the core industry, aimed at achieving these goals, and not include the entire conceivable and inconceivable set of possible competencies.
2. Usefulness for all who participate in its operation (specialists of various companies using the model as a tool, teachers). It should be remembered that the subject of the model are students who also have their goals, their motives for work and their needs. This means that the model should also be of interest to students and be useful to them.
3. The optimal set of model elements, the absence of repetitions and intersections.
4. Competence measurability and availability of accounting for expected changes. The optimal set of competencies and their measurability are aimed at the comfort of operating the model, the objectivity of measurements and the possibility of effective use of the results obtained. The presence of the accounting system of expected changes allows you to get the desired range of application of the system and makes the system useful to all participants. For example, assessment of students and teachers on the basis of the competency model, which successfully replaces attestation, with a change accounting system, makes it possible to competently plan career development, trace the dynamics of changes, and tie the results to wages. It also establishes the relationship between the development of a student and the growth of his future salary, making his expectations realistic.
5. Simplicity and transparency of the competency model. A very important aspect of the content of the competency model is its volume. Some manage to develop such a voluminous model that its description is a weighty volume with a multi-page extensive description of hundreds of competencies and multiple examples. Everyone knows perfectly well that the more extensive any instruction is, the less chance it has of being at least fully read, and not something studied. This rule also applies to the description of the competency model, although it does not mean that the documentation describing the system should be stingy and extremely short, but when creating it, the optimality rule should be observed.
Competences should be not only accurate, but also politically correct, not affecting self-esteem. For example, is it correct to measure a person’s honesty and what to do if its level is insufficient?
The competency model can be simplified (without competency levels) and more complex (with levels). The simple model “Competences without level” contains only the basic standards of behavior and, as a rule, the same set of behavioral indicators for all. It does not take into account the levels of training. The competence model may contain so-called levels of competence and allows you to cover a wider range of students' training levels and take into account various nuances. And such a model is called “Competence by level”. In this case, the behavior indicators for the same specialties belonging to different levels will be different. For example, for the administrator and the manager, some competences may well coincide, but the level of their manifestation is different, depending on the level of authority and responsibility.
The structure of the competency model is clearly demonstrated by a schematic image. As an example, below is a diagram of the so-called format-cluster competence model (see Fig. 2).

Figure 2. Format-cluster model of competencies.
Competency profile
The profile of competences, in essence, is a set of competencies that an employee must have who meets the position held, or a graduate of a specialty who meets the requirements for university graduates. But this is not just a set, but a list, including the necessary level of development of each competence for a particular specialty / position. The profile of competencies is most often made up in the form of a diagram that allows you to visually illustrate the required level. After assessing the employee’s competency level, the charts are compared. The discrepancies between the required level and the actual one become obvious. The difference between them - this is the area of training and development of the employee.
Thus, the competency profile is a very simple and convenient “visual aid” when using the competency model. An example of such a profile is shown in Fig. 3

It is important to note that the competency profile is not static, it has the property of changing. Moreover, it is the required levels of competencies that change. This is due to human development over time, as well as changes in qualification requirements. With the development of a competency model, the set of competencies can also change. Therefore, the developed competency profiles cannot be used for a long time, they have a certain “shelf life”. But this does not mean that they need to be developed every time. They require checking for relevance before use and, if necessary, updating.
Chapter 2. Versatile competence model of a computer security specialist
Opening an order is not an easy task, but if it is found, it is not at all difficult to understand.
Rene Descartes
Sources [2] close to the Ministry of Education and Science of the Russian Federation suggest initially classifying the competencies of graduates into two large groups:
- General competences (universal, key, superprofessional);
- Subject-specialized competencies (professional).
So, summing up the previous paragraph, we say that the main task of the competence-based approach in education is to establish the correspondence between the capabilities of an educational institution, the requirements of the real economy and the abilities of the student.
Since higher educational institutions are at the stage of waiting for the standards of the third generation, or are trying to somehow prove on their own that the standard of the third generation differs from the standard of the second generation only by renaming the subject for competence; Students and applicants are in a state of happy ignorance, what awaits them after graduation, and the real sector of the economy is struggling with the consequences of the financial and economic crises, it is proposed to consider the requirements of enterprises for computer security specialists.
