Vulnerability contest, or Break me completely!
 On March 19, we announced the start of the vulnerability search month “Check Badoo for Strength” . Today, we would like to take the first results and share with you intermediate results, tell you how we prepared for a strength test, examine the most interesting vulnerabilities, and make a feyspalm.
On March 19, we announced the start of the vulnerability search month “Check Badoo for Strength” . Today, we would like to take the first results and share with you intermediate results, tell you how we prepared for a strength test, examine the most interesting vulnerabilities, and make a feyspalm.And first, some statistics:
- in the first two weeks, participants sent us almost 500 applications with potential vulnerabilities;
- about 50 applications were duplicates;
- every tenth application contained a real vulnerability (the most dangerous were corrected within a few hours);
- More than 150 applications amounted to errors that are not related to the security of the site, and about 10% of them are related to platforms that do not participate in the competition.
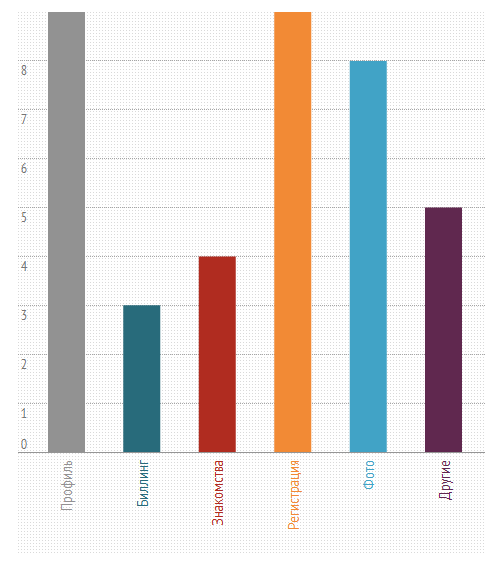
- most of the vulnerabilities accounted for the most important component of the system — the profile (as soon as the contestants did not mock user accounts: they deleted and uploaded photos, manipulated comments, interests, personal data and email addresses).
- More than half of the submitted vulnerabilities are various CSRFs, mainly affecting content uploaded or written by users (deleting and uploading photos and comments, working with a blacklist, favorites, etc.).
Graph of types of vulnerabilities and their distribution by components on the site


How we prepared for the contest ...
A few months ago, we embedded global XSS protection throughout the site. Immediately make a reservation that it is not a panacea and does not cover 100% of vulnerabilities. Its goal is to help the developer prevent a random error. The essence of the method lies in the automatic screening of absolutely all variables that are output through the blitz , except for those moments when the developer specifically allows the output data to appear in unshielded form.
')
The most interesting and the only full-fledged XSS recognizability was found in the output of additional SEO content in an unauthorized profile. Some profile data (mainly the “About Me” field) for various SEO needs was added to one of the meta tags. At this point, the output of raw data was once allowed, which allowed for an attack. Since the vulnerability worked only for unauthorized users, we assigned the first (least dangerous) category to it: it was impossible to get any confidential data through it. The only sensible uses that come to mind are to use account data as an open redirect for further phishing, but in this case you need to be sure that the user is not currently on the site.
... and how not prepared.
In 2013, the OWASP project lowered the CSRF attack rating by three points, despite the general growth of its popularity and the lack of protection of many large web projects. The essence of the attack is simple: when you go to a special page with a form containing a POST or GET request, you can change the content or account settings under a user session. In this place, everything was not as good as we would like. Only part of the functionality on the site (authorization, exit, change of personal information, etc.) was protected by unique session tokens. As soon as the first ten reports about this bug arrived, it became obvious that the problem had to be solved entirely. Within a few days after the start of the competition, we posted another global protection: all web services on the authorized part of the site began to check for the presence of tokens in POST or GET requests to them. With this fix, we closed most of the CSRF applications.
Next we look at some of the most interesting vulnerabilities and give comments to the participants who found them .
