Coordination of user actions in VMware before their execution
Here came the new requirements of FSTEC of Russia by order No. 21 on the part of personal data protection.
We decided to apply it on the customer (even in my head I always tell myself about them with a capital letter), he has the infrastructure on VMware. But what requirement did my colleague indicate to me: “Analysis of the potential impact of planned changes in the configuration of the information system and the personal data protection system on ensuring the protection of personal data and agreeing on changes in the configuration of the information system with an official (employee) responsible for ensuring the security of personal data” . The requirement works for UZ 1, UZ 2 and UZ 3. the breadth of coverage will probably be normal.
How does the requirement fall on the coordination of actions in VMware vSphere? Welcome under habrakat.
Considering how many changes are happening in the modern IT environment ... It is better to do for really critical operations on production (in fact, such an organizational process is often built up - especially in banks, administrators write papers, they are approved by the boss, then they go to configure). The requirement is difficult to fulfill directly from the point of view of automation.
I think most often we will bypass it org. by measures. But for those systems where this can be done, why not?
Especially in the light of the fact that most likely with new requirements - Order FSTEC # 21 - there is an excellent legal chance to leave certification on the threat model ...
')
Well ... Colleague: "Look, and how to implement the requirement for VMware vSphere." But you can. And it will be useful not only for PAP.
I just want to be sure that no one will reboot my virtualized production server from the VMware console - even by accident, because to click the mouse on the wrong place once in a while, he was wrong (((
There is such a solution - HyTrust. A lot has been written about him. But still, the sparrow in the Russian market has not been shot.
So on this account he has two features:
1) Secondary Approval - block unwanted action and send for approval with the notification by mail
2) Alerting - will inform the right people about it.
The first one can block the action of any user (even Full Access) if certain operations (for example, Power Off, Suspend, Reboot, etc.) are performed with certain machines (for example, with the label “Production”). As a result, an error is prohibited to the console requesting, an action is prohibited, confirmation is necessary. A letter will be sent to the confirmation mail - here one asks to restart the production server ... do you know about this? )
The chief / manager / security officer or any other coordinator need only enter the HyTrust interface by the link from the letter and confirm the operation. And better to ban :)
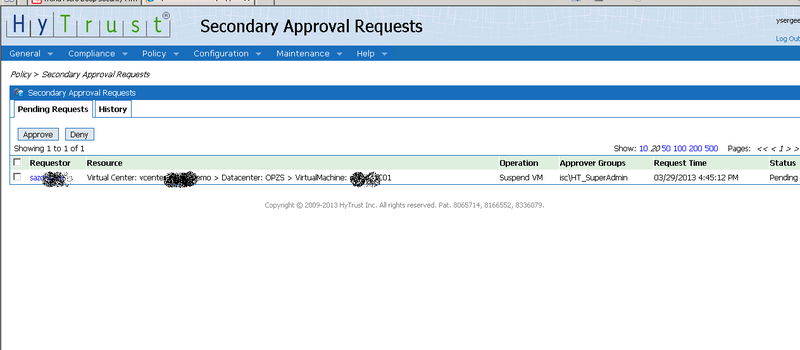
After that, the requester will know about it and can repeat the operation (even in the case of a ban, he can really, well, really want to perform it). Sometimes even a few minutes of downtime are expensive. The feature is interesting.
To protect PD, instead of (or in addition), you can use a ZPD tag or something else. The benefit of the solution allows you to invent and create tags with any name.
Second, the Alerting functionality is normally shown on youtube in the company's channel:
www.youtube.com/watch?v=WOV2LJ_wFiY
I recommend to see - there is a lot of things. Including on the part of attempts to implement Multitenancy in vCenter without vCloud)
We decided to apply it on the customer (even in my head I always tell myself about them with a capital letter), he has the infrastructure on VMware. But what requirement did my colleague indicate to me: “Analysis of the potential impact of planned changes in the configuration of the information system and the personal data protection system on ensuring the protection of personal data and agreeing on changes in the configuration of the information system with an official (employee) responsible for ensuring the security of personal data” . The requirement works for UZ 1, UZ 2 and UZ 3. the breadth of coverage will probably be normal.
How does the requirement fall on the coordination of actions in VMware vSphere? Welcome under habrakat.
Considering how many changes are happening in the modern IT environment ... It is better to do for really critical operations on production (in fact, such an organizational process is often built up - especially in banks, administrators write papers, they are approved by the boss, then they go to configure). The requirement is difficult to fulfill directly from the point of view of automation.
I think most often we will bypass it org. by measures. But for those systems where this can be done, why not?
Especially in the light of the fact that most likely with new requirements - Order FSTEC # 21 - there is an excellent legal chance to leave certification on the threat model ...
')
Well ... Colleague: "Look, and how to implement the requirement for VMware vSphere." But you can. And it will be useful not only for PAP.
I just want to be sure that no one will reboot my virtualized production server from the VMware console - even by accident, because to click the mouse on the wrong place once in a while, he was wrong (((
There is such a solution - HyTrust. A lot has been written about him. But still, the sparrow in the Russian market has not been shot.
So on this account he has two features:
1) Secondary Approval - block unwanted action and send for approval with the notification by mail
2) Alerting - will inform the right people about it.
The first one can block the action of any user (even Full Access) if certain operations (for example, Power Off, Suspend, Reboot, etc.) are performed with certain machines (for example, with the label “Production”). As a result, an error is prohibited to the console requesting, an action is prohibited, confirmation is necessary. A letter will be sent to the confirmation mail - here one asks to restart the production server ... do you know about this? )
The chief / manager / security officer or any other coordinator need only enter the HyTrust interface by the link from the letter and confirm the operation. And better to ban :)

After that, the requester will know about it and can repeat the operation (even in the case of a ban, he can really, well, really want to perform it). Sometimes even a few minutes of downtime are expensive. The feature is interesting.
To protect PD, instead of (or in addition), you can use a ZPD tag or something else. The benefit of the solution allows you to invent and create tags with any name.
Second, the Alerting functionality is normally shown on youtube in the company's channel:
www.youtube.com/watch?v=WOV2LJ_wFiY
I recommend to see - there is a lot of things. Including on the part of attempts to implement Multitenancy in vCenter without vCloud)
Source: https://habr.com/ru/post/181530/
All Articles