Completely free two-factor authentication for Citrix Web Interface 5.x using Mobile-OTP as a soft token
Two-factor authentication - providing login information from two different types of authentication, in most cases the first source is a username and password that are immutable and can be compromised (by trojans, keyloggers, etc.). For this, the second type of authentication is used, which is a device that generates a unique temporary password / code valid for a short period (5-30 seconds), which ensures security even if the temporary password is intercepted.
In addition, a temporary password is generated by devices that are not subject to interception risks, usually by hardware keys, for example:

Citrix Web Interface out of the box supports two-factor authentication using Aladdin SafeWord and RSA SecurID hardware keys, which cost between 25-50USD, as well as two-factor authentication using a RADIUS server, with which you can connect keys cheaper (about 5USD)
 In order to further save for the same purpose, you can use soft tokens on mobile phones. By the way, the goal of introducing soft tokens can also be convenience for the end user - the hardware key is an additional device that you should always have with you, and the majority of users have a phone at hand all the time.
In order to further save for the same purpose, you can use soft tokens on mobile phones. By the way, the goal of introducing soft tokens can also be convenience for the end user - the hardware key is an additional device that you should always have with you, and the majority of users have a phone at hand all the time.
')
There are a lot of free soft tokens for phones on the market, for example Google Authenticator , but our choice fell on the Mobile-OTP project for the following reasons:
OK, the choice is justified, let's move on to implementation.
You can use any ready-made RADIUS server, and only connect the pam module for MOTP (for example, motpy ). But it is easier to use the finished assembly MOTP-AS
MOTP-AS is a RADIUS server with support for Mobile-OTP plus a web interface for creating and connecting users. You can download VMWare image and run it right on the machine where WI is installed, or on another host in the same grid. It is clear that the MOTP-AS server should not be accessible from the outside .
MOTP-AS provides a convenient admin interface, connecting a soft token to the user is quite simple:
1. Add a client for RADIUS
"System" => "RADIUS" => "Add new RADIUS client"
Name: Citrix Web Interface
Secret: RADsecret - Radius secret (we will also point it to in the WI config)
IP: 192.168.0.100 - the address where the WI server will be available
2. Add a user
"Administration" => "Users" => "Add new User"
User: john
Name: John Doe
Role: user
3. Add a soft token
=> "Administration" => "Devices" => "Add new Device"
Name: nokia 6310i
Secret: 1234567812345678
Here, the value of the Secret field is taken from the client-generated phone, see the instructions of the specific client for generating the secret.
Shared Secret for the RADIUS server will be stored in a text file on the local disk, the path to it is indicated by the variable RADIUS_SECRET_PATH in the web.config file (the path must be relative to / WEB_INF)
- in the Citrix Web Interface management console, right-click and select “authentication methods”
- Click Properties and select Two-Factor authentication
- Specify RADIUS in the Two-Factor settings list
- Enter the address where the MOTP-AS server is available (leave the port as standard - 1812)
- click OK

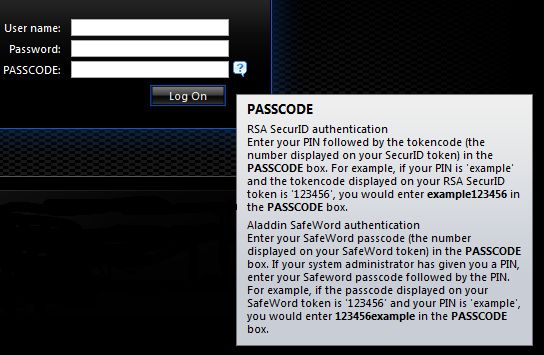
It should work like this: when entering the system, an additional PASSCODE code will be requested, where you need to enter a temporary password
Successfully applied to WI versions 5.3 and 5.4.
Detailed information on connecting users here
In addition, a temporary password is generated by devices that are not subject to interception risks, usually by hardware keys, for example:

Citrix Web Interface out of the box supports two-factor authentication using Aladdin SafeWord and RSA SecurID hardware keys, which cost between 25-50USD, as well as two-factor authentication using a RADIUS server, with which you can connect keys cheaper (about 5USD)
 In order to further save for the same purpose, you can use soft tokens on mobile phones. By the way, the goal of introducing soft tokens can also be convenience for the end user - the hardware key is an additional device that you should always have with you, and the majority of users have a phone at hand all the time.
In order to further save for the same purpose, you can use soft tokens on mobile phones. By the way, the goal of introducing soft tokens can also be convenience for the end user - the hardware key is an additional device that you should always have with you, and the majority of users have a phone at hand all the time.')
There are a lot of free soft tokens for phones on the market, for example Google Authenticator , but our choice fell on the Mobile-OTP project for the following reasons:
- customer availability for all phones (and not only for ios / android / blackberry) - J2ME, WP7, PalmOS, webOS, Maemo, Openmoko
- additional protection by pincode (which is not in Google Authenticator), that is, even if the device is lost, a temporary password without a pin will not be generated
- Availability of source codes for all clients - you can rebuild with your branding, if you really need
OK, the choice is justified, let's move on to implementation.
Install and configure RADIUS server for MOTP
You can use any ready-made RADIUS server, and only connect the pam module for MOTP (for example, motpy ). But it is easier to use the finished assembly MOTP-AS
MOTP-AS
MOTP-AS is a RADIUS server with support for Mobile-OTP plus a web interface for creating and connecting users. You can download VMWare image and run it right on the machine where WI is installed, or on another host in the same grid. It is clear that the MOTP-AS server should not be accessible from the outside .
Connecting users

MOTP-AS provides a convenient admin interface, connecting a soft token to the user is quite simple:
1. Add a client for RADIUS
"System" => "RADIUS" => "Add new RADIUS client"
Name: Citrix Web Interface
Secret: RADsecret - Radius secret (we will also point it to in the WI config)
IP: 192.168.0.100 - the address where the WI server will be available
2. Add a user
"Administration" => "Users" => "Add new User"
User: john
Name: John Doe
Role: user
3. Add a soft token
=> "Administration" => "Devices" => "Add new Device"
Name: nokia 6310i
Secret: 1234567812345678
Here, the value of the Secret field is taken from the client-generated phone, see the instructions of the specific client for generating the secret.
Configure Citrix Web Interface to use MOTP-AS as the second authentication factor.
Specify Shared Secret for RADIUS server on WI
Shared Secret for the RADIUS server will be stored in a text file on the local disk, the path to it is indicated by the variable RADIUS_SECRET_PATH in the web.config file (the path must be relative to / WEB_INF)
Enable RADIUS authentication for the XenApp site
- in the Citrix Web Interface management console, right-click and select “authentication methods”
- Click Properties and select Two-Factor authentication
- Specify RADIUS in the Two-Factor settings list
- Enter the address where the MOTP-AS server is available (leave the port as standard - 1812)
- click OK

Well, in principle, and all
It should work like this: when entering the system, an additional PASSCODE code will be requested, where you need to enter a temporary password

Successfully applied to WI versions 5.3 and 5.4.
Detailed information on connecting users here
Source: https://habr.com/ru/post/178595/
All Articles