Mail.Ru is testing a new way to infect computers

Sometime in the middle of the night, nostalgia broke through me and I decided to download the composition of Angelica Varum - “The Town” from rabbits.
I find it suitable bitrate, choose mp3 and download .
But for some reason the .exe file was downloaded ... and from a strange address dls3.moilru.ru/output/.../02/96/6b/9f/audio/varum_anzhelika_-_gorodok_zaycev_net.exe
What kind of nonsense I think.
')
I choose .rar format, the same is downloaded - .exe file size of 160KB.
I run whois by domain and get:
domain: MOILRU.RU nserver: ns1.reg.ru. nserver: ns2.reg.ru. state: REGISTERED, DELEGATED, UNVERIFIED person: Private Person registrar: REGRU-REG-RIPN admin-contact: http://www.reg.ru/whois/admin_contact created: 2013.05.13 paid-till: 2014.05.13 free-date: 2014.06.13 source: TCI Oops! Fresh!
Upload the file to VirusTotal and get a report on the file.
Screenshots of file properties.
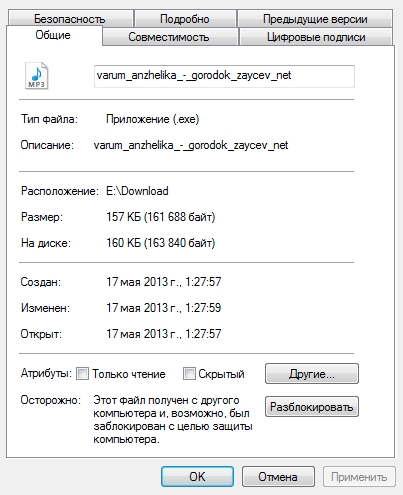
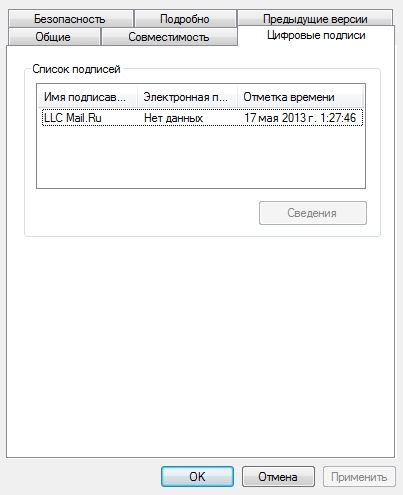
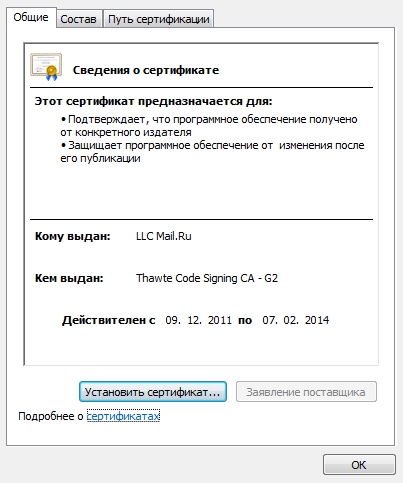
Selectively poked other songs, everywhere the executable file swings instead of mp3.
The downloaded files have a different size, but all have a signature with the mail.ru certificate.
My user agent:
Mozilla/5.0 (Windows NT 6.1; WOW64; rv:21.0) Gecko/20100101 Firefox/21.0 Change it to Android. Immediately a redirect goes to m.zaycev.net and now normal mp3 is being downloaded ...
Wow!
Listened, called, music for the night.
In the comments I was reminded of another article .
PS I ask a rhetorical question - how can one, without the knowledge of mail.ru, sign so many different files with its certificate?
PPS Checked the site's IP, DNS and gateway provider - no spoofing. Checked the second antivirus - clean.
Update.
(12 hours later):The distributing domain has been changed to downloader.com and the url format has been changed:
http://dwnloader.com/MjU1NTtodHRwJTNBJTJGJTJGZGwuemF5Y2V2Lm5ldCUyRjExNWE3ZGY2LTE4NjMtNGQxNy1iOWRjLWM5MTI0ZGIwZGVkOCUyRjE2NTA1JTJGMTY1MDUxOCUyRm5hdGFsaV8tX29fYm96aGVfa2Frb3lfbXV6aGNoaW5hXyh6YXljZXYubmV0KS5tcDM7bmFtZT1uYXRhbGlfLV9vX2JvemhlX2tha295X211emhjaGluYV8oemF5Y2V2Lm5ldCkubXAzO3NpemU9ODY1MDc1Mjt0eXBlPW1wMw== A little later, the domain was changed to dawnloader.ru again (78.140.165.153)
After two days, replaced by dwnloader.net (46.254.18.232).
Which redirects to other domains, with which the download occurs:
vengera.ru savtopo.ru dojdipo.ru astonka.ru hkovma.ru owsezam.ru gudlet.ru pilagi.ru zyankokhi.ru iqtaxib.ru goditsa.ru ekzofo.ru rfaksa.ru liqra.ru skachatfayl.ru dwnloader.net These domains are also involved in the infection of torrentino.com visitors.
All of them are on IP 146.255.192.214. Datacenter does not respond to sad :(
Inside the same file signed by the certificate from mail.ru.
I’m in Ukraine, maybe that's why I’m not getting a file signed by LLC Pentagon.
Update.
(16 hours later)There was an inscription at the jump:
The file is downloaded using a special loader (Trojans) from our partners, Mail.ru and Rambler . Running the bootloader is absolutely safe for your computer, which is digitally confirmed, but false positives of antiviruses are possible.
I translate: We have agreed with Kaspersky Lab, he does not consider these files to be Trojans, and Dr.Web, which classifies files as Trojans, is not an antivirus at all.
And the response from distributors:
From: Nikolay nik [a] openprog.ru
You complain about the Boot Loader (which supposedly contains a virus).
We hereby notify that there is a false positive response. The file itself is nothing more than an HTTP client for downloading any content and is definitely not a virus. The file is digitally signed by its manufacturer, Mail.Ru, and is located on Mail.Ru servers, which further confirms the origin and reliability of this file.
Heuristic analyzers of some antiviruses can be triggered by the internal structure and actions of this file, but we guarantee that the response data is false.
If you have questions about files that are distributed from our server, please write about them to nik [a] openprog.ru
They also lack IP and they have backdated new data centers :(
Source: https://habr.com/ru/post/179981/
All Articles