A new security hole in MegaFon allows hacking subscriber accounts
An almost successful hacker attack was made on one of our corporate cell phones.
Fortunately, quite quickly managed to figure out where the "grow legs."
We found another "hole" in the protection of Megaphone, which we share with you.
It applies to all subscribers of the network.
A few days ago I reported to the customer service about the "hole" on the site of MegaFon. At the time of 08/04/2013, the vulnerability was not fixed.
The scheme is elegant and simple, like an ax. Allows you to steal money from your account without your knowledge.
')
So, MegaFon has a necessary and useful thing - Service Guide. It allows you to manage services without long-term voice communication “your call is very important to us.”
And the entrance to it is made correctly, not allowing to perform hacking through the selection of a password. Simple, but captcha is present.
Everything is good, but captcha damages the usability of the site. Designers sometimes win common sense. There is a portal duplicating the functions of the phone messages.megafon.ru , the entrance to which is not protected from automatic password search:
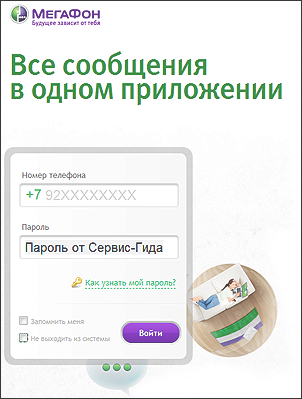
But the login-password pair is used for logging in as for Service Guide.
Service Guide allows you to manage services, connect tariffs, configure notifications.
What did the thieves do?
Having processed so automatically and massively thousands of phones you can earn indecent money.
To the credit of the mobile operator's specialists, it is worth noting that at the moment of entering the Service Guide and this “SMS site” an SMS notification arrives.
In my case, the entrance to the SMS portal occurred at 00:23 minutes, at that time I was awake, and immediately through the mobile Internet I changed the password from the Service Guide to a more stable one.
Unfortunately, changing the password does not reveal the user from the Megaphone SMS site, and malicious users can still sit there.
Thieves did not have time to enter the Service Guide before me. It is possible that their frequent input of an already irrelevant password into the Service Guide itself led to its blocking. But if I did not have time to change the password - who knows what they would do.
Within 24 hours, confirmation codes for paid subscriptions arrived twice. They continue to come now.
Protection measures against this attack for Megaphone:
1. Put a protection against automatic logging in here messages.megafon.ru and never joke like that - COMPLETED
2. Allow the use of Latin letters in the Service Guide password
3. Make different login / password pair for SG and SMS-site
Security measures for subscribers:
0. Do not use Service Guide at all, but if you have already begun
1. Put a stronger password on the Service Guide, for example
2. In any case, change the password from the Service Guide
3. In the Service Guide or subscriber service block the use of any paid services or subscriptions, writing off money from short numbers. For subscribers of MegaFon - this is a free service " Stop-content ".
Thanks for attention. I wish everyone safe communication and bug-free billing.
ZERO UPDATE: Useful related link from KiiA www.mobile-review.com/articles/2013/ums-podpiski.shtml
UPD1: Fresh article on Habré " about Service Guide "
UPD2: April 9, 2013 Megaphone added captcha to the form. The main gap is closed! Thanks to the staff of MegaFon for a fairly prompt response.
UPD3: Megaphone Answer in the comments to the article.
UPD4: Another article about the holes of Megaphone - fresh, not yet closed!
UPDATE2015 - the hole is not closed! Message from habrachiteli from Volgograd:
There is a captcha, but it protects nothing.
If you enter an incorrect login-password and any captcha, then we will see the message “incorrect login / password”.
And if we write the correct login-password and any captcha, then we will see "not correct captcha".
Thus, you can infinitely still brut form.
A captcha will be needed only with the pledge.
For a brutal, a captcha is not a hindrance, you can write 1111 in the captcha field always and normally brut.
