Apple mobile devices in the corporate sector. Configuration profiles
The first thing that comes to mind when thinking about mobile equipment for an employee of a large company is a laptop like HP EliteBook and a BlackBerry smartphone. The vast majority believes that the MacBook is very far from corporate standards, and is only suitable for designers, indie developers and advanced housewives. The iPhone is considered to be a stylish gadget for writing tweets and photographing “bows” for fashionable Instagram.

Now I will try to dispel such stereotypes and tell what mobile devices of the famous company from Cupertino are capable of.
I'll start with mobile devices based on Apple iOS. We will talk about versions 3.0 and above, which are currently running the following devices:
All these devices support the loading of configuration profiles, with the help of which one can flexibly configure the device for corporate use.
')
It makes no sense to reprint the official guidelines for working with profiles. I just dwell on the most interesting features.
First of all, the configuration profile is plain XML. It can be signed with a digital certificate and / or encrypted. Upon receipt of a signed profile, the device verifies the digital signing certificate and displays the status.
When you receive an encrypted profile, the decryption key must be on the device.
Profiles may contain the following data:
Consider some options in more detail. So what can be limited on the device using a profile?
As you can see, there are a lot of opportunities to bring a mobile device into compliance with the requirements of the enterprise security service. What is missing is the time ranges for which particular restrictions apply, for example, banning YouTube only during business hours. :-)
Access parameters for Wi-Fi, VPN, mail, LDAP, etc. quite the same type. It should be noted that all of them can include certificate authorization. Obviously, to authorize a certificate, a device must contain a pair of keys: a public key and a private key. Private key can not be transmitted in the profile. An infrastructure is needed to support the SCEP certificate rotation protocol. In this case, the private key is generated on the mobile device, then the public key is transmitted to the certification authority as part of the certificate request, after signing and generating the certificate, the finished certificate is transferred to the device and installed in the local storage. The SCEP request has a unique
Public certificates of root and publishing centers can be included in the profile. Installing an enterprise root certificate allows you to visit internal https resources without issuing warning messages about an invalid certificate. This applies to mail services, VPN gateway, Wi-Fi points - everything that uses corporate certificates in the authorization process.
When deleting a profile, all services and settings specified in it are also deleted. For example, if a profile contained access to an enterprise mail server, then after deleting the profile, the mailbox on the device will be deleted, the employee will not be able to accept new mail or read already received. Other mailboxes, such as personal mail on Gmail, will be available as before.
The profile can be protected with a PIN from deletion, the
It is possible to set the period or date after which the profile will be automatically deleted, the
A profile can be downloaded to a device in several ways:
The first and second methods are suitable for small companies where it is easier to install everything manually, the third method is the most technologically advanced and is recommended for use in large companies.
I will try to describe the profile loading in the third way, Over-the-Air .
The first phase is the delivery of the URL with the profile download address to the mobile device. This may be a link in an e-mail, in an SMS message, on a special web page. It is advisable to post a link to the https resource and protect the content from being changed, for example, with the secure_link technology of the nginx server.
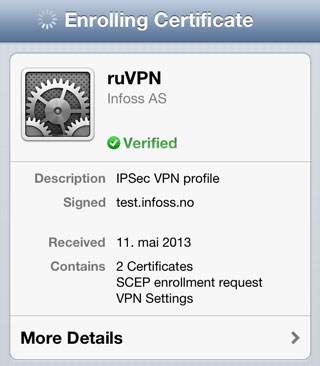
The first profile contains a request for user device parameters.
Files with the
After receiving the profile, the device requests the user permission to install. If the unlock screen by PIN-code is enabled in the security settings, the PIN-code will be requested. Then the device information will be transmitted to the profile server.