The search for information on open sources (in fact, and on closed sources too) did not yield results precisely on the competence model of a computer security specialist in the state educational system of the higher professional education of a new generation. However, an interesting article was found by S. M. Avdoshin [4]. In the article, the author summarizes the experience gained when working in a project to develop information standards for the information technology industry [5]. So, this project was carried out under the auspices of the Association of Computer and Information Technology Enterprises (APCIT) and on the website [6] of this association, the following competence models of specialists are freely available:
1. Programmer;
2. System architect;
3. Information Systems Specialist;
4. System analyst;
5. Specialist in system administration;
6. Information Technology Manager;
7. Database Administrator.
Why do we need all these seemingly irrelevant competencies? The fact is that the basis of computer and information security is the postulate that only an integrated approach can bring success in the field of security. Information security is a relatively young, rapidly developing field of information technology, for the successful assimilation of which it is important to learn from the very beginning a modern basis coordinated with other branches of information technology [7]. Those.All of the above competences in the field of information technology are necessary as a basis for building a high-quality, versatile competence model of a computer security specialist.
Competency models created by APKIT are divided into qualification levels from the lowest level 1 (assistant system administrator, personal computer operator) to the highest level 8 (information technology manager with a degree and experience in a management position for at least 5 years). In addition, according to these qualification levels, the competency models proposed by APCIT subdivide the training of bachelors, specialists and masters.
According to the current standard of higher education for the specialty "Computer Security" [8]: "The standard time for mastering the basic educational program for training an information security specialist in the specialty 075200 - computer security for full-time education is 5 years 6 months." Those.Students take 6 courses of study, therefore, according to some competency-based models developed at APCIT, it is possible to use the qualification levels of masters as a basis.
Based on the above, we select the following qualification levels:
1. Programmer - 3 qualification level;
2. System architect - 4 qualification level;
3. Information systems specialist - 3 qualification level;
4. System analyst - 3 qualification level;
5. System administration specialist - 5th qualification level;
6. Information Technology Manager - 4 qualification level;
7. Database Administrator - 4 qualification level.
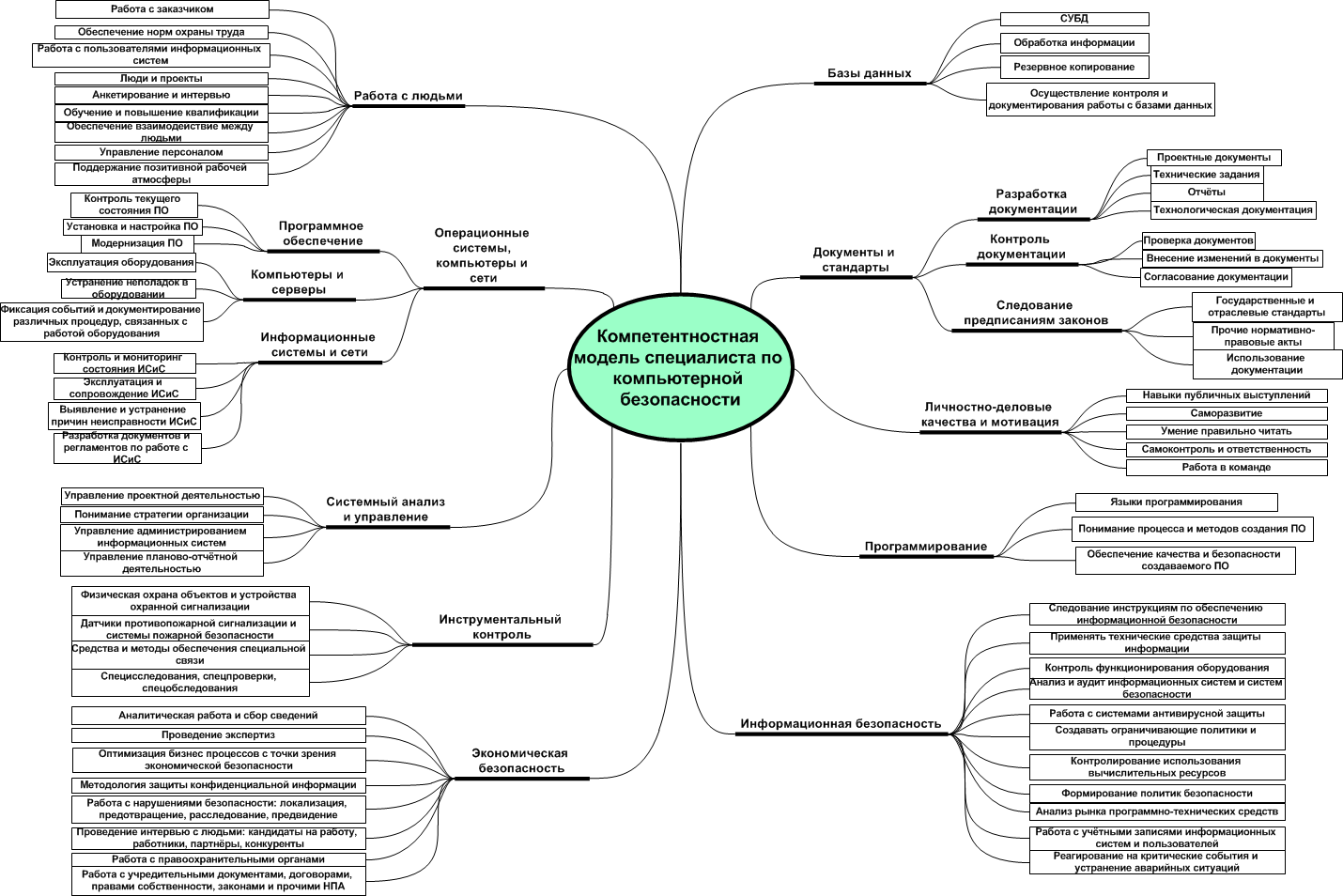
So, if you simply combine by the addition method those skills and abilities that correspond to the above list, you will get more than 2000 positions containing skills and abilities, and they will be repeated, because we are talking about one industry. If you select only unique skills and abilities peculiar to all the above basic competence models in the field of information technologies, you will get 673 unique skills and skills that experts from APCIT considered necessary to be included in the standard of training of relevant profiles.
