Arbor Pravail APS and DDOS
Good to everyone!
Not so long ago, we compared several systems of protection against DDOS attacks, which we managed to “touch”. As promised, we share our impressions of the device we have chosen.



')
Here we will not tell you what it is, where the DDOS attack comes from and why, we are sure that you already know this. We will consider the practice of using the system in a particular example (there will be many pictures). So, meet Arbor Pravail APS !
About two months have passed from the moment of order to receipt.

A clearly visible box, worn in places, torn in places, sometimes painted with a pen or something else, but is this the main thing ?! Rather - open!

Opened, it seemed familiar Intel 2U chassis with a beautiful "attractive face" and we certainly climbed to look inside =)

To check - nothing unusual, two processors, memory ... the design feature gave out an unusual Silicom network card to our eye with a large heatsink, like on a GPU, it’s hot, overseas miracle =)

Enough "pampering", it's time to look at it in action!

We connected it to one of our test routers and began to configure. The steps are standard - the console, the address on the management port, the installation of acl and almost everything. The main thing - do not forget the key with the license, will not filter =)
In this post, we will not go into the features of the settings of Pravail operation modes, they are quite simple (groups, filters, parameters), if Habravchanam will be interested, we will make a separate post for each item. In short - Pravail has basic settings for automatic protection of groups, which are based on several types of protected objects (web, dns, mail, vpn, voip, file, rlogin). Each type has a relatively detailed setting with three levels of protection. Switching between levels can be done in one click, at a time all groups can be protected only at one level.
Get down to business!
DDOS attacks, different, come to us constantly. It is interesting to look at Pravail in business, is it really as good as the manufacturer says about it, because all manufacturers only say the best things about their products, don't they? =)
As an example, we will take a special case from the ordinary life of a regular web server, which we have put on real protection “for” Pravail. On this server, we practice protecting sites that are attacked by all sorts of not very good robots.
Day X and hour Y coincided (it did not take long to wait). We recorded an anomaly on our links, the total “excess” incoming traffic was approximately 3.5Gbit (~ 650kpps), in general, this is not much by modern standards, spamhaus knows hello to crooked-tuned dns servers = \
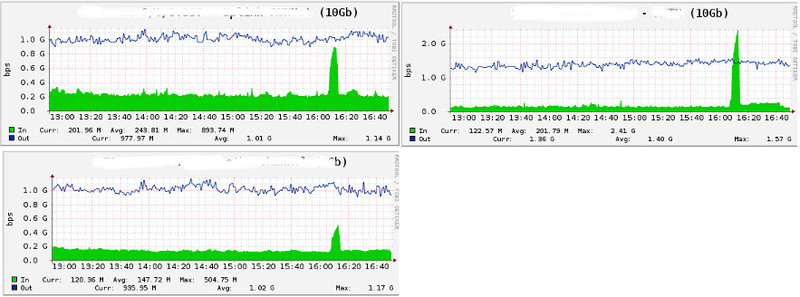
Through various filters on Pravail, everything “reached” about 130Mbit and 300k pps, what kind of traffic? Below we analyze in detail in the pictures.
Here we look at the reaction of the system to the attack, what Pravail sees and what can or should be done. Information will be displayed in the form of interface pictures with some description. The pictures are clear enough, there will be questions - ask.
In order that you can better represent the subject, please look at the picture:
This is the first thing we see getting into the system interface. Everything is clear and to the point.
After entering the Pravail interface, we get to the Dashboard. Here all important information on the protected groups and objects is collected. From where and where most of the traffic goes, what is the load on the interfaces and the system. If necessary, we can do several actions with groups and objects (block, view packets or detailed information about the traffic of the source country). All actions are done in one click, just move the cursor to the object of interest to us and select an action.
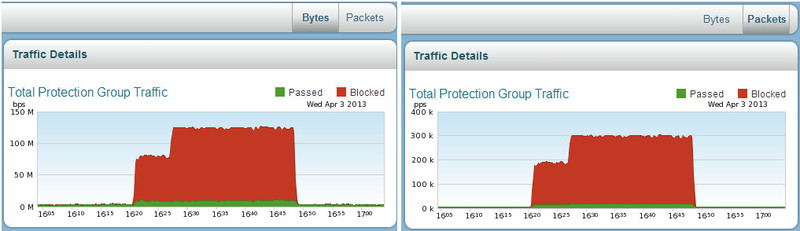
The first and most important schedule is the current situation with traffic in the group. The anomaly on the graph attracts our attention. We can look at the blocked hosts (reason, time, duration) and make a detailed analysis of the incoming packets (packet capture).