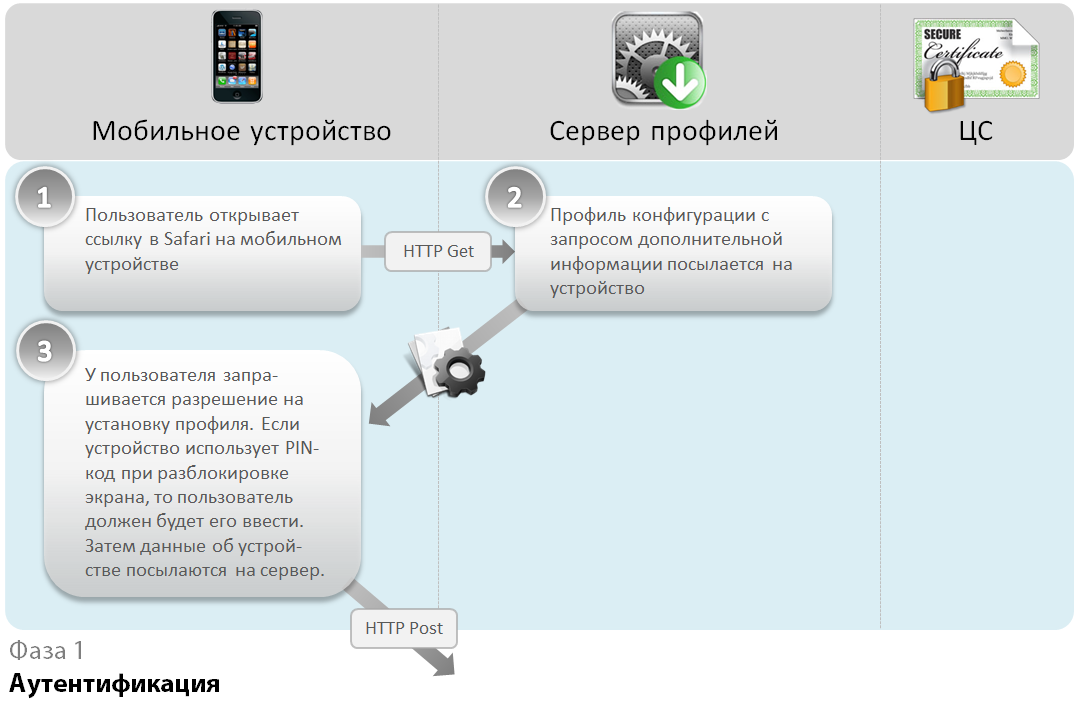
The next phase is the generation of an intermediate certificate for subsequent encryption of the main profile. The private key cannot be transferred to the device; therefore, SCEP is used, through which a pair of keys is generated on the device and then a certificate request is sent directly to the certification authority. Profile server is not involved in this process.
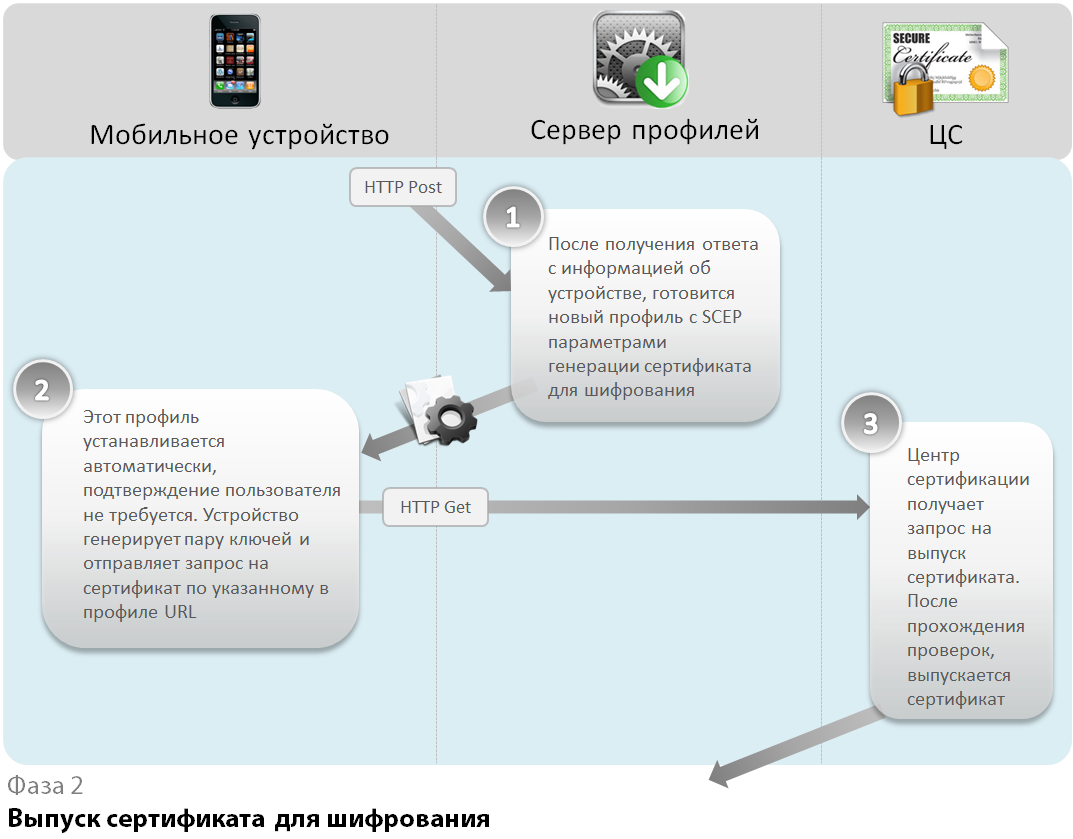
The certification authority signs the request, generates a certificate with the necessary parameters and sends it back to the device. The received certificate is installed in the local storage.