Vulnerability in processing the number of credits at purchase (BSI-13)
The author: Nikolai Ermishkin (Asd)
Category: 5
Why did we assign this vulnerability a fifth, highest degree of importance? Because it turned out to be so easy to use that it did not require any special skills and tools other than the browser and any debug console for it. The form for selecting the number of credits looked like this in the HTML code:
... <option data-ga-ev="100 - 45,00." value="100"> <option data-ga-ev="550 (50 !) - 200,00." value="550" selected="selected"> <option data-ga-ev="1250 (250 !) - 450,00." value="1250"> <option data-ga-ev="2750 (750 !) - 900,00." value="2750"> ... It turned out that the value of the value field was used directly! Replacing it with almost any number, it was possible to make a payment in the amount of 220 rubles and get this amount of credits to your account. The vulnerability was fixed in a few hours, and the user with the nickname Asd came in first place in our internal top as the first to discover the vulnerability of the highest degree of significance.
Comment asd
“At first, I simply walked through different sections of the site, tried to change the values of the parameters in the queries, but it was expected that a serious vulnerability such as sql injection could not be found in a project of this level. I remembered the study habrahabr.ru/post/117039 , in which the authors searched for vulnerabilities not directly on the sites, but even Amazon had not survived during their interaction with third-party services and during it. Searching for similar interactions on badoo, I found them in several places - import of contacts, account confirmation, payment of credits and super powers. Having visited the credit purchase page, I discovered the possibility of payment in several ways, and the schemes of interaction with payment systems differed very much.
I decided that it was quite realistic to make a mistake in one of them and began to investigate in more detail. First I chose webmoney, since I had a wallet at hand with a small amount of money. As far as I understand, the purchase is made as follows: the user selects one of the possible options (100, 550, 1250, 2750), his choice is saved somewhere in the internal account on the site, after which the user makes a payment on the webmoney site, during which the paid account It is compared with the saved one, and if they match and the payment is successful, the user receives his credits. Having looked at what parameters are transmitted when saving the account, I noticed that the number of paid loans is transferred directly, and not a certain value, denoting one of 4 possible options. Replacing it with a large number, I received a correct response from the server, with an invoice of 7.5wmz (standard price for 550 credits) and the number of credits I indicated. I paid it - and the credits turned out to be on my account, though in a slightly reduced form - only 2147483647 ”.
Misconfiguration when changing profile data (BSI-12)
Posted by: whitebureau
Category: 5
On the same day, another serious breach was found by the whitebureau user. When interacting with profiles of other users (displaying additional information, performing any actions), the cuid (current user id) parameter, which indicated the ID of this user, was passed in the request parameters.
GET http://badoo.com/ws/profile-ws.phtml?section=pimore&cuid=31337 These interactions were carried out through the same controller that was responsible for editing the profile, the differences were only in the action action, and whitebureau tried to add this userid parameter with an arbitrary value to the user editing request.
POST http://badoo.com/ws/profile-ws.phtml ... section=interested_in&interested_in_text=cats&cuid=31337 It turned out that checking this parameter against the current user ID was skipped when editing a profile. So we have a second critical vulnerability.
Comment whitebureau
Such errors are often found on large projects. And in particular on projects actively working with ajax. There is a confusion with superglobal php variables: developers use $ _REQUEST with all http request variables, instead of the more accurate $ _GET, $ _POST or $ _COOKIE. As a result, an attacker can very simply disorient the code by replacing the desired variable in a post or get request. The script will not notice the substitution.
Clickjacking on all pages of the site (BSI-9)
By: Eugene Farfel
Category: 1
We also received reports of non-critical, but interesting vulnerabilities. One of them was the possibility of so-called clickjacking (English clickjacking) on all pages of the site.
This term was first used by Jeremiah Grossman (English Jeremiah Grossman) in 2008, but so far few people thought about the significance and consequences of this vulnerability. What is clickjacking? As the OWASP says, “It’s a redistress attack”, it’s not a problem. top level page.
Simply put, you can show the site inside an iframe by blocking some of its elements with transparent div tags containing click handlers. In this way, it is possible to force an unsuspecting authorized user to perform arbitrary actions.
One of the most well-known methods of protection is called "framebusting". It checks the opening of the page inside the iframe using Javascript. If the address of the current page is different from what is written in the address bar of the browser, the redirection is performed:
var frameBusted = (top != self); if (frameBusted) top.location.href = '/index.htm'; As it turned out later, this method can be circumvented in most modern browsers:
<iframe sandbox src="http://badoo.com/></iframe> Therefore, since 2009, all modern browsers (even IE) support the X-Frame-Options header, in which you can completely prohibit inserting a site into an iframe, or allow this functionality only for a specific list of domains.
