EMET v4 released in beta
The new version of the Enhanced Mitigation Experience Toolkit (EMET) 4.0 has been released in beta. EMET uses the necessary preventive methods to protect applications from various kinds of attack, which are aimed at exploiting flaws in the software and changing the code execution flow. EMET helps protect applications, including from 0day exploits that can use ROP to bypass DEP and ASLR . The new version of EMET introduces a number of additional features that allow you to detect various scenarios of exploitation and application compromise.
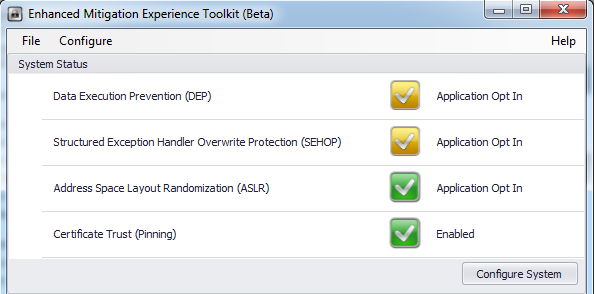
Downloadable distributive can be downloaded here . To install EMET .NET Framework 4 is required.
')
New features v4.
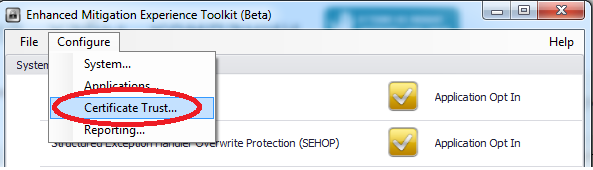
SSL / TLS Certificate Trust features
Additional features for managing SSL / TLS certificates for the Internet Explorer browser and creating special rules. The ability to detect an attack of the MITM type (Man in the middle) when using third-party certificates (the ability to filter Root CA certificates based on the Key Size, Allowed Country options).
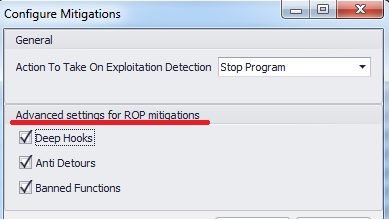
Strengthened mitigations, blocking bypasses
Includes new exploit blocking features that use new varieties of ROP (anti-EMET). In particular, several new handlers were added for the kernelbase! VirtualAlloc and ntdll! NtAllocateVirtualMemory functions , without which ROP mitigation could be circumvented. The “Banned API” feature allows you to block DEP, ASLR bypass techniques using ntdll! LdrHotPatchRoutine .
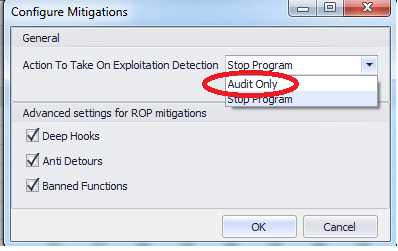
Audit Mode
Allows you to disable the ability to complete the EMET-controlled process in which an operation attempt was detected (by default).
More information on EMET settings and their decoding here (v3.5).
The official release of EMET v4.0 is expected on May 14, 2013.

Downloadable distributive can be downloaded here . To install EMET .NET Framework 4 is required.
')
New features v4.
SSL / TLS Certificate Trust features
Additional features for managing SSL / TLS certificates for the Internet Explorer browser and creating special rules. The ability to detect an attack of the MITM type (Man in the middle) when using third-party certificates (the ability to filter Root CA certificates based on the Key Size, Allowed Country options).

Strengthened mitigations, blocking bypasses
Includes new exploit blocking features that use new varieties of ROP (anti-EMET). In particular, several new handlers were added for the kernelbase! VirtualAlloc and ntdll! NtAllocateVirtualMemory functions , without which ROP mitigation could be circumvented. The “Banned API” feature allows you to block DEP, ASLR bypass techniques using ntdll! LdrHotPatchRoutine .

Audit Mode
Allows you to disable the ability to complete the EMET-controlled process in which an operation attempt was detected (by default).

More information on EMET settings and their decoding here (v3.5).
The official release of EMET v4.0 is expected on May 14, 2013.
Source: https://habr.com/ru/post/177265/
All Articles