But with a list of more than six hundred skills and abilities (not counting knowledge), it’s quite difficult to work due to the specific perception of information by the human brain [9], it is necessary to somehow classify these skills and abilities to reduce the complexity and complexity of creating competence models.
Following the methodology of object-oriented analysis and design [10], so that the model of a specialist looks like a model, and not as a pile of hard-to-read and difficult-to-distinguish competencies based on skills. It is necessary to make a classification of competencies. Since there are no methods for creating an ideal classification, you will have to rely on your own intuition and experience.
The first thing that comes to mind is the following classification:
subdivision first (subject)
1. Mathematics;
2. Physics;
3. Information technology;
4. Economics and governing documents;
5. Security in a broad sense.
But how does this differ from the GOSE VPO 2 generations, in which exactly the knowledge model goes. Perhaps nothing. Therefore, it is better to propose a classification based on skills, but not knowledge. Knowledge in the model should be in symbiosis with skills.
The following initial classification of competencies is proposed:
1. Documents and standards (global and domestic standards for information technology, information protection, health and fire safety, civil defense, quality standards, federal laws, the Labor Code, FSTEC guidelines, other regulatory and legal acts, internal and project documentation)
2. Personal business qualities and motivation (abilities, self-development, resistance to stress, the ability to mobilize their forces in a short period of time, the ability to persuade, the ability to listen, the ability to subjugate the crowd, focus on results, a high level of self-motivation)
3. Programming (languages programming, the process of software development, quality assurance methods of software products, inspections, etc., etc.)
4. Operating systems, computers and networks (ideology, architecture, design, implementation and support)
5. basics of data (creation, administration, protection)
6. System analysis and management (analysis of all information systems, business processes, infrastructure management)
7. Work with people (interaction with customers, personnel management, interaction with users, work with permitting and authorized bodies, work with government officials)
8. Economic security (economics, accounting and audit basics, forms of ownership, interests of criminals, physical security of objects organization of the security regime in the enterprise, understanding the interaction of all company structures, the ability to conduct internal investigations, interaction with the Ministry of Internal Affairs, the Federal Security Service and other security agencies, understanding of new business intelligence, psychology foundations)
9. Tool control (to prevent leakage of information on the physical fields, detection of bookmarks and bugs, check the equipment for the presence in it of extraneous embedded devices)
10. Information security (encryption, VPN, FireWall, Antivirus, IDS, access control, passwords, data recovery, security policies).
In the course of further work on classifications, skills and abilities were divided into subclasses, which are given in subsequent sections of this chapter.
