Investigation of Targeted Attacks in South Asia
In this post we want to present our investigation of the targeted attack, which was used to steal confidential information from various organizations around the world. During this investigation, it was discovered that the traces of this attack go to India, and Pakistan is the most affected country. In addition, the actions of intruders have been active for at least the past two years. A distinctive feature of the attack was the use of a valid digital certificate, which was used to sign malicious executables. We also discovered an exploit that was used by attackers to install malicious code into the system.

As part of this campaign, a valid digital certificate was used, which signed malicious executables. This was done to provide greater secrecy and create an image of the legitimacy of the installed malicious code. The certificate was issued at the end of July 2011 for the Indian company Technical and Commercial Consulting Pvt. Ltd., based in New Delhi.
')
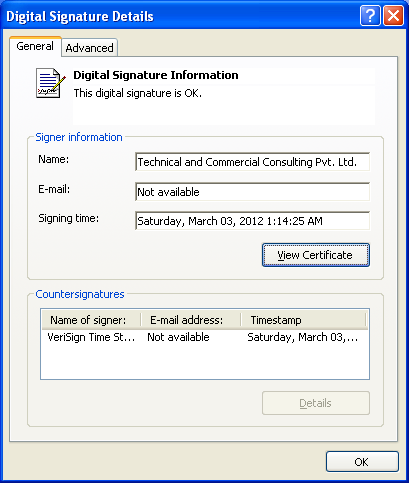
We promptly contacted VeriSign and, according to the information provided by us, this certificate was promptly withdrawn. In total, as a result of the investigation of this incident, more than 70 malicious files (!) Signed with this digital signature were detected. Based on the timestamps of these files, we created a timeline that reflects the timeline of the signing of these files.

Based on the information collected by us, it is clear that the attackers most actively signed malicious files from March to June 2012. Then we see a slight decline in activity from June to August 2012. Further, there is a surge in the use of the certificate in August and September 2012 despite that he was already recalled.
In addition to these signed files, during the investigation several normal executable files that were missing a signature were also found. Some of these files were discovered by us in early 2011.
Droppers and initial attack vector
In one of the attack vectors for users, attackers exploited the popular vulnerability CVE-2012-0158. This vulnerability was exploited through a specially crafted Microsoft Office file, as a result of which arbitrary code was executed in the OS. We observed an RTF document that, when it was opened on a vulnerable system, executed a two-stage shell code. This shellcode sent system information to the feds.comule.com domain, and also downloaded the malicious file from digitalapp.org.
Another attack vector was to use executable files that were masked as Microsoft Word or PDF files. These files were distributed via email. As soon as the user launched the file, this malicious program downloaded and launched for execution additional malicious modules. To disguise, the malicious code did display a Word document with a specific content to the user, and we saw several such documents on various topics.
One of the documents found used the theme of the Indian armed forces. In fact, we do not have specific information about which specific people or organizations these files were intended for. However, based on our telemetry system, we assume that the targets were people and educational institutions in Pakistan.
The screenshot below shows one of these PDF documents, the content of which, in fact, is a compilation from various sources. This document was delivered through a self-extracting archive, which had the name “pakistandefencetoindiantopmiltrysecreat.exe”.


The following screenshot shows a PDF document that was delivered via the executable file “pakterrisiomforindian.exe”. In this case, the content of the document is based on the text from the Asian Defense blog. On this blog, gather news about the military theme of the Asian region. The data of our telemetry system shows that this file was first discovered in August 2011 on computers in Pakistan.