TOP-5 host sources and traffic recipients. Here we see where and where the traffic is coming from. Host blocking is available (blacklist) and packet analysis.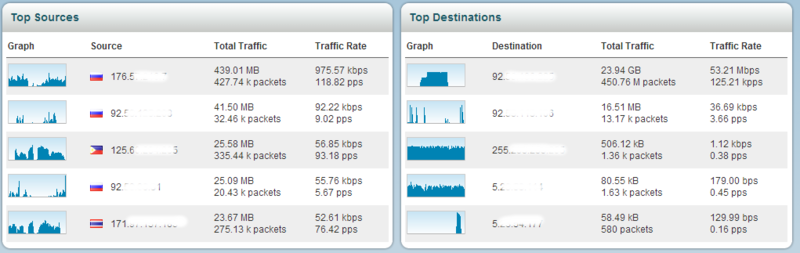
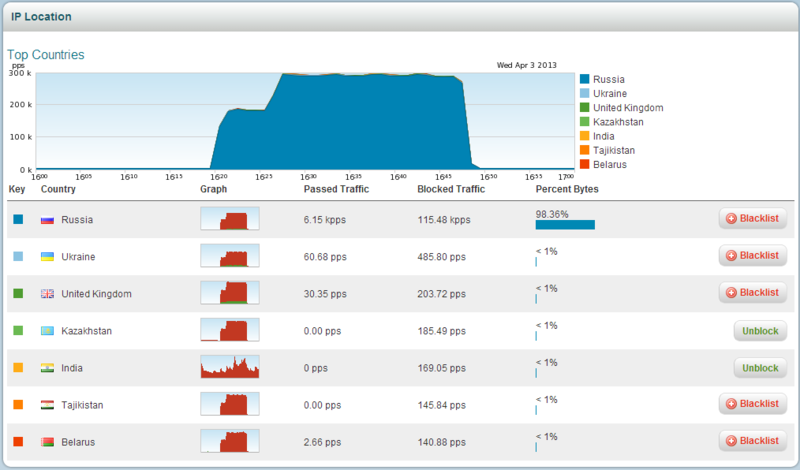
TOP-5 countries of traffic sources (remembering geography). It is possible to see the details of the traffic from the country, and block it for a specific group.

The state of the interfaces, our 10Gb ports on the input and output. Here we can do “packet capture” on each interface.

Summary of traffic. Nothing can be done here.
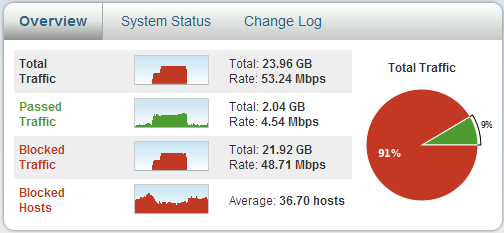
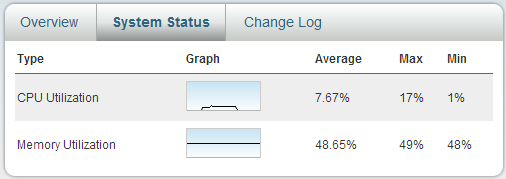
Load on the system: we look, we think. You can build assumptions for the future.
Next, we are transferred to the protected group, in our case - this group lists the IP addresses (you can also specify the network) of the protected objects. Inside we will see informative graphics with a minimum of actions regarding objects (ip addresses, countries, links, domains).
Protected group "protos" (we love SC, but the name is not connected =). We see the name, description, protected addresses, type of protection, its duration and the ability to edit the whole thing. You can select the period of data display.