Documents and standards
Documentation development
Project documents
- Develop project documents
- Develop specific provisions of the project charter
- Keep project accounting
- Develop project documentation using graphical specification languages
- Document results
- Develop a package of contractual documents
- Participate in the preparation of technical specifications
- Participate in the development of technical specifications
- Draw up a technical task
- ,
- ,
- , ,
- -
- ,
- ,
- ,
- ,
- , ,
- ,
- ,
- ,
- ,
- -
- -
- ,
- —
- , , ,
- -
- -
- ,
- ,
- , , , , , , ,
- , , , , , , , ,
- , , ,
- , , , , , ,
- , , , , , , , , , , , , , ,
- , , , , , , ,
- , , , , , , , , ,
- , , , , , , ,
- , , , , , , , , , ,
- -
- , ,
- , ,
- , ,
- -
- , ,
- , ,
- , ,
- , ,
- , ,
- , ,
- -
- ,
- , ,
- -
- -
- -
- -
- -
- -
- -
- ,
- /
- -
- -
- - -
- -
,
- ,
- ,
- -
- , ,
- -
- , -
- –
- - -
- -
- ,
- -
- -
- -
- -
- ,
- , -
- ,
- ,
- To develop schemes and procedures for disaster recovery of the computer network
- Develop a disaster recovery network computing network
- Carry out presentations of infrastructure development plans
- Maintain records and analysis of utilization of network resources
- Keep records and analysis of indicators of operating conditions
DBMS
- Use software and hardware to collect and process data
- Install and configure the necessary updates for database management systems
- Analyze the market for modern database management systems and databases
- Update database software
- Install and configure software tools for data collection
- Predict performance and required database resources
- Maintain and update knowledge of database administration
- Choose a database and database provider
- Identify and troubleshoot database management systems
- Organize and ensure the smooth functioning of database management systems and databases
- Process information
- Analyze information
- Structure information
- Save data to removable media
- Collect information
- Recover information
- Have a personal data processing toolkit
- Recover data in database
- Prepare and save backup data
- Create a data archiving plan
- Development of regulations for the collection and storage of information
- Keep a log of data archiving and media usage
- Monitor database structural changes
- Monitor database usage
- Conduct a feasibility study of the introduction of new database management systems and databases
- Apply regulatory and technical documentation when using database management systems and databases
- Prepare reports on the functioning of database management systems
Project Management
- Analyze project risks
- Manage project content
- Check compliance of the work performed with the requirements of the project documentation
- Project Transition Management
- Project Development Management
- Manage project integration
- Describe the main design decisions
- Manage project budget
- Have a project management tool
- Apply project management tools
- Supervise operators and technicians on duty and coordinate their activities
- Determine the composition and amount of information to build an adequate, complete and consistent model
- Manage project resources
- Efficiently allocate resources during the project
- Manage project risk
- Project Development Management
- Assess the resources needed to complete the work.
- Evaluation and improvement of project performance
- Form recommendations for adjusting the results of work
- Product Acceptance Management
- Manage project quality
- Monitor the allocation of resources during the project.
- Work with various types of source data on the subject area
- Manage project acceptance work
- Check the compliance of the work performed with the requirements of the project documentation
- Manage project contracts
- Develop a list of works in stages
- Develop a project charter
- Manage project schedule
- Manage work on project technologies
- Adapt new trends in scientific and technological development
- Evaluate and justify the complexity and timing of analytical work
- Analyze the organization's development strategy
- Monitor documentation update
- Justify proposals for the implementation of an information technology strategy
- Determine the method of work
- Conduct a comprehensive analysis of problems in the organization of the customer’s enterprise and identify their causes
- Assess the organization’s information resource needs
- Monitor the performance of work transferred to the outsourcing
- Monitor compliance with the norms of costs of material resources and time
- Identify and describe enterprise business processes
- Identify sources of research funding
- Determine the limits of applicability of systems analysis methods
- Monitor the work of suppliers and subcontractors
- Control the completion of relevant documentation
- Control the quality of the supplied products and services
- Plan the development of the technical base of the organization
- Simulate the organization's activities
- To form functional requirements for an information system for solving business problems of an enterprise
- Formulate recommendations for improving the efficiency of business processes
- Work with various types of basic data on the state of the information systems market
- Form scientific units
- Predict the timing of upgrading the information infrastructure
- Organize work on the integration of systems
- Analyze the causes of problems, incidents
- Develop technical and managerial solutions for replacing and upgrading software and hardware
- Analyze the results of monitoring the use of the computer network
- Analyze technological and architectural solutions in the field of informatization
- Analyze the quality of performance of work for compliance with the instructions for the operation of software and hardware
- Analyze accident reports
- Identify bottlenecks in the functioning of information systems
- Analyze system and network event logs
- To find ways to improve the efficiency of the enterprise using the capabilities of information systems
- Analyze operating modes and operating conditions
- Analyze failure statistics
- Monitor the implementation of the procedure for debiting technical devices
- Assess the quality of the built system architecture (adequacy, completeness, consistency)
- Formulate tasks in terms of system analysis
- Regularly check the reports on the results of the inventory and write-off of software and hardware
- Ensure the interaction of information systems with the use of modern technological tools and standards
- Control the availability and movement of software and hardware
- Determine the impact of system administration on the processes of other divisions
- Determine the rules of modernization, modification and work to improve the reliability and durability
- Assess the state of software and hardware resources
- Assess tool performance
- To form the requirements for the configuration of local computer networks necessary for the operation of the information system
- Approve a schedule for upgrading software and hardware
- Plan technical work
- Control the quality and volume of work performed
- Prepare proposals for making decisions on the purchase of equipment and software
- Monitor the progress of work
- Analyze the dynamics of changes in indicators
- Develop a schedule of test checks and preventive examinations
- Analyze the results of the work
- Analyze comments on the results of approvals
- Monitor the implementation of the schedule of test checks and preventive inspections
- Process statistics
- Supervise the execution of works in accordance with the technical specifications
- Create reports
- Monitor the schedules of inspections of technical documentation, regulations, instructions
- Prepare reports for IT management
- Develop a work schedule in stages
- Create analytical reports on the review of new hardware and software solutions
- Plan and adjust the work
- Track approved maintenance schedules
- Identify and articulate priorities
- Determine the necessary monitoring parameters
- Make analytical reports
- Monitor equipment delivery schedules and work progress
- Make and justify conclusions and make recommendations
Work with the customer
- Agree on the timing of preventive maintenance
- Develop techniques for analyzing customer needs in the field of information
- Conduct a business conversation with a group of customer representatives
- Conduct a business conversation with a customer representative
- Analyze customer requirements for the use of information systems
- Identify and document the conceptual apparatus, basic ideas, methods and processes of the customer's subject area
- Use terminology, conceptual apparatus, basic ideas, methods and processes on the customer's subject area
- Evaluate a business problem from a customer’s point of view.
