The researcher demonstrated the interception of control of the aircraft using an Android application
Today at the Hack In The Box conference in Amsterdam, Hugo Teso, a security consultant from n.runs AG, reported on a completely reliable scenario of hijacking an airplane using a simple Android application.
Teso has been working in the IT industry for the past 11 years, but even more time he is a commercial pilot, which allowed him to combine his two professions and study the state of affairs with the security of aviation computer systems and communication protocols.
')
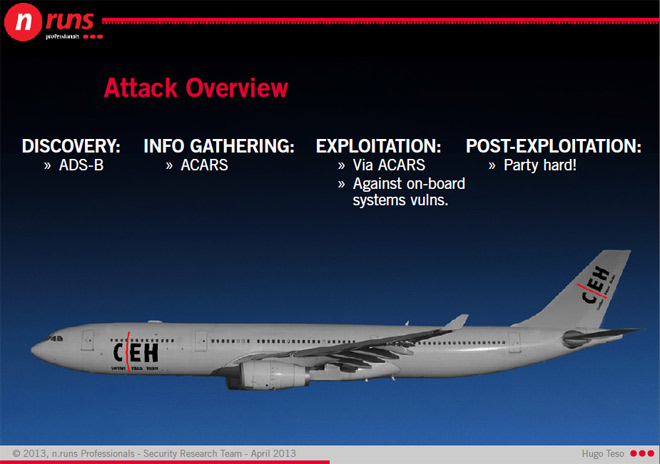
Taking advantage of two new aviation systems for vulnerability detection, information gathering and operation, creating a framework (SIMON) and an Android application (PlaneSploit) that deliver an attacking message to the aircraft's flight control system (Flight Management Systems), he demonstrated the ability to gain complete control over the aircraft by making the virtual plane "dance to its tune."
One of the two technologies he abused is Automatic Dependent Surveillance-Broadcast (ADS-B). It sends information about each aircraft (identifier, current position, altitude, etc.) via the onboard transmitter to the air traffic controller, allowing aircraft equipped with this system to receive flight and weather information about all other ships currently in the air in the current area. .
The second is the Aircraft Communications Addressing and Reporting System (ACARS), which is used to exchange messages between the aircraft and the dispatcher by radio or satellite, as well as to automatically deliver information about each phase of flight to the center.

Both of these technologies are extremely unsafe and susceptible to a number of passive and active attacks. Teso used ADS-B to select a target, and ACARS to collect information about the onboard computer, as well as to crack its vulnerabilities by sending a fake malicious message.
Based on his own research, Teso developed the SIMON framework, which intentionally made it work only in a virtual environment, so that it cannot be used on real planes. His test lab consists of a set of software and hardware, but the means of connection and communication, as well as the methods of hacking, are absolutely the same that could be used in real life.
Since it is almost impossible to detect the framework in the Flight Management System, there is no need to mask it as a rootkit. Using SIMON, an attacker can download certain malicious code to a remote FSM, download flight plans, detailed commands, or even custom plug-ins that can be developed for the framework.
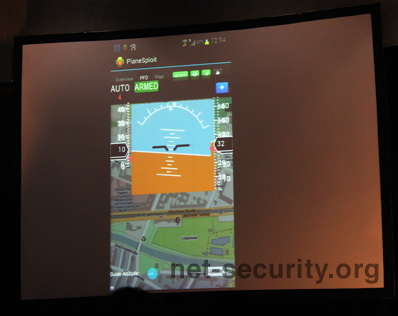
To make things even more interesting - or simple - Tesco showed an Android application that uses SIMON to control the aircraft remotely on the move. The application, intricately called PlaneSploit, with a simple interface full of different features. And this is a worthy example of technological evolution - ten years ago we did not have phones with color screens, and today we are hacking airplanes from smartphones.
PlaneSploit uses the Flightradar24 tracker and you can tap on any plane in the area. In a virtual environment, the distance of the aircraft does not matter, but in the real world everything will depend on the antenna used (if we are talking directly about the aircraft) or the system (if you use ACARS, such as SITA or ARINC).
The user interface of the application is divided into functions: detection, information collection, operation and post-operation. The attacker can click on any active aircraft and get its ID, current position and final point of flight. If the aircraft's system is hacked (the researcher specified a number of attack vectors, but didn’t specifically cover methods), the application alerts the user with a message or a push notification. The payload can be loaded with a simple tap, and from this point on the flight control system is remotely controlled by the hacker. Hacking other systems related to FMS is also possible.
Teso at the conference showed some functionality of its application:
Teso, for obvious reasons, did not disclose many details about the tools he used to attack and the vulnerabilities that have yet to be fixed. However, he notes that he was pleasantly surprised by the response of the industry to his research, which did not deny their existence, but promised to help him in his research.
He notes that the old systems, which originate in the 70s, will be difficult, if not impossible, to fix, but the new ones just patch with new firmware and changes in the programs.
The solution for pilots to regain control of the aircraft is still simple - this kind of attack only works when autopilot is on, so you just have to turn it off, then landing on “analog instruments”.
The bad news is that there are not so many new aircraft, and the pilots need to understand that the computer has been hacked in order to carry out maneuvers.
Teso has been working in the IT industry for the past 11 years, but even more time he is a commercial pilot, which allowed him to combine his two professions and study the state of affairs with the security of aviation computer systems and communication protocols.

