Microsoft and Adobe have released updates for their products.
Microsoft announced the release of a series of updates aimed at eliminating vulnerabilities in their products. Previously announced in the pre-release (May 9) security fixes cover 33 unique vulnerabilities (2 fixes with the Critical status and 8 with the Important status). A detailed report (including correlation fixes with CVE ID) can be found here . As in past months, updates are aimed at fixing Critical vulnerabilities in Internet Explorer and are of the Remote Code Execution type . One of these updates closes the vulnerability in all versions of the browser, starting with version 6 and ending with the latest IE 10. Another Critical fix is aimed at closing flaw in IE 8. The 0day exploit for this vulnerability was recently used to launch an attack on US government agencies with subsequent delivery of malicious code. IE patching requires a reboot.

One of the Critical updates ( MS13-037 ) fixes 10 vulnerabilities in Internet Explorer (version 6-10). To exploit these vulnerabilities, a use-after-free technique is used when accessing the browser code to an already deleted object in memory, which may result in memory corruption and then executing arbitrary code in the context of the current user. These include: CVE-2013-0811, CVE-2013-1306, CVE-2013-1307, CVE-2013-1308, CVE-2013-1309, CVE-2013-1310, CVE-2013-1311, CVE-2013- 1312, CVE-2013-1313, CVE-2013-2551.
')
Another Critical update ( MS13-038 ) also removes a vulnerability that is exploited by the use-after-free method, but only for IE8. We mentioned that the exploit for this vulnerability was used in attacks on US government agencies, so the vulnerability is is-being-exploited-in-the-wild .
Note that Microsoft on May 8 released a special tool Fix It tool, which is designed to fix a vulnerability in IE8.
Two important updates are aimed at fixing vulnerabilities in kernel-mode drivers. MS13-039 regulates the fixing of the CVE-2013-1305 vulnerability in the http.sys driver for Windows 8, Server 2012, RT and is of the Denial of Service type . The vulnerability is present in the driver code that incorrectly processes some HTTP headers. As a result, an attacker can cause an infinite loop during the processing of HTTP headers, when they are delivered to the http.sys driver, which is a serious problem for both the server and the client.
The second important update for kernel mode drivers ( MS13-046 ) is related to components such as the DirectX driver (dxgkrnl.sys) and the Windows subsystem driver (win32k.sys). In the case of dxgkrnl.sys, we are talking about fixing the CVE-2013-1332 vulnerability, which is of type Elevation of Privelege and concerns the incorrect operation of the driver code with objects in memory. These vulnerabilities are present in all versions of the OS starting with Windows XP and ending with Windows 8, Server 2012 and RT. In the case of win32k.sys, we are talking about CVE-2013-1333 and CVE-2013-1334 vulnerabilities, which also have the Elevation of Privelege type .
In general, fixes are focused on products such as Microsoft Windows , Office,. NET Framework , Windows Essentials and Microsoft Lync .
We recommend that our users install updates as soon as possible and, if you have not already done so, enable automatic delivery of updates using Windows Update (this option is enabled by default).
Adobe has released updates for its products: ColdFusion (hotfix), Adobe Flash Player , Adobe Reader, and Acrobat .
Updates for Adobe Flash Player fix a total of 13 vulnerabilities that could lead to the execution of arbitrary code.
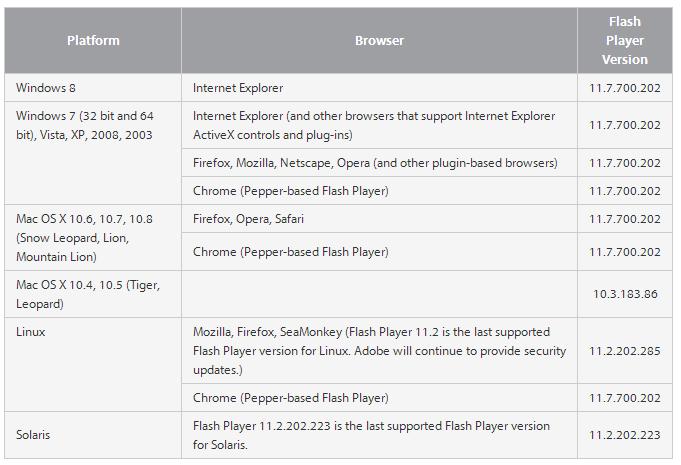
We recommend that users check the version of Flash Player used by your browser, for this you can use the official. adobe source here or here . Note that browsers such as Google Chrome and Internet Explorer 10 are automatically updated with the release of the new version of Flash Player. You can get information on updating Flash for your browser via this link .
Current Flash Player versions for browsers:
Updates for Adobe Reader and Acrobat close 27 vulnerabilities , most of which can lead to the execution of arbitrary code when viewing a specially crafted PDF. These include: CVE-2013-2718, CVE-2013-2719, CVE-2013-2720, CVE-2013-2721, CVE-2013-2722, CVE-2013-2723, CVE-2013-2725, CVE-2013- 2726, CVE-2013-2731, CVE-2013-2732, CVE-2013-2734, CVE-2013-2735, CVE-2013-2736, CVE-2013-3337, CVE-2013-3338, CVE-2013-3339, CVE-2013-3340, CVE-2013-3341.

