Restrict access to packaged applications
 We all know that with the release of Windows 8, Microsoft decided to completely change the way users view desktop applications. Packed applications, they are Metro-applications, are distinguished by uniformity, updated simplified appearance and new user interaction. In these applications, distractions are minimized, virtually all graphic effects, including Windows Aero, over which Microsoft has been working for the last few years, have been removed, and all applications have the same color gamut, fonts, and so on. We are not going to dwell on whether Microsoft did well, that they decided to return to applications in the style of Windows 3.1, however, we will have to accept this and take some actions to service such applications.
We all know that with the release of Windows 8, Microsoft decided to completely change the way users view desktop applications. Packed applications, they are Metro-applications, are distinguished by uniformity, updated simplified appearance and new user interaction. In these applications, distractions are minimized, virtually all graphic effects, including Windows Aero, over which Microsoft has been working for the last few years, have been removed, and all applications have the same color gamut, fonts, and so on. We are not going to dwell on whether Microsoft did well, that they decided to return to applications in the style of Windows 3.1, however, we will have to accept this and take some actions to service such applications.As everyone knows, starting with operating systems such as Windows 7, specifically to perform tasks related to restricting user access to specific files or applications, in addition to Microsoft's SRP policies, they created a new technology, which they called AppLocker. An AppLocker policy is a collection of AppLocker rules that include various settings intended to be enforced. As characteristic of GPOs, each rule is stored in a particular policy, and the policies themselves are already distributed according to your hierarchy of GPOs.
Unlike classic applications, all packaged applications have common attributes — the name of the publisher, the name of the product, and its version. Therefore, all applications can be managed using one type of rules. In Windows Server 2012 and Windows 8 operating systems, AppLocker rules for packaged applications can be created separately from classic applications, that is, a separate collection has been specifically allocated for them. A single AppLocker rule for a packaged application can control both the installation and the operation of the application. Since all packaged applications are signed, AppLocker only supports publisher rules for packaged applications. Let's see how to restrict access to packaged applications.
I would like to immediately note that a mandatory requirement is the availability of such applications on the computer where the rules will be created, so we will have to install such applications now.
Let's go to the Windows Marketplace and find some standard applications, for example, let it be such standard applications as Microsoft Zune Music, Microsoft Zune Video, Microsoft Bing News, Microsoft Bing Maps, Microsoft Bing Travel and Microsoft Bing Sports. Install these applications on your computer. How they look and what their main purpose is, you already know what I am more than sure about. The installation of some packaged applications is shown in the following illustration:
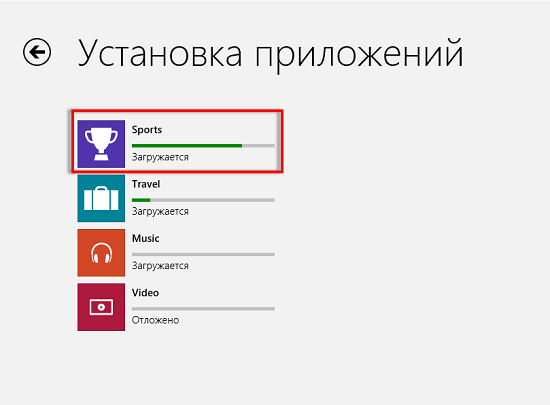
Fig. 1. Install four packaged applications from the Windows Marketplace
 Again, be sure to pay attention at the time that the target computer to which the AppLocker rules will apply must be running the Application Identity service . You can either manually monitor this moment directly from the services snap-in of each computer, or centrally configure such services by means of a special extension of the client side of group policy, which, in my opinion, is much more logical. By default, it has a “Manual” startup type, so that in any case you will have to take some measures.
Again, be sure to pay attention at the time that the target computer to which the AppLocker rules will apply must be running the Application Identity service . You can either manually monitor this moment directly from the services snap-in of each computer, or centrally configure such services by means of a special extension of the client side of group policy, which, in my opinion, is much more logical. By default, it has a “Manual” startup type, so that in any case you will have to take some measures.Now you can go to the rules AppLocker.