Summary of protected group. Traffic in Mbps and pps, bad and good in details.
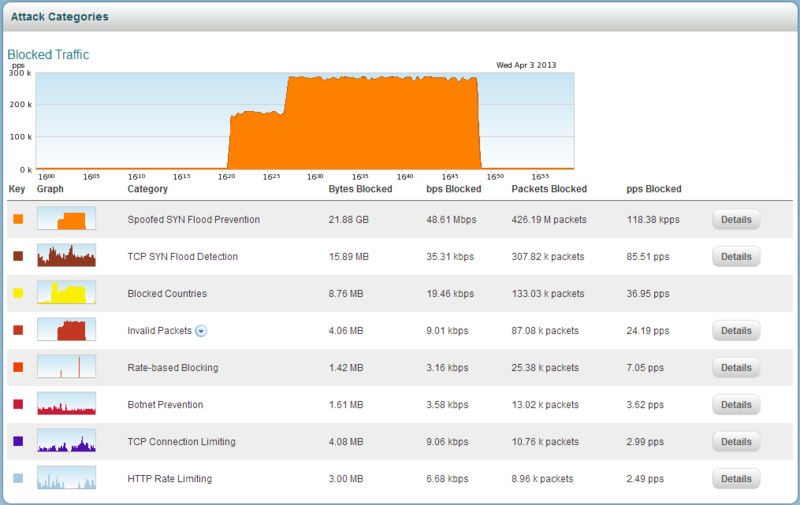
Sources of bad traffic. If necessary - you can see in details at the "blocked hosts" (blocked IP addresses) of each category. “Detail” gives us details, each category has its own data.
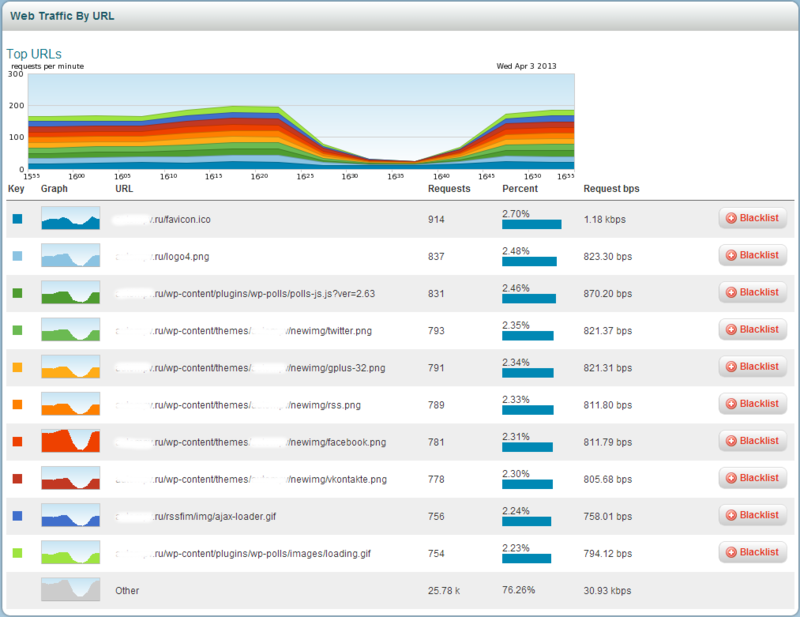
TOP queries to sites per minute. By addresses. More requests - higher in the top. It is possible to close obviously "invalid" requests. “Blacklist” is triggered earlier.