Payload
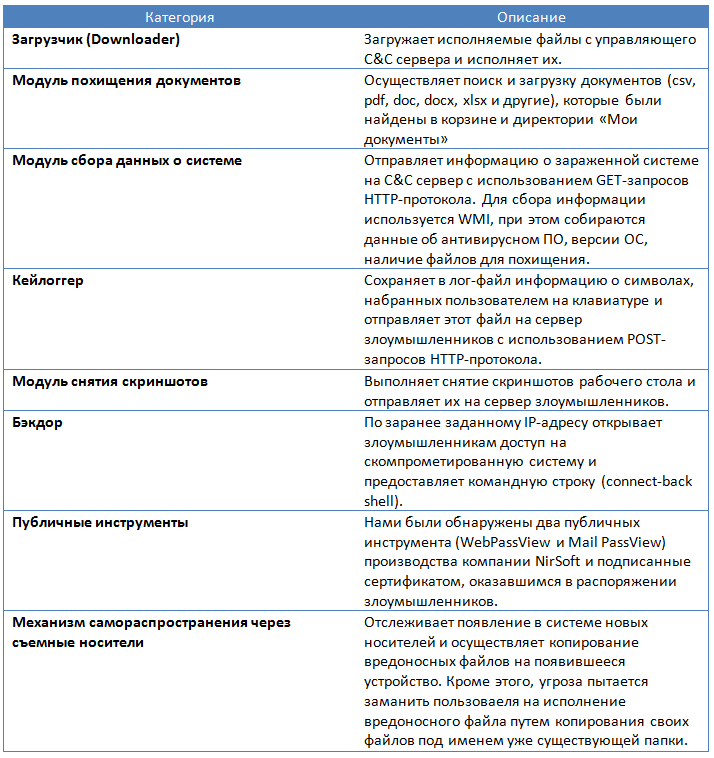
We found a sufficient number of payload types that were used in this attack. For its installation, as in other cases, droppers were used. Its main task is to send important data from an infected computer to an attacking remote server. The following table contains families of executable files and their modules with a description of functions. All these modules were used in the targeted attack.
The information stolen from the infected computer is sent to the attacker's server in unencrypted form. Such a decision is really puzzling, since it compromises the length of time the malicious code has been on the computer, which, in turn, is an important factor for the targeted attack. In this case, network traffic analysis allows you to detect malicious activity. The screenshot below shows the part of the keylogger log file.
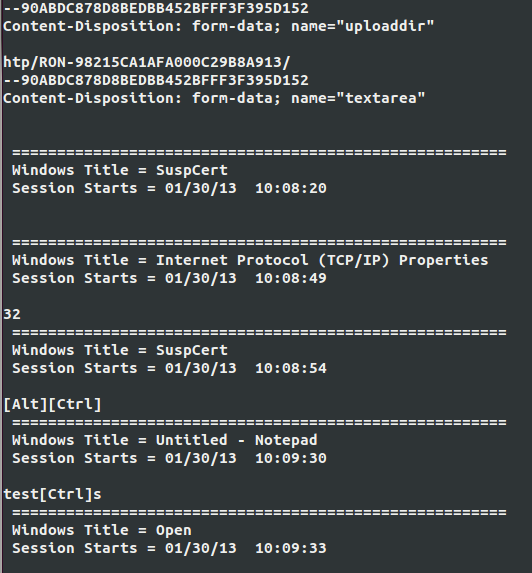
This log file is quite informative and displays the characters typed by the user, as well as information about the window in which they were typed and at what time. Due to the fact that these files are sent to the server in an unencrypted form, the task of detecting malicious code on a computer is solved quite simply by analyzing the traffic on the network.
It should be noted that this malicious code added items to the “Start” menu with a deceptive name for the user. The screenshot below shows an example of such a menu item.

The Trojan uses methods that allow its various components to ensure their survival after a reboot. But at the same time, it can not be called invisible. Since targeted attacks usually try to be imperceptible in the system for as long as possible, we were surprised by the lack of appropriate mechanisms for this threat.
C & C structure
Most of the malicious files that we have analyzed contain embedded URLs that are used to download additional modules, as well as to send data from the infected system to the attacker's server. Sometimes the URLs of the managers of the C & C servers are stored in the body of the malicious code in an unencrypted form. In other cases, a fairly basic encryption method is used using one-character rotation (ROT-1) operation as shown below.
“Gjmftbttpdjbuf / ofu” -> “filesassociate.net”
We found more than 20 domains that were used in this campaign. Despite the fact that some of these domains are still marked as active, most of them are no longer translated to IP addresses. For most of these domains, hosting was performed on OVH servers. This web hosting has a negative reputation because it is often used in spam and malware distribution operations. In a recent HOSTExploit report , he was ranked 5th in the ranking of 50 web hosts that serve malicious content (top 50).
The names of many of these domains, in spelling, are very similar to the names of legitimate sites and companies. This approach is a common tactic to hide the true goals of using domains that acted as command C & C servers. For example, domain names such as “wearwellgarments.eu” and “secuina.com” were used, which are very similar to the legitimate websites “wearwellgarments.com” and “secunia.com”, the latter belongs to the well-known security company Secunia .
The origin of the malicious files
Analysis of this campaign allowed us to determine the geographical origin of malicious files. With the help of several key indicators, it was established that these files were collected in India. Malicious files were digitally signed by an Indian company. In addition, signature time stamps vary between 5:06 and 13:45 UTC, which corresponds to an 8 hour working day between 10:36 and 19:15 in India. It is likely that the authors lived in this particular time zone.
Several malicious files have detected strings related to Indian culture, and some scripts use a variable called ramukaka .
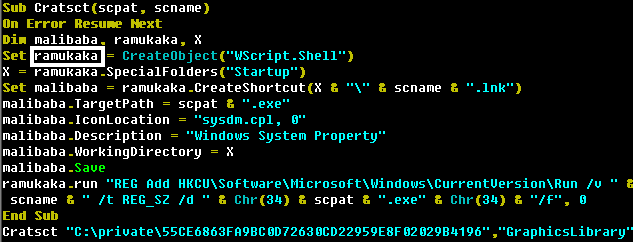
The combination of “Ramu Kaka” is quite common in Bollywood films and means attendants. Since this variable is used in a function whose purpose is to ensure the persistence of the presence of malicious code in the system, this name is quite well combined with its real function.
But the most compelling argument in favor of India, as the country of origin of the malicious files, is the data of our telemetry system. We found that many variants of the Trojan program were recorded in the same region in a rather short period of time. Each variant of malicious code had insignificant differences from each other.
Infection statistics
According to our telemetry system, it is clear that Pakistan was the region that suffered the most from the activities of this attack. The following diagram shows the distribution of detections recorded for all malicious files that we associate with this campaign over the past two years.