')
Taking advantage of two new aviation systems for vulnerability detection, information gathering and operation, creating a framework (SIMON) and an Android application (PlaneSploit) that deliver an attacking message to the aircraft's flight control system (Flight Management Systems), he demonstrated the ability to gain complete control over the aircraft by making the virtual plane "dance to its tune."
One of the two technologies he abused is Automatic Dependent Surveillance-Broadcast (ADS-B). It sends information about each aircraft (identifier, current position, altitude, etc.) via the onboard transmitter to the air traffic controller, allowing aircraft equipped with this system to receive flight and weather information about all other ships currently in the air in the current area. .
The second is the Aircraft Communications Addressing and Reporting System (ACARS), which is used to exchange messages between the aircraft and the dispatcher by radio or satellite, as well as to automatically deliver information about each phase of flight to the center.

Both of these technologies are extremely unsafe and susceptible to a number of passive and active attacks. Teso used ADS-B to select a target, and ACARS to collect information about the onboard computer, as well as to crack its vulnerabilities by sending a fake malicious message.

Based on his own research, Teso developed the SIMON framework, which intentionally made it work only in a virtual environment, so that it cannot be used on real planes. His test lab consists of a set of software and hardware, but the means of connection and communication, as well as the methods of hacking, are absolutely the same that could be used in real life.
Since it is almost impossible to detect the framework in the Flight Management System, there is no need to mask it as a rootkit. Using SIMON, an attacker can download certain malicious code to a remote FSM, download flight plans, detailed commands, or even custom plug-ins that can be developed for the framework.
To make things even more interesting - or simple - Tesco showed an Android application that uses SIMON to control the aircraft remotely on the move. The application, intricately called PlaneSploit, with a simple interface full of different features. And this is a worthy example of technological evolution - ten years ago we did not have phones with color screens, and today we are hacking airplanes from smartphones.
PlaneSploit uses the Flightradar24 tracker and you can tap on any plane in the area. In a virtual environment, the distance of the aircraft does not matter, but in the real world everything will depend on the antenna used (if we are talking directly about the aircraft) or the system (if you use ACARS, such as SITA or ARINC).
The user interface of the application is divided into functions: detection, information collection, operation and post-operation. The attacker can click on any active aircraft and get its ID, current position and final point of flight. If the aircraft's system is hacked (the researcher specified a number of attack vectors, but didn’t specifically cover methods), the application alerts the user with a message or a push notification. The payload can be loaded with a simple tap, and from this point on the flight control system is remotely controlled by the hacker. Hacking other systems related to FMS is also possible.
Teso at the conference showed some functionality of its application:
- flight to a given hacker point;
- setting filters - points in space, when approaching which the plane will do something;
- meeting with the land;
- notify pilots of problems
Teso, for obvious reasons, did not disclose many details about the tools he used to attack and the vulnerabilities that have yet to be fixed. However, he notes that he was pleasantly surprised by the response of the industry to his research, which did not deny their existence, but promised to help him in his research.

He notes that the old systems, which originate in the 70s, will be difficult, if not impossible, to fix, but the new ones just patch with new firmware and changes in the programs.
The solution for pilots to regain control of the aircraft is still simple - this kind of attack only works when autopilot is on, so you just have to turn it off, then landing on “analog instruments”.
The bad news is that there are not so many new aircraft, and the pilots need to understand that the computer has been hacked in order to carry out maneuvers.
Source: https://habr.com/ru/post/176381/
All Articles