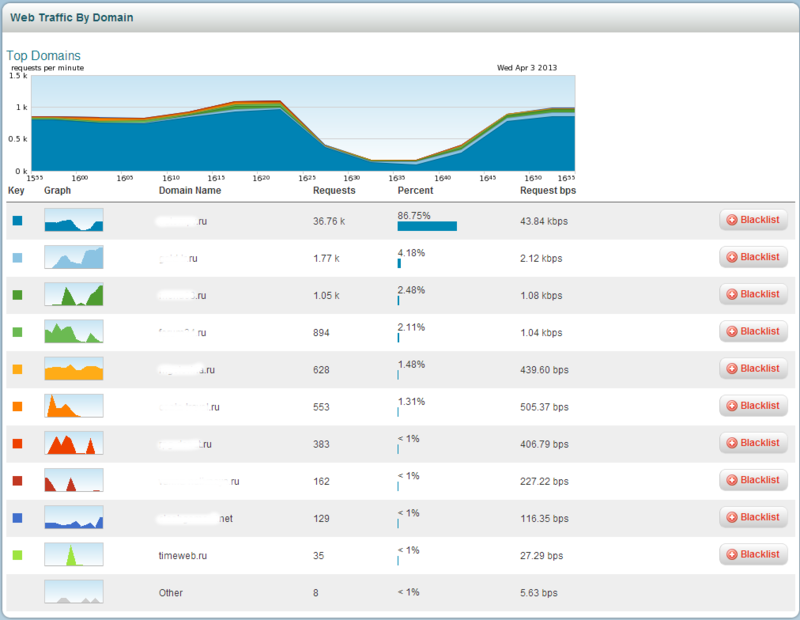
TOP queries to domains per minute. It works by analogy with TOP-url's.
"Best" countries. Determined by ip address. You can make "packet capture" for the desired country. My favorite section. Who knows why? =)
TOP protocols by type, informative schedule.
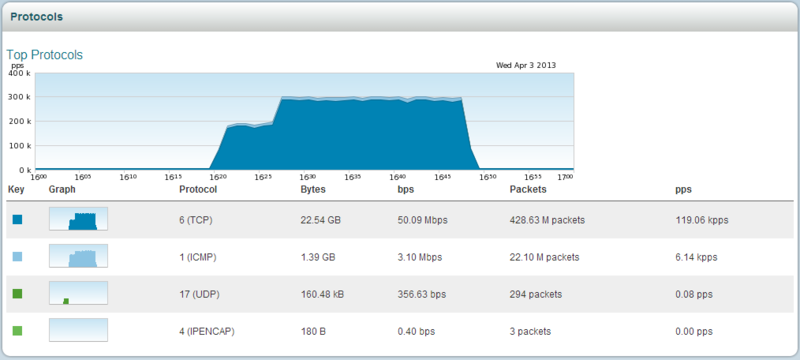
TOP services. You can also do packet capture.