- Vulnerability fixed, Megaphone Well done!
Fortunately, quite quickly managed to figure out where the "grow legs."
We found another "hole" in the protection of Megaphone, which we share with you.
It applies to all subscribers of the network.
A few days ago I reported to the customer service about the "hole" on the site of MegaFon. At the time of 08/04/2013, the vulnerability was not fixed.
The scheme is elegant and simple, like an ax. Allows you to steal money from your account without your knowledge.
')
So, MegaFon has a necessary and useful thing - Service Guide. It allows you to manage services without long-term voice communication “your call is very important to us.”
And the entrance to it is made correctly, not allowing to perform hacking through the selection of a password. Simple, but captcha is present.
Everything is good, but captcha damages the usability of the site. Designers sometimes win common sense. There is a portal duplicating the functions of the phone messages.megafon.ru , the entrance to which is not protected from automatic password search:

But the login-password pair is used for logging in as for Service Guide.
Service Guide allows you to manage services, connect tariffs, configure notifications.
What did the thieves do?
- With the help of this SMS-site, they pick up (apparently, by brute force) the password from the Service Guide, and enter it.
- They get access to the Service Guide: to read incoming SMS and send them.
- Subscribe to paid services (stupid MegafonPro, my estimated opinion).
- By subscription comes SMS with a confirmation code.
- Enter this code on the subscription site.
- Receive agent interest from Megaphone for the debited money from your account for a paid subscription.
Having processed so automatically and massively thousands of phones you can earn indecent money.
To the credit of the mobile operator's specialists, it is worth noting that at the moment of entering the Service Guide and this “SMS site” an SMS notification arrives.
In my case, the entrance to the SMS portal occurred at 00:23 minutes, at that time I was awake, and immediately through the mobile Internet I changed the password from the Service Guide to a more stable one.
Unfortunately, changing the password does not reveal the user from the Megaphone SMS site, and malicious users can still sit there.
Thieves did not have time to enter the Service Guide before me. It is possible that their frequent input of an already irrelevant password into the Service Guide itself led to its blocking. But if I did not have time to change the password - who knows what they would do.
Within 24 hours, confirmation codes for paid subscriptions arrived twice. They continue to come now.
Protection measures against this attack for Megaphone:
1. Put a protection against automatic logging in here messages.megafon.ru and never joke like that - COMPLETED
2. Allow the use of Latin letters in the Service Guide password
3. Make different login / password pair for SG and SMS-site
Security measures for subscribers:
0. Do not use Service Guide at all, but if you have already begun
1. Put a stronger password on the Service Guide, for example
2. In any case, change the password from the Service Guide
3. In the Service Guide or subscriber service block the use of any paid services or subscriptions, writing off money from short numbers. For subscribers of MegaFon - this is a free service " Stop-content ".
Thanks for attention. I wish everyone safe communication and bug-free billing.
ZERO UPDATE: Useful related link from KiiA www.mobile-review.com/articles/2013/ums-podpiski.shtml
UPD1: Fresh article on Habré " about Service Guide "
UPD2: April 9, 2013 Megaphone added captcha to the form. The main gap is closed! Thanks to the staff of MegaFon for a fairly prompt response.
UPD3: Megaphone Answer in the comments to the article.
UPD4: Another article about the holes of Megaphone - fresh, not yet closed!
UPDATE2015 - the hole is not closed! Message from habrachiteli from Volgograd:
There is a captcha, but it protects nothing.
If you enter an incorrect login-password and any captcha, then we will see the message “incorrect login / password”.
And if we write the correct login-password and any captcha, then we will see "not correct captcha".
Thus, you can infinitely still brut form.
A captcha will be needed only with the pledge.
For a brutal, a captcha is not a hindrance, you can write 1111 in the captcha field always and normally brut.
- Vulnerability fixed, Megaphone Well done!
Source: https://habr.com/ru/post/175939/
All Articles