The mobile device informs the server profiles about the end of the second phase in the form of a message signed by the new certificate.
It's time for the third phase. There is a certificate and a private key on the mobile device, there is a certificate on the profile server. So you can encrypt the main profile and send it to your mobile device.
The content of the main profile depends on the requirements of the security service and the level of development of the network infrastructure of the enterprise and branches. This is the most crucial part of the profile implementation project and includes the participation of several departments and services of the enterprise. Profile data can be taken from Active Directory, corporate databases or other systems.

The technology of loading configuration profiles with some assumptions also applies to mobile devices based on OS X 10.8+, that is, for fresh MacBook, MacBook Air / Pro.
According to the described scheme, loading of ruVPN.net service profiles is working , at Habré recently successfully passed load testing , when anyone could install a profile with VPN settings on their device. The main profile contained a SCEP certificate request for accessing the IPSec VPN server. The profile was automatically removed from the devices of the testing participants. 05/27/2013 00:00:00 UTC. Many thanks to all the test participants!

Now I will try to dispel such stereotypes and tell what mobile devices of the famous company from Cupertino are capable of.
I'll start with mobile devices based on Apple iOS. We will talk about versions 3.0 and above, which are currently running the following devices:
- iPhone 3G, 3Gs, 4, 4s, 5
- iPad 2, 3, 4
- iPod touch, generations 2 to 5
- iPad mini
All these devices support the loading of configuration profiles, with the help of which one can flexibly configure the device for corporate use.
')
It makes no sense to reprint the official guidelines for working with profiles. I just dwell on the most interesting features.
First of all, the configuration profile is plain XML. It can be signed with a digital certificate and / or encrypted. Upon receipt of a signed profile, the device verifies the digital signing certificate and displays the status.

When you receive an encrypted profile, the decryption key must be on the device.
Profiles may contain the following data:
- Restriction of mobile device functions
- Wi-Fi connection settings
- VPN access options
- Mail server settings (Exchange, POP3, IMAP, SMTP)
- LDAP directory access settings (for global address books)
- CalDAV calendar access options
- Digital certificates
- Requests for automatic rotation of certificates under the SCEP protocol (including for the above services)
Consider some options in more detail. So what can be limited on the device using a profile?
- Deny access to the device without a password, the
forcePINparameter - Prevent using the same password all the time,
maxPINAgeInDaysparameter - Set password length,
minLengthparameter - Prohibit the use of the same password when changing the password,
pinHistoryparameter - Deny the password consisting of one numbers (although this is already a mockery of the user), the
requireAlphanumericparameter - Forbid to install applications from AppStore , parameter
allowAppInstallation - Disable Siri, parameter
allowAssistant - Disable the use of the camera in the device , the parameter
allowCamera - Ban adult content, parameter
allowExplicitContent - Close access to Game Center, parameter
allowGameCenter - Disable screenshots ,
allowScreenShot - Close access to YouTube (!), Parameter
allowYouTube - Close access to iTunes, parameter
allowiTunes - Disallow use of Safari browser, parameter
allowSafari - Disallow use of unknown certificates , parameter
allowUntrusted-TLSPrompt - Disallow installation of profiles without user intervention, parameter
allowUIConfiguration-ProfileInstallation
As you can see, there are a lot of opportunities to bring a mobile device into compliance with the requirements of the enterprise security service. What is missing is the time ranges for which particular restrictions apply, for example, banning YouTube only during business hours. :-)
Access parameters for Wi-Fi, VPN, mail, LDAP, etc. quite the same type. It should be noted that all of them can include certificate authorization. Obviously, to authorize a certificate, a device must contain a pair of keys: a public key and a private key. Private key can not be transmitted in the profile. An infrastructure is needed to support the SCEP certificate rotation protocol. In this case, the private key is generated on the mobile device, then the public key is transmitted to the certification authority as part of the certificate request, after signing and generating the certificate, the finished certificate is transferred to the device and installed in the local storage. The SCEP request has a unique
PayloadUUID that can be specified in the PayloadCertificate-UUID other settings. In this way, the certificates obtained are associated with the settings of Wi-Fi, VPN, mail, LDAP, and so on.Public certificates of root and publishing centers can be included in the profile. Installing an enterprise root certificate allows you to visit internal https resources without issuing warning messages about an invalid certificate. This applies to mail services, VPN gateway, Wi-Fi points - everything that uses corporate certificates in the authorization process.