TOP-ip addresses. You can watch the reason for blocking or disassemble packages. If the traffic from this address goes now. And, of course, “whitelist”, if the necessary addresses were blocked.

In general, this is all that Pravail gives us on monitoring the status of the protected group.
As a result, we have an excellent corporate-class device for protection against attacks on applications, which practically works in automatic mode. Of course, complex attacks will require manual adjustment of protection settings.
This device can be safely placed at the corporate network border and / or preventively protect important systems. Practice shows that with some adaptation of the system to the specifics of the protected object - you can achieve a confidently positive result. The protected object under attack will work quite well.
Can Internet providers use it? They can, but to protect individual nodes.
Why did we decide to choose Pravail? Because of all the systems that we saw, it was he who left the most pleasant impressions of work.
And now - we have something to protect ourselves and our users!
Not so long ago, we compared several systems of protection against DDOS attacks, which we managed to “touch”. As promised, we share our impressions of the device we have chosen.



')
Here we will not tell you what it is, where the DDOS attack comes from and why, we are sure that you already know this. We will consider the practice of using the system in a particular example (there will be many pictures). So, meet Arbor Pravail APS !
Quick reference
Arbor Networks was founded in 2000 at the University of Michigan, the innovative development of which was funded by the US Department of Defense. Since then, Arbor has specialized in detecting and handling online threats.
“He” has arrived!
About two months have passed from the moment of order to receipt.

A clearly visible box, worn in places, torn in places, sometimes painted with a pen or something else, but is this the main thing ?! Rather - open!

Opened, it seemed familiar Intel 2U chassis with a beautiful "attractive face" and we certainly climbed to look inside =)

To check - nothing unusual, two processors, memory ... the design feature gave out an unusual Silicom network card to our eye with a large heatsink, like on a GPU, it’s hot, overseas miracle =)

Enough "pampering", it's time to look at it in action!

We connected it to one of our test routers and began to configure. The steps are standard - the console, the address on the management port, the installation of acl and almost everything. The main thing - do not forget the key with the license, will not filter =)
In this post, we will not go into the features of the settings of Pravail operation modes, they are quite simple (groups, filters, parameters), if Habravchanam will be interested, we will make a separate post for each item. In short - Pravail has basic settings for automatic protection of groups, which are based on several types of protected objects (web, dns, mail, vpn, voip, file, rlogin). Each type has a relatively detailed setting with three levels of protection. Switching between levels can be done in one click, at a time all groups can be protected only at one level.
Get down to business!
Pravail vs DDOS = start
DDOS attacks, different, come to us constantly. It is interesting to look at Pravail in business, is it really as good as the manufacturer says about it, because all manufacturers only say the best things about their products, don't they? =)
As an example, we will take a special case from the ordinary life of a regular web server, which we have put on real protection “for” Pravail. On this server, we practice protecting sites that are attacked by all sorts of not very good robots.
Attack start
Day X and hour Y coincided (it did not take long to wait). We recorded an anomaly on our links, the total “excess” incoming traffic was approximately 3.5Gbit (~ 650kpps), in general, this is not much by modern standards, spamhaus knows hello to crooked-tuned dns servers = \

Through various filters on Pravail, everything “reached” about 130Mbit and 300k pps, what kind of traffic? Below we analyze in detail in the pictures.
Pravail: Start
Here we look at the reaction of the system to the attack, what Pravail sees and what can or should be done. Information will be displayed in the form of interface pictures with some description. The pictures are clear enough, there will be questions - ask.
In order that you can better represent the subject, please look at the picture:
Dashboard Pravail APS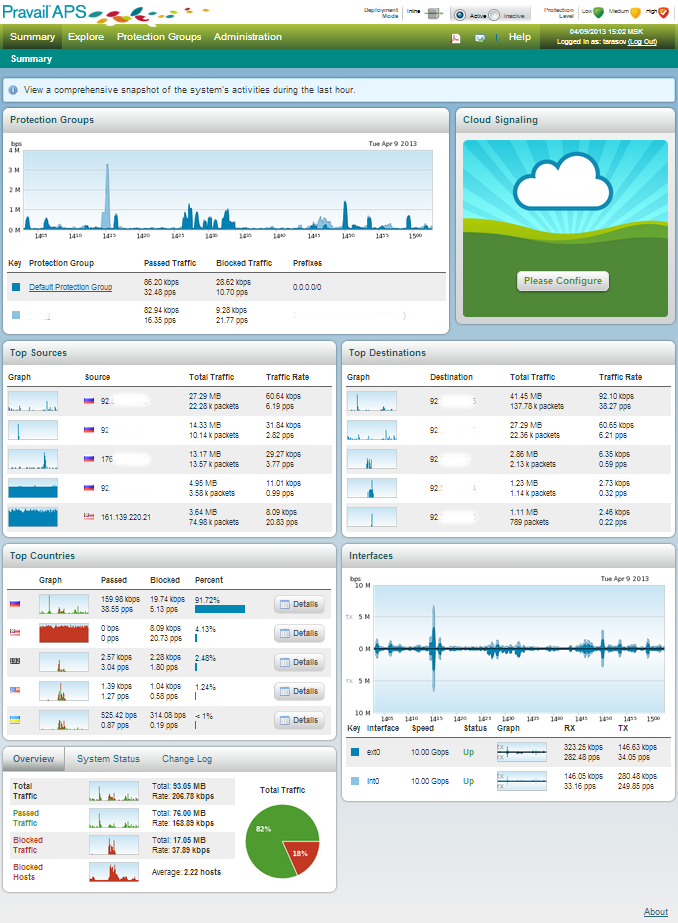

