Win32 / Gapz: the last episode
Today we publish the last part of the Win32 / Gapz bootkit analysis, and also want to submit a PDF that contains an analysis of this interesting threat with all the technical details. His analysis took several months of intensive reverse. In Gapz, we saw that the developers of these kinds of threats had reached a new level of complexity. We also believe that Win32 / Gapz, in fact, is the most complex bootkit of all that we have seen before. Detailed technical analysis of this threat can be found in our PDF document Mind the Gapz: The most complex bootkit ever analyzed? .
Our colleagues Yevgeny Rodionov and Alexander Matrosov conducted an analysis of the Win32 / Gapz code, starting in December 2012. This analysis revealed more and more interesting details about this threat.

')
We already wrote about Gapz earlier:
Win32 / Gapz has a fairly low prevalence level (since the beginning of its first detection, we recorded less than one hundred active samples). Most of these detections were in Russia. All known C & C panels were already closed at the time of the analysis started in December 2012. Domains for loading additional payload were registered through the DynDNS service. Below is a list of such URLs that were found in the dropper after unpacking:
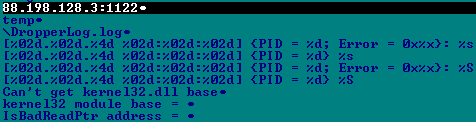
Modification of Win32 / Gapz.C , which contains the MBR infection functionality, sends debug information about the infection process to the following IP address:
Hosting for this IP address is located in Germany and, at the time of publication, is still online.
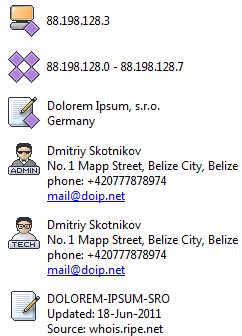
We found that this IP is associated with several domains: meetafora.ru, sukarabotay.com. Both of these domains were registered in 2011, and they expire in mid-2013. Now this IP has already stopped accepting debug information from the bot.
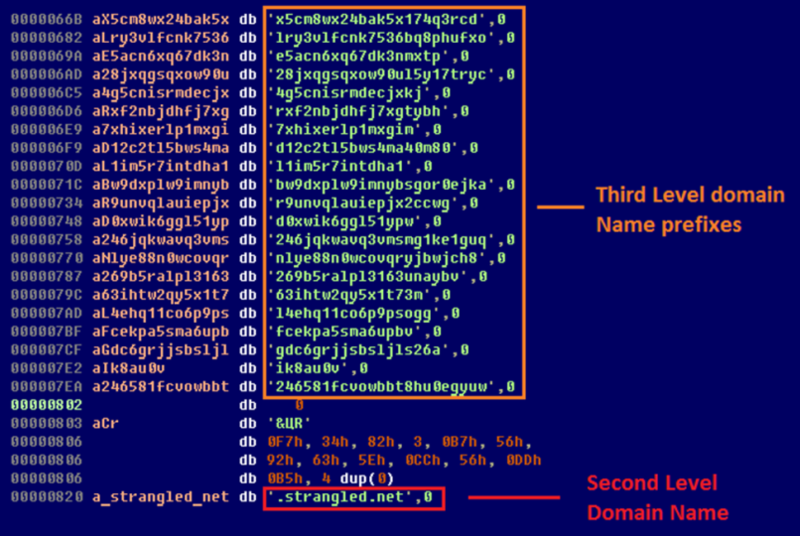
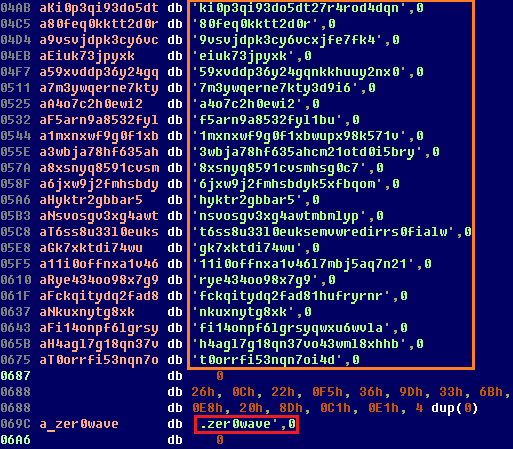
In all versions of Gapz that contained the bootkit, the addresses of additional C & Cs were extracted from the configuration file, which is stored in a hidden FS. This file is embedded in the main kernel-mode component located on a hidden disk. C & C domains are generated as third level domains (the variable component is the third level domain) using the dynamic DNS service strangled.net (used in Win32 / Gapz.A ).
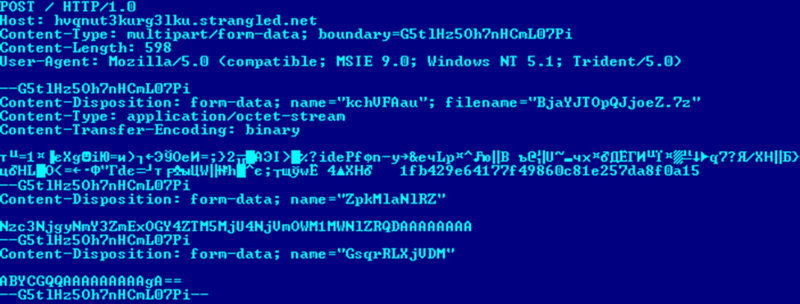
An example of networking with such a domain is presented below.
Win32 / Gapz.C modification uses a different domain generation scheme:
Interaction with the network in kernel mode is based on the manual implementation of the TCP / IP stack and HTTP protocol in order to bypass the check using local IPS / IDS. Full information on the implementation of the stack, see here .
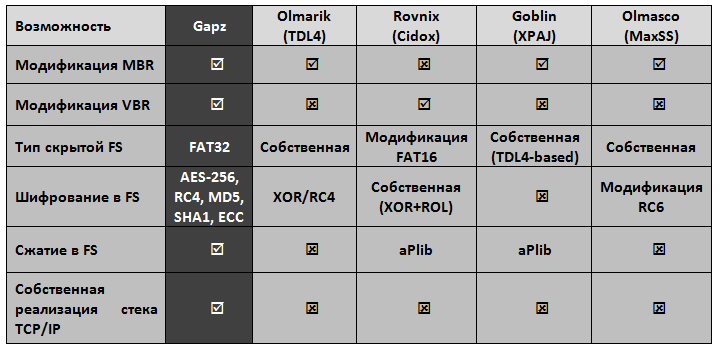
We believe that the Win32 / Gapz family is the most complex bootkit we’ve seen before. Below is a table of comparisons of Gapz features with other prominent members of bootkits:
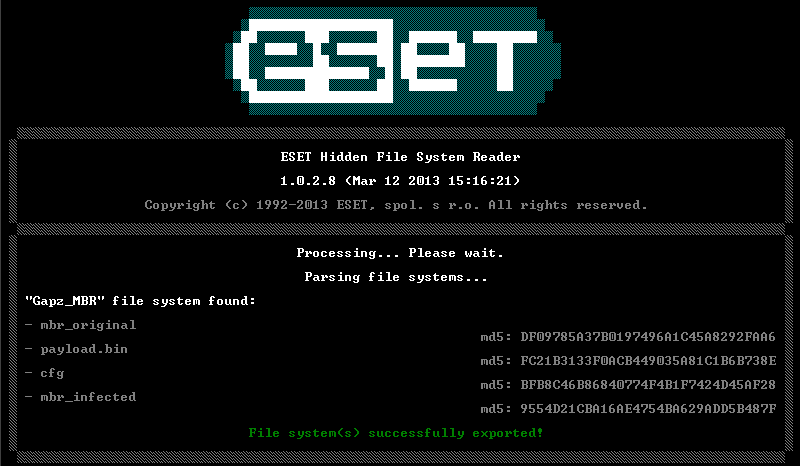
Hidden File System Reader with FS Gapz support
To assist security professionals and AV resellers facing Gapz, we updated our Hidden File System Reader tool with the requirements for this bootkit. Now it can also save hidden FS components from Gapz. The utility can be downloaded here .
Our colleagues Yevgeny Rodionov and Alexander Matrosov conducted an analysis of the Win32 / Gapz code, starting in December 2012. This analysis revealed more and more interesting details about this threat.

