Threat rating in May 2013: increased activity of Zeus modifications
Last month, an increase in the activity of the ZBot (ZeuS) family was recorded in the world, its rating was 1.36%. Under the general name Win32 / Spy.Zbot, we detect all possible modifications of this Trojan program, including Citadel and Gameover . ZeuS peak activity occurred on May 2, when its prevalence rate reached 4.83%.
The main purpose of attackers using ZeuS, is theft of user authentication data from various services, including online banking. The information stolen in this way is used to transfer funds to dummy accounts, from which they are promptly cashed by “mules” - persons who are ready to withdraw funds of dubious origin at a small percentage. Note that an impressive number of ZeuS modifications are due to the leakage of the source codes of this trojan in 2011.
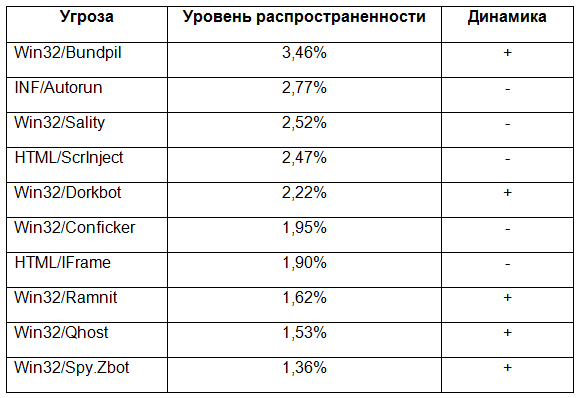
As for the other dozens of global threats, the growth was demonstrated by Win32 / Bundpil (3.46%) and Win32 / Dorkbot (2.22%), Win32 / Ramnit virus (1.62%), as well as the Win32 / Qhost Trojan ( 1.53%). The Win32 / Bundpil worm, which spreads via removable media, retained first place and even increased activity compared to April.
')
The increase in the activity of the Win32 / Dorkbot worm is associated with the May spam campaign for spreading malware. Users were sent messages with malicious links, during the transition to which there was a risk of installing a Win32 / PowerLoader Trojan that downloaded Win32 / Dorkbot to the computer.
To disguise malicious links in emails, the Google URL Shortener service was used, thanks to which shortened addresses began with ”http://goo.gl/”. According to the statistics of the transition from malicious links that participated in this campaign, Russia has become one of the leaders in the number of victims of the attack.
Malicious elements embedded in web pages, which are detected under the common names HTML / ScrInject (2.47%) and HTML / Iframe (1.90%), declined in May. HTML / ScrInject has been losing ground over the past two months; the same two months, the INF / Autorun (2.77%) and Win32 / Conficker (1.95%) activity falls.
The rating of threats in Russia has not changed much compared to April. It is worth noting that the Win32 / Qhost Trojan program, which has been declining since the beginning of this year, experienced a boom in May - its rating was 12.40%. In addition, malicious Java scripts with general JS / Iframe detection (2.84%) showed growth. All other threats have reduced activity.
The Win32 / Agent.UPF Trojan, which we wrote about in detail in the last report, markedly reduced its activity - this month its prevalence rate was 1.55%. We also note that the Win32 / StartPage Trojan, which was present in our rankings of the previous two months, significantly lost ground in May and left the top ten most active threats.
In May, Russia's total share in the global malware volume was 8.14%.
The global rating of the most active threats is as follows:
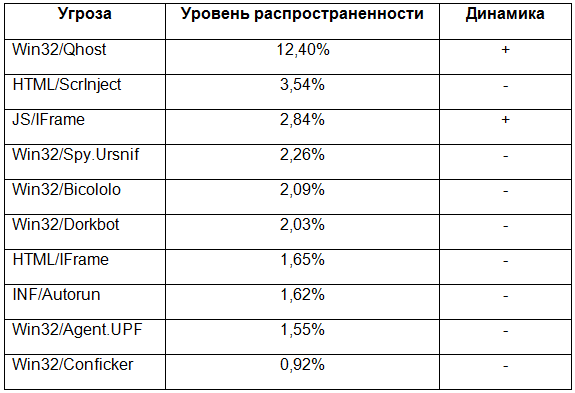
Threat Statistics for Russia:
The main purpose of attackers using ZeuS, is theft of user authentication data from various services, including online banking. The information stolen in this way is used to transfer funds to dummy accounts, from which they are promptly cashed by “mules” - persons who are ready to withdraw funds of dubious origin at a small percentage. Note that an impressive number of ZeuS modifications are due to the leakage of the source codes of this trojan in 2011.
As for the other dozens of global threats, the growth was demonstrated by Win32 / Bundpil (3.46%) and Win32 / Dorkbot (2.22%), Win32 / Ramnit virus (1.62%), as well as the Win32 / Qhost Trojan ( 1.53%). The Win32 / Bundpil worm, which spreads via removable media, retained first place and even increased activity compared to April.
')
The increase in the activity of the Win32 / Dorkbot worm is associated with the May spam campaign for spreading malware. Users were sent messages with malicious links, during the transition to which there was a risk of installing a Win32 / PowerLoader Trojan that downloaded Win32 / Dorkbot to the computer.
To disguise malicious links in emails, the Google URL Shortener service was used, thanks to which shortened addresses began with ”http://goo.gl/”. According to the statistics of the transition from malicious links that participated in this campaign, Russia has become one of the leaders in the number of victims of the attack.
Malicious elements embedded in web pages, which are detected under the common names HTML / ScrInject (2.47%) and HTML / Iframe (1.90%), declined in May. HTML / ScrInject has been losing ground over the past two months; the same two months, the INF / Autorun (2.77%) and Win32 / Conficker (1.95%) activity falls.
The rating of threats in Russia has not changed much compared to April. It is worth noting that the Win32 / Qhost Trojan program, which has been declining since the beginning of this year, experienced a boom in May - its rating was 12.40%. In addition, malicious Java scripts with general JS / Iframe detection (2.84%) showed growth. All other threats have reduced activity.
The Win32 / Agent.UPF Trojan, which we wrote about in detail in the last report, markedly reduced its activity - this month its prevalence rate was 1.55%. We also note that the Win32 / StartPage Trojan, which was present in our rankings of the previous two months, significantly lost ground in May and left the top ten most active threats.
In May, Russia's total share in the global malware volume was 8.14%.
The global rating of the most active threats is as follows:

Threat Statistics for Russia:

Source: https://habr.com/ru/post/182070/
All Articles