In addition to this, we collected statistics based on the syncholy data. For this, three domains were used, and we were able to obtain the geography of the spread of infected hosts based on the IP addresses that addressed our registered domains.
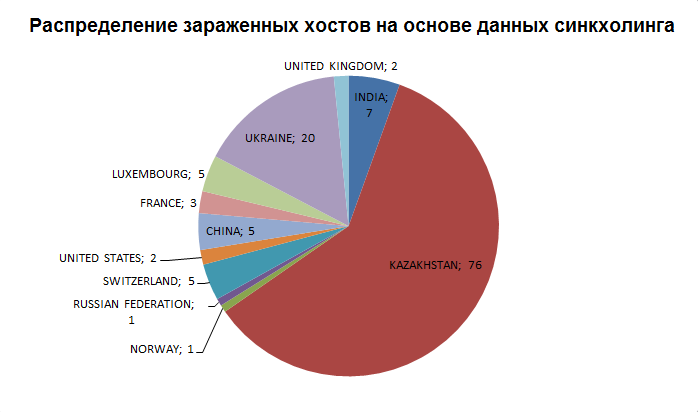
Obviously, the statistics on the two diagrams are completely different. In the case of statistics obtained through syncholy, Ukraine and Kazakhstan account for three-quarters of all IP addresses of hosts that we were able to fix. Apparently with the help of syncholing, we managed to fix only some small part of the infected systems, while the statistics on the detections shows the picture more holistically.
Conclusion
In our analysis, we looked at a targeted attack and provided evidence that this attack targets various targets around the world. Obviously, it has roots in India. Despite the fact that malicious activity has been recorded in many countries around the world, Pakistan has the highest number of infections. In fact, targeted attacks have long ceased to be rare, but in this case, a relatively small number of any tools and techniques can be noted that would allow the malicious code to provide itself with good secrecy in the system. The attackers used simple obfuscation of strings in executable files, did not use encryption when transmitting traffic over the network, gave legitimacy to malware by embedding additional items in the Start menu, used existing publicly available tools to collect information about the infected system. These methods tell us that the attackers reacted to this operation without a proper approach. On the other hand, they may not have seen the need to use means of concealment, since the existing methods provided the proper minimum masking.
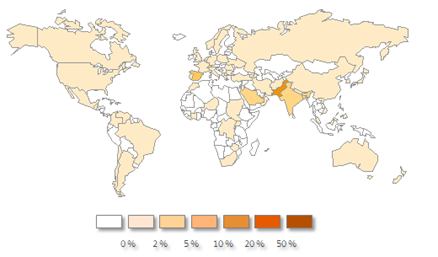
After the publication of our analysis, Symantec also identified the regions most affected by this attack. As in the case of our telemetry systems, Symantec confirmed that the compromised hosts are most in South Asia, namely Pakistan. India is indicated as a potential country of origin for this attack.
[Symantec data]
Object Names
ESET detects the malicious objects used in this campaign under the following names.
Win32 / Agent.NLD worm
Win32 / Spy.Agent.NZD trojan
Win32 / Spy.Agent.OBF trojan
Win32 / Spy.Agent.OBV trojan
Win32 / Spy.KeyLogger.NZL trojan
Win32 / Spy.KeyLogger.NZN trojan
Win32 / Spy.VB.NOF trojan
Win32 / Spy.VB.NRP trojan
Win32 / TrojanDownloader.Agent.RNT trojan
Win32 / TrojanDownloader.Agent.RNV trojan
Win32 / TrojanDownloader.Agent.RNW trojan
Win32 / VB.NTC trojan
Win32 / VB.NVM trojan
Win32 / VB.NWB trojan
Win32 / VB.QPK trojan
Win32 / VB.QTV trojan
Win32 / VB.QTY trojan
Win32 / Spy.Agent.NVL trojan
Win32 / Spy.Agent.OAZ trojan