- Choose with the customer the best ways to solve problems
- Prepare materials for presentation to the customer
- Negotiate
- Be proficient in customer terminology in one or more subject areas
- Negotiate with the management of the customer’s enterprise
- Hold meetings and negotiations
- Conduct interviews with key employees of the customer
- Document the results of stakeholder engagement in the process of developing, testing and implementing computer systems
- Interact with customer service inside and outside the organization
- Understand customer terminology
- Formulate a commercial offer
- To control the observance of technological, production and labor discipline by personnel
- Follow the rules of conduct in emergency situations.
- Monitor compliance with occupational health and hygiene requirements
- Comply with labor protection requirements
- Provide working conditions in accordance with the tasks performed
- Monitor compliance with fire safety requirements
- Analyze the efficiency of working time
- Monitor compliance with labor protection requirements
- Monitor and analyze the efficiency of working time
- Process the results of the survey
- To structure and analyze requests of structural divisions
- Analyze user reviews
- Perform user knowledge and skills checks
- Develop fragments of the information system user training methodology
- Analyze user needs
- Analyze user requirements
- Interact with the customer in the process of project implementation
- Interact with customer representatives or subject matter experts
- Identify user problems
- Advise users of the information system
- To provide technical support for the process of training and certification of information system users
- Organize in the structural divisions of the collection of applications for the installation of software and hardware
- Organize user training for new system tools
- Answer questions from users of the information system
- Develop fragments of training methods and certification of users of the information system
- Educate users
- Set tasks for project executives and monitor their implementation
- To form a team of project performers
- Distribute work in the project team
- Select the contractors and evaluate their compliance with the qualification requirements
- Conduct training project performers
- Assess the results of the work of the project executors and adjust their activities
- Develop qualification requirements for project executors in accordance with the project objectives
- Conduct oral interviews
- Conduct written questionnaires and oral interviews
- Process interview results
- Prepare and conduct surveys
- Take part in the development of profiles
- Conduct a written survey
- Develop interview questionnaires
- Conduct a written survey
- Prepare and conduct oral interviews
- Training and professional development
- Participate in improving the skills of workers in the implementation of new database management systems and databases
- Plan advanced training and professional retraining
- Develop a schedule for professional development of specialists
- Check the staff knowledge in filling out the necessary documentation
- Conduct professional retraining when introducing new technologies
- To verify the knowledge and skills gained
- Mentoring
- Participate in the development of training materials
- Transfer knowledge and experience
- Carry out staff training
- Organize and prepare technical meetings with other departments
- Cooperate with other employees in the working group
- Find and engage experts in related and narrow areas
- To distribute work in the directions between adjacent divisions
- Explain the interaction algorithm of system analysts, programmers and other specialists.
- Plan, organize and monitor the work of system analysts, programmers and other specialists
- Analyze the problems of interaction between system analysts, programmers and other specialists.
- Personnel Management
- Determine staffing needs and qualifications
- Plan the work of the group of performers
- Evaluate staff performance
- Provide a rational arrangement and loading staff
- Define qualification requirements for contractors
- Maintain a high professional level of staff
- Organize and prepare technical meetings
- Plan human resource development
- Organize and control the work of subordinates
- Lead the working group
- Participate in the work of qualifying commissions
- Work with staff
- Set tasks for system analysts, programmers and other specialists
- Provide constructive feedback to project implementers on the results of their work
- Introduce corporate culture and social ethics
- Create and maintain a microclimate in the team
- Argue and convince interlocutors
- Interpersonal Relationship Management
- Manage conflict situations
- Motivate liaison partners
- Resolve conflicts
- Create and maintain authority among colleagues and customers
- Managing the relationships of project participants
With competences in economic security, the situation is much more interesting than with information. The fact is that in the territory of the Russian Federation specialists in this area are trained only by departmental educational institutions. But some information about the necessary skills can be found in the manuals of large companies [11], in which there are experts in this field.