')
We already wrote about Gapz earlier:
- Droppers Gapz and Redyms are based on the Power Loader code
- Modern bootkit technology and detailed analysis of Win32 / Gapz
Win32 / Gapz has a fairly low prevalence level (since the beginning of its first detection, we recorded less than one hundred active samples). Most of these detections were in Russia. All known C & C panels were already closed at the time of the analysis started in December 2012. Domains for loading additional payload were registered through the DynDNS service. Below is a list of such URLs that were found in the dropper after unpacking:
- hxxp: //xpiracyrt.is-into-cars.com/apps/32.lz
- hxxp: //retguard.is-into-cars.com/apps/32.lz
- hxxp: //soparesolv.is-into-cars.com/apps/32.lz
- hxxp: //xpiracyrt.is-into-cars.com/upds/7/1/upd.lz
- hxxp: //retguard.is-into-cars.com/upds/7/1/upd.lz
- hxxp: //soparesolv.is-into-cars.com/upds/7/1/upd.lz
Modification of Win32 / Gapz.C , which contains the MBR infection functionality, sends debug information about the infection process to the following IP address:

Hosting for this IP address is located in Germany and, at the time of publication, is still online.

We found that this IP is associated with several domains: meetafora.ru, sukarabotay.com. Both of these domains were registered in 2011, and they expire in mid-2013. Now this IP has already stopped accepting debug information from the bot.
In all versions of Gapz that contained the bootkit, the addresses of additional C & Cs were extracted from the configuration file, which is stored in a hidden FS. This file is embedded in the main kernel-mode component located on a hidden disk. C & C domains are generated as third level domains (the variable component is the third level domain) using the dynamic DNS service strangled.net (used in Win32 / Gapz.A ).

An example of networking with such a domain is presented below.

Win32 / Gapz.C modification uses a different domain generation scheme:

Interaction with the network in kernel mode is based on the manual implementation of the TCP / IP stack and HTTP protocol in order to bypass the check using local IPS / IDS. Full information on the implementation of the stack, see here .
We believe that the Win32 / Gapz family is the most complex bootkit we’ve seen before. Below is a table of comparisons of Gapz features with other prominent members of bootkits:

Hidden File System Reader with FS Gapz support
To assist security professionals and AV resellers facing Gapz, we updated our Hidden File System Reader tool with the requirements for this bootkit. Now it can also save hidden FS components from Gapz. The utility can be downloaded here .

Source: https://habr.com/ru/post/175911/
All Articles