Microsoft released another set of updates, April 2013
Microsoft announced the release of the next series of patches aimed at eliminating vulnerabilities in their products. Previously announced pre-release (April 4), security fixes cover a total of 12 unique vulnerabilities ( 2 fixes with the Critical status and 7 with the Important status ). A detailed report (including correlation fixes with CVE ID) can be found here . One of the critical updates (as in the past month) is aimed at eliminating the vulnerability that is present in all versions of Internet Explorer, starting with version 6 and ending with the latest IE 10 ( MS13-028 ). The vulnerability belongs to the class Remote Code Execution and can potentially be used to successfully implement drive-by download / installation attacks. Also, immediately three fixes with the Important status are aimed at eliminating vulnerabilities in the kernel, are associated with incorrect operation of the code with objects in memory and are of the Elevation of Privilege type.

The source says that we are talking about flaws in IE, the successful exploitation of which was demonstrated by VUPEN rewriters at the Pwn2Own contest in Vancouver. For a demonstration of the work of the exploit, they received $ 100,000.
')
The Internet Explorer hotfix resolves two vulnerabilities CVE-2013-1303 and CVE-2013-1304. These vulnerabilities are exploited when browsing a specially crafted web page by the browser, while the attacker gets the same rights in the system as the current user. It uses the use-after-free technique, in which the browser code continues to use the memory block after it is actually released.
Recall that flaw of the Remote Code Execution type has a Critical rating, since its operation can lead to situations of code execution without user intervention . That is, the vulnerability, potentially, can be used by malicious code with the possibility of self-propagation (for example, network worms). In another case, the possible hidden / "silent" installation code when clicking on a malicious link.

To apply the fix to IE, a reboot is required.
Another Critical update addresses the vulnerability in the RDP client ( MS13-029 ). The vulnerability also has the “Remote Code Execution” type and is contained in the ActiveX component of the Remote Desktop Connection 6.1 and Remote Desktop Connection 7.0 clients (mstscax.dll). At the same time, flaw covers the OS to Windows 8 and does not include Windows RT (Windows XP - Seven as Critical and server versions as Moderate) . The user is also at risk when viewing a specially crafted web page. Both Critical vulnerabilities are marked as:
This underlines the fact that they were not seen in exploitation in the wild. A fix may require a reboot.
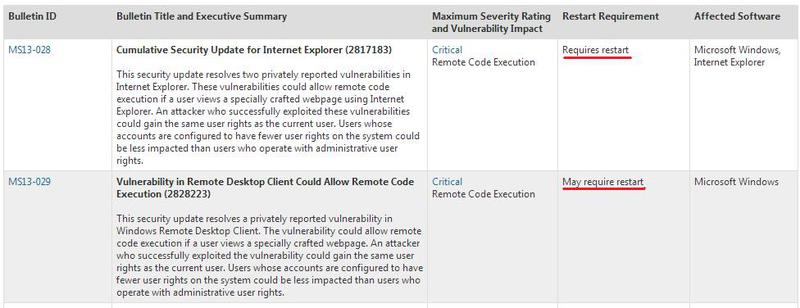
At once three fixes with the Important status belong to the kernel and the vulnerabilities are of type Elevation of Privilege. These are MS13-031 , MS13-033 and MS13-036 . MS13-031 deals with two vulnerabilities: CVE-2013-1284 and CVE-2013-1294 (Exploit code would be difficult to build), which, apparently, are in the kernel code ntoskrnl (incorrect work with objects in the kernel) . Applicable to all versions from Windows XP to Windows 8 and RT x32, x64 . After successful exploitation, the attacker can read the kernel mode memory. MS13-033 closes flaw in the csrss process (Client / Server Run-time Subsystem) - part of the Win32 / Windows subsystem that runs in user mode. Vulnerability in the case of csrss is also associated with incorrect work with objects in memory. MS13-036 has similar symptoms and is related to win32k.sys, part of the Win32 subsystem operating in kernel mode and the NTFS file system driver ntfs.sys. Operation of these flaws is possible using a specially prepared application that runs on the local machine.
Recall that MS releases monthly updates for Windows XP starting with SP3 and Windows XP x64 starting with SP2 . MS announced the end of support for Windows XP SP3 from April 8, 2014, that is, a year later.