Analytical work and data collection
- He is able to analyze the observed situation or facts: he is able to analyze particulars so that later one can come to a conclusion (that is, initially starting from signs and then to come, to reduce particulars to the whole)
- In information and analytical work with sources of information on issues affecting the economic interests of society, it is able to analyze information: it collects essential and reliable information from many different sources, determines the type, form and amount of necessary information. Separates, classifies, sorts meaningful critical information for analysis from “noise” information, which can be neglected, monitors the quality of primary information so that further prediction methods are reliable. Allocates in the essential information separate themes, directions. Quickly processes and understands large amounts of information, delves into the information. Interprets the information, the situation, given the context. Calculates the moves and options for the situation
- When analyzing those facts that have fallen into the sphere of attention, he can evaluate information on the subject of authenticity (to understand the type of information: customized or true), without succumbing to momentary moods or judgments or effective data, can choose the correct version. Can find information about companies, people who lead companies (who is behind them, whose capital)
- Conduct analytical work
- Able to analyze information: collects significant and reliable information from a variety of different sources, determines the type, form and amount of necessary information. , «» , , , . , , .
- , , , , .
- -
- -
- , , , , ( )
- , , , ,
- ,
- Able to work in a mode not clearly formulated task or hypothesis, or with a minimum amount of information
- Able to be attentive and observant to the details of information, in situations in order not to miss the possible facts or signs of threats to the activities of the enterprise
- When considering a violation, not only fixes the fact of the violation itself, but is able to analyze and suggest possible other non-obvious reasons or goals.
- Determines, in particular, foresees in advance what kind of security breach would entail which financial (for example, lowering company capitalization) losses or other risks
- , : , , (, , , .), , , , . ( , , , , )
- , ,
- , , ( , , , )
- , , , , ,
- , ( .), ,
- : , , , , ,
- , , , ,
- , , , , ,
- - (, , .), ,
- — .
- , , — . ,
- , (, , - , ),
- , ,
- —
- ( , .)
- (, , )
- ,
- (, .), ,
- , ( , ), ( ), ( ), ( ), ( ), ( , , — , )
- - -
- , ,
- -
- ,
, , . .
A year has passed, they hear reports.
Biologist: “I developed a method by which, knowing the pedigree of horses and taking their blood tests, you can predict the result with a probability of 90%.”
Mathematician: “I developed a method by which, knowing the statistics of the races for the year, the number of spectators on the podium, the amount of bets and the ratio between men and women among those who made bets, you can predict the result with a probability of 96%.”
Physicist: “I can give a method that allows you to predict the results of races with 100% probability, but I need another 10 million dollars, a laboratory, a staff of assistants and five years of time, and now I have a model of a spherical horse in a vacuum ...”
Collection of the best anecdotes of all times on anekdot.ru
In order to connect the model with reality, it is necessary to make an experiment on real people, which will quantitatively show the quality of compliance of an individual with the accepted competence model. There is a sufficiently large number of methods that allow assessing competencies. The most complete and widespread methods of competency assessment are Assessment Center methods [12] and the 360 degree method.
These methods are quite complex and require fairly large human and financial resources, so they are used mainly only in large companies. In the framework of this work, these methods will not be used due to severe time constraints. Although for the qualitative and quantitative assessment of the model, their application is mandatory.
As was said to the epigraph in the introduction to this work, we needed to ask the main goal of the work or the main question and try to answer it. The main goal is to create a model of a specialist in this work achieved.
The perfect computer security specialist.
As a result of the work done, 67 competencies turned out:
1. Project documents
2. Technical tasks
3. Reports
4. Technological documentation
5. Documentation coordination
6. Amendments to documents
7. Document verification
8. State and industry standards
9. Other normative legal acts
10. Use of documentation
11. Teamwork
12. Self-control and responsibility
13. The ability to read correctly
14. Self-development
15. Public speaking skills
16. Programming languages
17. Understanding the software development process and methods
18. Ensuring the quality and security of the software being created
19. Monitoring the current status of software
20. Installing and configuring software
21. Modernization of software
22. Fixing events and documenting various procedures related to equipment operation
23. Troubleshooting equipment
24. Operation of equipment
25. Monitoring and monitoring of the state of IC & S
26. Operation and maintenance ISIS
27. Identification and elimination of causes of malfunction of ISIS
28. Development of documents and regulations for working with ISIS
29. DBMS
30. Information processing
31. Backup
32. Monitoring and documenting work with databases
33. Project management
34. Understanding the organization’s strategy
35. Information systems administration
36. Management planning and reporting activities
37. Work with the customer
38. Ensuring labor protection standards
39. Working with information system users
40. People and projects
41. Questionnaire and interviews
42. Ensuring interaction between people dmi
43. Human Resource Management
44. Maintaining a positive working atmosphere
45. Analytical work and gathering information
46. Conducting expertise
47. Optimizing business processes in terms of economic security
48. Methodology for protecting confidential information
49. Working with security breaches: localization, prevention, investigation, foresight.
50. Conducting interviews with people: candidates for work, employees, partners, competitors.
51. Work with law enforcement agencies
52. Work with constituent documents, contracts, property rights, laws and other NLA
53. Physical protection of objects and security alarm devices
54. Sensors for fire alarm systems and fire safety systems
55. Means and methods of providing special communications
56. Special studies, special checks, special surveys
57. Follow the instructions for ensuring information security
58. Apply technical means of information protection
59. Control the operation of equipment
60. Analyze and audit information systems and security systems
61. Working with systems anti-virus protection
62. Establish restrictive policies and procedures
63. Controlling the use of computing resources
64. Forming security policies
65. Analysis of the software market technical tools
66. Working with accounts of information systems and users
67. Responding to critical events and elimination of emergency situations
Now, if we take as a specialist’s competence assessments a certain percentage of knowledge of skills, personal and business skills, responsibility and target qualities to the desired result, then 100% compliance for each competence would be an ideal option ( see fig. 4 and 5).

Figure 4 The evaluation model of the ideal computer security specialist.
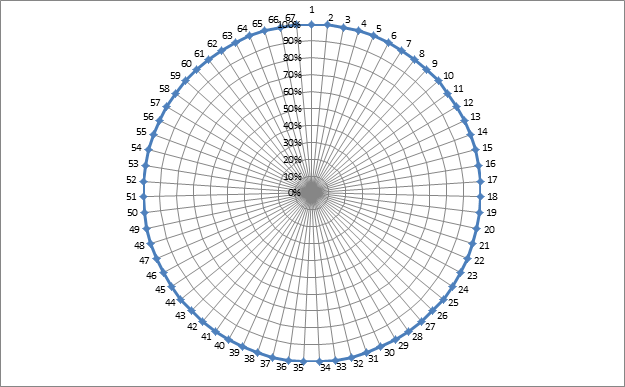
Figure 5 The model of a specialist, where the name of competencies is replaced with the numbers from the list of 67 competencies for ease of perception.
Thus, we have a model of a spherical safety in a vacuum?
Realistic assessment of a computer security specialist.
Since there are no ideal people and training processes, we will try to evaluate what a more or less realistic picture of the specialist’s compliance with this competency model looks like.
We can immediately say that domestic educational institutions do not pay due attention to such competencies that relate to teamwork, self-development, public speaking skills, competent documentation and work with customers. Based on these assumptions, it is possible to construct the assessment shown in Figure 6.

Figure 6 Competence assessment, close to reality.
Some terrible picture turns out. But this is not surprising. For now in educational institutions the main emphasis is on the transfer of knowledge, and, knowledge, as a rule, obsolete 5 years, or even 10 years in relation to technology and the requirements of today.
The evolution of the specialist model from course to course.
All of the above referred to the assessment of an already prepared specialist, i.e. University graduate. But a good model must imply the development of itself, and therefore include sub-models. Since the specialist is trained for 6 courses, it is advisable to point out that the model must evolve with the student. Figure 7 shows roughly how this model should evolve. The dependence is not the number of competencies, but the power of competences because competencies must develop as knowledge and skills are accumulated in the learning process and from one basic competence that was given to a student in the first year there will be ten total competencies to graduate, some basic competences may unite.But all this must be taken into account in the framework of individual subjects throughout the whole process of learning. But such research goes beyond the scope of this paper.
In addition, this work does not take into account the knowledge component, because in order to build a complete model taking into account knowledge, it is necessary to review the curriculum for each discipline taught in this specialty, which will take more than the time allotted to perform this work.