When deleting a profile, all services and settings specified in it are also deleted. For example, if a profile contained access to an enterprise mail server, then after deleting the profile, the mailbox on the device will be deleted, the employee will not be able to accept new mail or read already received. Other mailboxes, such as personal mail on Gmail, will be available as before.
The profile can be protected with a PIN from deletion, the
HasRemovalPasscode parameter; You can generally disable deletion, the PayloadRemoval-Disallowed option. In the latter case, the profile can be deleted only by completely resetting all the device settings, while the entire contents of the device is deleted. Such settings are well suited for companies with strict information security requirements.It is possible to set the period or date after which the profile will be automatically deleted, the
DurationUntilRemoval and RemovalDate . This is well suited for temporary employees or company consultants.A profile can be downloaded to a device in several ways:
- Wired The device is connected via USB to a computer running the iPhone Configuration Utility program, the necessary configuration profile is selected and downloaded to the device.
- Direct . A link opens with a profile file (.mobileconfig) in Safari browser and confirms the installation of the profile.
- Over-the-Air . The profile download page opens in Safari browser, then the primary profile is installed with the generation of an intermediate certificate for encrypting the main profile. The content of the profile is encrypted.
The first and second methods are suitable for small companies where it is easier to install everything manually, the third method is the most technologically advanced and is recommended for use in large companies.
I will try to describe the profile loading in the third way, Over-the-Air .
The first phase is the delivery of the URL with the profile download address to the mobile device. This may be a link in an e-mail, in an SMS message, on a special web page. It is advisable to post a link to the https resource and protect the content from being changed, for example, with the secure_link technology of the nginx server.
The first profile contains a request for user device parameters.
XML content
It looks like this:
The Challenge parameter is the transaction identifier for the profile server.
<?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> <plist version="1.0"> <dict> <key>PayloadContent</key> <dict> <key>URL</key> <string>https://ruvpn.net/profile/qefdJW98Vx9YFyyzs4C2F/1369640562</string> <key>DeviceAttributes</key> <array> <string>UDID</string> <string>IMEI</string> <string>ICCID</string> <string>VERSION</string> <string>PRODUCT</string> <string>DEVICE_NAME</string> <string>MAC_ADDRESS_EN0</string> </array> <key>Challenge</key> <string>Pa$$word</string> </dict> <key>PayloadOrganization</key> <string>Infoss AS</string> <key>PayloadDisplayName</key> <string>VPN configuration</string> <key>PayloadVersion</key> <integer>1</integer> <key>PayloadUUID</key> <string>fdb37dd45-b5bb-4d8c-daf3-e908683420c9</string> <key>PayloadIdentifier</key> <string>no.infoss.mobileconfig.ipsec</string> <key>PayloadDescription</key> <string>Please accept this profile</string> <key>PayloadType</key> <string>Profile Service</string> <key>RemovalDate</key> <date>2013-05-27T00:00:00Z</date> </dict> </plist> The Challenge parameter is the transaction identifier for the profile server.
Files with the
.mobileconfig extension .mobileconfig recognized only in Safari, so the link must be opened in it.After receiving the profile, the device requests the user permission to install. If the unlock screen by PIN-code is enabled in the security settings, the PIN-code will be requested. Then the device information will be transmitted to the profile server.

Sample device response as XML
Here is an approximate answer from the iPad:
The answer is signed by the embedded Apple device certificate. The profile server must check the signature for validity.
