Honest lot
Alice, Bob, Carol and Dave decided to choose whom to run for Klin. They could ask Trent, who is trustworthy, but he is already lying drunk in the next room. Then conscious friends decided to come up with a distributed protocol for the draw.
Alice encrypts all four names with her key and randomly writes on a piece of paper and shows it to everyone. Then Bob takes the encrypted lines on this piece of paper, encrypts it with his key and also writes new ciphertexts on a new piece of paper in random order. Then Carol and Dave do it.
Thus, in front of Alice there is a leaf with four encrypted strings, and at the same time each of the participants sorted them as he wanted.
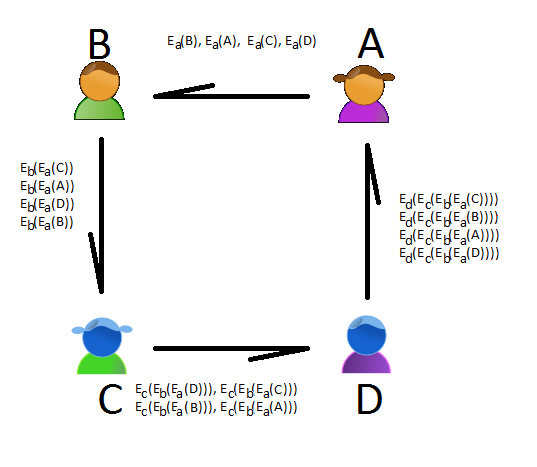
Figure 1 - Scheme for transferring encrypted messages between participants (an Ea (s) entry denotes encryption with Alice's key s)
Then Alice selects one of these lines.
After that, Dave shows how he encrypts the strings with the key and the whole drunken company tensely decrypts the strings with Dave's key, making sure that the decoded strings match those that Carol gave Dave and remembering which of them Alice chose. The same happens with the keys of the other participants. Finally, Alice shows her key, and suffering from thirst, our heroes unscramble the last lines and see what name Alice chose.
')
Everything is good, of course, but what if Alice the Fox wants to deceive everyone, or friends who are immensely respectful of Bob want to come to an agreement against him?
It would seem that Alice is the first to encrypt messages and herself chooses one of the ciphertexts. But at the same time, she does not know how other participants sorted him, and encrypted them with their keys. Therefore, it just stands in front of a blind choice between four equivalent lines.
In the case of Bob, even if all the participants behind him show their keys to each other, they still don’t know how Bob encrypted and sorted the lines in his step, and after his turn in front of them there will also be a set of incomprehensible ciphertexts sorted in the Bob order.
PS The protocol was invented at lunch with a colleague and inspired by Bruce Schneier’s Applied Cryptography. And thanks to my muse for help in preparing the article.
Alice encrypts all four names with her key and randomly writes on a piece of paper and shows it to everyone. Then Bob takes the encrypted lines on this piece of paper, encrypts it with his key and also writes new ciphertexts on a new piece of paper in random order. Then Carol and Dave do it.
Thus, in front of Alice there is a leaf with four encrypted strings, and at the same time each of the participants sorted them as he wanted.

Figure 1 - Scheme for transferring encrypted messages between participants (an Ea (s) entry denotes encryption with Alice's key s)
Then Alice selects one of these lines.
After that, Dave shows how he encrypts the strings with the key and the whole drunken company tensely decrypts the strings with Dave's key, making sure that the decoded strings match those that Carol gave Dave and remembering which of them Alice chose. The same happens with the keys of the other participants. Finally, Alice shows her key, and suffering from thirst, our heroes unscramble the last lines and see what name Alice chose.
')
Everything is good, of course, but what if Alice the Fox wants to deceive everyone, or friends who are immensely respectful of Bob want to come to an agreement against him?
It would seem that Alice is the first to encrypt messages and herself chooses one of the ciphertexts. But at the same time, she does not know how other participants sorted him, and encrypted them with their keys. Therefore, it just stands in front of a blind choice between four equivalent lines.
In the case of Bob, even if all the participants behind him show their keys to each other, they still don’t know how Bob encrypted and sorted the lines in his step, and after his turn in front of them there will also be a set of incomprehensible ciphertexts sorted in the Bob order.
PS The protocol was invented at lunch with a colleague and inspired by Bruce Schneier’s Applied Cryptography. And thanks to my muse for help in preparing the article.
Source: https://habr.com/ru/post/178951/
All Articles