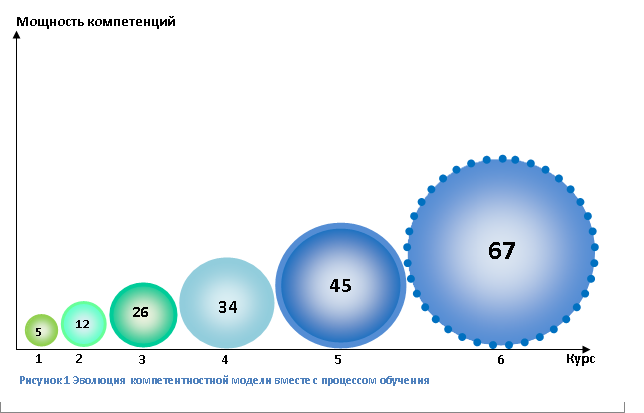
Figure 7 Evolution of the competency model along with the learning process
Conclusion
The goal of the school should always be to cultivate a harmonious personality, not a specialist.
Albert Einstein
If we sum up the present work, we can see that competencies are the link between the university and the enterprise, which the specialist will work after graduation. However, the training of specialists in the university at present does not take into account the real needs of enterprises in the knowledge and skills that are really necessary for work. Training of specialists in the framework of academic disciplines is shifted mainly towards fundamental scientific subjects, losing real needs in interaction with people, teamwork, the ability to competently work with documents. Undoubtedly, fundamental training is very important as a base, but it is impossible to dwell only on fundamental natural sciences. Need to move on.Now within the framework of the project of the Ministry of Education and Science of the Russian Federation, there is a unique chance to develop and use in the training of specialists a comprehensive standard based on the competency model. Universities in the third generation State Educational Institution of Higher Professional Education are given a great deal of freedom to create such standards for a number of specialties, and these opportunities must be used to ensure that a specialist graduating from an institution of higher education is closer to the ideal, and not to that dreadful sea urchin, which now turns out if you look at knowledge , skills and graduate skills. The higher school should first of all take care of the upbringing of the person, and then from the person to make a specialist.Universities in the third generation State Educational Institution of Higher Professional Education are given a great deal of freedom to create such standards for a number of specialties, and these opportunities must be used to ensure that a specialist graduating from an institution of higher education is closer to the ideal, and not to that dreadful sea urchin, which now turns out if you look at knowledge , skills and graduate skills. The higher school should first of all take care of the upbringing of the person, and then from the person to make a specialist.Universities in the third generation State Educational Institution of Higher Professional Education are given a great deal of freedom to create such standards for a number of specialties, and these opportunities must be used to ensure that a specialist graduating from an institution of higher education is closer to the ideal, and not to that dreadful sea urchin, which now turns out if you look at knowledge , skills and graduate skills. The higher school should first of all take care of the upbringing of the person, and then from the person to make a specialist.and further from the person to make a specialist.and further from the person to make a specialist.
References
[1] The project of the WCC - the national union of personnel specialists "personnel-technology library" Methodical manual "Building a model of competences in the company", supplement to the magazine "Handbook of personnel management" No. 11, 2008.
[2] V.I. Baidenko , Identification of the composition of the competencies of graduates of universities, as a necessary stage in the design of a state-of-the-art higher education system of a new generation (Methodological manual), Moscow: 2006.
[3] The Bologna Process: Mid-way / Under scientific. ed.dr ped Sciences, Professor V. I. Baidenko. - M .: Research Center for Problems of the Quality of Training Specialists, Russian New University, 2005. - 379 p.
[4] Avdoshin S. M., On the Experience of Using Professional Standards in the Formation of Educational Educational Programs in the Direction 230400 “Applied Engineering”, Moscow: State University - Higher School of Economics, - 2007.
[5] Development of professional standards for the information technology industry . IT Education Committee. APKIT website www.apkit.ru/default.asp?artID=5573
[6] Professional standards are published on the AP KIT website www.apkit.ru/default.asp?artID=5573
[7] Fundamentals of Information Security / V. Galatenko. Edited by Corresponding Member of the RAS V. B. Betelina / M .: INTUIT.RU “Internet University of Information Technologies”, 2003. - 280 p.
[8] State Educational Standard of Higher Professional Education, Specialty - 075200 - “Computer Security”, Moscow: Ministry of Education of the Russian Federation, 2000.
[9] Miller George, Min. Information Processing, The Psychology Review, vol. 63, N 2, March 1956.
[10] G. Buch Object-oriented analysis and design with examples of applications in C ++, 2nd ed. / Trans. from English- M .: "Publishing Binom", St. Petersburg: "Nevsky Dialect", 2001. - 560 p., Il.
[11] Methodology and development tools for typical competence models for the target group of positions of structural subdivisions of regional branches of the IRCs of the Svyazinvest group. A guide for HR professionals. M .: Svyazinvest, 2006.
[12] ASSESSMENT CENTER: a technology for evaluating and developing personnel, http://www.kadry.ru/articles/detail.php?ID=15683
Source: https://habr.com/ru/post/182176/
All Articles