As part of this campaign, a valid digital certificate was used, which signed malicious executables. This was done to provide greater secrecy and create an image of the legitimacy of the installed malicious code. The certificate was issued at the end of July 2011 for the Indian company Technical and Commercial Consulting Pvt. Ltd., based in New Delhi.
')

We promptly contacted VeriSign and, according to the information provided by us, this certificate was promptly withdrawn. In total, as a result of the investigation of this incident, more than 70 malicious files (!) Signed with this digital signature were detected. Based on the timestamps of these files, we created a timeline that reflects the timeline of the signing of these files.

Based on the information collected by us, it is clear that the attackers most actively signed malicious files from March to June 2012. Then we see a slight decline in activity from June to August 2012. Further, there is a surge in the use of the certificate in August and September 2012 despite that he was already recalled.
In addition to these signed files, during the investigation several normal executable files that were missing a signature were also found. Some of these files were discovered by us in early 2011.
Droppers and initial attack vector
In one of the attack vectors for users, attackers exploited the popular vulnerability CVE-2012-0158. This vulnerability was exploited through a specially crafted Microsoft Office file, as a result of which arbitrary code was executed in the OS. We observed an RTF document that, when it was opened on a vulnerable system, executed a two-stage shell code. This shellcode sent system information to the feds.comule.com domain, and also downloaded the malicious file from digitalapp.org.
Another attack vector was to use executable files that were masked as Microsoft Word or PDF files. These files were distributed via email. As soon as the user launched the file, this malicious program downloaded and launched for execution additional malicious modules. To disguise, the malicious code did display a Word document with a specific content to the user, and we saw several such documents on various topics.
One of the documents found used the theme of the Indian armed forces. In fact, we do not have specific information about which specific people or organizations these files were intended for. However, based on our telemetry system, we assume that the targets were people and educational institutions in Pakistan.
The screenshot below shows one of these PDF documents, the content of which, in fact, is a compilation from various sources. This document was delivered through a self-extracting archive, which had the name “pakistandefencetoindiantopmiltrysecreat.exe”.


The following screenshot shows a PDF document that was delivered via the executable file “pakterrisiomforindian.exe”. In this case, the content of the document is based on the text from the Asian Defense blog. On this blog, gather news about the military theme of the Asian region. The data of our telemetry system shows that this file was first discovered in August 2011 on computers in Pakistan.

Payload
We found a sufficient number of payload types that were used in this attack. For its installation, as in other cases, droppers were used. Its main task is to send important data from an infected computer to an attacking remote server. The following table contains families of executable files and their modules with a description of functions. All these modules were used in the targeted attack.

The information stolen from the infected computer is sent to the attacker's server in unencrypted form. Such a decision is really puzzling, since it compromises the length of time the malicious code has been on the computer, which, in turn, is an important factor for the targeted attack. In this case, network traffic analysis allows you to detect malicious activity. The screenshot below shows the part of the keylogger log file.

This log file is quite informative and displays the characters typed by the user, as well as information about the window in which they were typed and at what time. Due to the fact that these files are sent to the server in an unencrypted form, the task of detecting malicious code on a computer is solved quite simply by analyzing the traffic on the network.
It should be noted that this malicious code added items to the “Start” menu with a deceptive name for the user. The screenshot below shows an example of such a menu item.

