New IE8 0day operated in-the-wild
Today it became known that the new 0day for Internet Explorer version 8 (excluding versions 6, 7, 9, 10) is being actively exploited in the wild and was used to install malware. In particular, the traces of the attack were found on the computers of US government officials responsible for the field of nuclear research. The vulnerability is type “Remote Code Execution” (CVE-2013-1347).
As evidenced by information from the Microsoft Security Advisory ( 2847140 ), the vulnerability is present when accessing an freed memory block (use-after-free).
The initial point of infection was the compromised US Department of Labor website, which redirected users to a set of exploits and then installed Poison Ivy RAT .
MS recommends using EMET to prevent such attacks. Configure EMET for IE here .
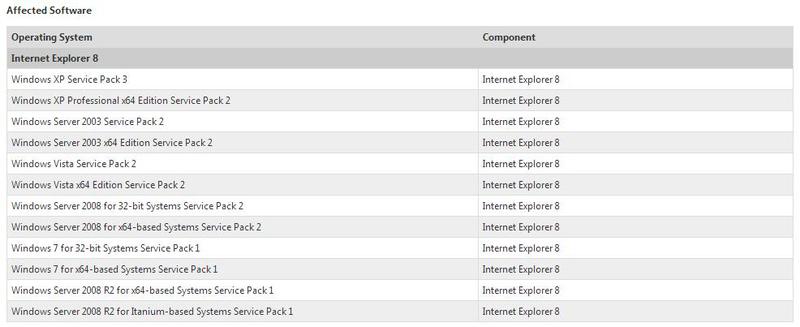
As evidenced by information from the Microsoft Security Advisory ( 2847140 ), the vulnerability is present when accessing an freed memory block (use-after-free).
Microsoft is aware of the vulnerability of Internet Explorer 8. He is aware of these vulnerability.
')
Internet Explorer 6, Internet Explorer 7, Internet Explorer 9, and Internet Explorer 10 are not affected by the vulnerability.
This is a remote code execution vulnerability. The Internet Explorer has been selected or has been allocated. It can be an attacker to use the Internet Explorer. This is a site where you’ve been able to access this website.
The initial point of infection was the compromised US Department of Labor website, which redirected users to a set of exploits and then installed Poison Ivy RAT .
MS recommends using EMET to prevent such attacks. Configure EMET for IE here .

Source: https://habr.com/ru/post/178689/
All Articles