One of the updates is aimed at eliminating the use-after-free vulnerability (CVE-2013-2550), which can be used to bypass sandbox mode in Adobe Reader. Vulnerabilities leading to stack overflow (CVE-2013-2724) and memory buffer (CVE-2013-2730, CVE-2013-2733) are also subject to correction.
Software versions to be updated.
Adobe Reader and Acrobat users have an auto-update feature. To update manually use this recommendation .
In the case of ColdFusion, hotfix addresses two vulnerabilities: CVE-2013-1389 and CVE-2013-3336.
Vulnerability CVE-2013-3336 allows unauthorized users to receive files from a remote server, in addition, it has the status of is-being-exploited-in-the-wild , that is, this vulnerability is already exploited by hackers.

be secure.

One of the Critical updates ( MS13-037 ) fixes 10 vulnerabilities in Internet Explorer (version 6-10). To exploit these vulnerabilities, a use-after-free technique is used when accessing the browser code to an already deleted object in memory, which may result in memory corruption and then executing arbitrary code in the context of the current user. These include: CVE-2013-0811, CVE-2013-1306, CVE-2013-1307, CVE-2013-1308, CVE-2013-1309, CVE-2013-1310, CVE-2013-1311, CVE-2013- 1312, CVE-2013-1313, CVE-2013-2551.
')
Another Critical update ( MS13-038 ) also removes a vulnerability that is exploited by the use-after-free method, but only for IE8. We mentioned that the exploit for this vulnerability was used in attacks on US government agencies, so the vulnerability is is-being-exploited-in-the-wild .
Note that Microsoft on May 8 released a special tool Fix It tool, which is designed to fix a vulnerability in IE8.

Two important updates are aimed at fixing vulnerabilities in kernel-mode drivers. MS13-039 regulates the fixing of the CVE-2013-1305 vulnerability in the http.sys driver for Windows 8, Server 2012, RT and is of the Denial of Service type . The vulnerability is present in the driver code that incorrectly processes some HTTP headers. As a result, an attacker can cause an infinite loop during the processing of HTTP headers, when they are delivered to the http.sys driver, which is a serious problem for both the server and the client.
The second important update for kernel mode drivers ( MS13-046 ) is related to components such as the DirectX driver (dxgkrnl.sys) and the Windows subsystem driver (win32k.sys). In the case of dxgkrnl.sys, we are talking about fixing the CVE-2013-1332 vulnerability, which is of type Elevation of Privelege and concerns the incorrect operation of the driver code with objects in memory. These vulnerabilities are present in all versions of the OS starting with Windows XP and ending with Windows 8, Server 2012 and RT. In the case of win32k.sys, we are talking about CVE-2013-1333 and CVE-2013-1334 vulnerabilities, which also have the Elevation of Privelege type .
In general, fixes are focused on products such as Microsoft Windows , Office,. NET Framework , Windows Essentials and Microsoft Lync .
We recommend that our users install updates as soon as possible and, if you have not already done so, enable automatic delivery of updates using Windows Update (this option is enabled by default).
Adobe has released updates for its products: ColdFusion (hotfix), Adobe Flash Player , Adobe Reader, and Acrobat .
Updates for Adobe Flash Player fix a total of 13 vulnerabilities that could lead to the execution of arbitrary code.

We recommend that users check the version of Flash Player used by your browser, for this you can use the official. adobe source here or here . Note that browsers such as Google Chrome and Internet Explorer 10 are automatically updated with the release of the new version of Flash Player. You can get information on updating Flash for your browser via this link .
Current Flash Player versions for browsers:

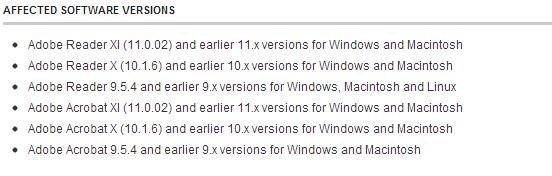
Updates for Adobe Reader and Acrobat close 27 vulnerabilities , most of which can lead to the execution of arbitrary code when viewing a specially crafted PDF. These include: CVE-2013-2718, CVE-2013-2719, CVE-2013-2720, CVE-2013-2721, CVE-2013-2722, CVE-2013-2723, CVE-2013-2725, CVE-2013- 2726, CVE-2013-2731, CVE-2013-2732, CVE-2013-2734, CVE-2013-2735, CVE-2013-2736, CVE-2013-3337, CVE-2013-3338, CVE-2013-3339, CVE-2013-3340, CVE-2013-3341.

One of the updates is aimed at eliminating the use-after-free vulnerability (CVE-2013-2550), which can be used to bypass sandbox mode in Adobe Reader. Vulnerabilities leading to stack overflow (CVE-2013-2724) and memory buffer (CVE-2013-2730, CVE-2013-2733) are also subject to correction.
Software versions to be updated.

Adobe Reader and Acrobat users have an auto-update feature. To update manually use this recommendation .
In the case of ColdFusion, hotfix addresses two vulnerabilities: CVE-2013-1389 and CVE-2013-3336.
Vulnerability CVE-2013-3336 allows unauthorized users to receive files from a remote server, in addition, it has the status of is-being-exploited-in-the-wild , that is, this vulnerability is already exploited by hackers.

be secure.
Source: https://habr.com/ru/post/179315/
All Articles