The Trojan uses methods that allow its various components to ensure their survival after a reboot. But at the same time, it can not be called invisible. Since targeted attacks usually try to be imperceptible in the system for as long as possible, we were surprised by the lack of appropriate mechanisms for this threat.
C & C structure
Most of the malicious files that we have analyzed contain embedded URLs that are used to download additional modules, as well as to send data from the infected system to the attacker's server. Sometimes the URLs of the managers of the C & C servers are stored in the body of the malicious code in an unencrypted form. In other cases, a fairly basic encryption method is used using one-character rotation (ROT-1) operation as shown below.
“Gjmftbttpdjbuf / ofu” -> “filesassociate.net”
We found more than 20 domains that were used in this campaign. Despite the fact that some of these domains are still marked as active, most of them are no longer translated to IP addresses. For most of these domains, hosting was performed on OVH servers. This web hosting has a negative reputation because it is often used in spam and malware distribution operations. In a recent HOSTExploit report , he was ranked 5th in the ranking of 50 web hosts that serve malicious content (top 50).
The names of many of these domains, in spelling, are very similar to the names of legitimate sites and companies. This approach is a common tactic to hide the true goals of using domains that acted as command C & C servers. For example, domain names such as “wearwellgarments.eu” and “secuina.com” were used, which are very similar to the legitimate websites “wearwellgarments.com” and “secunia.com”, the latter belongs to the well-known security company Secunia .
The origin of the malicious files
Analysis of this campaign allowed us to determine the geographical origin of malicious files. With the help of several key indicators, it was established that these files were collected in India. Malicious files were digitally signed by an Indian company. In addition, signature time stamps vary between 5:06 and 13:45 UTC, which corresponds to an 8 hour working day between 10:36 and 19:15 in India. It is likely that the authors lived in this particular time zone.
Several malicious files have detected strings related to Indian culture, and some scripts use a variable called ramukaka .

The combination of “Ramu Kaka” is quite common in Bollywood films and means attendants. Since this variable is used in a function whose purpose is to ensure the persistence of the presence of malicious code in the system, this name is quite well combined with its real function.
But the most compelling argument in favor of India, as the country of origin of the malicious files, is the data of our telemetry system. We found that many variants of the Trojan program were recorded in the same region in a rather short period of time. Each variant of malicious code had insignificant differences from each other.
Infection statistics
According to our telemetry system, it is clear that Pakistan was the region that suffered the most from the activities of this attack. The following diagram shows the distribution of detections recorded for all malicious files that we associate with this campaign over the past two years.

In addition to this, we collected statistics based on the syncholy data. For this, three domains were used, and we were able to obtain the geography of the spread of infected hosts based on the IP addresses that addressed our registered domains.

Obviously, the statistics on the two diagrams are completely different. In the case of statistics obtained through syncholy, Ukraine and Kazakhstan account for three-quarters of all IP addresses of hosts that we were able to fix. Apparently with the help of syncholing, we managed to fix only some small part of the infected systems, while the statistics on the detections shows the picture more holistically.
Conclusion
In our analysis, we looked at a targeted attack and provided evidence that this attack targets various targets around the world. Obviously, it has roots in India. Despite the fact that malicious activity has been recorded in many countries around the world, Pakistan has the highest number of infections. In fact, targeted attacks have long ceased to be rare, but in this case, a relatively small number of any tools and techniques can be noted that would allow the malicious code to provide itself with good secrecy in the system. The attackers used simple obfuscation of strings in executable files, did not use encryption when transmitting traffic over the network, gave legitimacy to malware by embedding additional items in the Start menu, used existing publicly available tools to collect information about the infected system. These methods tell us that the attackers reacted to this operation without a proper approach. On the other hand, they may not have seen the need to use means of concealment, since the existing methods provided the proper minimum masking.
After the publication of our analysis, Symantec also identified the regions most affected by this attack. As in the case of our telemetry systems, Symantec confirmed that the compromised hosts are most in South Asia, namely Pakistan. India is indicated as a potential country of origin for this attack.

[Symantec data]
Object Names
ESET detects the malicious objects used in this campaign under the following names.
Win32 / Agent.NLD worm
Win32 / Spy.Agent.NZD trojan
Win32 / Spy.Agent.OBF trojan
Win32 / Spy.Agent.OBV trojan
Win32 / Spy.KeyLogger.NZL trojan
Win32 / Spy.KeyLogger.NZN trojan
Win32 / Spy.VB.NOF trojan
Win32 / Spy.VB.NRP trojan
Win32 / TrojanDownloader.Agent.RNT trojan
Win32 / TrojanDownloader.Agent.RNV trojan
Win32 / TrojanDownloader.Agent.RNW trojan
Win32 / VB.NTC trojan
Win32 / VB.NVM trojan
Win32 / VB.NWB trojan
Win32 / VB.QPK trojan
Win32 / VB.QTV trojan
Win32 / VB.QTY trojan
Win32 / Spy.Agent.NVL trojan
Win32 / Spy.Agent.OAZ trojan
Source: https://habr.com/ru/post/180225/
All Articles