<?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> <plist version="1.0"> <dict> <key>PRODUCT</key> <string>iPad2,5</string> <key>UDID</key> <string>1cfc707bbde274a4643f93341fca784ba0ec898c</string> <key>VERSION</key> <string>10B329</string> </dict> </plist> The answer is signed by the embedded Apple device certificate. The profile server must check the signature for validity.
The next phase is the generation of an intermediate certificate for subsequent encryption of the main profile. The private key cannot be transferred to the device; therefore, SCEP is used, through which a pair of keys is generated on the device and then a certificate request is sent directly to the certification authority. Profile server is not involved in this process.

Sample XML for Phase 2
<?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> <plist version="1.0"> <dict> <key>PayloadVersion</key> <integer>1</integer> <key>PayloadUUID</key> <string>Ignored</string> <key>PayloadType</key> <string>Configuration</string> <key>PayloadIdentifier</key> <string>Ignored</string> <key>PayloadContent</key> <array> <dict> <key>PayloadContent</key> <dict> <key>URL</key> <string>https://scep.infoss.no/enroll/zYu47Jr45XDtnv0b1Eg/1369640566</string> <key>Name</key> <string>ruVPN CA</string> <key>Subject</key> <array> <array> <array> <string>CN</string> <string>Encryption</string> </array> </array> <array> <array> <string>O</string> <string>Infoss AS</string> </array> </array> </array> <key>Challenge</key> <string>Pa$$word</string> <key>Keysize</key> <integer>2048</integer> <key>Key Type</key> <string>RSA</string> </dict> <key>PayloadDescription</key> <string>Provides device encryption identity</string> <key>PayloadUUID</key> <string>CAE1D4F6-1BBA-859F-89E2-48DFA7112F14</string> <key>PayloadType</key> <string>com.apple.security.scep</string> <key>PayloadDisplayName</key> <string>Encryption Identity</string> <key>PayloadVersion</key> <integer>1</integer> <key>PayloadOrganization</key> <string>Infoss AS</string> <key>PayloadIdentifier</key> <string>no.infoss.mobileconfig.ipsec</string> </dict> </array> </dict> </plist> The certification authority signs the request, generates a certificate with the necessary parameters and sends it back to the device. The received certificate is installed in the local storage.
The mobile device informs the server profiles about the end of the second phase in the form of a message signed by the new certificate.
It's time for the third phase. There is a certificate and a private key on the mobile device, there is a certificate on the profile server. So you can encrypt the main profile and send it to your mobile device.
The content of the main profile depends on the requirements of the security service and the level of development of the network infrastructure of the enterprise and branches. This is the most crucial part of the profile implementation project and includes the participation of several departments and services of the enterprise. Profile data can be taken from Active Directory, corporate databases or other systems.

The technology of loading configuration profiles with some assumptions also applies to mobile devices based on OS X 10.8+, that is, for fresh MacBook, MacBook Air / Pro.
A little about MDM
It is worth mentioning such technology as MDM. In the case of a configured Mobile Device Management (MDM) server, the parameters of this server can be entered into the main profile, and after installing the profile, the mobile device will receive control commands from the server. With MDM, the following device operations are possible:
• Request information from the device:
o General settings
o network settings
o Security Settings
o Active limitations
o Configuration profiles
o Application Download Profiles
o Applications
• Device Management
o Change device settings
o Install / remove configuration profiles
o Install / remove application download profiles
o Add / Remove Applications
o Password changes
o Complete removal of all information on the device
Commands from the MDM server are received using the push notification method.
The implementation of MDM is advisable in large enterprises and allows you to remotely control the mobile devices of employees.
• Request information from the device:
o General settings
o network settings
o Security Settings
o Active limitations
o Configuration profiles
o Application Download Profiles
o Applications
• Device Management
o Change device settings
o Install / remove configuration profiles
o Install / remove application download profiles
o Add / Remove Applications
o Password changes
o Complete removal of all information on the device
Commands from the MDM server are received using the push notification method.
The implementation of MDM is advisable in large enterprises and allows you to remotely control the mobile devices of employees.
According to the described scheme, loading of ruVPN.net service profiles is working , at Habré recently successfully passed load testing , when anyone could install a profile with VPN settings on their device. The main profile contained a SCEP certificate request for accessing the IPSec VPN server. The profile was automatically removed from the devices of the testing participants. 05/27/2013 00:00:00 UTC. Many thanks to all the test participants!
Source: https://habr.com/ru/post/181223/
All Articles