Creating an AppLocker Rule
To create a rule that restricts access to a packaged application, say, to Microsoft Bing Sports, you need to do the following:
- To begin with, we naturally create a new group policy object in the Group Policy Management snap-in, since it’s best if the rules intended to restrict applications are located in a separate GPO and call it, say, AppLocker Rules . After that, it will be necessary to associate such an object with a subdivision, which includes computer accounts to which the rules we create should apply. For example, in my case, the binding goes for the entire domain, but in a real environment, the ideal option would be to distribute target computers across specific departments. The final task of the preliminary stage will, of course, be the discovery of the Group Policy Management Editor itself;
- Now, in the snap-in snap-in, expand Computer Configuration \ Policies \ Windows Configuration \ Security Settings \ Application Control Policies and go to the node called AppLocker ( Computer Configuration \ Policies \ Windows Settings \ Security Settings \ Application Control Policies \ AppLocker ). We now turn to the latest collection, which is called “Rules for Packed Applications,” which in English sounds like “ Packaged app Rules ”. Being inside this collection, we will create our rule, that is, we should select the option “Create New Rule” ( Create New Rule );
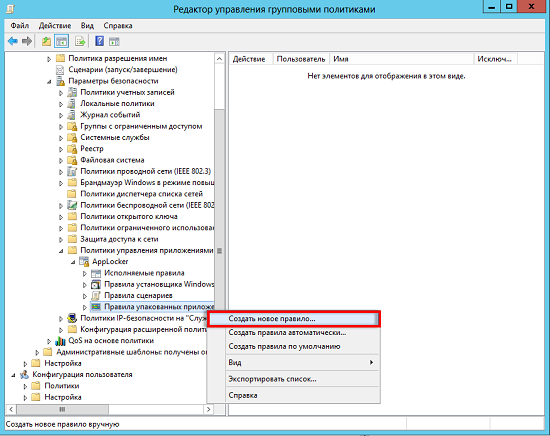
Fig. 2. Creating a new AppLocker rule - You will be presented with the AppLocker Executable Rules Creation wizard dialog box. Here, on the first page of the wizard, you just need to read the information provided, and then click on the "Next" button;
- On the page with permissions, of course, you need to choose whether you will eventually allow the user to launch the packaged application of your choice, or, conversely, you want to once and for all prohibit users from using any means. Since in this case the main task was to prohibit access to a specific packaged application, we will now stop on this option. In addition, here you can select a specific user or group of users to which this rule will apply. In this case, ignore this option and move on;
')
Fig. 3. Definition of permissions for the created rule - As you will see in the illustration at number 5, the next page is called “Publisher” , and here you can’t choose either the path rule or the file hash rule that you could work with in other AppLocker categories in the same Windows 7 or Windows Server 2008 R2. Here you can choose one of the following options:
- Use for example the installed packaged application ( Use an installed packaged app as a reference ). In this case, you should select an application that is already installed on the computer. When creating a rule, the publisher, the package name, and the version of this application will be used;
- Use as an example the installer of the packaged application ( Use a packaged app installer as a reference ). Having stopped on this variant, you will need to specify the installation file of the packaged application with the appx extension. As in the previous case, the publisher, the package name and its version will also be used to define the rule. This option is acceptable if users install such applications manually, say, using PowerShell.
Since our applications are already installed, we will focus on the first option and click on the select button. In the dialog box that appears, as seen in the illustration below, all installed packaged applications will be displayed. Despite the fact that on the left you can mark a checkbox for setting checkboxes, don’t count on much, as you will not be able to set more than one flag at a time. For example, now we will create a rule for Microsoft Bing Sports, that is, we choose it;
Fig. 4. Select an installed packaged application. - As you can see in this illustration, which was discussed a little higher, at the bottom of this wizard page you can specify properties for the rule being created. The following properties are available here:
- Any Publisher . This property is responsible for all publishers for the category of files you select. For example, if you initially select the value “Allow” , then in this case this rule will further prohibit the execution of unsigned applications. Or, of course, you can once and for all ban the use of any packaged applications;
- Publisher ( Publisher name ). Using this control you can specify that all files signed by the publisher with a specific name should fall under the scope of the rule;
- Package name . This property of the rule allows you, in addition to data about the publisher, to add to the rule the name of the package of the packaged application itself. In this case, it is Microsoft. BingSports;
- Package version . This is the most flexible property of the rule being created. Here you can determine the version of the application you are managing. For example, to specify a specific version of a packaged application, you, as in the case of regular exe-files or dynamic libraries, can check the box with options with custom values, and then manually specify the version number and choose whether you want the rule to apply to for applications whose version is higher than the value specified by you, lower it, or for the rule to be applied only to a specific version of the software product.
Since applications are updated quite often, we now ignore the version of the application and move the slider to the package name. Looks like it's done. Go to the next page of the wizard.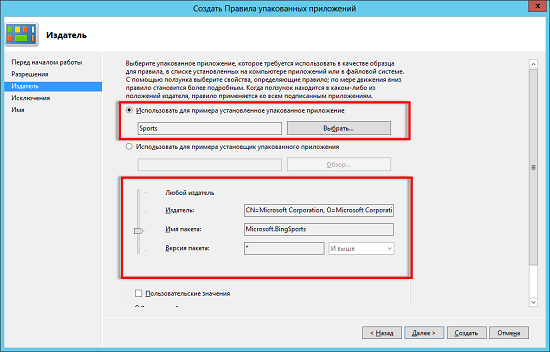
Fig. 5. Setting properties defining the rule for a packaged application - We will not add exceptions now, so we go to the last page. As you can see in the following illustration, the name of the rule here is quite digestible, therefore, to create our new rule, we immediately press the “Create” button.

Fig. 6. The last page of the AppLocker Create Rule Wizard
Immediately check that we have succeeded. Update the policy settings and go to the start screen "Start" . Let's try to open our sports application.
As can be seen on the last illustration in this article, a message appeared where it was written that this application was blocked by the system administrator, that is, the message that we expected to see. Consequently, the focus was a success.

Fig. 7. Checking the actions performed
Summarize
In this short article, you learned how to limit access to one of Microsoft's innovations in their latest operating system - packaged applications, which are often called by Metro applications. It was told about how exactly such rules can be created, what they are based on, and also about one important prerequisite that must be followed before the deployment of such rules. Do you use packaged applications in your company and do you plan to restrict users to accessing some APPX files?
Source: https://habr.com/ru/post/175481/
All Articles