Support for Windows 7 without SP1 has been discontinued .

In general, the April suite of updates addresses vulnerabilities in the following products: Microsoft Internet Explorer (6-10 on Windows XP-8 x32 and x64), Windows SharePoint Server, Office Web Apps, Windows Defender for Windows 8 and Windows RT .
We recommend that our users install updates as soon as possible and, if you have not already done so, enable automatic delivery of updates using Windows Update (this option is enabled by default).

be secure.

The source says that we are talking about flaws in IE, the successful exploitation of which was demonstrated by VUPEN rewriters at the Pwn2Own contest in Vancouver. For a demonstration of the work of the exploit, they received $ 100,000.
')
The Internet Explorer hotfix resolves two vulnerabilities CVE-2013-1303 and CVE-2013-1304. These vulnerabilities are exploited when browsing a specially crafted web page by the browser, while the attacker gets the same rights in the system as the current user. It uses the use-after-free technique, in which the browser code continues to use the memory block after it is actually released.
Recall that flaw of the Remote Code Execution type has a Critical rating, since its operation can lead to situations of code execution without user intervention . That is, the vulnerability, potentially, can be used by malicious code with the possibility of self-propagation (for example, network worms). In another case, the possible hidden / "silent" installation code when clicking on a malicious link.

To apply the fix to IE, a reboot is required.

Another Critical update addresses the vulnerability in the RDP client ( MS13-029 ). The vulnerability also has the “Remote Code Execution” type and is contained in the ActiveX component of the Remote Desktop Connection 6.1 and Remote Desktop Connection 7.0 clients (mstscax.dll). At the same time, flaw covers the OS to Windows 8 and does not include Windows RT (Windows XP - Seven as Critical and server versions as Moderate) . The user is also at risk when viewing a specially crafted web page. Both Critical vulnerabilities are marked as:
This issue was privately reported.
This underlines the fact that they were not seen in exploitation in the wild. A fix may require a reboot.

At once three fixes with the Important status belong to the kernel and the vulnerabilities are of type Elevation of Privilege. These are MS13-031 , MS13-033 and MS13-036 . MS13-031 deals with two vulnerabilities: CVE-2013-1284 and CVE-2013-1294 (Exploit code would be difficult to build), which, apparently, are in the kernel code ntoskrnl (incorrect work with objects in the kernel) . Applicable to all versions from Windows XP to Windows 8 and RT x32, x64 . After successful exploitation, the attacker can read the kernel mode memory. MS13-033 closes flaw in the csrss process (Client / Server Run-time Subsystem) - part of the Win32 / Windows subsystem that runs in user mode. Vulnerability in the case of csrss is also associated with incorrect work with objects in memory. MS13-036 has similar symptoms and is related to win32k.sys, part of the Win32 subsystem operating in kernel mode and the NTFS file system driver ntfs.sys. Operation of these flaws is possible using a specially prepared application that runs on the local machine.
Recall that MS releases monthly updates for Windows XP starting with SP3 and Windows XP x64 starting with SP2 . MS announced the end of support for Windows XP SP3 from April 8, 2014, that is, a year later.

Support for Windows 7 without SP1 has been discontinued .

In general, the April suite of updates addresses vulnerabilities in the following products: Microsoft Internet Explorer (6-10 on Windows XP-8 x32 and x64), Windows SharePoint Server, Office Web Apps, Windows Defender for Windows 8 and Windows RT .
We recommend that our users install updates as soon as possible and, if you have not already done so, enable automatic delivery of updates using Windows Update (this option is enabled by default).

be secure.
Source: https://habr.com/ru/post/175531/
All Articles