Is your site protected from clickjacking?
Comment by Eugene Farfel
Today, almost all Internet resources are subject to similar Clickjacking vulnerabilities. The process of finding them is not particularly difficult, there is a general rule - if a resource does not use the X-Frame-Options header in its responses, then the existence of the possibility to embed it in a frame with the subsequent creation of various kinds of phishing pages is almost guaranteed. Thus, the vulnerability can be considered found by the results of viewing HTTP-headers.
A study of the .js files used by Badoo showed that a common but erroneous method of replacing the window.top.location property was used to exit the frame. When using this method, the page that embeds Badoo in a frame received an onload event and could take action to counteract it. One of such measures is browser redirection to the address returned with response code 204. A request to such a URL does not lead to navigation in the browser (the page with the frame remains open), but also cancels the attempt of the Badoo code to replace location.
The first patch introduced by Badoo supplemented this code by replacing the body of the page inside the frame with a blank line. This fix, although it did not solve the problem of embedding in a frame, removed all the contents from it and made it impossible to create phishing pages. This fix was also easily managed using the sandbox attribute of the iframe tag, which disables javascript in the frame.
In principle, the only way to protect against Clickjacking attacks is to use the X-Frame-Options header for all pages for which it is not supposed to embed a frame and confirm all actions that change the state of the system on pages that imply embedding in a frame.
CSRF and Custom Email Changes (BSI-38)
Posted by: graphite
Category: 3
(partly about this vulnerability is in BSI-21, author Ilya Kiel)
This is what we did not expect, so these are descriptions of how to change the email address for an arbitrary user. But in one day, as many as three descriptions of various vulnerabilities related to the re-send password component came, with which it was possible to change the user's mailbox, that is, to “hijack” his account.
There is a form for re-sending the password during registration, in which you can change your email if a typo crept into it. It turned out that the user can even change the already confirmed email address using the CSRF:
<form action=http://eu1.badoo.com/not_confirmed/" method="post" id="form"> <input type="hidden" name="post" value="1" /> <input type="hidden" name="newemail" value="attacker@somemail.com" /> <input type="submit" /> </form> <script>$('#form').submit();</script> There were several ways to fix the vulnerability:
1. Add a verification for confirmation.
2. Add a CSRF token.
3. Add a captcha.
Since the module is critical, all three methods were applied, and users who found vulnerabilities were rewarded.
Comment Graphite
Since I had never been acquainted with Badoo before, in the first place, I decided to find out what can be done here. Immediately attention was attracted by the possibility of importing contacts from different mail services - I wanted to check whether such an address is included in the list of additional e-mail for password recovery. Alas, not paid. But my thoughts had already gone in this direction, and after a while I came across a form for resending an e-mail to confirm registration with the possibility to enter another e-mail, instead of the wrong one. In this form, there was a CSRF, but what was most surprising was that if an authenticated user filled out this form, he changed the e-mail in the profile. Obviously, in this scenario there was no check on whether the user has already confirmed his e-mail.
CSRF and Linking External Social Networking Account (BSI-44)
Posted by: chipik
Category: 4
Also found vulnerabilities in the interaction of the site with external resources. We have a functionality that allows you to associate a profile on a site with external Facebook, VK or Google+ accounts. Through them, users can log in to the site without memorizing a username and password. A chipik participant checked this algorithm for strength and found a way to deceive him.
With the help of the Tamper Data plug-in for Firefox, you can intercept a request to bind an external account and get an Authorization Token. If an attacker forces an authorized user to click on a link with this token using CSRF, his account will be tied to the attacker's external account and allow the latter to log in with this user. The most correct decision was to add a session-unique CSRF token to all transactions with an account link.
Comment chipik
Thank you, E.H. for the vector :)
We remind you that applications are accepted until April 19 and you still have a chance to take part in the competition, get a reward, and also help make our platform more secure.
After the end of the competition, we will select the 3 most active participants and give them an additional £ 1,000.
We also have 50 cool T-shirts with the symbols of the contest and thank-you letters signed by the jury, which we will distribute to the most active participants.
Keep testing us for strength!
Stanislav Eremin and the team Badoo Development
Source: https://habr.com/ru/post/175865/
All Articles