This is the first thing we see getting into the system interface. Everything is clear and to the point.
Here, look, look what I found!
After entering the Pravail interface, we get to the Dashboard. Here all important information on the protected groups and objects is collected. From where and where most of the traffic goes, what is the load on the interfaces and the system. If necessary, we can do several actions with groups and objects (block, view packets or detailed information about the traffic of the source country). All actions are done in one click, just move the cursor to the object of interest to us and select an action.
The first and most important schedule is the current situation with traffic in the group. The anomaly on the graph attracts our attention. We can look at the blocked hosts (reason, time, duration) and make a detailed analysis of the incoming packets (packet capture).

TOP-5 host sources and traffic recipients. Here we see where and where the traffic is coming from. Host blocking is available (blacklist) and packet analysis.

TOP-5 countries of traffic sources (remembering geography). It is possible to see the details of the traffic from the country, and block it for a specific group.

The state of the interfaces, our 10Gb ports on the input and output. Here we can do “packet capture” on each interface.

Summary of traffic. Nothing can be done here.

Load on the system: we look, we think. You can build assumptions for the future.

Well, I found, and then what?
Next, we are transferred to the protected group, in our case - this group lists the IP addresses (you can also specify the network) of the protected objects. Inside we will see informative graphics with a minimum of actions regarding objects (ip addresses, countries, links, domains).
Protected group "protos" (we love SC, but the name is not connected =). We see the name, description, protected addresses, type of protection, its duration and the ability to edit the whole thing. You can select the period of data display.

Summary of protected group. Traffic in Mbps and pps, bad and good in details.

Sources of bad traffic. If necessary - you can see in details at the "blocked hosts" (blocked IP addresses) of each category. “Detail” gives us details, each category has its own data.

TOP queries to sites per minute. By addresses. More requests - higher in the top. It is possible to close obviously "invalid" requests. “Blacklist” is triggered earlier.

TOP queries to domains per minute. It works by analogy with TOP-url's.

"Best" countries. Determined by ip address. You can make "packet capture" for the desired country. My favorite section. Who knows why? =)

TOP protocols by type, informative schedule.

TOP services. You can also do packet capture.

TOP-ip addresses. You can watch the reason for blocking or disassemble packages. If the traffic from this address goes now. And, of course, “whitelist”, if the necessary addresses were blocked.

In general, this is all that Pravail gives us on monitoring the status of the protected group.
What is the result?
As a result, we have an excellent corporate-class device for protection against attacks on applications, which practically works in automatic mode. Of course, complex attacks will require manual adjustment of protection settings.
This device can be safely placed at the corporate network border and / or preventively protect important systems. Practice shows that with some adaptation of the system to the specifics of the protected object - you can achieve a confidently positive result. The protected object under attack will work quite well.
Can Internet providers use it? They can, but to protect individual nodes.
Why did we decide to choose Pravail? Because of all the systems that we saw, it was he who left the most pleasant impressions of work.
And now - we have something to protect ourselves and our users!
Source: https://habr.com/ru/post/175919/
All Articles